Connect Two Private LANs from Different Companies Using Netgate 2100
-
Hi @johnpoz
Maybe I'm not describing my interpretation of the bridge suggestion properly.
I asking for confirmation of the physical connections first (that is the most important thing to get right, as I ready bridges if not properly connected can cause loops and take an entire network down), and then where to set up the firewall rules. On the bridge itself or on the LAN interface used for the cable coming in from the other company.
I would really like to get my server off an outside company's private subnet. I have no control over the other company's private subnet.
But from what I've studied, that may not be possible to set up a traditional internal firewall/router set-up between the two subnets without changing things on the main perimeter firewalls/routers on the two private subnets. That will just create a bunch of hassle between the companies..... I'm looking for something I can quietly do myself and no one will notice. And I'm the only one that can control the 2100. I can shut the other company off completely from my server if some happens (virus, etc.), even if the cable is still connected to the 2100.
I had looked at a bridge before. I had dismissed the bridge idea previously because from what I know of bridges, it's essentially joining of two networks and treating them at the IP level as the same network. That is not a go.
From what @netblues mentioned, probably the least complex and least intrusive solution (though it does not get my server off the other company's subnet) is to use two LAN ports on the 2100. Connect NIC2 on my server to one LAN port on the 2100. Connect the cable coming in from the other company to another LAN port on the 2100. Create a bridge between the two LAN ports.
Though it's not clear if this is considered a transparent bridge or not. And it's not clear to me what IP address I should use for the bridge. It seems bridges can not use NAT, so I have to create the pass rule(s) to allow only incoming traffic from the other company's subnet on TCP port XX through the bridge to reach my server on their subnet IP address denoted on NIC2 on my server.
That is what I'm asking to confirm if I'm interpreting @netblues suggestion on the bridge application correctly.
-
@jtd again putting in a pfsense box is way over the top for what you have described..
You have this right?
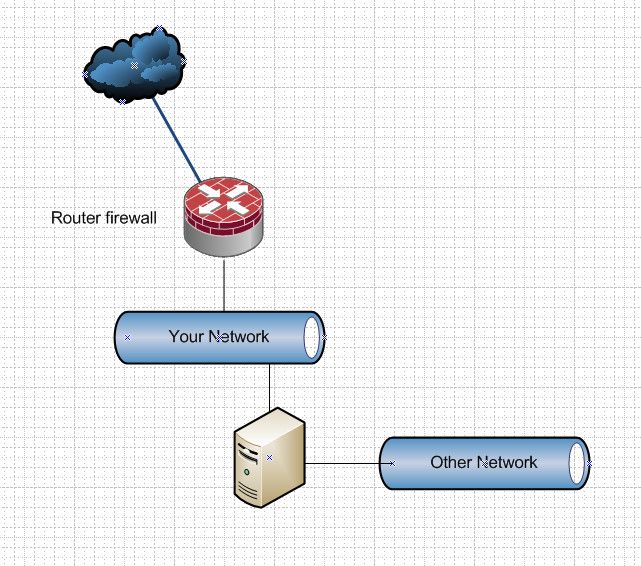
What do you think setting up pfsense with a transparent firewall, etc.. gets you vs what can already be done via simple firewall rules on that server?
I agree should of prob never been setup like this in the first place. But setting up a pfsense box as just a transparent firewall just seems like overkill for something that can already be done via just the firewall on the server..
You clearly still want to allow access from this other company to this server, So other than filtering access to other services on this server, smb, ftp, AD, whatever - which can just be done in the servers host firewall. I am not understanding what putting in a pfsense box just for this server gets you other than cost complexity and time?
If you were replacing your current edge firewall with pfsense, and wanted to allow this other company network into this server via your shiny new pfsense box for you whole network that would be different. But sounds like your going to put this in to just be firewall between this 1 server connection and this other network..
-
@jtd Obviously, as johnpoz said, using the built in firewall of the server will do the same as the pf.
However since we dont know if you have the necessary admin rights on your server for this, or maybe there is a chance someone else is also fiddling with the server firewall, an external firewall is maybe something to consider.
Yes, it IS an overkill for just one host, but still.Routing is a no go. Way too many things to change.
A bridge doesn't need an ip, since it operates at layer 2.
So filtering at layer two, is also called a transaparent firewall.
And no, there is no loop to be created if you bridge your servers second lan with the foreign network.
Think of pfsense as a plain l2 lan switch, just with rules. -
Thank you both for the information. Greatly appreciated. I am slowly getting what you are saying on the bridge setup.
Yes all your comments are correct and valid... Without saying too much, when I say server, really this was not the most professional job. It's a Mac Mini, and I would love to replace it with a proper hardened Linux server one day given the value of the data it handles.
For the price, I'm OK using the 2100 as a secure firewall in this case, setting it up once and leaving it. That way I know the network is protected and only I can control what comes into the network. All I need is for something to happen and you know how that goes. Not worth the risk.
@johnpoz your diagram is correct.
Yes, so we're agreed on the physical connections and that a transparent firewall is what I set up using the 2100 (2 LAN ports) between the 2nd NIC on my server and LAN1 port on the 2100, then the cable coming into the comms room which will connect the LAN2 port, which is the interface to the other company's private subnet.
I'm assuming I would leave the static IP information in my 2nd NIC the same, and it would still sit on the other company's subnet and be visible to them on their network based on the firewall rule I set up.
I'll set this 2100 up in the lab this evening as a transparent firewall and test it before connecting it to the live network.
@netblues When you use the term Layer 2 filtering, are you saying set up the firewall rules the same way I normally would after setting up the transparent firewall? Do I do this on the transparent bridge interface or on the LAN2 port interface? Do I not need an IP address on the bridge interface for management?
Thanks, I think my questions are coming to and end and I'll set this up in the lab over the next couple days and get back to you all. Appreciated.
-
@jtd said in Connect Two Private LANs from Different Companies Using Netgate 2100:
That way I know the network is protected and only I can control what comes into the network.
Its not coming into the "network" its coming into this one "server" (mac mini).. Did you setup this box to route traffic. Now true it could be exploited and then from that a jump off point into your network. But any services allowed to this box could be used to exploit it and do that - firewall or not.. This is true for any box exposed to any outside access at all.. This is why normally you put servers that are serving public in a "dmz" where it is isolated from the rest of your network.
macOS comes with a firewall.. You can limit the access to just the services you want, etc.
If I was worried about their access to this box, in any way. I would isolate this box from the rest of your network.. And limit its access to stuff in your network it might need and that is it, etc.
Yes the 2100 can be used as a transparent firewall with no changes being needed on this servers IP or the other companies network or access, they wouldn't really even know the 2100 is there, etc. I just don't see how it really gets you anything that couldn't just be done on the boxes own firewall.
-
@johnpoz I hear all your points. I've looked at the DMZ, etc before. Understand about the software firewall in MacOS.
All that will take time. I've tried and succeeded in hardening the perimeter network over time. This 2100 is the last bit, and then I need to leave things for a while before moving the public servers to a DMZ, etc. I can not say too much on a public forum.
I'll let you all know how it goes in a couple days. Appreciate all your help and solid input.
-
@jtd Sounds sensible to me.
What you are doing is creating a perimeter firewall system you can maintain. It provides you with the flexibility to change the physical hardware behind it, and monitor what is actually happening in a more uniform way across you business. -
As usual, the "enemy" is much closer than we think :)
So yes, a perimeter is nice to have.
Have a look here
https://docs.netgate.com/pfsense/en/latest/bridges/firewall.htmlRegarding firewall rules and firewalling.
-
I got the setup configured with the bridge using two of the LAN ports.
I set it up in the lab first and observed the behaviour for a day (I just let everything pass on the bridge in the lab test).
Based on that behaviour, and the applications needing to get through the bridge, I created pass rules for the specific application needed. There's a lot of communications going on I noticed that had nothing to do with the needed application. Blocking those at the bridge has no impact on the application.
It's in production now running the final firewall rules I came up with, and all looks good so far.
Yes, not ideal (which I confirmed with a couple proven Tier 1 Internet network carrier level IP guru colleagues), but this gives us a hardened, dedicated firewall on this backdoor under our total control.
Thanks for this. Greatly appreciated.
-
@jtd said in Connect Two Private LANs from Different Companies Using Netgate 2100:
There's a lot of communications going on I noticed that had nothing to do with the needed application
:)
pfsense is more than pf
A dedicated firewall gives you visibility and monitoring
Well done