Pfsense DNS specific to VLAN
-
@narsaw said in Pfsense DNS specific to VLAN:
KidsPCVlan10->DC->Pfsense-> 1.1.1.3 (dns específico para vlan)
SOLUTION 1: YOU CAN USE Pi Hole
SOLUTION 2: YOU CAN CONFIGURE YOUR DNS SERVER TO DO DNS FORWARDING (TO YOUR EXTERNAL DNS SERVER)
SOLUTION 3: AS @SteveITS MENTIONED You can simply use a blacklist on vlan 10 pfsense to block access to dangerous sites.
Whatever your choice, they are all simple and easy.
I'll be here if you need help. -
@silence for solution 2 I am bit confused on how this would work. The DC does DNS for all PC's in my network (including kidsPC) so if the DC forwards to a kidSafeDNS the all PC that rely on the DC for DNS will be pointed the kidSafeDNS. My understanding is that conditional forwarding does not work for this case.
Here is what I am chasing.
KidsPCVlan10->DC->Pfsense-> 1.1.1.3 (kids safe stuff)
DadPCVlan20->DC->pfsense-> 8.8.8.8 (unrestricted)OR (is this conditional forwarding?? (does not work I've been told))
KidsPCVlan10->DC-> 1.1.1.3 (kids safe stuff)
DadPCVlan20->DC-> 8.8.8.8 (unrestricted)I guess this must not be a very common thing that Parents / organizations do? Or perhaps they have multiple DCs
The Pi Hole and pfblockerNG are interesting ideas that are probably worth exploring but would rather using a simple DNS.
-
Try configuring pfSense to forward your network domain to the DC, and point the kids’ devices to pfSense for DNS.
-
@steveits Thx but that wont work. All PC's in the home is part of my DC's domain so they must all point to it for DNS or else the active directory will not work properly. In my DC, I have this line in my Samba DC config.
dns forwarder = 192.168.77.254That IP is my pfsense router, which makes pfsense thinks all DNS request is coming from that IP/subnet. which in turn resolves via root certs.
In the end it seems like I have over reached in my home network trying to run it like an IT dept :)
-
@narsaw said in Pfsense DNS specific to VLAN:
my home network trying to run it like an IT dept :)
no, not at all so far I'm just looking at simple configurations! all he wants to do is simple quick and easy I just see that maybe he's drowning you in a glass of water.
FIRST: IN DHCP OF VLAN 10 AND 20 CONFIGURE DNS OF WINDOWS SERVER AND IN DNS OF WINDOWS SERVER FORWARD TO PFSENSE DNS (IN PFSENSE FORWARD VLAN 10 TO SECURE DNS AND VLAN 20 TO PUBLIC DNS 8.8.8.8 AND READY NO IT IS SO DIFFICULT.
If you don't know how to do it, I can guide you step by step.
-
@silence said in Pfsense DNS specific to VLAN:
PFSENSE FORWARD VLAN 10 TO SECURE DNS AND VLAN 20 TO PUBLIC DNS 8.8.8.8
How would you do that? Maybe I'm missing something.
My understanding is that all of the DNS requests being forwarded from the domain controller would be coming into pfsense from the IP address of the domain controller. There is no way for pfsense to parse it into different vlans.
Here's a filtered log for a domain computer that uses a domain controller for local DNS queries that then forwards to pfsense. As you can see there are no DNS queries in the logs to port 53 from the computer's ip 192.168.163.8.
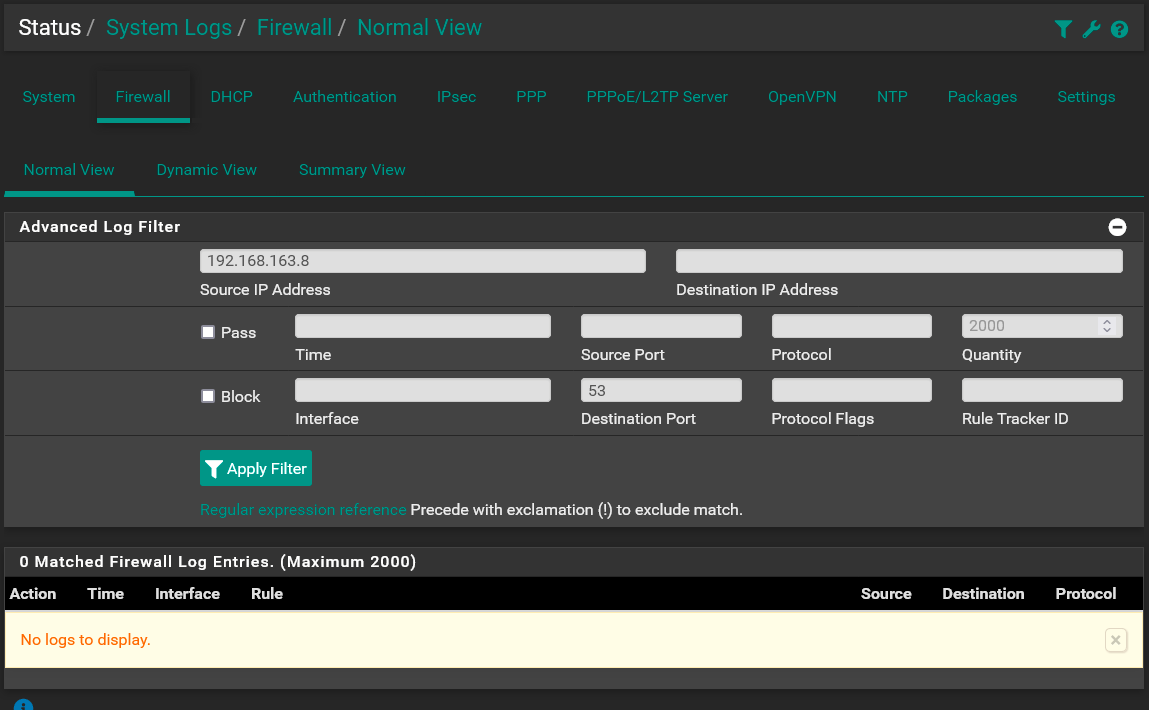
And if you run the same query for the domain controller you get the following:
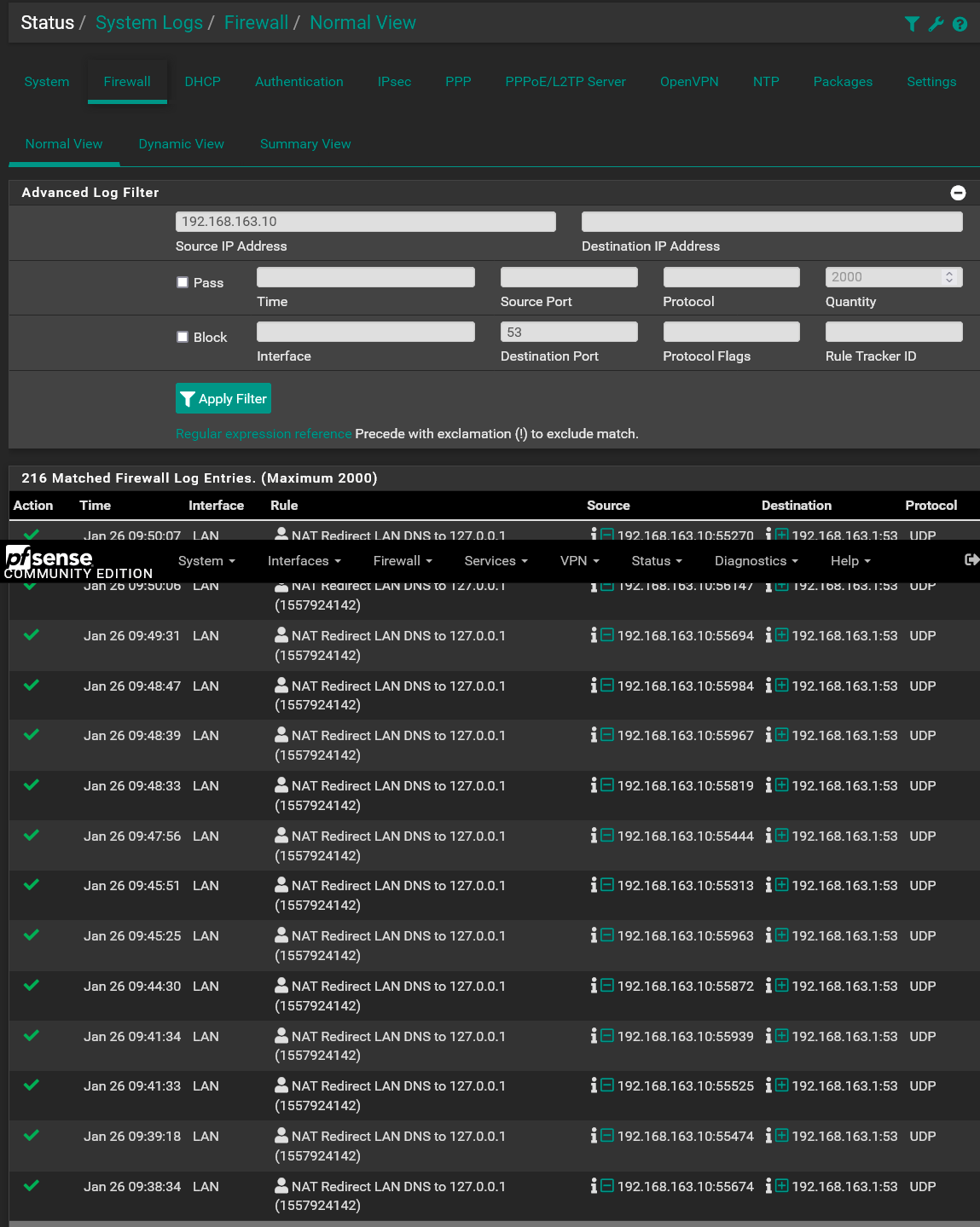
The only thing pfsense is going to see is a DNS request coming from the domain controller. Pfsense will resolve the name and return the result back to the domain controller which then sends the result to the client.
-
@narsaw said in Pfsense DNS specific to VLAN:
Thx but that wont work. All PC's in the home is part of my DC's domain so they must all point to it for DNS or else the active directory will not work properly
That's where I'm trying to get you to. :) I've done it. Especially useful if IPv6 is defaulting to the router DNS. In the DNS Resolver settings add a Domain Override for your example.lan domain name pointing to the DC IP. Any queries for example.lan coming to pfSense will be forwarded to the DC. The kids can use pfSense for DNS, which otherwise is set to forward to 1.1.1.3 or whatever.
The rest of the PCs query the DC directly. I think that will accomplish what you want.
-
@dma_pf said in Pfsense DNS specific to VLAN:
How would you do that? Maybe I'm missing something.
PC CLIENTE VLAN 10 ---> PFSENSE DNS VLAN 10 ---> DNS SERVER ----> DNS SECURE 1.1.1.3
PC CLIENTE VLAN 20 ---> PFSENSNE DNS VLAN 20 ---> DNS PUBLIC 8.8.8.8 -
@silence You may have missed the earlier discussion as all PCs have are pointing the DC for DNS and not pfsense directly. The DC forwards request to pfsense that it does not know about (i.e non local DNS request)
-
@narsaw said in Pfsense DNS specific to VLAN:
You may have missed the earlier discussion as all PCs have are pointing the DC for DNS and not pfsense directly. The DC forwards request to pfsense that it does not know about (i.e non local DNS request)
I don't know if you still have a problem, but both the answer @SteveITS gave you and mine can work, it's up to you which one you want to use! but your case is very easy.
I even have the same situation as you at my work.
all pc use their DC (FOR LOCAL DNS) BUT FOR SOMETHING EXTRA THEY GO TO PFSENSE DNS AND HE KNOWS WHAT TO DO I HAVE VLAN RESTINCTIONS WITHOUT ANY TYPE OF PROBLEM. AND IT HAS ALWAYS WORKED VERY WELL.