Seperate pfSense machine and Proxmox Machine
-
I have pfSense setup as my main firewall and Proxmox connected to the pfSense firewall, I had a hard time figuring out how to let updates go through the firewall then all of sudden the firewall let me update the Proxmox software.
I have know clue why it started working all of a sudden.
I also have many OS's on my VM and it is not letting me update most of the OS's.
( apt get update etc.)So what I am asking is do I have to create an any rule for VM's to update their software, and are they still protected if I open the door for them to update?
Also when you create a firewall rule does it take affect right away or is there a delay, I am asking this because when I create rules I test them right away and most times I can never truly verify what I just created.
-
There is nothing special required to allow that. The default ruleset allows all outbound connections so if it's being blocked it can only be by a rule you have added or by being on a internal interface other than LAN.
Do you see traffic blocked in the firewall log?
Do you have Snort, Suricata or pfBlocker enabled? They can appear dynamically.
Changes to the firewall rules do happen immediately but existing states are not removed. So if you have pass rules that have created a state and then you add a block rule above it and existing traffic will continue until open states timeout.
Steve
-
@ace-1 said in Seperate pfSense machine and Proxmox Machine:
many OS's on my VM and it is not letting me update most of the OS's.
sounds like a network configuration problems in Proxmox to me
-
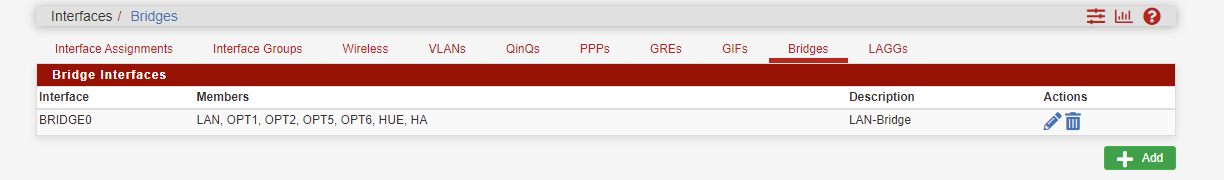
As you can see by the pic I have LAN under the LAN-Bridge, I had alot of nic's lying around so I made my own firewall. I also just bunched everything together because I don't know enough yet on how to created different networks, i need all these systems to talk with other.
OPT1 and OPT2 are windows servers, LAN is a TP-link switch, OPT5 empty, OPT6 is a UNIFI UAP AC Pro, HUE is the hub, and HA is Home Assistant that runs the house.
I have snort and pfblocker enabled but when I disabled both of them I still couldn't updated some of the VM machines. I restarted pfsense to break the states but still get some VM's that update and some that just give errors when updating.
Parrot will update
Ubuntu won't update
RaspberryPi won't update
TrueNAS will updateI also have a VPN setup to controll all traffic through the LAN-Bridge with a couple of rules to let Netflix's out.
-
Well assuming you have rules on the bridge to pass the traffic it's almost certainly Snort or pfBlocker preventing it.
Do you have Snort in blocking mode? If so it's probably that, it will alert on apt updates with the default rulesets if you install everything. Disabling Snort does not remove block rules so check the alerts and blocked hosts there.Steve
-
I turned off the snort blocking setting and it worked. Thanks
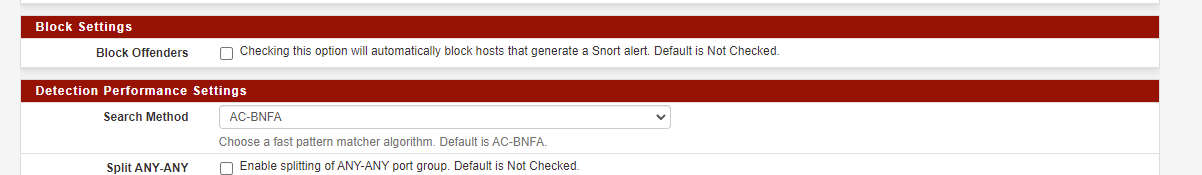
By turning this off does it leave vulnerable anywhere?
-
I had to completely turn off snort and clear all the block list.
I like to use snort but there must be something I am doing to block all these OS's update.
-
Like I said if you just load all the rules and don't tune anything it will alert and block on most Linux pkg updates. You need to suppress the alerts or disable the rules that are triggering it. https://docs.netgate.com/pfsense/en/latest/packages/snort/suppress-list.html
We usually recommend running Snort for a least a week in non-blocking mode whilst monitoring the alerts. Only enable blocking once it's no longer alerting on legitimate traffic.
Steve