2.5.2 Multi Wan DNS - DNS Forwarding and Static Routes - DNS Query not using proper GW
-
Hi,
I did not found similar thread on forum.
Either I don't understand, or something is wrong here
Simple configuration, 1 pfsense box, 2 WAN, 1 LAN
DNS Query not using sticky configured GW - instead it use all GW on system.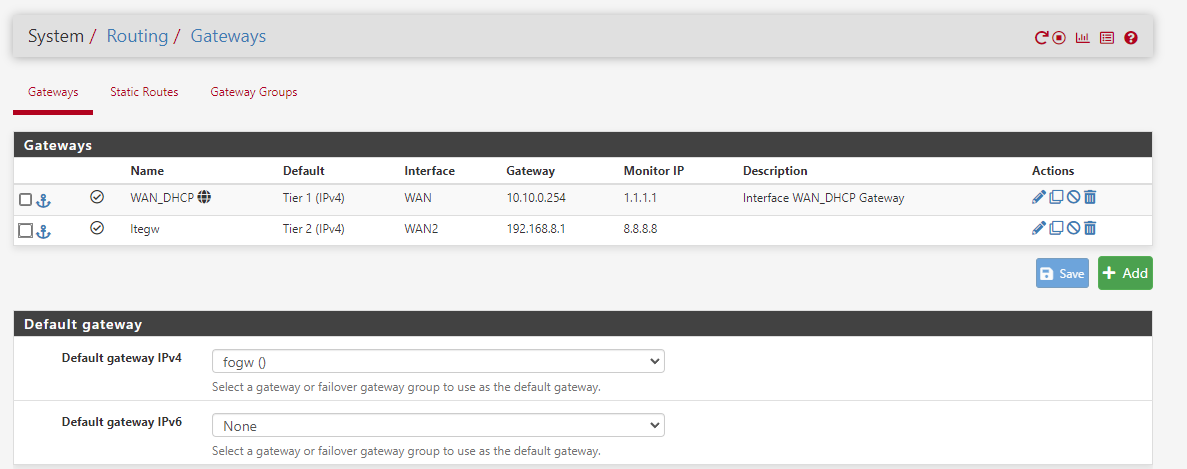
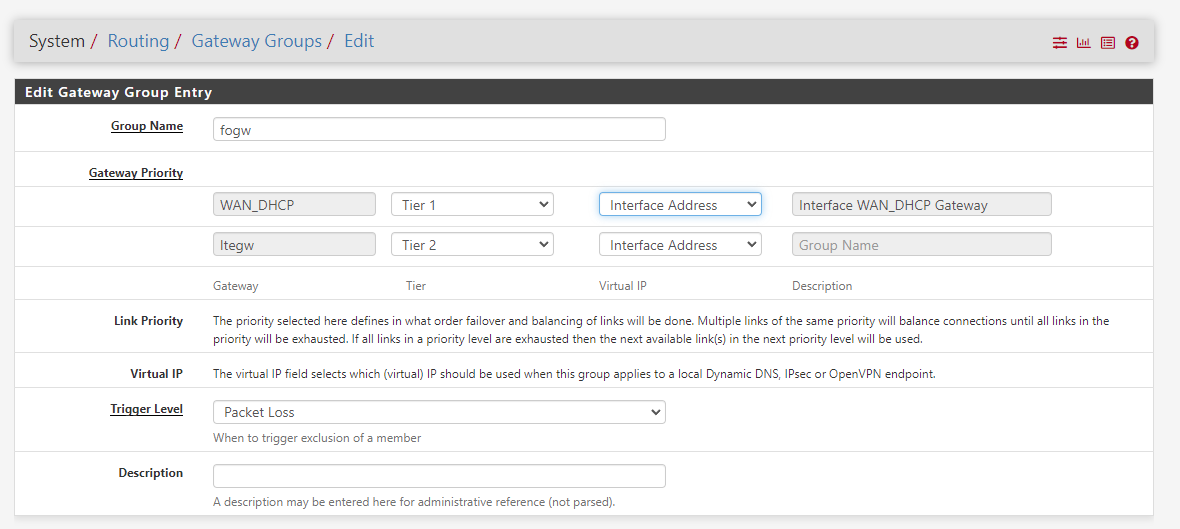
DNS - DNS Forwarding and Static Routes
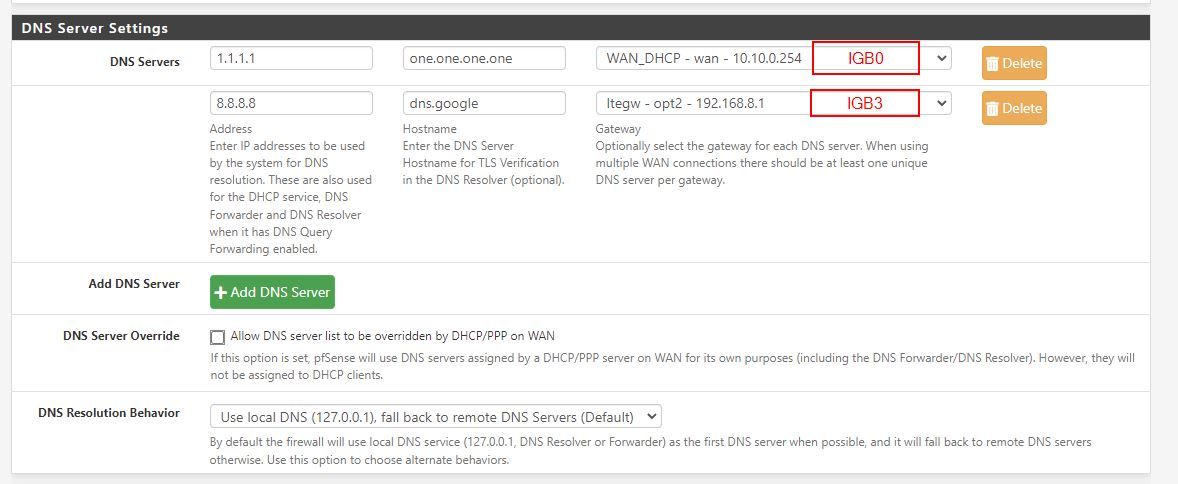
Routes
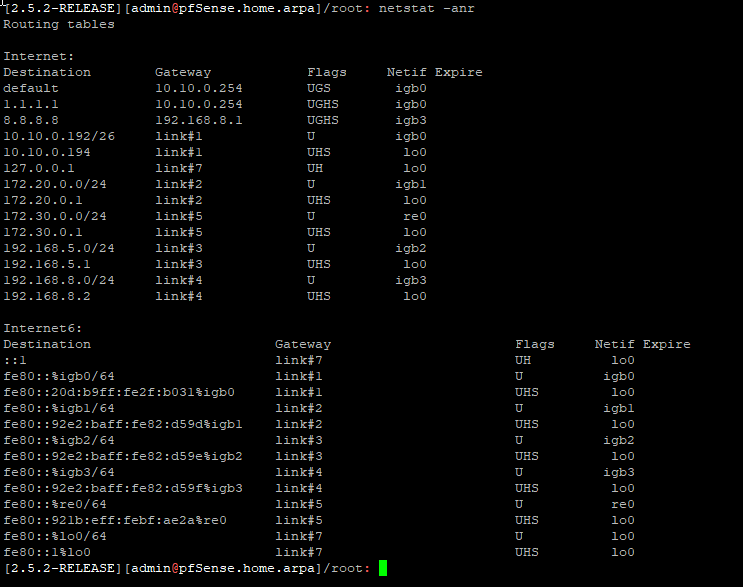
So how come i see traffic to DNS server 1 and 2 on all GW ?
Unbound is ignoring routing table ? - how it is possible ?Main GW - IGB0
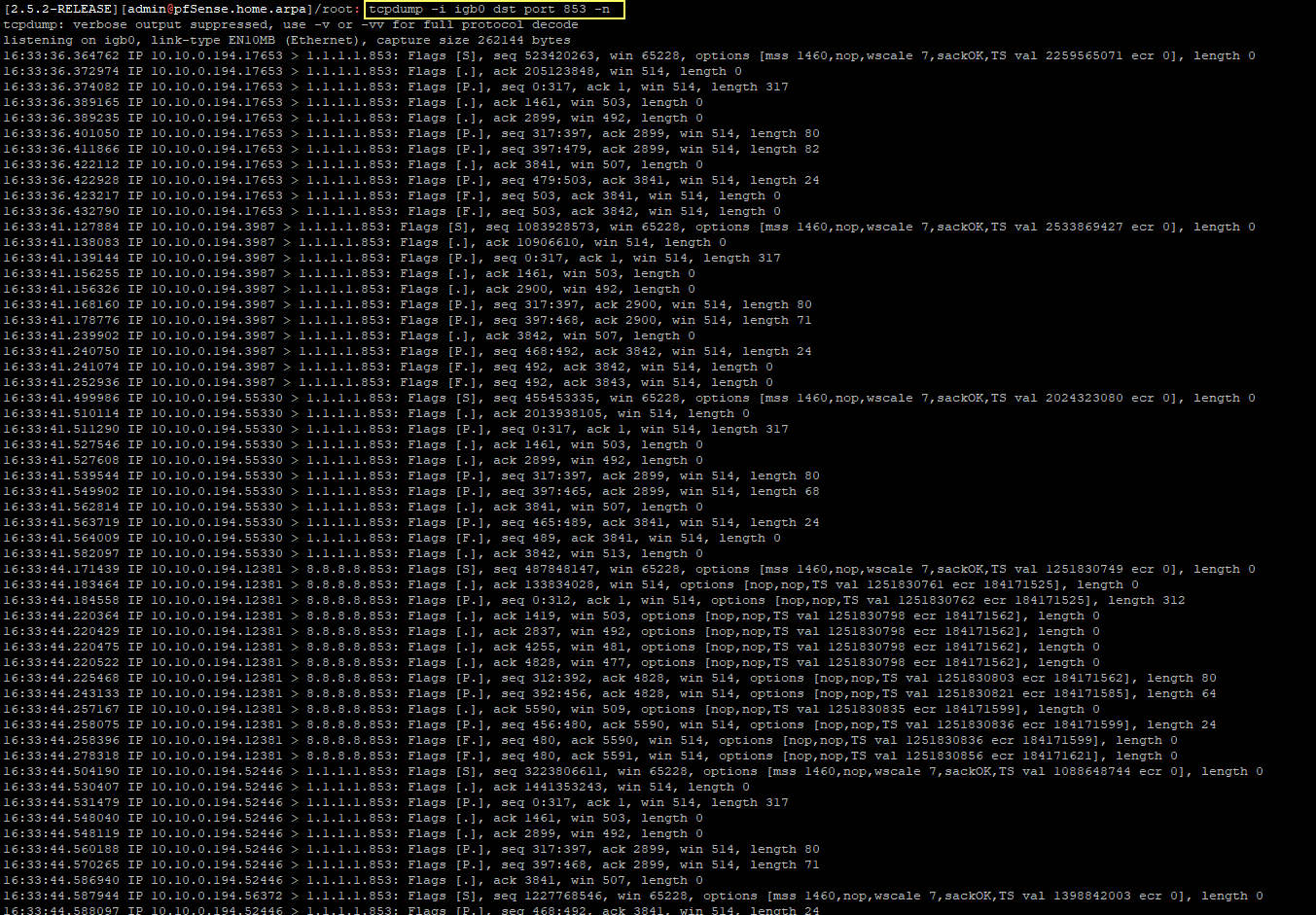
Backup GW - IGB3
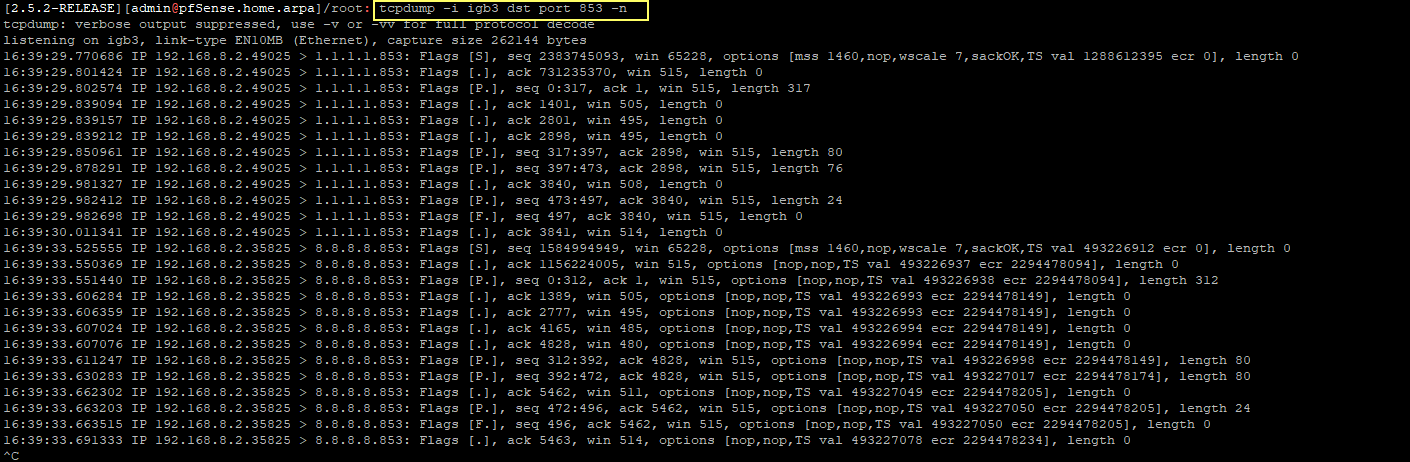
-
@pfsense_user_123
The stated DNS gateways are only used by unbound if it is running in forwarder mode. Is it? -
@viragomann
Sorry for that, the description requires clarification.Answering your question:
This is traffic generated by PC client for which pfsense is the default gateway, and DNS configuration on that PC leads to pfsense box LAN interface, where Resolver(unbound) acts as Forwarder,
It is not a pfsense resolver bypass traffic (for ex PC client with static DNS set to 1.1.1.1 - NO)
This traffic comes from pfsense (gateway box)
I've checked on 2.6.0-RC (amd64)
built on Mon Jan 24 18:44:12 UTC 2022
It acts exactly same, looks like "by designed" -
@pfsense_user_123
This behavior is incomprehensible for me, because in the case of an ISP that allows DNS traffic only within its network to its servers, such behavior completely disqualifies the use of different DNS servers for different ISPs - since all inquiries are sent to all of them, consequently some of them will be randomly not handled (blocked) by that ISP.
Unbelievable that no one paid attention before, which may mean that my config is not entirely correct after all. -
@pfsense_user_123
Normally pfSense use only the stated gateways in the general settings for accessing the DNS servers. But I don't know if this is also true for the DNS Resolver in forwarder mode.
But maybe you can workaround this by adding a static route for each DNS server. -
@viragomann
Static route is already in place.
DNS server setting webgui part is responsible for injecting static route. (3rd screen)
The "problem" is in Unbound behaviour, which is controlled via "interface section" in Unboud (Resolver) settings. In default Unbound will use any available interface, regardless routing table.
Changing to localhost does the job.cat /var/unbound/unbound.conf
Outgoing interfaces to be used
outgoing-interface: 127.0.0.1
outgoing-interface: ::1 -
Changing to localhost interface in unbound kills all connections despite using unbound itself as DNS only forwarding to root dns.
-
@cool_corona
You are right it looks like some built-in "kill state" procedure somewhere in background.
Check on UAT before playing in production.Therefore it is my private system i don't care... but flushing states in our company in prime time... it wouldn't be funny.
-
@pfsense_user_123 Yeah but I cannot establish new connections at all until changed back to all interfaces again...
Still playing in a sandbox so it doesnt matter.
-
What I wrote above is a wrong statement,
This is not true => You are right it looks like some built-in "kill state" procedure somewhere in background.
No proof = not true.
I can not indicate in the code where the flush would be executed.
Coincidence with something else... but still not a PRD so don't care.