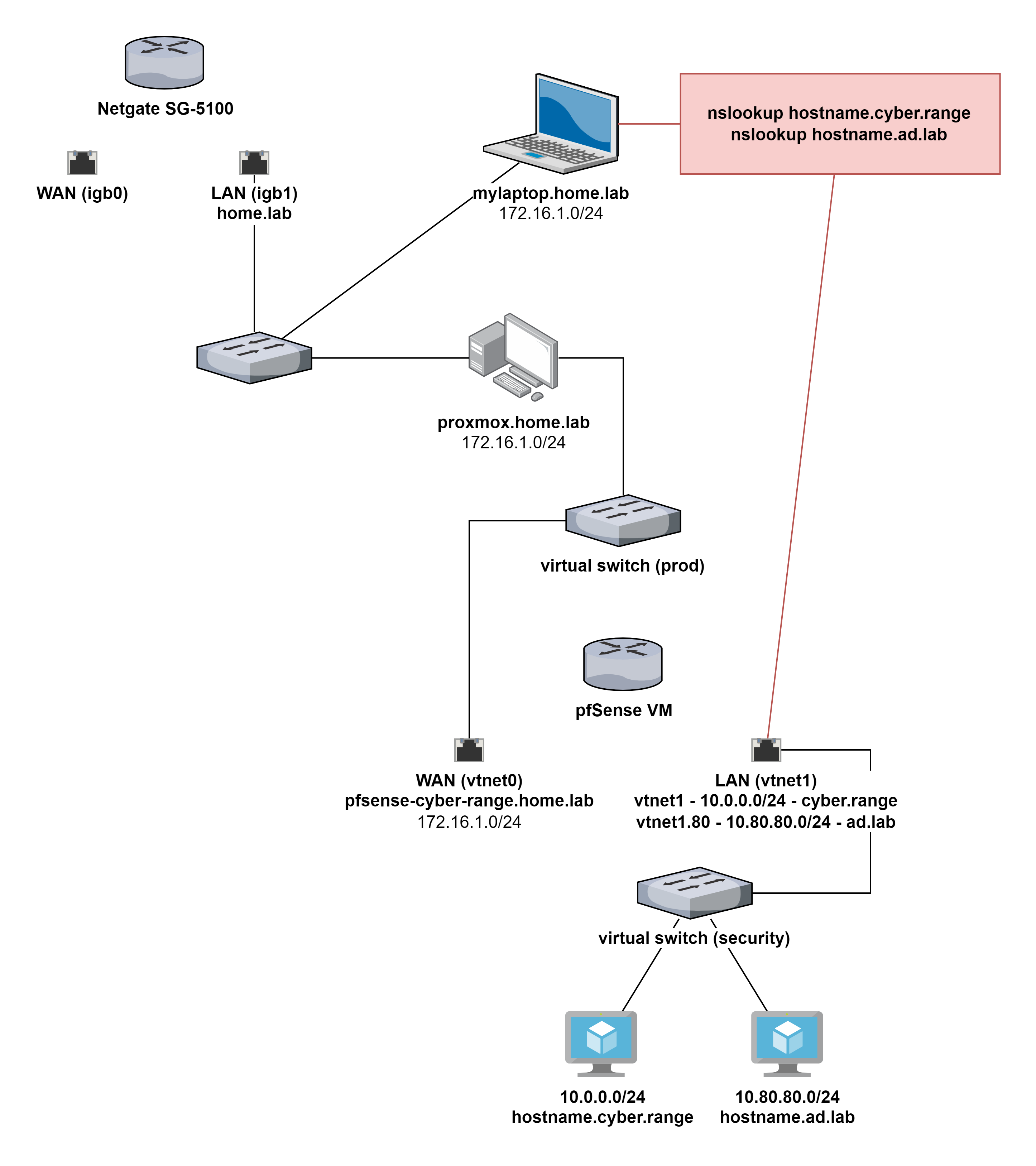
Local DNS Zone Resolution Between Two pfSense Hosts
-

I have spent far longer Googling and researching forums on this issue than I'd like to admit. In my head, I understand the mechanics of what I would like to do. I have tried to remove as much extraneous information from the diagram as possible.
A brief rundown of my setup:
- Netgate SG-5100
- Serves physical home network and is DNS resolver
- Register DHCP leases and reservations in DNS resolver
- Local domain is
home.lab
- pfSense VM in Proxmox
- Firewall and NAT for vulnerable infrastructure and security testing
- Local domain:
cyber.range - VLAN 80: DHCP set local domain as
ad.lab - Register DHCP leases and reservations in DNS resolver
I'd like to be able to resolve addresses from
mylaptop.home.labto any host incyber.rangeorad.lab. I understand the resolver forcyber.rangeis10.0.0.1and the resolver forad.labis10.80.80.1.I can route to both
10.0.0.0/24and10.80.80.0/24and have allowed DNS and ICMP (for connectivity testing) to both interfaces in the firewall. I've added forward lookup zones in the SG-5100 and added ACLs for172.16.1.0/24in the pfSense VM.If I run
nslookup hostname.ad.lab, I getNXDOMAINand looking at packet captures, I don't even see the packets coming from the host. If I runnslookup hostname.ad.lab 10.80.80.1, I get a server failure, but I do see the packets reaching the other side. I've tried a few different things like adding aprivate-domain,domain-insecure, andlocal-zonedirective to the configuration in the GUI. I've tried adjusting the DNSSEC settings, but I am just struggling to get this to work.Thank you for your time and my apologies in advance if I've duplicated another question.
- Netgate SG-5100
-
@0xben said in Local DNS Zone Resolution Between Two pfSense Hosts:
I understand the resolver for cyber.range is 10.0.0.1 and the resolver for ad.lab is 10.80.80.1.
Huh?? You don't list these what are they running for dns? Where is your laptop pointing for dns? Unbound on pfsense? Did you setup domain overrides so it knows where to resolve these domains from?
I don't even see where your routing anything? How is your laptop even suppose to get to these 2 networks from its 172.16.1/24
-
@johnpoz Thank you for taking the time to reply. I have configured static routes on the SG-5100 (172.16.1.0/24). Route to 10.0.0.0/24 via 172.16.1.2 and route to 10.80.80.0/24 via 172.16.1.2. I should have specified the WAN IP on the pfSense VM is 172.16.1.2
10.0.0.1 is the default gateway for the native VLAN under the pfSense VM. 10.80.80.1 is the default gateway for the
ad.labVLAN under the pfSense VM.In my head, I am thinking, a host on
10.80.80.0/24would send DNS lookups 10.80.80.1/24 to resolve anything under thead.lablocal domain. Since, the pfSense VM is providing DNS resolution for DHCP leases and reservations, my first instinct was to route DNS requests forad.labfrom172.16.1.0/24to10.80.80.1, since that is the gateway for that VLAN.Not sure if this is the right way to think about it, but that's what I'm hoping to learn here.
-
@johnpoz Also, sorry. I missed some details on the last reply. On both pfSense instances, I am using the Unbound DNS resolver service.
I did indeed try domain overrides, trying multiple configurations to no avail.
-
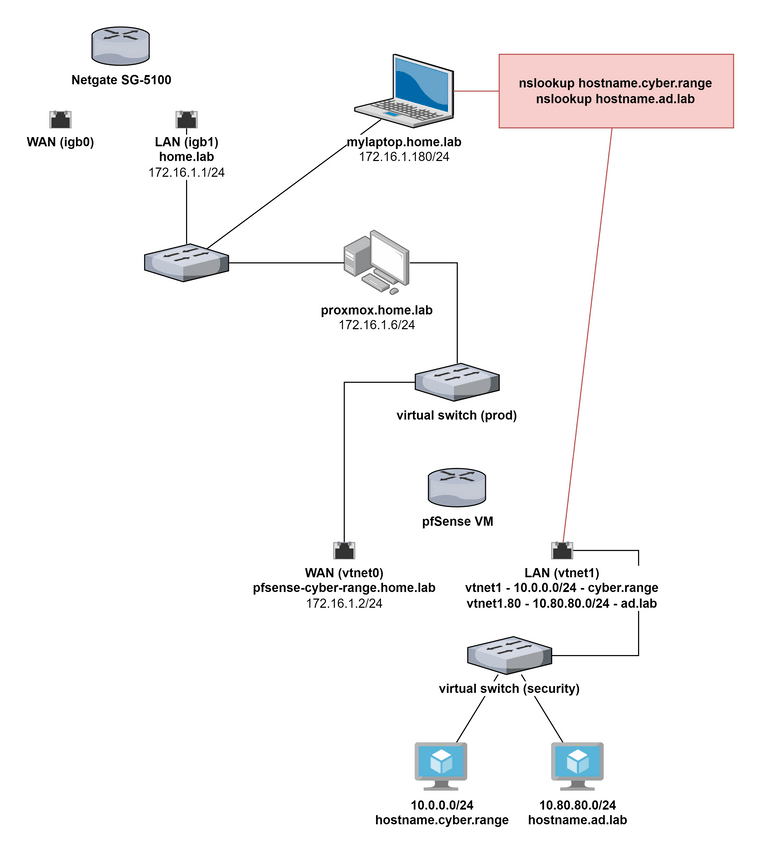
Here's a more accurate map of the network
-
@0xben said in Local DNS Zone Resolution Between Two pfSense Hosts:
trying multiple configurations to no avail.
I don't know if I'm lost here but I think what you need is simple
send your dns requests to your first dns server, in this configure so that when you cannot resolve your request, forward it to the second dns server, and in this configure exactly the same but now forwarding to a secure public dns.
I explain?
-
@silence I totally get what you're saying and I fully recognize that I am most likely the problem here. I understand that you're saying to put the DNS servers in a hierarchy so that it'll fail over to the next one in the list if a resolution fails.
I tried so many things to get that to work and I believe that was one thing I tried, but I'm certainly willing to try it again. Thanks for your input here.
-
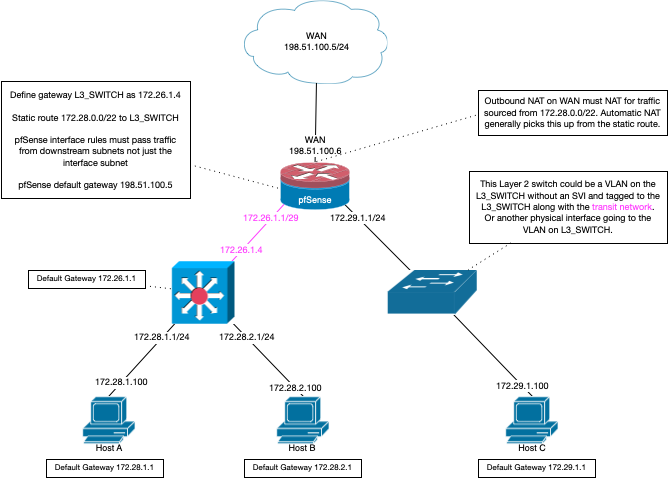
@0xben still where is there routing? What you show there is a downstream router doing nat??
If you want to route, you have a host in your transit network 172.16.1/24 which is going to be asymmetrical..
And your also doing this via proxmox? So what sort of network connection to the physical.. Bridge, nat? What rules did you put on the pfsense VM to allow traffic from its wan..
@0xben said in Local DNS Zone Resolution Between Two pfSense Hosts:
so that it'll fail over to the next one in the list if a resolution fails.
No that has nothing to do with anything.
Where does the laptop point for dns - that should be its pfsense, and then that pfsense should have domain overrides to know where to go find your downstream domains, from that pfsense doing dns for them. And it should just point to the 2nd pfsense wan IP.. etc..
You must of turned off natting if you want to actually resolve devices in the downstream networks IPs.. But you have not gave any details of that setup.. And again your laptop is in the transit if that is the case. To setup a downstream router, you would need a transit network and routing configured.. Along with firewall rules to allow the traffic, etc..
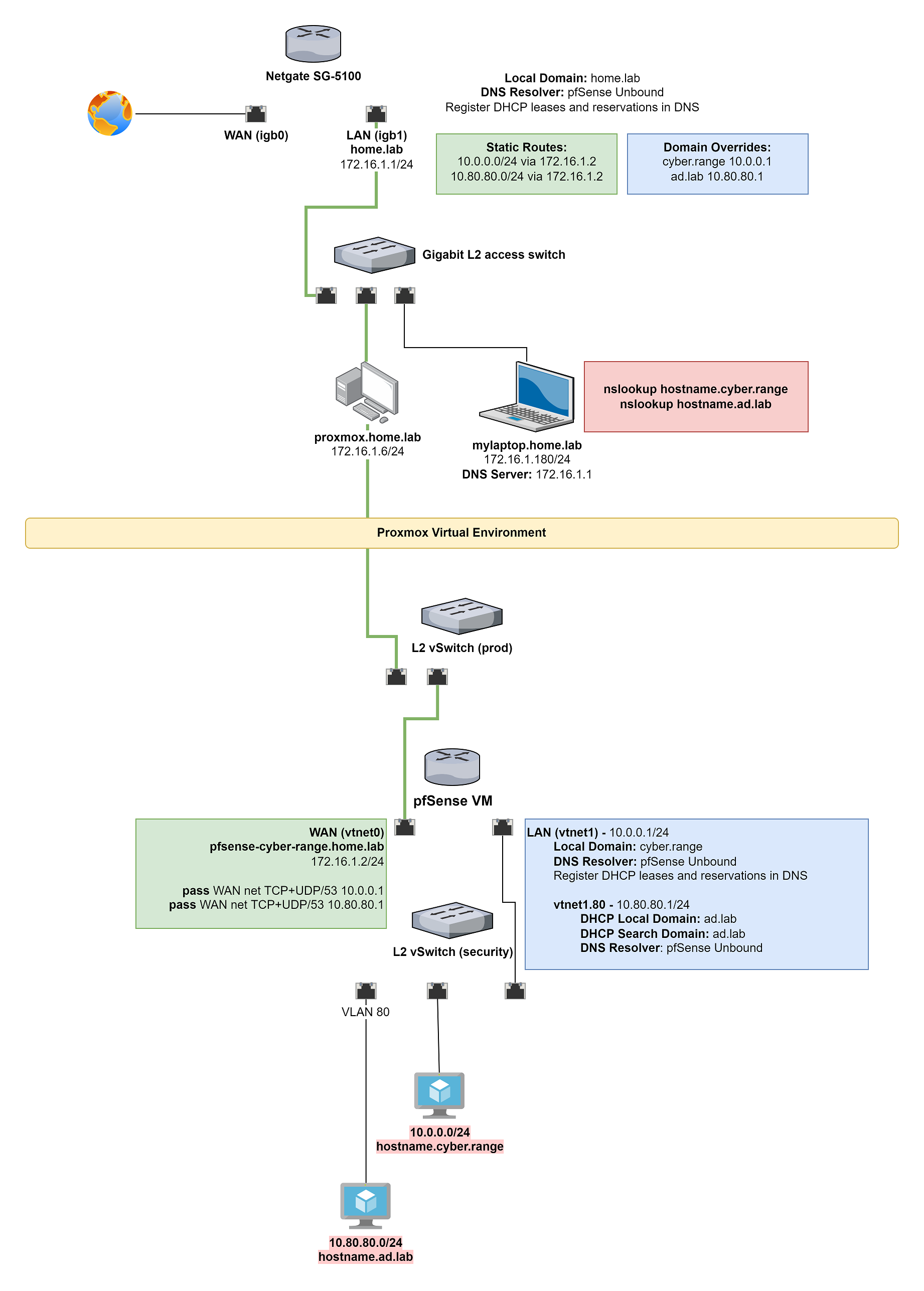
-
@johnpoz Firstly, thank you for your time and diagram. I don't want it to seem like you have to wrangle details out of me. I am trying my best to straddle the line between too much information, such that the details are lost in the mix. I appreciate your patience and you working with me here.
I sincerely hope this iteration of the diagram would improve your understanding of my setup.
- On both sides where pfSense is deployed, pfSense is both the DHCP server and the DNS resolver (Unbound)
- I already had the static routes in place
- Routing is good, connectivity good
- I can reach the ports on the specified IPs
- I tried my absolute best to work with the domain overrides, but couldn't get it working
If you refer to my latest iteration of the diagram, it should clearly indicate:
- The DNS resolver setup
- The DNS server on the client
- Static routes into the upstream NAT network
- Firewall rules to allow TCP+UDP/53 into the NAT networks
- The domain overrides I attempted on the downstream router
-
@0xben again is your pfsense doing nat? If your doing nat you would have to allow upstream unbound on dns to ask your downstream dns for those records via a domain override.
But what would be the point if your natting? Since your laptop would never be able to access an IP in 10.0.0 or 10.80.80
The only way you would be able to access resources behind your pfsense VM if your natting is port forwards.
If you want your laptop to resolve some cyber.range fqdn and get the IP of the device behind your downstream pfsense then you would need to setup routing. But if your going to route you should not use this 172.16.1 network as the transit or your going to run into asymmetrical issues.
Oh I see you do have some routes setup.. Did you turn off natting in pfsense vm? Again routing with 172.16.1 is bad idea, you need a transit network (no hosts).. See the drawing I posted on how to do downstream router.
Pretty pointless to try and use 80.1 and 0.1 ad dns overide.. Since they are the same thing (unbound) unless your running say unbound and bind for these 2 different domains.. For your domain override in the upstream you just need to point to say the wan IP of pfs VM, and allow unbound to answer queries on this.
BTW currently register dhcp is bad idea - this is going to restart unbound every time a lease is renewed..
-
@johnpoz The laptop can reach those NAT networks via static (asymmetric) routing. I understand this is bad practice and I should just port forward or have a transit network (as you've mentioned), but since this is just a lab environment, I've enabled this setting on the upstream router (172.16.1.1)
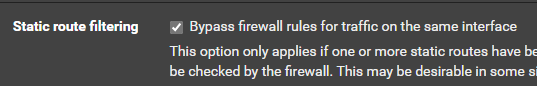
Pretty pointless to try and use 80.1 and 0.1 ad dns overide.. Since they are the same thing (unbound)
I didn't think to hit the WAN IP of the downstream router -- as I thought it would be interface-specific, especially with the alternate local domain on
80.1, but what you're saying makes sense. I understand that I would just need to ensure Unbound is listening on the WAN IP, as to my knowledge it only listens on 127.0.0.1 by default.BTW currently register dhcp is bad idea - this is going to restart unbound every time a lease is renewed.
Alas, I am painfully aware of this, but have decided to live with it, since it's my home network and the network isn't that big. It is my understanding that a fix is in the pipeline for the next major release.
I am going to take some time to review your input here and make sure I've got a good understanding. Thank you again for all your contributions here on the forum.
-
@0xben Your setup is quite easy to setup.. But you really should have a transit network between your routers, and not have any hosts on this network..
Unbound while it can return an IP for any fqdn.. Not really meant as an authoritative ns that might listen on different IPs and only serve up specific IPs.
Unbound listening on any interface will serve up any host overrides you have created for whatever.domain.tld, etc. that it knows about.
Your dhcp registrations isn't going to be able to create records for domainX and domainY.. It will register your dhcp entries under the general domain you setup on pfsense.