IKEv2 IPSEC VPN - Randomly stopped working
-
This post is deleted! -
@mamawe Alright, here is the log after the failed rekey (newest at top)
EDIT: I SEE ITS SAYING NO_PROPOSAL_CHOSEN.....LET ME CHANGE MY WINDOWS BACK TO PFS ECP384 and report back.
Feb 9 11:20:25 charon 7913 16[CFG] vici client 93 disconnected
Feb 9 11:20:25 charon 7913 02[CFG] vici client 93 requests: list-sas
Feb 9 11:20:25 charon 7913 16[CFG] vici client 93 registered for: list-sa
Feb 9 11:20:25 charon 7913 02[CFG] vici client 93 connected
Feb 9 11:20:19 charon 7913 13[CFG] vici client 92 disconnected
Feb 9 11:20:19 charon 7913 12[CFG] vici client 92 requests: list-sas
Feb 9 11:20:19 charon 7913 13[CFG] vici client 92 registered for: list-sa
Feb 9 11:20:19 charon 7913 05[CFG] vici client 92 connected
Feb 9 11:20:14 charon 7913 02[CFG] vici client 91 disconnected
Feb 9 11:20:14 charon 7913 16[CFG] vici client 91 requests: list-sas
Feb 9 11:20:14 charon 7913 02[CFG] vici client 91 registered for: list-sa
Feb 9 11:20:14 charon 7913 14[CFG] vici client 91 connected
Feb 9 11:20:08 charon 7913 13[CFG] vici client 90 disconnected
Feb 9 11:20:08 charon 7913 05[CFG] vici client 90 requests: list-sas
Feb 9 11:20:08 charon 7913 05[CFG] vici client 90 registered for: list-sa
Feb 9 11:20:08 charon 7913 10[CFG] vici client 90 connected
Feb 9 11:20:04 charon 7913 13[MGR] IKE_SA checkout not successful
Feb 9 11:20:04 charon 7913 13[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:20:03 charon 7913 14[CFG] vici client 89 disconnected
Feb 9 11:20:03 charon 7913 02[CFG] vici client 89 requests: list-sas
Feb 9 11:20:03 charon 7913 02[CFG] vici client 89 registered for: list-sa
Feb 9 11:20:03 charon 7913 14[CFG] vici client 89 connected
Feb 9 11:20:00 charon 7913 09[MGR] IKE_SA checkout not successful
Feb 9 11:20:00 charon 7913 09[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:20:00 charon 7913 16[MGR] checkin and destroy of IKE_SA successful
Feb 9 11:20:00 charon 7913 16[CFG] <con-mobile|7> lease 192.168.4.1 by 'Prime3@pfsense.local.lan' went offline
Feb 9 11:20:00 charon 7913 16[IKE] <con-mobile|7> IKE_SA con-mobile[7] state change: DELETING => DESTROYING
Feb 9 11:20:00 charon 7913 16[MGR] <con-mobile|7> checkin and destroy IKE_SA con-mobile[7]
Feb 9 11:20:00 charon 7913 16[IKE] <con-mobile|7> IKE_SA deleted
Feb 9 11:20:00 charon 7913 16[ENC] <con-mobile|7> parsed INFORMATIONAL response 4 [ ]
Feb 9 11:20:00 charon 7913 16[NET] <con-mobile|7> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (80 bytes)
Feb 9 11:20:00 charon 7913 16[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:20:00 charon 7913 16[MGR] checkout IKEv2 SA by message with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:20:00 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:20:00 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:20:00 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:20:00 charon 7913 16[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:20:00 charon 7913 16[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:20:00 charon 7913 16[NET] <con-mobile|7> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (80 bytes)
Feb 9 11:20:00 charon 7913 16[ENC] <con-mobile|7> generating INFORMATIONAL request 4 [ D ]
Feb 9 11:20:00 charon 7913 16[IKE] <con-mobile|7> sending DELETE for IKE_SA con-mobile[7]
Feb 9 11:20:00 charon 7913 16[IKE] <con-mobile|7> IKE_SA con-mobile[7] state change: ESTABLISHED => DELETING
Feb 9 11:20:00 charon 7913 16[IKE] <con-mobile|7> deleting IKE_SA con-mobile[7] between $HOME_ip[$HOME_ip]...$WORK_ip[192.168.77.169]
Feb 9 11:20:00 charon 7913 16[IKE] <con-mobile|7> activating IKE_DELETE task
Feb 9 11:20:00 charon 7913 16[IKE] <con-mobile|7> activating new tasks
Feb 9 11:20:00 charon 7913 16[IKE] <con-mobile|7> queueing IKE_DELETE task
Feb 9 11:20:00 charon 7913 16[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:20:00 charon 7913 16[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:58 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:58 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:57 charon 7913 10[CFG] vici client 88 disconnected
Feb 9 11:19:57 charon 7913 05[CFG] vici client 88 requests: list-sas
Feb 9 11:19:57 charon 7913 10[CFG] vici client 88 registered for: list-sa
Feb 9 11:19:57 charon 7913 13[CFG] vici client 88 connected
Feb 9 11:19:55 charon 7913 05[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:55 charon 7913 05[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:55 charon 7913 05[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:55 charon 7913 05[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:54 charon 7913 05[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:54 charon 7913 05[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:54 charon 7913 05[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:54 charon 7913 05[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:52 charon 7913 05[MGR] IKE_SA checkout not successful
Feb 9 11:19:52 charon 7913 05[MGR] checkout IKEv2 SA with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:51 charon 7913 14[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:51 charon 7913 14[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> nothing to initiate
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> activating new tasks
Feb 9 11:19:51 charon 7913 14[CHD] <con-mobile|7> CHILD_SA con-mobile{4} state change: CREATED => DESTROYING
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> failed to establish CHILD_SA, keeping IKE_SA
Feb 9 11:19:51 charon 7913 14[CFG] <con-mobile|7> configured proposals: ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ, ESP:AES_GCM_16_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_512_256/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_256_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_512_256/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_512_256/ECP_384/NO_EXT_SEQ
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> received NO_PROPOSAL_CHOSEN notify, no CHILD_SA built
Feb 9 11:19:51 charon 7913 14[ENC] <con-mobile|7> parsed CREATE_CHILD_SA response 3 [ N(NO_PROP) ]
Feb 9 11:19:51 charon 7913 14[NET] <con-mobile|7> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (80 bytes)
Feb 9 11:19:51 charon 7913 14[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:51 charon 7913 14[MGR] checkout IKEv2 SA by message with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:51 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:51 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:51 charon 7913 14[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:51 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:19:51 charon 7913 14[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:51 charon 7913 14[NET] <con-mobile|7> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (80 bytes)
Feb 9 11:19:51 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:19:51 charon 7913 14[ENC] <con-mobile|7> generating INFORMATIONAL response 0 [ D ]
Feb 9 11:19:51 charon 7913 14[NET] <con-mobile|7> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (928 bytes)
Feb 9 11:19:51 charon 7913 14[ENC] <con-mobile|7> generating CREATE_CHILD_SA request 3 [ N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> establishing CHILD_SA con-mobile{4} reqid 1
Feb 9 11:19:51 charon 7913 14[CFG] <con-mobile|7> configured proposals: ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ, ESP:AES_GCM_16_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_512_256/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_256_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_512_256/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_512_256/ECP_384/NO_EXT_SEQ
Feb 9 11:19:51 charon 7913 14[CFG] <con-mobile|7> 192.168.4.1/32|/0
Feb 9 11:19:51 charon 7913 14[CFG] <con-mobile|7> proposing traffic selectors for other:
Feb 9 11:19:51 charon 7913 14[CFG] <con-mobile|7> 192.168.0.0/27|/0
Feb 9 11:19:51 charon 7913 14[CFG] <con-mobile|7> proposing traffic selectors for us:
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> activating CHILD_CREATE task
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> activating new tasks
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> queueing CHILD_CREATE task
Feb 9 11:19:51 charon 7913 14[CHD] <con-mobile|7> CHILD_SA con-mobile{3} state change: DELETED => DESTROYING
Feb 9 11:19:51 charon 7913 14[CHD] <con-mobile|7> CHILD_SA con-mobile{3} state change: DELETING => DELETED
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> CHILD_SA closed
Feb 9 11:19:51 charon 7913 14[CHD] <con-mobile|7> CHILD_SA con-mobile{3} state change: INSTALLED => DELETING
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> sending DELETE for ESP CHILD_SA with SPI c87cf382
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> closing CHILD_SA con-mobile{3} with SPIs c87cf382_i (0 bytes) c81f0dc6_o (0 bytes) and TS 192.168.0.0/27|/0 === 192.168.4.1/32|/0
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> received DELETE for ESP CHILD_SA with SPI c81f0dc6
Feb 9 11:19:51 charon 7913 14[ENC] <con-mobile|7> parsed INFORMATIONAL request 0 [ D ]
Feb 9 11:19:51 charon 7913 14[NET] <con-mobile|7> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (80 bytes)
Feb 9 11:19:51 charon 7913 14[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:51 charon 7913 14[MGR] checkout IKEv2 SA by message with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:51 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:51 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:51 charon 7913 14[CFG] vici client 87 disconnected
Feb 9 11:19:51 charon 7913 09[CFG] vici client 87 requests: list-sas
Feb 9 11:19:51 charon 7913 14[CFG] vici client 87 registered for: list-sa
Feb 9 11:19:51 charon 7913 16[CFG] vici client 87 connected
Feb 9 11:19:50 charon 7913 16[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:50 charon 7913 16[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:50 charon 7913 16[IKE] <con-mobile|7> nothing to initiate
Feb 9 11:19:50 charon 7913 16[IKE] <con-mobile|7> activating new tasks
Feb 9 11:19:50 charon 7913 16[ENC] <con-mobile|7> parsed INFORMATIONAL response 2 [ ]
Feb 9 11:19:50 charon 7913 16[NET] <con-mobile|7> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (80 bytes)
Feb 9 11:19:50 charon 7913 16[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:50 charon 7913 16[MGR] checkout IKEv2 SA by message with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:50 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:50 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:50 charon 7913 16[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:50 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:19:50 charon 7913 16[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:50 charon 7913 16[NET] <con-mobile|7> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (80 bytes)
Feb 9 11:19:50 charon 7913 16[ENC] <con-mobile|7> generating INFORMATIONAL request 2 [ ]
Feb 9 11:19:50 charon 7913 16[IKE] <con-mobile|7> activating IKE_DPD task
Feb 9 11:19:50 charon 7913 16[IKE] <con-mobile|7> activating new tasks
Feb 9 11:19:50 charon 7913 16[IKE] <con-mobile|7> queueing IKE_DPD task
Feb 9 11:19:50 charon 7913 16[IKE] <con-mobile|7> sending DPD request
Feb 9 11:19:50 charon 7913 16[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:50 charon 7913 16[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:46 charon 7913 13[CFG] vici client 86 disconnected
Feb 9 11:19:46 charon 7913 05[CFG] vici client 86 requests: list-sas
Feb 9 11:19:46 charon 7913 05[CFG] vici client 86 registered for: list-sa
Feb 9 11:19:46 charon 7913 10[CFG] vici client 86 connected
Feb 9 11:19:44 charon 7913 13[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:44 charon 7913 13[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:44 charon 7913 13[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:44 charon 7913 13[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:40 charon 7913 09[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:40 charon 7913 09[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:40 charon 7913 09[IKE] <con-mobile|7> nothing to initiate
Feb 9 11:19:40 charon 7913 09[IKE] <con-mobile|7> activating new tasks
Feb 9 11:19:40 charon 7913 09[ENC] <con-mobile|7> parsed INFORMATIONAL response 1 [ ]
Feb 9 11:19:40 charon 7913 09[NET] <con-mobile|7> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (80 bytes)
Feb 9 11:19:40 charon 7913 09[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:40 charon 7913 09[MGR] checkout IKEv2 SA by message with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:40 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:40 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:40 charon 7913 09[CFG] vici client 85 disconnected
Feb 9 11:19:40 charon 7913 14[CFG] vici client 85 requests: list-sas
Feb 9 11:19:40 charon 7913 09[CFG] vici client 85 registered for: list-sa
Feb 9 11:19:40 charon 7913 14[CFG] vici client 85 connected
Feb 9 11:19:40 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:19:40 charon 7913 16[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:40 charon 7913 16[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:40 charon 7913 16[NET] <con-mobile|7> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (80 bytes)
Feb 9 11:19:40 charon 7913 16[ENC] <con-mobile|7> generating INFORMATIONAL request 1 [ ]
Feb 9 11:19:40 charon 7913 16[IKE] <con-mobile|7> activating IKE_DPD task
Feb 9 11:19:40 charon 7913 16[IKE] <con-mobile|7> activating new tasks
Feb 9 11:19:40 charon 7913 16[IKE] <con-mobile|7> queueing IKE_DPD task
Feb 9 11:19:40 charon 7913 16[IKE] <con-mobile|7> sending DPD request
Feb 9 11:19:40 charon 7913 16[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:40 charon 7913 16[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:39 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:39 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:34 charon 7913 10[CFG] vici client 84 disconnected
Feb 9 11:19:34 charon 7913 05[CFG] vici client 84 requests: list-sas
Feb 9 11:19:34 charon 7913 10[CFG] vici client 84 registered for: list-sa
Feb 9 11:19:34 charon 7913 13[CFG] vici client 84 connected
Feb 9 11:19:34 charon 7913 05[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:34 charon 7913 05[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:34 charon 7913 05[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:34 charon 7913 05[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:30 charon 7913 05[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:30 charon 7913 05[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:30 charon 7913 05[IKE] <con-mobile|7> nothing to initiate
Feb 9 11:19:30 charon 7913 05[IKE] <con-mobile|7> activating new tasks
Feb 9 11:19:30 charon 7913 05[ENC] <con-mobile|7> parsed INFORMATIONAL response 0 [ ]
Feb 9 11:19:30 charon 7913 05[NET] <con-mobile|7> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (80 bytes)
Feb 9 11:19:30 charon 7913 05[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:30 charon 7913 05[MGR] checkout IKEv2 SA by message with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:30 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:30 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:30 charon 7913 05[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:30 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:19:30 charon 7913 05[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:30 charon 7913 05[NET] <con-mobile|7> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (80 bytes)
Feb 9 11:19:30 charon 7913 05[ENC] <con-mobile|7> generating INFORMATIONAL request 0 [ ]
Feb 9 11:19:30 charon 7913 05[IKE] <con-mobile|7> activating IKE_DPD task
Feb 9 11:19:30 charon 7913 05[IKE] <con-mobile|7> activating new tasks
Feb 9 11:19:30 charon 7913 05[IKE] <con-mobile|7> queueing IKE_DPD task
Feb 9 11:19:30 charon 7913 05[IKE] <con-mobile|7> sending DPD request
Feb 9 11:19:30 charon 7913 05[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:30 charon 7913 05[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:28 charon 7913 02[CFG] vici client 83 disconnected
Feb 9 11:19:28 charon 7913 14[CFG] vici client 83 requests: list-sas
Feb 9 11:19:28 charon 7913 02[CFG] vici client 83 registered for: list-sa
Feb 9 11:19:28 charon 7913 14[CFG] vici client 83 connected
Feb 9 11:19:28 charon 7913 09[MGR] <con-mobile|7> checkin of IKE_SA successful
Feb 9 11:19:28 charon 7913 09[MGR] <con-mobile|7> checkin IKE_SA con-mobile[7]
Feb 9 11:19:28 charon 7913 09[IKE] <con-mobile|7> IKE_SA con-mobile[7] will timeout in 32 seconds
Feb 9 11:19:28 charon 7913 09[IKE] <con-mobile|7> initiator did not reauthenticate as requested
Feb 9 11:19:28 charon 7913 09[MGR] IKE_SA con-mobile[7] successfully checked out
Feb 9 11:19:28 charon 7913 09[MGR] checkout IKEv2 SA with SPIs ea5c9b788d513ffa_i de554a7302525ca8_r
Feb 9 11:19:28 charon 7913 09[MGR] IKE_SA checkout not successful
Feb 9 11:19:28 charon 7913 09[MGR] checkout IKEv2 SA with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:24 charon 7913 09[MGR] IKE_SA checkout not successful
Feb 9 11:19:24 charon 7913 09[MGR] checkout IKEv2 SA with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:24 charon 7913 09[MGR] IKE_SA checkout not successful
Feb 9 11:19:24 charon 7913 09[MGR] checkout IKEv2 SA with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:22 charon 7913 13[CFG] vici client 82 disconnected
Feb 9 11:19:22 charon 7913 10[CFG] vici client 82 requests: list-sas
Feb 9 11:19:22 charon 7913 05[CFG] vici client 82 registered for: list-sa
Feb 9 11:19:22 charon 7913 13[CFG] vici client 82 connected
Feb 9 11:19:22 charon 7913 10[MGR] IKE_SA checkout not successful
Feb 9 11:19:22 charon 7913 10[MGR] checkout IKEv2 SA with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:20 charon 7913 10[MGR] checkin and destroy of IKE_SA successful
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: DELETING => DESTROYING
Feb 9 11:19:20 charon 7913 10[MGR] <con-mobile|6> checkin and destroy IKE_SA con-mobile[6]
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_SA deleted
Feb 9 11:19:20 charon 7913 10[ENC] <con-mobile|6> parsed INFORMATIONAL response 27 [ ]
Feb 9 11:19:20 charon 7913 10[NET] <con-mobile|6> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (80 bytes)
Feb 9 11:19:20 charon 7913 10[MGR] IKE_SA con-mobile[6] successfully checked out
Feb 9 11:19:20 charon 7913 10[MGR] checkout IKEv2 SA by message with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:20 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:20 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:20 charon 7913 10[MGR] <con-mobile|6> checkin of IKE_SA successful
Feb 9 11:19:20 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:19:20 charon 7913 10[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6]
Feb 9 11:19:20 charon 7913 10[NET] <con-mobile|6> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (80 bytes)
Feb 9 11:19:20 charon 7913 10[ENC] <con-mobile|6> generating INFORMATIONAL request 27 [ D ]
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> sending DELETE for IKE_SA con-mobile[6]
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: REKEYED => DELETING
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> deleting IKE_SA con-mobile[6] between $HOME_ip[$HOME_ip]...$WORK_ip[192.168.77.169]
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_REKEY task
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> reinitiating already active tasks
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: REKEYING => REKEYED
Feb 9 11:19:20 charon 7913 10[MGR] <con-mobile|6> checkin of IKE_SA successful
Feb 9 11:19:20 charon 7913 10[MGR] <con-mobile|6> checkin IKE_SA con-mobile[7]
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> rescheduling reauthentication in 8s after rekeying, lifetime reduced to 40s
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_SA con-mobile[7] rekeyed between $HOME_ip[$HOME_ip]...$WORK_ip[192.168.77.169]
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> maximum IKE_SA lifetime 296s
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> scheduling reauthentication in 277s
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> scheduling rekeying in 264s
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_SA con-mobile[7] state change: CONNECTING => ESTABLISHED
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_512/ECP_521, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> proposal matches
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> selecting proposal:
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> no acceptable ENCRYPTION_ALGORITHM found
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> selecting proposal:
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> no acceptable DIFFIE_HELLMAN_GROUP found
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> selecting proposal:
Feb 9 11:19:20 charon 7913 10[ENC] <con-mobile|6> parsed CREATE_CHILD_SA response 26 [ SA KE No ]
Feb 9 11:19:20 charon 7913 10[NET] <con-mobile|6> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (448 bytes)
Feb 9 11:19:20 charon 7913 10[MGR] IKE_SA con-mobile[6] successfully checked out
Feb 9 11:19:20 charon 7913 10[MGR] checkout IKEv2 SA by message with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:20 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:20 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:20 charon 7913 10[MGR] <con-mobile|6> checkin of IKE_SA successful
Feb 9 11:19:20 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:19:20 charon 7913 10[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6]
Feb 9 11:19:20 charon 7913 10[NET] <con-mobile|6> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (720 bytes)
Feb 9 11:19:20 charon 7913 10[ENC] <con-mobile|6> generating CREATE_CHILD_SA request 26 [ SA No KE ]
Feb 9 11:19:20 charon 7913 10[CFG] <con-mobile|6> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_512/ECP_521, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384
Feb 9 11:19:20 charon 7913 10[LIB] <con-mobile|6> size of DH secret exponent: 2047 bits
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_SA con-mobile[7] state change: CREATED => CONNECTING
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> initiating IKE_SA con-mobile[7] to $WORK_ip
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: ESTABLISHED => REKEYING
Feb 9 11:19:20 charon 7913 10[MGR] <con-mobile|6> created IKE_SA (unnamed)[7]
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> activating IKE_REKEY task
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> activating new tasks
Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> queueing IKE_REKEY task
Feb 9 11:19:20 charon 7913 10[MGR] IKE_SA con-mobile[6] successfully checked out
Feb 9 11:19:20 charon 7913 10[MGR] checkout IKEv2 SA with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:17 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:17 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:16 charon 7913 09[CFG] vici client 81 disconnected
Feb 9 11:19:16 charon 7913 09[CFG] vici client 81 requests: list-sas
Feb 9 11:19:16 charon 7913 14[CFG] vici client 81 registered for: list-sa
Feb 9 11:19:16 charon 7913 02[CFG] vici client 81 connected
Feb 9 11:19:16 charon 7913 09[MGR] <con-mobile|6> checkin of IKE_SA successful
Feb 9 11:19:16 charon 7913 09[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6]
Feb 9 11:19:16 charon 7913 09[MGR] IKE_SA con-mobile[6] successfully checked out
Feb 9 11:19:16 charon 7913 09[MGR] checkout IKEv2 SA with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:12 charon 7913 09[MGR] <con-mobile|6> checkin of IKE_SA successful
Feb 9 11:19:12 charon 7913 09[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6]
Feb 9 11:19:12 charon 7913 09[IKE] <con-mobile|6> nothing to initiate
Feb 9 11:19:12 charon 7913 09[IKE] <con-mobile|6> activating new tasks
Feb 9 11:19:12 charon 7913 09[ENC] <con-mobile|6> parsed INFORMATIONAL response 25 [ ]
Feb 9 11:19:12 charon 7913 09[NET] <con-mobile|6> received packet: from $WORK_ip[63247] to $HOME_ip[4500] (80 bytes)
Feb 9 11:19:12 charon 7913 09[MGR] IKE_SA con-mobile[6] successfully checked out
Feb 9 11:19:12 charon 7913 09[MGR] checkout IKEv2 SA by message with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r
Feb 9 11:19:12 charon 7913 08[NET] waiting for data on sockets
Feb 9 11:19:12 charon 7913 08[NET] received packet: from $WORK_ip[63247] to $HOME_ip[4500]
Feb 9 11:19:12 charon 7913 09[MGR] <con-mobile|6> checkin of IKE_SA successful
Feb 9 11:19:12 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[63247]
Feb 9 11:19:12 charon 7913 09[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6]
Feb 9 11:19:12 charon 7913 09[NET] <con-mobile|6> sending packet: from $HOME_ip[4500] to $WORK_ip[63247] (80 bytes)
Feb 9 11:19:12 charon 7913 09[ENC] <con-mobile|6> generating INFORMATIONAL request 25 [ ]
Feb 9 11:19:12 charon 7913 09[IKE] <con-mobile|6> activating IKE_DPD task
Feb 9 11:19:12 charon 7913 09[IKE] <con-mobile|6> activating new tasks
Feb 9 11:19:12 charon 7913 09[IKE] <con-mobile|6> queueing IKE_DPD task
Feb 9 11:19:12 charon 7913 09[IKE] <con-mobile|6> sending DPD request
Feb 9 11:19:12 charon 7913 09[MGR] IKE_SA con-mobile[6] successfully checked out
Feb 9 11:19:12 charon 7913 09[MGR] checkout IKEv2 SA with SPIs 25b0f0a1358f0192_i 20bbe3bda5d3c436_r -
@brswattt There are two lines that seem interesting to me:
Feb 9 11:19:28 charon 7913 09[IKE] <con-mobile|7> initiator did not reauthenticate as requested ... Feb 9 11:19:20 charon 7913 10[IKE] <con-mobile|6> rescheduling reauthentication in 8s after rekeying, lifetime reduced to 40sDo you really need reauthentication?
This is set in phase 1 configuration under "Expiration and Replacement".
-
@mamawe What is the benefit with and without? I'm not sure if I do need it exactly, I just want the client to connect after the lifetime expires, thats all.
So now I'm back to not being able to connect, I changed my Phase 1 / Phase 2 encryption to 1 set.
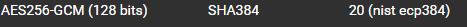
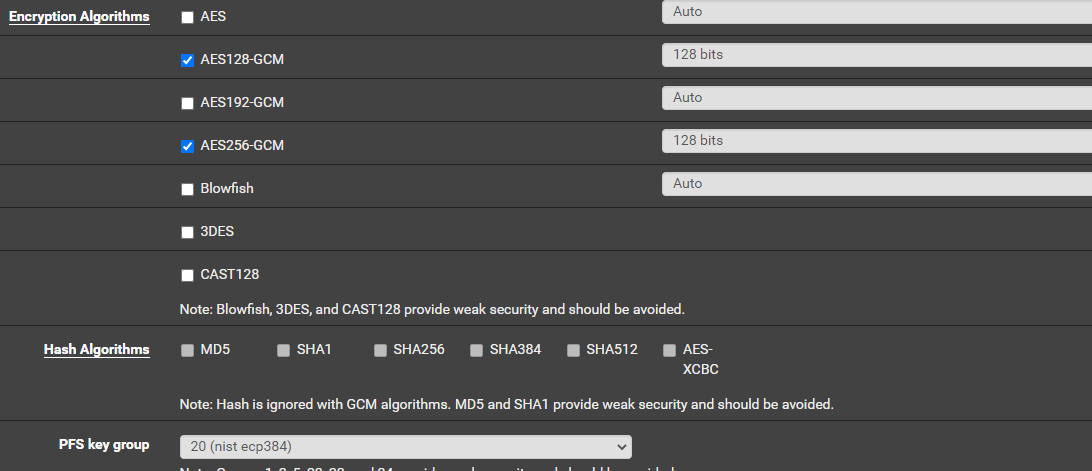
This is my windows IPSEC Config for the connection:
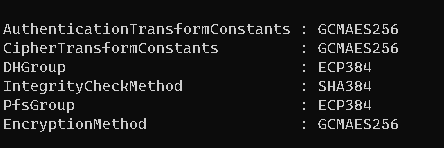
Feb 9 12:00:23 charon 7913 07[MGR] <con-mobile|25> checkin of IKE_SA successful Feb 9 12:00:23 charon 7913 07[MGR] <con-mobile|25> checkin IKE_SA con-mobile[25] Feb 9 12:00:23 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[4500] Feb 9 12:00:23 charon 7913 07[NET] <con-mobile|25> sending packet: from $HOME_ip[4500] to $WORK_ip[4500] (142 bytes) Feb 9 12:00:23 charon 7913 07[NET] <con-mobile|25> sending packet: from $HOME_ip[4500] to $WORK_ip[4500] (1248 bytes) Feb 9 12:00:23 charon 7913 07[IKE] <con-mobile|25> received retransmit of request with ID 1, retransmitting response Feb 9 12:00:23 charon 7913 07[ENC] <con-mobile|25> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Feb 9 12:00:23 charon 7913 07[ENC] <con-mobile|25> received fragment #2 of 3, reassembled fragmented IKE message (1462 bytes) Feb 9 12:00:23 charon 7913 07[ENC] <con-mobile|25> parsed IKE_AUTH request 1 [ EF(2/3) ] Feb 9 12:00:23 charon 7913 07[NET] <con-mobile|25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (572 bytes) Feb 9 12:00:23 charon 7913 07[MGR] IKE_SA con-mobile[25] successfully checked out Feb 9 12:00:23 charon 7913 09[MGR] <con-mobile|25> checkin of IKE_SA successful Feb 9 12:00:23 charon 7913 09[MGR] <con-mobile|25> checkin IKE_SA con-mobile[25] Feb 9 12:00:23 charon 7913 09[ENC] <con-mobile|25> received fragment #3 of 3, waiting for complete IKE message Feb 9 12:00:23 charon 7913 09[ENC] <con-mobile|25> parsed IKE_AUTH request 1 [ EF(3/3) ] Feb 9 12:00:23 charon 7913 09[NET] <con-mobile|25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (476 bytes) Feb 9 12:00:23 charon 7913 09[MGR] IKE_SA con-mobile[25] successfully checked out Feb 9 12:00:23 charon 7913 02[MGR] <con-mobile|25> checkin of IKE_SA successful Feb 9 12:00:23 charon 7913 02[MGR] <con-mobile|25> checkin IKE_SA con-mobile[25] Feb 9 12:00:23 charon 7913 02[ENC] <con-mobile|25> received fragment #1 of 3, waiting for complete IKE message Feb 9 12:00:23 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:23 charon 7913 09[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:23 charon 7913 02[ENC] <con-mobile|25> parsed IKE_AUTH request 1 [ EF(1/3) ] Feb 9 12:00:23 charon 7913 07[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:23 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:23 charon 7913 02[NET] <con-mobile|25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (572 bytes) Feb 9 12:00:23 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:23 charon 7913 02[MGR] IKE_SA con-mobile[25] successfully checked out Feb 9 12:00:23 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:23 charon 7913 02[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:23 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:23 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:22 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[4500] Feb 9 12:00:22 charon 7913 02[MGR] <con-mobile|25> checkin of IKE_SA successful Feb 9 12:00:22 charon 7913 02[MGR] <con-mobile|25> checkin IKE_SA con-mobile[25] Feb 9 12:00:22 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[4500] Feb 9 12:00:22 charon 7913 02[NET] <con-mobile|25> sending packet: from $HOME_ip[4500] to $WORK_ip[4500] (142 bytes) Feb 9 12:00:22 charon 7913 02[NET] <con-mobile|25> sending packet: from $HOME_ip[4500] to $WORK_ip[4500] (1248 bytes) Feb 9 12:00:22 charon 7913 02[IKE] <con-mobile|25> received retransmit of request with ID 1, retransmitting response Feb 9 12:00:22 charon 7913 02[ENC] <con-mobile|25> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Feb 9 12:00:22 charon 7913 02[ENC] <con-mobile|25> received fragment #3 of 3, reassembled fragmented IKE message (1462 bytes) Feb 9 12:00:22 charon 7913 02[ENC] <con-mobile|25> parsed IKE_AUTH request 1 [ EF(3/3) ] Feb 9 12:00:22 charon 7913 02[NET] <con-mobile|25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (476 bytes) Feb 9 12:00:22 charon 7913 02[MGR] IKE_SA con-mobile[25] successfully checked out Feb 9 12:00:22 charon 7913 07[MGR] <con-mobile|25> checkin of IKE_SA successful Feb 9 12:00:22 charon 7913 07[MGR] <con-mobile|25> checkin IKE_SA con-mobile[25] Feb 9 12:00:22 charon 7913 07[ENC] <con-mobile|25> received fragment #2 of 3, waiting for complete IKE message Feb 9 12:00:22 charon 7913 07[ENC] <con-mobile|25> parsed IKE_AUTH request 1 [ EF(2/3) ] Feb 9 12:00:22 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:22 charon 7913 07[NET] <con-mobile|25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (572 bytes) Feb 9 12:00:22 charon 7913 02[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:22 charon 7913 07[MGR] IKE_SA con-mobile[25] successfully checked out Feb 9 12:00:22 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:22 charon 7913 02[MGR] <con-mobile|25> checkin of IKE_SA successful Feb 9 12:00:22 charon 7913 02[MGR] <con-mobile|25> checkin IKE_SA con-mobile[25] Feb 9 12:00:22 charon 7913 02[ENC] <con-mobile|25> received fragment #1 of 3, waiting for complete IKE message Feb 9 12:00:22 charon 7913 02[ENC] <con-mobile|25> parsed IKE_AUTH request 1 [ EF(1/3) ] Feb 9 12:00:22 charon 7913 02[NET] <con-mobile|25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (572 bytes) Feb 9 12:00:22 charon 7913 07[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:22 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:22 charon 7913 02[MGR] IKE_SA con-mobile[25] successfully checked out Feb 9 12:00:22 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:22 charon 7913 02[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:22 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:22 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:21 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[4500] Feb 9 12:00:21 charon 7913 02[MGR] <con-mobile|25> checkin of IKE_SA successful Feb 9 12:00:21 charon 7913 02[MGR] <con-mobile|25> checkin IKE_SA con-mobile[25] Feb 9 12:00:21 charon 7913 06[NET] sending packet: from $HOME_ip[4500] to $WORK_ip[4500] Feb 9 12:00:21 charon 7913 02[NET] <con-mobile|25> sending packet: from $HOME_ip[4500] to $WORK_ip[4500] (142 bytes) Feb 9 12:00:21 charon 7913 02[NET] <con-mobile|25> sending packet: from $HOME_ip[4500] to $WORK_ip[4500] (1248 bytes) Feb 9 12:00:21 charon 7913 02[ENC] <con-mobile|25> generating IKE_AUTH response 1 [ EF(2/2) ] Feb 9 12:00:21 charon 7913 02[ENC] <con-mobile|25> generating IKE_AUTH response 1 [ EF(1/2) ] Feb 9 12:00:21 charon 7913 02[ENC] <con-mobile|25> splitting IKE message (1325 bytes) into 2 fragments Feb 9 12:00:21 charon 7913 02[ENC] <con-mobile|25> generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ] Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> sending end entity cert "CN=$HOME_ip" Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> authentication of '$HOME_ip' (myself) with RSA signature successful Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> peer supports MOBIKE Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> processing INTERNAL_IP6_SERVER attribute Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> processing INTERNAL_IP6_DNS attribute Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> processing INTERNAL_IP6_ADDRESS attribute Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> processing INTERNAL_IP4_SERVER attribute Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> processing INTERNAL_IP4_NBNS attribute Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> processing INTERNAL_IP4_DNS attribute Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> processing INTERNAL_IP4_ADDRESS attribute Feb 9 12:00:21 charon 7913 02[IKE] <con-mobile|25> initiating EAP_IDENTITY method (id 0x00) Feb 9 12:00:21 charon 7913 02[CFG] <con-mobile|25> selected peer config 'con-mobile' Feb 9 12:00:21 charon 7913 02[CFG] <25> candidate "con-mobile", match: 1/1/1052 (me/other/ike) Feb 9 12:00:21 charon 7913 02[CFG] <25> looking for peer configs matching $HOME_ip[%any]...$WORK_ip[192.168.77.169] Feb 9 12:00:21 charon 7913 02[IKE] <25> received 58 cert requests for an unknown ca Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 74:90:04:91:02:a8:6b:bb:9d:67:27:dd:97:60:38:21:b6:5e:9b:51 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 42:d8:92:49:26:ea:53:93:82:22:7a:e5:fa:02:df:b3:99:e5:80:c4 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 87:00:6b:d6:d0:7d:11:75:69:82:01:a5:40:cf:55:f9:61:b8:38:4e Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 8b:39:c2:d3:d4:8a:d5:6c:00:c4:d9:b2:1e:88:c6:9e:22:a2:f6:f7 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 37:c2:ef:4f:95:7f:3d:f6:14:c3:9c:5d:b9:52:c2:8a:91:43:56:ce Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 4f:9c:7d:21:79:9c:ad:0e:d8:b9:0c:57:9f:1a:02:99:e7:90:f3:87 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 17:4a:b8:2b:5f:fb:05:67:75:27:ad:49:5a:4a:5d:c4:22:cc:ea:4e Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 67:ec:9f:90:2d:cd:64:ae:fe:7e:bc:cd:f8:8c:51:28:f1:93:2c:12 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid ee:e5:9f:1e:2a:a5:44:c3:cb:25:43:a6:9a:5b:d4:6a:25:bc:bb:8e Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid c8:95:13:68:01:97:28:0a:2c:55:c3:fc:d3:90:f5:3a:05:3b:c9:fb Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid bb:c2:3e:29:0b:b3:28:77:1d:ad:3e:a2:4d:bd:f4:23:bd:06:b0:3d Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid e6:ff:c3:94:e8:38:59:7f:51:d4:80:42:19:76:27:cf:db:94:8e:c6 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 21:0f:2c:89:f7:c4:cd:5d:1b:82:5e:38:d6:c6:59:3b:a6:93:75:ae Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid b1:81:08:1a:19:a4:c0:94:1f:fa:e8:95:28:c1:24:c9:9b:34:ac:c7 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 55:e4:81:d1:11:80:be:d8:89:b9:08:a3:31:f9:a1:24:09:16:b9:70 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 3e:22:d4:2c:1f:02:44:b8:04:10:65:61:7c:c7:6b:ae:da:87:29:9c Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 6d:aa:9b:09:87:c4:d0:d4:22:ed:40:07:37:4d:19:f1:91:ff:de:d3 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid e2:7f:7b:d8:77:d5:df:9e:0a:3f:9e:b4:cb:0e:2e:a9:ef:db:69:77 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 42:32:b6:16:fa:04:fd:fe:5d:4b:7a:c3:fd:f7:4c:40:1d:5a:43:af Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid ab:30:d3:af:4b:d8:f1:6b:58:69:ee:45:69:29:da:84:b8:73:94:88 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid d5:2e:13:c1:ab:e3:49:da:e8:b4:95:94:ef:7c:38:43:60:64:66:bd Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 4a:81:0c:de:f0:c0:90:0f:19:06:42:31:35:a2:a2:8d:d3:44:fd:08 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 6e:58:4e:33:75:bd:57:f6:d5:42:1b:16:01:c2:d8:c0:f5:3a:9f:6e Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 87:db:d4:5f:b0:92:8d:4e:1d:f8:15:67:e7:f2:ab:af:d6:2b:67:75 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid ba:42:b0:81:88:53:88:1d:86:63:bd:4c:c0:5e:08:fe:ea:6e:bb:77 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 69:c4:27:db:59:69:68:18:47:e2:52:17:0a:e0:e5:7f:ab:9d:ef:0f Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 73:97:82:ea:b4:04:16:6e:25:d4:82:3c:37:db:f8:a8:12:fb:cf:26 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid f8:16:51:3c:fd:1b:44:9f:2e:6b:28:a1:97:22:1f:b8:1f:51:4e:3c Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 90:e2:41:c2:11:41:8b:95:b1:a9:e0:9c:37:24:7e:84:9f:e4:be:a1 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid a2:af:24:0a:da:e8:67:79:c8:a8:50:b3:c7:46:ee:d9:f7:1b:16:78 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid c4:30:28:c5:d3:e3:08:0c:10:44:8b:2c:77:ba:24:53:97:60:bb:f9 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 30:a4:e6:4f:de:76:8a:fc:ed:5a:90:84:28:30:46:79:2c:29:15:70 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid f7:93:19:ef:df:c1:f5:20:fb:ac:85:55:2c:f2:d2:8f:5a:b9:ca:0b Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid b5:99:33:43:ac:a2:17:c5:08:ba:88:8c:a6:92:7e:26:b3:0f:87:a9 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid a8:e3:02:96:70:a6:8b:57:eb:ec:ef:cc:29:4e:91:74:9a:d4:92:38 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid ed:0d:c8:d6:2c:d3:13:29:d8:82:fe:2d:c3:fc:c5:10:d3:4d:bb:14 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 86:26:cb:1b:c5:54:b3:9f:bd:6b:ed:63:7f:b9:89:a9:80:f1:f4:8a Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 5e:8c:53:18:22:60:1d:56:71:d6:6a:a0:cc:64:a0:60:07:43:d5:a8 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid f8:92:0b:e9:08:a9:c5:d5:a0:fb:f3:9a:aa:98:a5:74:37:49:ad:9f Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 87:e3:bf:32:24:27:c1:40:5d:27:36:c3:81:e0:1d:1a:71:d4:a0:39 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid da:ed:64:74:14:9c:14:3c:ab:dd:99:a9:bd:5b:28:4d:8b:3c:c9:d8 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid e1:a0:5a:95:34:75:78:a7:ff:4d:cf:32:52:5d:f2:f8:2c:1a:e1:15 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 64:1d:f8:d5:0e:23:31:c2:29:b2:50:cb:32:f5:6d:f5:5c:8e:00:fa Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 7c:32:d4:85:fd:89:0a:66:b5:97:ce:86:f4:d5:26:a9:21:07:e8:3e Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 3e:df:29:0c:c1:f5:cc:73:2c:eb:3d:24:e1:7e:52:da:bd:27:e2:f0 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 34:4f:30:2d:25:69:31:91:ea:f7:73:5c:ab:f5:86:8d:37:82:40:ec Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid f9:27:b6:1b:0a:37:f3:c3:1a:fa:17:ec:2d:46:17:16:12:9d:0c:0e Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 88:a9:5a:ef:c0:84:fc:13:74:41:6b:b1:63:32:c2:cf:92:59:bb:3b Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 01:f0:33:4c:1a:a1:d9:ee:5b:7b:a9:de:43:bc:02:7d:57:09:33:fb Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for "CN=pfsense.local.lan" Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 6a:47:a2:67:c9:2e:2f:19:68:8b:9b:86:61:66:95:ed:c1:2c:13:00 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 5c:b8:69:fe:8d:ef:c1:ed:66:27:ee:b2:12:0f:72:1b:b8:0a:0e:04 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 4a:5c:75:22:aa:46:bf:a4:08:9d:39:97:4e:bd:b4:a3:60:f7:a0:1d Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid dd:bc:bd:86:9c:3f:07:ed:40:e3:1b:08:ef:ce:c4:d1:88:cd:3b:15 Feb 9 12:00:21 charon 7913 02[IKE] <25> received cert request for unknown ca with keyid 0e:ac:82:60:40:56:27:97:e5:25:13:fc:2a:e1:0a:53:95:59:e4:a4 Feb 9 12:00:21 charon 7913 02[ENC] <25> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Feb 9 12:00:21 charon 7913 02[ENC] <25> received fragment #3 of 3, reassembled fragmented IKE message (1462 bytes) Feb 9 12:00:21 charon 7913 02[ENC] <25> parsed IKE_AUTH request 1 [ EF(3/3) ] Feb 9 12:00:21 charon 7913 02[NET] <25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (476 bytes) Feb 9 12:00:21 charon 7913 02[MGR] IKE_SA (unnamed)[25] successfully checked out Feb 9 12:00:21 charon 7913 02[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:21 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:21 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:21 charon 7913 10[MGR] <25> checkin of IKE_SA successful Feb 9 12:00:21 charon 7913 10[MGR] <25> checkin IKE_SA (unnamed)[25] Feb 9 12:00:21 charon 7913 10[ENC] <25> received fragment #2 of 3, waiting for complete IKE message Feb 9 12:00:21 charon 7913 10[ENC] <25> parsed IKE_AUTH request 1 [ EF(2/3) ] Feb 9 12:00:21 charon 7913 10[NET] <25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (572 bytes) Feb 9 12:00:21 charon 7913 10[MGR] IKE_SA (unnamed)[25] successfully checked out Feb 9 12:00:21 charon 7913 10[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:21 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:21 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:21 charon 7913 10[MGR] <25> checkin of IKE_SA successful Feb 9 12:00:21 charon 7913 10[MGR] <25> checkin IKE_SA (unnamed)[25] Feb 9 12:00:21 charon 7913 10[ENC] <25> received fragment #1 of 3, waiting for complete IKE message Feb 9 12:00:21 charon 7913 10[ENC] <25> parsed IKE_AUTH request 1 [ EF(1/3) ] Feb 9 12:00:21 charon 7913 10[NET] <25> received packet: from $WORK_ip[4500] to $HOME_ip[4500] (572 bytes) Feb 9 12:00:21 charon 7913 10[MGR] IKE_SA (unnamed)[25] successfully checked out Feb 9 12:00:21 charon 7913 10[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 4af671f3400afd23_r Feb 9 12:00:21 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:21 charon 7913 08[NET] received packet: from $WORK_ip[4500] to $HOME_ip[4500] Feb 9 12:00:21 charon 7913 10[MGR] <25> checkin of IKE_SA successful Feb 9 12:00:21 charon 7913 10[MGR] <25> checkin IKE_SA (unnamed)[25] Feb 9 12:00:21 charon 7913 06[NET] sending packet: from $HOME_ip[500] to $WORK_ip[500] Feb 9 12:00:21 charon 7913 10[NET] <25> sending packet: from $HOME_ip[500] to $WORK_ip[500] (313 bytes) Feb 9 12:00:21 charon 7913 10[ENC] <25> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(CHDLESS_SUP) N(MULT_AUTH) ] Feb 9 12:00:21 charon 7913 10[IKE] <25> sending cert request for "CN=pfsense.local.lan" Feb 9 12:00:21 charon 7913 10[IKE] <25> remote host is behind NAT Feb 9 12:00:21 charon 7913 10[CFG] <25> selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 9 12:00:21 charon 7913 10[CFG] <25> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 9 12:00:21 charon 7913 10[CFG] <25> received proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 9 12:00:21 charon 7913 10[CFG] <25> proposal matches Feb 9 12:00:21 charon 7913 10[CFG] <25> selecting proposal: Feb 9 12:00:21 charon 7913 10[IKE] <25> IKE_SA (unnamed)[25] state change: CREATED => CONNECTING Feb 9 12:00:21 charon 7913 10[IKE] <25> $WORK_ip is initiating an IKE_SA Feb 9 12:00:21 charon 7913 10[ENC] <25> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02 Feb 9 12:00:21 charon 7913 10[IKE] <25> received Vid-Initial-Contact vendor ID Feb 9 12:00:21 charon 7913 10[IKE] <25> received MS-Negotiation Discovery Capable vendor ID Feb 9 12:00:21 charon 7913 10[IKE] <25> received MS NT5 ISAKMPOAKLEY v9 vendor ID Feb 9 12:00:21 charon 7913 10[CFG] <25> found matching ike config: $HOME_ip...0.0.0.0/0, ::/0 with prio 1052 Feb 9 12:00:21 charon 7913 10[CFG] <25> candidate: $HOME_ip...0.0.0.0/0, ::/0, prio 1052 Feb 9 12:00:21 charon 7913 10[CFG] <25> looking for an IKEv2 config for $HOME_ip...$WORK_ip Feb 9 12:00:21 charon 7913 10[ENC] <25> parsed IKE_SA_INIT request 0 [ SA KE No N(FRAG_SUP) N(NATD_S_IP) N(NATD_D_IP) V V V V ] Feb 9 12:00:21 charon 7913 10[NET] <25> received packet: from $WORK_ip[500] to $HOME_ip[500] (376 bytes) Feb 9 12:00:21 charon 7913 10[MGR] created IKE_SA (unnamed)[25] Feb 9 12:00:21 charon 7913 10[MGR] checkout IKEv2 SA by message with SPIs e4f8c37ffe76d934_i 0000000000000000_r Feb 9 12:00:21 charon 7913 08[NET] waiting for data on sockets Feb 9 12:00:21 charon 7913 08[NET] received packet: from $WORK_ip[500] to $HOME_ip[500] -
Update:
I reset all the lifetimes to their default values (left blank and let it refill). Turned off reauth.
Connected.... Rekey in about 3 hours. Will update when I get home from work if it stayed connected. -
@brswattt said in IKEv2 IPSEC VPN - Randomly stopped working:
Feb 9 11:19:51 charon 7913 14[IKE] <con-mobile|7> received NO_PROPOSAL_CHOSEN notify, no CHILD_SA built
I noticed this line, looks like your client has some issues, during rekey you should see at lease 1 proposal
can you dump the ipsec log from your client?
-
@lolipoplo I have corrected that specific issue, my Windows client had a registry key forcing certain proposal settings. I don't have that issue now.
I just saw a phase 2 rekey go and be successful. I'm thinking about triggering a manual rekey for phase 1 to see if it works.
-
Okay, I triggered a manual rekey of the Phase 1 connection and it doesn't seem like it worked. I was able to connect after though.
Feb 9 15:42:47 charon 71704 12[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:47 charon 71704 12[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:47 charon 71704 12[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:47 charon 71704 12[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:44 charon 71704 13[CFG] vici client 1385 disconnected Feb 9 15:42:44 charon 71704 13[CFG] vici client 1385 requests: list-sas Feb 9 15:42:44 charon 71704 13[CFG] vici client 1385 registered for: list-sa Feb 9 15:42:44 charon 71704 07[CFG] vici client 1385 connected Feb 9 15:42:44 charon 71704 15[CFG] vici client 1384 disconnected Feb 9 15:42:44 charon 71704 10[CFG] vici client 1384 requests: list-sas Feb 9 15:42:44 charon 71704 10[CFG] vici client 1384 registered for: list-sa Feb 9 15:42:44 charon 71704 15[CFG] vici client 1384 connected Feb 9 15:42:39 charon 71704 11[CFG] vici client 1383 disconnected Feb 9 15:42:39 charon 71704 09[CFG] vici client 1383 requests: list-sas Feb 9 15:42:39 charon 71704 11[CFG] vici client 1383 registered for: list-sa Feb 9 15:42:39 charon 71704 08[CFG] vici client 1383 connected Feb 9 15:42:38 charon 71704 15[CFG] vici client 1382 disconnected Feb 9 15:42:38 charon 71704 10[CFG] vici client 1382 requests: list-sas Feb 9 15:42:38 charon 71704 10[CFG] vici client 1382 registered for: list-sa Feb 9 15:42:38 charon 71704 07[CFG] vici client 1382 connected Feb 9 15:42:36 charon 71704 15[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:36 charon 71704 15[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:36 charon 71704 15[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:36 charon 71704 15[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:35 charon 71704 15[MGR] IKE_SA checkout not successful Feb 9 15:42:35 charon 71704 15[MGR] checkout IKEv2 SA by message with SPIs 66b6641a86f9ba9a_i 22d4293daaeb31a6_r Feb 9 15:42:35 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:35 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:34 charon 71704 15[MGR] IKE_SA checkout not successful Feb 9 15:42:34 charon 71704 15[MGR] checkout IKEv2 SA by message with SPIs 66b6641a86f9ba9a_i 22d4293daaeb31a6_r Feb 9 15:42:34 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:34 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:33 charon 71704 12[MGR] IKE_SA checkout not successful Feb 9 15:42:33 charon 71704 12[MGR] checkout IKEv2 SA by message with SPIs 66b6641a86f9ba9a_i 22d4293daaeb31a6_r Feb 9 15:42:33 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:33 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:33 charon 71704 08[CFG] vici client 1381 disconnected Feb 9 15:42:33 charon 71704 11[CFG] vici client 1381 requests: list-sas Feb 9 15:42:33 charon 71704 08[CFG] vici client 1381 registered for: list-sa Feb 9 15:42:33 charon 71704 11[CFG] vici client 1381 connected Feb 9 15:42:32 charon 71704 09[MGR] IKE_SA checkout not successful Feb 9 15:42:32 charon 71704 09[MGR] checkout IKEv2 SA by message with SPIs 66b6641a86f9ba9a_i 22d4293daaeb31a6_r Feb 9 15:42:32 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:32 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:31 charon 71704 07[CFG] vici client 1380 disconnected Feb 9 15:42:31 charon 71704 10[CFG] vici client 1380 requests: list-sas Feb 9 15:42:31 charon 71704 15[CFG] vici client 1380 registered for: list-sa Feb 9 15:42:31 charon 71704 07[CFG] vici client 1380 connected Feb 9 15:42:30 charon 71704 10[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:30 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[53561] Feb 9 15:42:30 charon 71704 10[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:30 charon 71704 10[NET] <con-mobile|3> sending packet: from $HOME_IP[4500] to $WORK_IP[53561] (245 bytes) Feb 9 15:42:30 charon 71704 10[IKE] <con-mobile|3> retransmit 3 of request with message ID 270 Feb 9 15:42:30 charon 71704 10[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:30 charon 71704 10[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:28 charon 71704 11[CFG] vici client 1379 disconnected Feb 9 15:42:28 charon 71704 14[CFG] vici client 1379 requests: list-sas Feb 9 15:42:28 charon 71704 08[CFG] vici client 1379 registered for: list-sa Feb 9 15:42:28 charon 71704 14[CFG] vici client 1379 connected Feb 9 15:42:26 charon 71704 11[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:26 charon 71704 11[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:26 charon 71704 11[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:26 charon 71704 11[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:25 charon 71704 07[CFG] vici client 1378 disconnected Feb 9 15:42:25 charon 71704 15[CFG] vici client 1378 requests: list-sas Feb 9 15:42:25 charon 71704 07[CFG] vici client 1378 registered for: list-sa Feb 9 15:42:25 charon 71704 06[CFG] vici client 1378 connected Feb 9 15:42:24 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:24 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:22 charon 71704 14[CFG] vici client 1377 disconnected Feb 9 15:42:22 charon 71704 08[CFG] vici client 1377 requests: list-sas Feb 9 15:42:22 charon 71704 08[CFG] vici client 1377 registered for: list-sa Feb 9 15:42:22 charon 71704 11[CFG] vici client 1377 connected Feb 9 15:42:19 charon 71704 06[CFG] vici client 1376 disconnected Feb 9 15:42:19 charon 71704 07[CFG] vici client 1376 requests: list-sas Feb 9 15:42:19 charon 71704 15[CFG] vici client 1376 registered for: list-sa Feb 9 15:42:19 charon 71704 07[CFG] vici client 1376 connected Feb 9 15:42:17 charon 71704 12[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:17 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[53561] Feb 9 15:42:17 charon 71704 12[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:17 charon 71704 12[NET] <con-mobile|3> sending packet: from $HOME_IP[4500] to $WORK_IP[53561] (245 bytes) Feb 9 15:42:17 charon 71704 12[IKE] <con-mobile|3> retransmit 2 of request with message ID 270 Feb 9 15:42:17 charon 71704 12[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:17 charon 71704 12[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:16 charon 71704 08[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:16 charon 71704 08[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:16 charon 71704 08[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:16 charon 71704 08[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:16 charon 71704 11[CFG] vici client 1375 disconnected Feb 9 15:42:16 charon 71704 08[CFG] vici client 1375 requests: list-sas Feb 9 15:42:16 charon 71704 08[CFG] vici client 1375 registered for: list-sa Feb 9 15:42:16 charon 71704 11[CFG] vici client 1375 connected Feb 9 15:42:15 charon 71704 16[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:15 charon 71704 16[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:15 charon 71704 16[IKE] <con-mobile|3> INFORMATIONAL request with message ID 503 processing failed Feb 9 15:42:15 charon 71704 16[IKE] <con-mobile|3> integrity check failed Feb 9 15:42:15 charon 71704 16[ENC] <con-mobile|3> could not decrypt payloads Feb 9 15:42:15 charon 71704 16[ENC] <con-mobile|3> verifying encrypted payload integrity failed Feb 9 15:42:15 charon 71704 16[NET] <con-mobile|3> received packet: from $WORK_IP[53561] to $HOME_IP[4500] (72 bytes) Feb 9 15:42:15 charon 71704 16[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:15 charon 71704 16[MGR] checkout IKEv2 SA by message with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:15 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:15 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:14 charon 71704 14[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:14 charon 71704 14[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:14 charon 71704 14[IKE] <con-mobile|3> INFORMATIONAL request with message ID 503 processing failed Feb 9 15:42:14 charon 71704 14[IKE] <con-mobile|3> integrity check failed Feb 9 15:42:14 charon 71704 14[ENC] <con-mobile|3> could not decrypt payloads Feb 9 15:42:14 charon 71704 14[ENC] <con-mobile|3> verifying encrypted payload integrity failed Feb 9 15:42:14 charon 71704 14[NET] <con-mobile|3> received packet: from $WORK_IP[53561] to $HOME_IP[4500] (72 bytes) Feb 9 15:42:14 charon 71704 14[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:14 charon 71704 14[MGR] checkout IKEv2 SA by message with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:14 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:14 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:13 charon 71704 07[CFG] vici client 1374 disconnected Feb 9 15:42:13 charon 71704 07[CFG] vici client 1374 requests: list-sas Feb 9 15:42:13 charon 71704 15[CFG] vici client 1374 registered for: list-sa Feb 9 15:42:13 charon 71704 06[CFG] vici client 1374 connected Feb 9 15:42:13 charon 71704 07[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:13 charon 71704 07[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:13 charon 71704 07[IKE] <con-mobile|3> INFORMATIONAL request with message ID 503 processing failed Feb 9 15:42:13 charon 71704 07[IKE] <con-mobile|3> integrity check failed Feb 9 15:42:13 charon 71704 07[ENC] <con-mobile|3> could not decrypt payloads Feb 9 15:42:13 charon 71704 07[ENC] <con-mobile|3> verifying encrypted payload integrity failed Feb 9 15:42:13 charon 71704 07[NET] <con-mobile|3> received packet: from $WORK_IP[53561] to $HOME_IP[4500] (72 bytes) Feb 9 15:42:13 charon 71704 07[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:13 charon 71704 07[MGR] checkout IKEv2 SA by message with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:13 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:13 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:11 charon 71704 11[CFG] vici client 1373 disconnected Feb 9 15:42:11 charon 71704 11[CFG] vici client 1373 requests: list-sas Feb 9 15:42:11 charon 71704 16[CFG] vici client 1373 registered for: list-sa Feb 9 15:42:11 charon 71704 11[CFG] vici client 1373 connected Feb 9 15:42:09 charon 71704 16[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:09 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[53561] Feb 9 15:42:09 charon 71704 16[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:09 charon 71704 16[NET] <con-mobile|3> sending packet: from $HOME_IP[4500] to $WORK_IP[53561] (245 bytes) Feb 9 15:42:09 charon 71704 16[IKE] <con-mobile|3> retransmit 1 of request with message ID 270 Feb 9 15:42:09 charon 71704 16[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:09 charon 71704 16[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:07 charon 71704 06[CFG] vici client 1372 disconnected Feb 9 15:42:07 charon 71704 15[CFG] vici client 1372 requests: list-sas Feb 9 15:42:07 charon 71704 15[CFG] vici client 1372 registered for: list-sa Feb 9 15:42:07 charon 71704 06[CFG] vici client 1372 connected Feb 9 15:42:06 charon 71704 13[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:06 charon 71704 13[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:06 charon 71704 13[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:06 charon 71704 13[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:05 charon 71704 10[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:05 charon 71704 10[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:05 charon 71704 10[IKE] <con-mobile|3> CREATE_CHILD_SA response with message ID 270 processing failed Feb 9 15:42:05 charon 71704 10[IKE] <con-mobile|3> integrity check failed Feb 9 15:42:05 charon 71704 10[ENC] <con-mobile|3> could not decrypt payloads Feb 9 15:42:05 charon 71704 10[ENC] <con-mobile|3> verifying encrypted payload integrity failed Feb 9 15:42:05 charon 71704 10[NET] <con-mobile|3> received packet: from $WORK_IP[53561] to $HOME_IP[4500] (264 bytes) Feb 9 15:42:05 charon 71704 10[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:05 charon 71704 10[MGR] checkout IKEv2 SA by message with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:05 charon 71704 01[NET] waiting for data on sockets Feb 9 15:42:05 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 15:42:05 charon 71704 10[MGR] <con-mobile|3> checkin of IKE_SA successful Feb 9 15:42:05 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[53561] Feb 9 15:42:05 charon 71704 10[MGR] <con-mobile|3> checkin IKE_SA con-mobile[3] Feb 9 15:42:05 charon 71704 10[NET] <con-mobile|3> sending packet: from $HOME_IP[4500] to $WORK_IP[53561] (245 bytes) Feb 9 15:42:05 charon 71704 10[ENC] <con-mobile|3> generating CREATE_CHILD_SA request 270 [ SA No KE ] Feb 9 15:42:05 charon 71704 10[CFG] <con-mobile|3> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 9 15:42:05 charon 71704 10[IKE] <con-mobile|3> IKE_SA con-mobile[4] state change: CREATED => CONNECTING Feb 9 15:42:05 charon 71704 10[IKE] <con-mobile|3> initiating IKE_SA con-mobile[4] to $WORK_IP Feb 9 15:42:05 charon 71704 10[IKE] <con-mobile|3> IKE_SA con-mobile[3] state change: ESTABLISHED => REKEYING Feb 9 15:42:05 charon 71704 10[MGR] <con-mobile|3> created IKE_SA (unnamed)[4] Feb 9 15:42:05 charon 71704 10[IKE] <con-mobile|3> activating IKE_REKEY task Feb 9 15:42:05 charon 71704 10[IKE] <con-mobile|3> activating new tasks Feb 9 15:42:05 charon 71704 10[IKE] <con-mobile|3> queueing IKE_REKEY task Feb 9 15:42:05 charon 71704 10[MGR] IKE_SA con-mobile[3] successfully checked out Feb 9 15:42:05 charon 71704 10[MGR] checkout IKEv2 SA with SPIs 909dd139ad9a2016_i 28cb1ec1bac43146_r Feb 9 15:42:05 charon 71704 07[CFG] received stroke: rekey 'con-mobile[3]' -
So the rekey didn't work of course....here is the log
Only thing I can see that is weird is the "verifying encrypted payload integrity failed"/ "CREATE_CHILD_SA response with message ID 355 processing failed" Any idea guys? Real annoying, now I can't even connect back.
Feb 9 19:35:11 charon 71704 14[CFG] vici client 4445 disconnected Feb 9 19:35:11 charon 71704 11[CFG] vici client 4445 requests: list-sas Feb 9 19:35:11 charon 71704 12[CFG] vici client 4445 registered for: list-sa Feb 9 19:35:11 charon 71704 11[CFG] vici client 4445 connected Feb 9 19:35:09 charon 71704 14[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:35:09 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[53561] Feb 9 19:35:09 charon 71704 14[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:35:09 charon 71704 14[NET] <con-mobile|6> sending packet: from $HOME_IP[4500] to $WORK_IP[53561] (245 bytes) Feb 9 19:35:09 charon 71704 14[IKE] <con-mobile|6> retransmit 3 of request with message ID 355 Feb 9 19:35:09 charon 71704 14[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:35:09 charon 71704 14[MGR] checkout IKEv2 SA with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:35:08 charon 71704 10[CFG] vici client 4444 disconnected Feb 9 19:35:08 charon 71704 07[CFG] vici client 4444 requests: list-sas Feb 9 19:35:08 charon 71704 10[CFG] vici client 4444 registered for: list-sa Feb 9 19:35:08 charon 71704 07[CFG] vici client 4444 connected Feb 9 19:35:06 charon 71704 16[MGR] IKE_SA checkout not successful Feb 9 19:35:06 charon 71704 16[MGR] checkout IKEv2 SA by message with SPIs ee9bd6c6f5645f0e_i adf777d30f13ecb5_r Feb 9 19:35:06 charon 71704 01[NET] waiting for data on sockets Feb 9 19:35:06 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:35:05 charon 71704 16[MGR] IKE_SA checkout not successful Feb 9 19:35:05 charon 71704 16[MGR] checkout IKEv2 SA by message with SPIs ee9bd6c6f5645f0e_i adf777d30f13ecb5_r Feb 9 19:35:05 charon 71704 01[NET] waiting for data on sockets Feb 9 19:35:05 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:35:04 charon 71704 11[CFG] vici client 4443 disconnected Feb 9 19:35:04 charon 71704 12[CFG] vici client 4443 requests: list-sas Feb 9 19:35:04 charon 71704 11[CFG] vici client 4443 registered for: list-sa Feb 9 19:35:04 charon 71704 14[CFG] vici client 4443 connected Feb 9 19:35:04 charon 71704 11[MGR] IKE_SA checkout not successful Feb 9 19:35:04 charon 71704 11[MGR] checkout IKEv2 SA by message with SPIs ee9bd6c6f5645f0e_i adf777d30f13ecb5_r Feb 9 19:35:04 charon 71704 01[NET] waiting for data on sockets Feb 9 19:35:04 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:35:04 charon 71704 01[NET] waiting for data on sockets Feb 9 19:35:04 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:35:03 charon 71704 11[MGR] IKE_SA checkout not successful Feb 9 19:35:03 charon 71704 11[MGR] checkout IKEv2 SA by message with SPIs ee9bd6c6f5645f0e_i adf777d30f13ecb5_r Feb 9 19:35:03 charon 71704 01[NET] waiting for data on sockets Feb 9 19:35:03 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:35:03 charon 71704 06[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:35:03 charon 71704 06[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:35:03 charon 71704 06[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:35:03 charon 71704 06[MGR] checkout IKEv2 SA with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:35:03 charon 71704 07[CFG] vici client 4442 disconnected Feb 9 19:35:03 charon 71704 16[CFG] vici client 4442 requests: list-sas Feb 9 19:35:03 charon 71704 07[CFG] vici client 4442 registered for: list-sa Feb 9 19:35:03 charon 71704 16[CFG] vici client 4442 connected Feb 9 19:34:58 charon 71704 14[CFG] vici client 4441 disconnected Feb 9 19:34:58 charon 71704 12[CFG] vici client 4441 requests: list-sas Feb 9 19:34:58 charon 71704 14[CFG] vici client 4441 registered for: list-sa Feb 9 19:34:58 charon 71704 12[CFG] vici client 4441 connected Feb 9 19:34:57 charon 71704 16[CFG] vici client 4440 disconnected Feb 9 19:34:57 charon 71704 07[CFG] vici client 4440 requests: list-sas Feb 9 19:34:57 charon 71704 16[CFG] vici client 4440 registered for: list-sa Feb 9 19:34:57 charon 71704 10[CFG] vici client 4440 connected Feb 9 19:34:56 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[53561] Feb 9 19:34:56 charon 71704 07[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:56 charon 71704 07[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:56 charon 71704 07[NET] <con-mobile|6> sending packet: from $HOME_IP[4500] to $WORK_IP[53561] (245 bytes) Feb 9 19:34:56 charon 71704 07[IKE] <con-mobile|6> retransmit 2 of request with message ID 355 Feb 9 19:34:56 charon 71704 07[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:34:56 charon 71704 07[MGR] checkout IKEv2 SA with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:34:53 charon 71704 07[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:53 charon 71704 07[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:53 charon 71704 07[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:34:53 charon 71704 07[MGR] checkout IKEv2 SA with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:34:52 charon 71704 12[CFG] vici client 4439 disconnected Feb 9 19:34:52 charon 71704 15[CFG] vici client 4439 requests: list-sas Feb 9 19:34:52 charon 71704 15[CFG] vici client 4439 registered for: list-sa Feb 9 19:34:52 charon 71704 14[CFG] vici client 4439 connected Feb 9 19:34:52 charon 71704 10[CFG] vici client 4438 disconnected Feb 9 19:34:52 charon 71704 16[CFG] vici client 4438 requests: list-sas Feb 9 19:34:52 charon 71704 10[CFG] vici client 4438 registered for: list-sa Feb 9 19:34:52 charon 71704 16[CFG] vici client 4438 connected Feb 9 19:34:51 charon 71704 06[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:51 charon 71704 06[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:51 charon 71704 06[IKE] <con-mobile|6> INFORMATIONAL request with message ID 1016 processing failed Feb 9 19:34:51 charon 71704 06[IKE] <con-mobile|6> integrity check failed Feb 9 19:34:51 charon 71704 06[ENC] <con-mobile|6> could not decrypt payloads Feb 9 19:34:51 charon 71704 06[ENC] <con-mobile|6> verifying encrypted payload integrity failed Feb 9 19:34:51 charon 71704 06[NET] <con-mobile|6> received packet: from $WORK_IP[53561] to $HOME_IP[4500] (72 bytes) Feb 9 19:34:51 charon 71704 06[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:34:51 charon 71704 06[MGR] checkout IKEv2 SA by message with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:34:51 charon 71704 01[NET] waiting for data on sockets Feb 9 19:34:51 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:34:50 charon 71704 06[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:50 charon 71704 06[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:50 charon 71704 06[IKE] <con-mobile|6> INFORMATIONAL request with message ID 1016 processing failed Feb 9 19:34:50 charon 71704 06[IKE] <con-mobile|6> integrity check failed Feb 9 19:34:50 charon 71704 06[ENC] <con-mobile|6> could not decrypt payloads Feb 9 19:34:50 charon 71704 06[ENC] <con-mobile|6> verifying encrypted payload integrity failed Feb 9 19:34:50 charon 71704 06[NET] <con-mobile|6> received packet: from $WORK_IP[53561] to $HOME_IP[4500] (72 bytes) Feb 9 19:34:50 charon 71704 06[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:34:50 charon 71704 06[MGR] checkout IKEv2 SA by message with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:34:50 charon 71704 01[NET] waiting for data on sockets Feb 9 19:34:50 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:34:49 charon 71704 06[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:49 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[53561] Feb 9 19:34:49 charon 71704 06[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:49 charon 71704 06[NET] <con-mobile|6> sending packet: from $HOME_IP[4500] to $WORK_IP[53561] (245 bytes) Feb 9 19:34:49 charon 71704 06[IKE] <con-mobile|6> retransmit 1 of request with message ID 355 Feb 9 19:34:49 charon 71704 06[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:34:49 charon 71704 06[MGR] checkout IKEv2 SA with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:34:49 charon 71704 07[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:49 charon 71704 07[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:49 charon 71704 07[IKE] <con-mobile|6> INFORMATIONAL request with message ID 1016 processing failed Feb 9 19:34:49 charon 71704 07[IKE] <con-mobile|6> integrity check failed Feb 9 19:34:49 charon 71704 07[ENC] <con-mobile|6> could not decrypt payloads Feb 9 19:34:49 charon 71704 07[ENC] <con-mobile|6> verifying encrypted payload integrity failed Feb 9 19:34:49 charon 71704 07[NET] <con-mobile|6> received packet: from $WORK_IP[53561] to $HOME_IP[4500] (72 bytes) Feb 9 19:34:49 charon 71704 07[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:34:49 charon 71704 07[MGR] checkout IKEv2 SA by message with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:34:49 charon 71704 01[NET] waiting for data on sockets Feb 9 19:34:49 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:34:47 charon 71704 07[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:47 charon 71704 07[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:47 charon 71704 07[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:34:47 charon 71704 07[MGR] checkout IKEv2 SA with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:34:46 charon 71704 09[CFG] vici client 4437 disconnected Feb 9 19:34:46 charon 71704 11[CFG] vici client 4437 requests: list-sas Feb 9 19:34:46 charon 71704 10[CFG] vici client 4437 registered for: list-sa Feb 9 19:34:46 charon 71704 09[CFG] vici client 4437 connected Feb 9 19:34:46 charon 71704 16[CFG] vici client 4436 disconnected Feb 9 19:34:46 charon 71704 06[CFG] vici client 4436 requests: list-sas Feb 9 19:34:46 charon 71704 06[CFG] vici client 4436 registered for: list-sa Feb 9 19:34:46 charon 71704 11[CFG] vici client 4436 connected Feb 9 19:34:45 charon 71704 16[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:45 charon 71704 16[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:45 charon 71704 16[IKE] <con-mobile|6> CREATE_CHILD_SA response with message ID 355 processing failed Feb 9 19:34:45 charon 71704 16[IKE] <con-mobile|6> integrity check failed Feb 9 19:34:45 charon 71704 16[ENC] <con-mobile|6> could not decrypt payloads Feb 9 19:34:45 charon 71704 16[ENC] <con-mobile|6> verifying encrypted payload integrity failed Feb 9 19:34:45 charon 71704 16[NET] <con-mobile|6> received packet: from $WORK_IP[53561] to $HOME_IP[4500] (264 bytes) Feb 9 19:34:45 charon 71704 16[MGR] IKE_SA con-mobile[6] successfully checked out Feb 9 19:34:45 charon 71704 16[MGR] checkout IKEv2 SA by message with SPIs 1421db634937e70d_i 638725af6178c479_r Feb 9 19:34:45 charon 71704 01[NET] waiting for data on sockets Feb 9 19:34:45 charon 71704 01[NET] received packet: from $WORK_IP[53561] to $HOME_IP[4500] Feb 9 19:34:45 charon 71704 16[MGR] <con-mobile|6> checkin of IKE_SA successful Feb 9 19:34:45 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[53561] Feb 9 19:34:45 charon 71704 16[MGR] <con-mobile|6> checkin IKE_SA con-mobile[6] Feb 9 19:34:45 charon 71704 16[NET] <con-mobile|6> sending packet: from $HOME_IP[4500] to $WORK_IP[53561] (245 bytes) Feb 9 19:34:45 charon 71704 16[ENC] <con-mobile|6> generating CREATE_CHILD_SA request 355 [ SA No KE ] Feb 9 19:34:45 charon 71704 16[CFG] <con-mobile|6> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 9 19:34:45 charon 71704 16[IKE] <con-mobile|6> IKE_SA con-mobile[7] state change: CREATED => CONNECTING Feb 9 19:34:45 charon 71704 16[IKE] <con-mobile|6> initiating IKE_SA con-mobile[7] to $WORK_IP Feb 9 19:34:45 charon 71704 16[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: ESTABLISHED => REKEYING Feb 9 19:34:45 charon 71704 16[MGR] <con-mobile|6> created IKE_SA (unnamed)[7] Feb 9 19:34:45 charon 71704 16[IKE] <con-mobile|6> activating IKE_REKEY task Feb 9 19:34:45 charon 71704 16[IKE] <con-mobile|6> activating new tasks Feb 9 19:34:45 charon 71704 16[IKE] <con-mobile|6> queueing IKE_REKEY task -
CONNECTION ATTEMPT AFTER REKEY FAIL LOG:
Feb 9 20:07:10 charon 71704 07[CFG] vici client 4816 disconnected Feb 9 20:07:10 charon 71704 15[CFG] vici client 4816 requests: list-sas Feb 9 20:07:10 charon 71704 13[CFG] vici client 4816 registered for: list-sa Feb 9 20:07:10 charon 71704 15[CFG] vici client 4816 connected Feb 9 20:07:04 charon 71704 10[CFG] vici client 4815 disconnected Feb 9 20:07:04 charon 71704 12[CFG] vici client 4815 requests: list-sas Feb 9 20:07:04 charon 71704 12[CFG] vici client 4815 registered for: list-sa Feb 9 20:07:04 charon 71704 10[CFG] vici client 4815 connected Feb 9 20:06:58 charon 71704 15[CFG] vici client 4814 disconnected Feb 9 20:06:58 charon 71704 13[CFG] vici client 4814 requests: list-sas Feb 9 20:06:58 charon 71704 15[CFG] vici client 4814 registered for: list-sa Feb 9 20:06:58 charon 71704 15[CFG] vici client 4814 connected Feb 9 20:06:52 charon 71704 11[CFG] vici client 4813 disconnected Feb 9 20:06:52 charon 71704 12[CFG] vici client 4813 requests: list-sas Feb 9 20:06:52 charon 71704 11[CFG] vici client 4813 registered for: list-sa Feb 9 20:06:52 charon 71704 10[CFG] vici client 4813 connected Feb 9 20:06:51 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[4500] Feb 9 20:06:51 charon 71704 12[MGR] <con-mobile|22> checkin of IKE_SA successful Feb 9 20:06:51 charon 71704 12[MGR] <con-mobile|22> checkin IKE_SA con-mobile[22] Feb 9 20:06:51 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[4500] Feb 9 20:06:51 charon 71704 12[NET] <con-mobile|22> sending packet: from $HOME_IP[4500] to $WORK_IP[4500] (142 bytes) Feb 9 20:06:51 charon 71704 12[NET] <con-mobile|22> sending packet: from $HOME_IP[4500] to $WORK_IP[4500] (1248 bytes) Feb 9 20:06:51 charon 71704 12[IKE] <con-mobile|22> received retransmit of request with ID 1, retransmitting response Feb 9 20:06:51 charon 71704 12[ENC] <con-mobile|22> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Feb 9 20:06:51 charon 71704 12[ENC] <con-mobile|22> received fragment #3 of 3, reassembled fragmented IKE message (1462 bytes) Feb 9 20:06:51 charon 71704 12[ENC] <con-mobile|22> parsed IKE_AUTH request 1 [ EF(3/3) ] Feb 9 20:06:51 charon 71704 12[NET] <con-mobile|22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (476 bytes) Feb 9 20:06:51 charon 71704 12[MGR] IKE_SA con-mobile[22] successfully checked out Feb 9 20:06:51 charon 71704 10[MGR] <con-mobile|22> checkin of IKE_SA successful Feb 9 20:06:51 charon 71704 10[MGR] <con-mobile|22> checkin IKE_SA con-mobile[22] Feb 9 20:06:51 charon 71704 10[ENC] <con-mobile|22> received fragment #2 of 3, waiting for complete IKE message Feb 9 20:06:51 charon 71704 10[ENC] <con-mobile|22> parsed IKE_AUTH request 1 [ EF(2/3) ] Feb 9 20:06:51 charon 71704 12[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:51 charon 71704 10[NET] <con-mobile|22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (572 bytes) Feb 9 20:06:51 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:51 charon 71704 10[MGR] IKE_SA con-mobile[22] successfully checked out Feb 9 20:06:51 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:51 charon 71704 10[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:51 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:51 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:51 charon 71704 10[MGR] <con-mobile|22> checkin of IKE_SA successful Feb 9 20:06:51 charon 71704 10[MGR] <con-mobile|22> checkin IKE_SA con-mobile[22] Feb 9 20:06:51 charon 71704 10[ENC] <con-mobile|22> received fragment #1 of 3, waiting for complete IKE message Feb 9 20:06:51 charon 71704 10[ENC] <con-mobile|22> parsed IKE_AUTH request 1 [ EF(1/3) ] Feb 9 20:06:51 charon 71704 10[NET] <con-mobile|22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (572 bytes) Feb 9 20:06:51 charon 71704 10[MGR] IKE_SA con-mobile[22] successfully checked out Feb 9 20:06:51 charon 71704 10[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:51 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:51 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:50 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[4500] Feb 9 20:06:50 charon 71704 10[MGR] <con-mobile|22> checkin of IKE_SA successful Feb 9 20:06:50 charon 71704 10[MGR] <con-mobile|22> checkin IKE_SA con-mobile[22] Feb 9 20:06:50 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[4500] Feb 9 20:06:50 charon 71704 10[NET] <con-mobile|22> sending packet: from $HOME_IP[4500] to $WORK_IP[4500] (142 bytes) Feb 9 20:06:50 charon 71704 10[NET] <con-mobile|22> sending packet: from $HOME_IP[4500] to $WORK_IP[4500] (1248 bytes) Feb 9 20:06:50 charon 71704 10[IKE] <con-mobile|22> received retransmit of request with ID 1, retransmitting response Feb 9 20:06:50 charon 71704 10[ENC] <con-mobile|22> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Feb 9 20:06:50 charon 71704 10[ENC] <con-mobile|22> received fragment #2 of 3, reassembled fragmented IKE message (1462 bytes) Feb 9 20:06:50 charon 71704 10[ENC] <con-mobile|22> parsed IKE_AUTH request 1 [ EF(2/3) ] Feb 9 20:06:50 charon 71704 10[NET] <con-mobile|22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (572 bytes) Feb 9 20:06:50 charon 71704 10[MGR] IKE_SA con-mobile[22] successfully checked out Feb 9 20:06:50 charon 71704 12[MGR] <con-mobile|22> checkin of IKE_SA successful Feb 9 20:06:50 charon 71704 12[MGR] <con-mobile|22> checkin IKE_SA con-mobile[22] Feb 9 20:06:50 charon 71704 12[ENC] <con-mobile|22> received fragment #3 of 3, waiting for complete IKE message Feb 9 20:06:50 charon 71704 12[ENC] <con-mobile|22> parsed IKE_AUTH request 1 [ EF(3/3) ] Feb 9 20:06:50 charon 71704 12[NET] <con-mobile|22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (476 bytes) Feb 9 20:06:50 charon 71704 12[MGR] IKE_SA con-mobile[22] successfully checked out Feb 9 20:06:50 charon 71704 11[MGR] <con-mobile|22> checkin of IKE_SA successful Feb 9 20:06:50 charon 71704 11[MGR] <con-mobile|22> checkin IKE_SA con-mobile[22] Feb 9 20:06:50 charon 71704 11[ENC] <con-mobile|22> received fragment #1 of 3, waiting for complete IKE message Feb 9 20:06:50 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:50 charon 71704 11[ENC] <con-mobile|22> parsed IKE_AUTH request 1 [ EF(1/3) ] Feb 9 20:06:50 charon 71704 12[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:50 charon 71704 10[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:50 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:50 charon 71704 11[NET] <con-mobile|22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (572 bytes) Feb 9 20:06:50 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:50 charon 71704 11[MGR] IKE_SA con-mobile[22] successfully checked out Feb 9 20:06:50 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:50 charon 71704 11[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:50 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:50 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:50 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[4500] Feb 9 20:06:50 charon 71704 11[MGR] <con-mobile|22> checkin of IKE_SA successful Feb 9 20:06:50 charon 71704 11[MGR] <con-mobile|22> checkin IKE_SA con-mobile[22] Feb 9 20:06:50 charon 71704 02[NET] sending packet: from $HOME_IP[4500] to $WORK_IP[4500] Feb 9 20:06:50 charon 71704 11[NET] <con-mobile|22> sending packet: from $HOME_IP[4500] to $WORK_IP[4500] (142 bytes) Feb 9 20:06:50 charon 71704 11[NET] <con-mobile|22> sending packet: from $HOME_IP[4500] to $WORK_IP[4500] (1248 bytes) Feb 9 20:06:50 charon 71704 11[ENC] <con-mobile|22> generating IKE_AUTH response 1 [ EF(2/2) ] Feb 9 20:06:50 charon 71704 11[ENC] <con-mobile|22> generating IKE_AUTH response 1 [ EF(1/2) ] Feb 9 20:06:50 charon 71704 11[ENC] <con-mobile|22> splitting IKE message (1325 bytes) into 2 fragments Feb 9 20:06:50 charon 71704 11[ENC] <con-mobile|22> generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ] Feb 9 20:06:50 charon 71704 11[IKE] <con-mobile|22> sending end entity cert "CN=$HOME_IP" Feb 9 20:06:50 charon 71704 11[IKE] <con-mobile|22> authentication of '$HOME_IP' (myself) with RSA signature successful Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> peer supports MOBIKE Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> processing INTERNAL_IP6_SERVER attribute Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> processing INTERNAL_IP6_DNS attribute Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> processing INTERNAL_IP6_ADDRESS attribute Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> processing INTERNAL_IP4_SERVER attribute Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> processing INTERNAL_IP4_NBNS attribute Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> processing INTERNAL_IP4_DNS attribute Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> processing INTERNAL_IP4_ADDRESS attribute Feb 9 20:06:49 charon 71704 11[IKE] <con-mobile|22> initiating EAP_IDENTITY method (id 0x00) Feb 9 20:06:49 charon 71704 11[CFG] <con-mobile|22> selected peer config 'con-mobile' Feb 9 20:06:49 charon 71704 11[CFG] <22> candidate "con-mobile", match: 1/1/1052 (me/other/ike) Feb 9 20:06:49 charon 71704 11[CFG] <22> looking for peer configs matching $HOME_IP[%any]...$WORK_IP[192.168.77.169] Feb 9 20:06:49 charon 71704 11[IKE] <22> received 58 cert requests for an unknown ca Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 74:90:04:91:02:a8:6b:bb:9d:67:27:dd:97:60:38:21:b6:5e:9b:51 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 42:d8:92:49:26:ea:53:93:82:22:7a:e5:fa:02:df:b3:99:e5:80:c4 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 87:00:6b:d6:d0:7d:11:75:69:82:01:a5:40:cf:55:f9:61:b8:38:4e Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 8b:39:c2:d3:d4:8a:d5:6c:00:c4:d9:b2:1e:88:c6:9e:22:a2:f6:f7 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 37:c2:ef:4f:95:7f:3d:f6:14:c3:9c:5d:b9:52:c2:8a:91:43:56:ce Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 4f:9c:7d:21:79:9c:ad:0e:d8:b9:0c:57:9f:1a:02:99:e7:90:f3:87 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 17:4a:b8:2b:5f:fb:05:67:75:27:ad:49:5a:4a:5d:c4:22:cc:ea:4e Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 67:ec:9f:90:2d:cd:64:ae:fe:7e:bc:cd:f8:8c:51:28:f1:93:2c:12 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid ee:e5:9f:1e:2a:a5:44:c3:cb:25:43:a6:9a:5b:d4:6a:25:bc:bb:8e Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid c8:95:13:68:01:97:28:0a:2c:55:c3:fc:d3:90:f5:3a:05:3b:c9:fb Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid bb:c2:3e:29:0b:b3:28:77:1d:ad:3e:a2:4d:bd:f4:23:bd:06:b0:3d Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid e6:ff:c3:94:e8:38:59:7f:51:d4:80:42:19:76:27:cf:db:94:8e:c6 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 21:0f:2c:89:f7:c4:cd:5d:1b:82:5e:38:d6:c6:59:3b:a6:93:75:ae Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid b1:81:08:1a:19:a4:c0:94:1f:fa:e8:95:28:c1:24:c9:9b:34:ac:c7 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 55:e4:81:d1:11:80:be:d8:89:b9:08:a3:31:f9:a1:24:09:16:b9:70 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 3e:22:d4:2c:1f:02:44:b8:04:10:65:61:7c:c7:6b:ae:da:87:29:9c Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 6d:aa:9b:09:87:c4:d0:d4:22:ed:40:07:37:4d:19:f1:91:ff:de:d3 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid e2:7f:7b:d8:77:d5:df:9e:0a:3f:9e:b4:cb:0e:2e:a9:ef:db:69:77 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 42:32:b6:16:fa:04:fd:fe:5d:4b:7a:c3:fd:f7:4c:40:1d:5a:43:af Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid ab:30:d3:af:4b:d8:f1:6b:58:69:ee:45:69:29:da:84:b8:73:94:88 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid d5:2e:13:c1:ab:e3:49:da:e8:b4:95:94:ef:7c:38:43:60:64:66:bd Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 4a:81:0c:de:f0:c0:90:0f:19:06:42:31:35:a2:a2:8d:d3:44:fd:08 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 6e:58:4e:33:75:bd:57:f6:d5:42:1b:16:01:c2:d8:c0:f5:3a:9f:6e Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 87:db:d4:5f:b0:92:8d:4e:1d:f8:15:67:e7:f2:ab:af:d6:2b:67:75 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid ba:42:b0:81:88:53:88:1d:86:63:bd:4c:c0:5e:08:fe:ea:6e:bb:77 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 69:c4:27:db:59:69:68:18:47:e2:52:17:0a:e0:e5:7f:ab:9d:ef:0f Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 73:97:82:ea:b4:04:16:6e:25:d4:82:3c:37:db:f8:a8:12:fb:cf:26 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid f8:16:51:3c:fd:1b:44:9f:2e:6b:28:a1:97:22:1f:b8:1f:51:4e:3c Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 90:e2:41:c2:11:41:8b:95:b1:a9:e0:9c:37:24:7e:84:9f:e4:be:a1 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid a2:af:24:0a:da:e8:67:79:c8:a8:50:b3:c7:46:ee:d9:f7:1b:16:78 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid c4:30:28:c5:d3:e3:08:0c:10:44:8b:2c:77:ba:24:53:97:60:bb:f9 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 30:a4:e6:4f:de:76:8a:fc:ed:5a:90:84:28:30:46:79:2c:29:15:70 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid f7:93:19:ef:df:c1:f5:20:fb:ac:85:55:2c:f2:d2:8f:5a:b9:ca:0b Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid b5:99:33:43:ac:a2:17:c5:08:ba:88:8c:a6:92:7e:26:b3:0f:87:a9 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid a8:e3:02:96:70:a6:8b:57:eb:ec:ef:cc:29:4e:91:74:9a:d4:92:38 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid ed:0d:c8:d6:2c:d3:13:29:d8:82:fe:2d:c3:fc:c5:10:d3:4d:bb:14 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 86:26:cb:1b:c5:54:b3:9f:bd:6b:ed:63:7f:b9:89:a9:80:f1:f4:8a Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 5e:8c:53:18:22:60:1d:56:71:d6:6a:a0:cc:64:a0:60:07:43:d5:a8 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid f8:92:0b:e9:08:a9:c5:d5:a0:fb:f3:9a:aa:98:a5:74:37:49:ad:9f Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 87:e3:bf:32:24:27:c1:40:5d:27:36:c3:81:e0:1d:1a:71:d4:a0:39 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid da:ed:64:74:14:9c:14:3c:ab:dd:99:a9:bd:5b:28:4d:8b:3c:c9:d8 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid e1:a0:5a:95:34:75:78:a7:ff:4d:cf:32:52:5d:f2:f8:2c:1a:e1:15 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 64:1d:f8:d5:0e:23:31:c2:29:b2:50:cb:32:f5:6d:f5:5c:8e:00:fa Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 7c:32:d4:85:fd:89:0a:66:b5:97:ce:86:f4:d5:26:a9:21:07:e8:3e Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 3e:df:29:0c:c1:f5:cc:73:2c:eb:3d:24:e1:7e:52:da:bd:27:e2:f0 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 34:4f:30:2d:25:69:31:91:ea:f7:73:5c:ab:f5:86:8d:37:82:40:ec Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid f9:27:b6:1b:0a:37:f3:c3:1a:fa:17:ec:2d:46:17:16:12:9d:0c:0e Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 88:a9:5a:ef:c0:84:fc:13:74:41:6b:b1:63:32:c2:cf:92:59:bb:3b Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 01:f0:33:4c:1a:a1:d9:ee:5b:7b:a9:de:43:bc:02:7d:57:09:33:fb Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for "CN=pfsense.local.lan" Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 6a:47:a2:67:c9:2e:2f:19:68:8b:9b:86:61:66:95:ed:c1:2c:13:00 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 5c:b8:69:fe:8d:ef:c1:ed:66:27:ee:b2:12:0f:72:1b:b8:0a:0e:04 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 4a:5c:75:22:aa:46:bf:a4:08:9d:39:97:4e:bd:b4:a3:60:f7:a0:1d Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid dd:bc:bd:86:9c:3f:07:ed:40:e3:1b:08:ef:ce:c4:d1:88:cd:3b:15 Feb 9 20:06:49 charon 71704 11[IKE] <22> received cert request for unknown ca with keyid 0e:ac:82:60:40:56:27:97:e5:25:13:fc:2a:e1:0a:53:95:59:e4:a4 Feb 9 20:06:49 charon 71704 11[ENC] <22> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Feb 9 20:06:49 charon 71704 11[ENC] <22> received fragment #2 of 3, reassembled fragmented IKE message (1462 bytes) Feb 9 20:06:49 charon 71704 11[ENC] <22> parsed IKE_AUTH request 1 [ EF(2/3) ] Feb 9 20:06:49 charon 71704 11[NET] <22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (572 bytes) Feb 9 20:06:49 charon 71704 11[MGR] IKE_SA (unnamed)[22] successfully checked out Feb 9 20:06:49 charon 71704 10[MGR] <22> checkin of IKE_SA successful Feb 9 20:06:49 charon 71704 10[MGR] <22> checkin IKE_SA (unnamed)[22] Feb 9 20:06:49 charon 71704 10[ENC] <22> received fragment #3 of 3, waiting for complete IKE message Feb 9 20:06:49 charon 71704 10[ENC] <22> parsed IKE_AUTH request 1 [ EF(3/3) ] Feb 9 20:06:49 charon 71704 10[NET] <22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (476 bytes) Feb 9 20:06:49 charon 71704 10[MGR] IKE_SA (unnamed)[22] successfully checked out Feb 9 20:06:49 charon 71704 12[MGR] <22> checkin of IKE_SA successful Feb 9 20:06:49 charon 71704 12[MGR] <22> checkin IKE_SA (unnamed)[22] Feb 9 20:06:49 charon 71704 12[ENC] <22> received fragment #1 of 3, waiting for complete IKE message Feb 9 20:06:49 charon 71704 12[ENC] <22> parsed IKE_AUTH request 1 [ EF(1/3) ] Feb 9 20:06:49 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:49 charon 71704 10[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:49 charon 71704 12[NET] <22> received packet: from $WORK_IP[4500] to $HOME_IP[4500] (572 bytes) Feb 9 20:06:49 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:49 charon 71704 11[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:49 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:49 charon 71704 12[MGR] IKE_SA (unnamed)[22] successfully checked out Feb 9 20:06:49 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:49 charon 71704 12[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i c1dec6d4df43d766_r Feb 9 20:06:49 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:49 charon 71704 01[NET] received packet: from $WORK_IP[4500] to $HOME_IP[4500] Feb 9 20:06:49 charon 71704 12[MGR] <22> checkin of IKE_SA successful Feb 9 20:06:49 charon 71704 12[MGR] <22> checkin IKE_SA (unnamed)[22] Feb 9 20:06:49 charon 71704 02[NET] sending packet: from $HOME_IP[500] to $WORK_IP[500] Feb 9 20:06:49 charon 71704 12[NET] <22> sending packet: from $HOME_IP[500] to $WORK_IP[500] (313 bytes) Feb 9 20:06:49 charon 71704 12[ENC] <22> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(CHDLESS_SUP) N(MULT_AUTH) ] Feb 9 20:06:49 charon 71704 12[IKE] <22> sending cert request for "CN=pfsense.local.lan" Feb 9 20:06:49 charon 71704 12[IKE] <22> remote host is behind NAT Feb 9 20:06:49 charon 71704 12[CFG] <22> selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 9 20:06:49 charon 71704 12[CFG] <22> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Feb 9 20:06:49 charon 71704 12[CFG] <22> received proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 9 20:06:49 charon 71704 12[CFG] <22> proposal matches Feb 9 20:06:49 charon 71704 12[CFG] <22> selecting proposal: Feb 9 20:06:49 charon 71704 12[IKE] <22> IKE_SA (unnamed)[22] state change: CREATED => CONNECTING Feb 9 20:06:49 charon 71704 12[IKE] <22> $WORK_IP is initiating an IKE_SA Feb 9 20:06:49 charon 71704 12[ENC] <22> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02 Feb 9 20:06:49 charon 71704 12[IKE] <22> received Vid-Initial-Contact vendor ID Feb 9 20:06:49 charon 71704 12[IKE] <22> received MS-Negotiation Discovery Capable vendor ID Feb 9 20:06:49 charon 71704 12[IKE] <22> received MS NT5 ISAKMPOAKLEY v9 vendor ID Feb 9 20:06:49 charon 71704 12[CFG] <22> found matching ike config: $HOME_IP...0.0.0.0/0, ::/0 with prio 1052 Feb 9 20:06:49 charon 71704 12[CFG] <22> candidate: $HOME_IP...0.0.0.0/0, ::/0, prio 1052 Feb 9 20:06:49 charon 71704 12[CFG] <22> looking for an IKEv2 config for $HOME_IP...$WORK_IP Feb 9 20:06:49 charon 71704 12[ENC] <22> parsed IKE_SA_INIT request 0 [ SA KE No N(FRAG_SUP) N(NATD_S_IP) N(NATD_D_IP) V V V V ] Feb 9 20:06:49 charon 71704 12[NET] <22> received packet: from $WORK_IP[500] to $HOME_IP[500] (376 bytes) Feb 9 20:06:49 charon 71704 12[MGR] created IKE_SA (unnamed)[22] Feb 9 20:06:49 charon 71704 12[MGR] checkout IKEv2 SA by message with SPIs 5ee9fe8f57c94e02_i 0000000000000000_r Feb 9 20:06:49 charon 71704 01[NET] waiting for data on sockets Feb 9 20:06:49 charon 71704 01[NET] received packet: from $WORK_IP[500] to $HOME_IP[500] -
@brswattt said in IKEv2 IPSEC VPN - Randomly stopped working:
@mamawe What is the benefit with and without? I'm not sure if I do need it exactly, I just want the client to connect after the lifetime expires, thats all.
The benefit depends on what your situation is.
Basically rekeying means replacing only the session keys while reauthentication means tearing down the IKE session and creating a new one from scratch. With IKEv2, rekeying can be done for Child SAs (ESP) as well as for the IKE SAs (IKE itself) by exchanging CREATE_CHILD_SA messages. IKEv1 supports only reauthentication of the IKE SA.
I personally haven't been in a situation where I needed reauthentication with IKEv2.
This page from the Strongswan Wiki may explain the topic better than I can do it.
-
@mamawe Regarding rekeying, if you follow the link to interoperability issues with Windows on the Strongswan Wiki page, you can find that at least with Windows 7 clients rekeying of the IKE SA does only work with DH group modp1024.
I don't know if that applies to your client.
-
@mamawe it's a Windows 10 machine. Definitely a Windows issue as my Android phone had no problem rekeying both phases.
-
@brswattt Looks like that bug reaches out to windows 10 as well. I triggered a manual rekey with
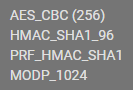 these algorithim settings (windows default), and I can rekey just fine.
these algorithim settings (windows default), and I can rekey just fine.go back to this:
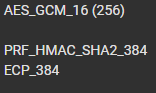 and rekey fails 100% of the time.
and rekey fails 100% of the time.I dont understand how in 2022 windows 10 is still forcing you to use less secure parameters
Even setting the Group to DH2 with the AESGCM256, it still doesn't work, so I'm forced to use AES/SHA1/DH2 which isn't secure at all. Thanks Microsoft.That algorithm works on Android though. Very stupid.
-
I added/changed it to AES/SHA256/DH14 in my router and client settings and rekey works! Way better than SHA1/DH2. I can live with this..