Unable to limit bandwidth on schedule
-
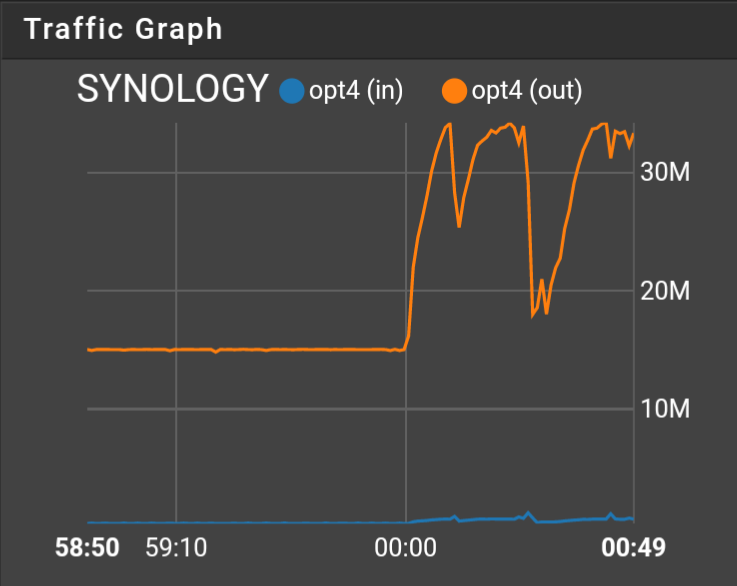
I am trying to limit bandwidth during the day between two VPN endpoints but it's not working. The link has a maximum speed of 30Mbps. Backup jobs are being sent over this link, but I want to limit the backup jobs to 15Mbps during the day so that other traffic can flow. I have created a schedule, a limiter, and a floating match rule. The schedule goes to active or inactive at the appropriate times, but the limiter doesn't have any effect unless I reset the state tables. How do I get the rule to follow the schedule like it should?
-
@blueh2o It's been a while since I messed with this, long enough I don't recall the issues. Can you post your limiter details? Are all times covered by a schedule?
In the end for our usage I found rsync has a bandwidth parameter and so ended up using that. Then on the both ends used a match rule to put the traffic in a low priority queue, with no limiter in pfSense. I know this doesn't answer your question but may be helpful.
param: --bwlimit=7000
This option allows you to specify the maximum transfer rate for the data sent over the socket, specified in units per second. The RATE value can be suffixed with a string to indicate a size multiplier, and may be a fractional value (e.g. "--bwlimit=1.5m"). If no suffix is specified, the value will be assumed to be in units of 1024 bytes (as if "K" or "KiB" had been appended). See the --max-size option for a description of all the available suffixes. A value of zero specifies no limit. -
-
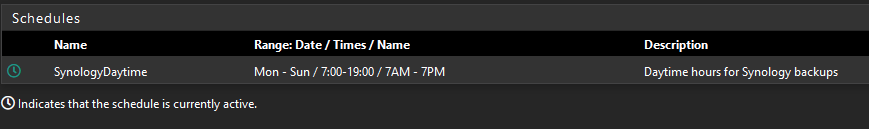
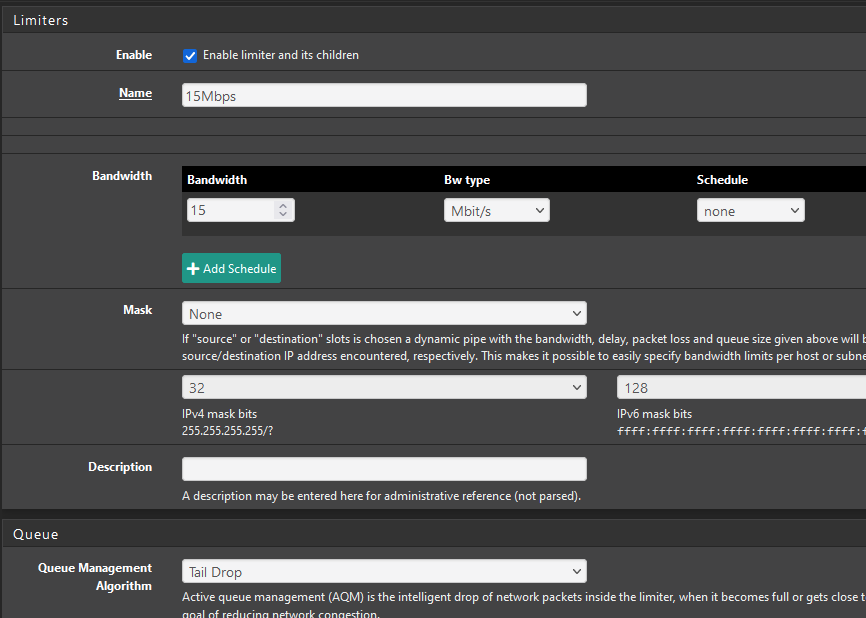
@blueh2o It looks like you have one schedule and the limiter has no schedule assigned. Per the docs , "If a limiter contains multiple bandwidth specifications, they must each use a different schedule. For example if the firewall has a “Work Day” schedule, then it must also have an “Off Hours” schedule that contains all of the time not included in “Work Day” for the second bandwidth specification."
It looks like you need to 1) create more schedules for 7p-11:59p and 12a-7a, then 2) click +Add Schedule on the limiter to add the two new limits and schedule.
https://docs.netgate.com/pfsense/en/latest/firewall/time-based-rules.html#defining-times-for-a-schedule
"The time cannot cross midnight on any day" -
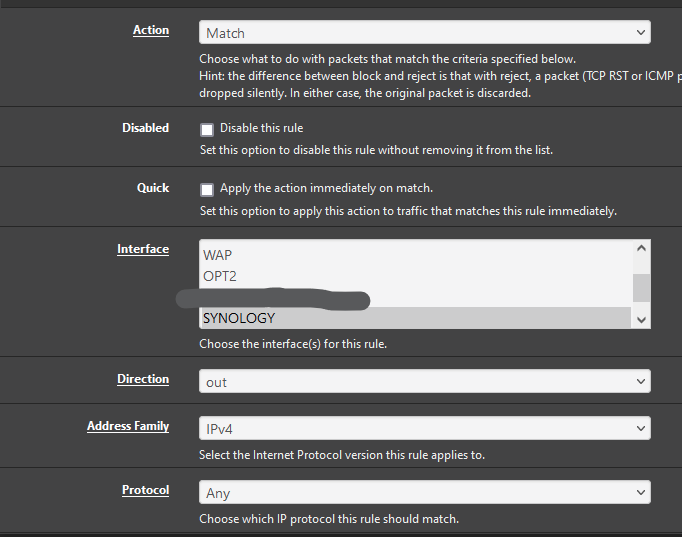
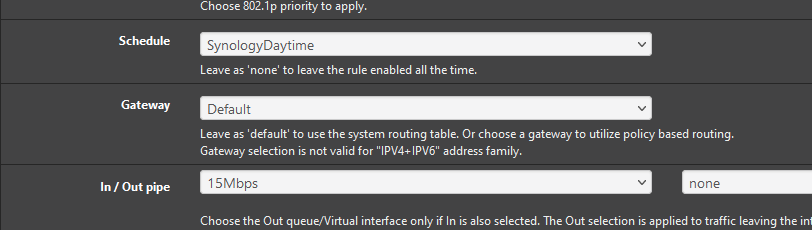
@steveits Am I doing this correctly?
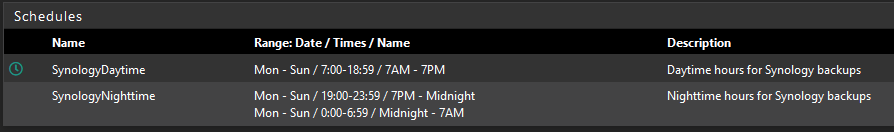
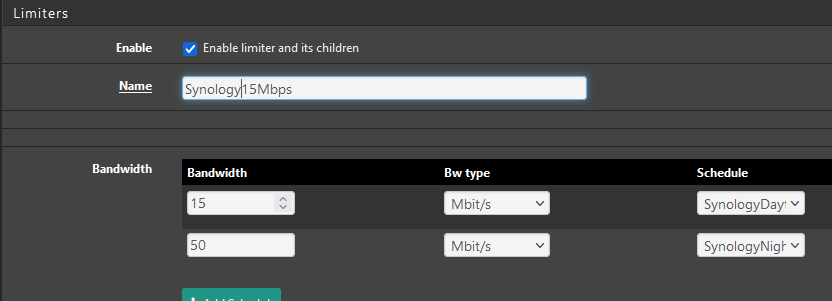
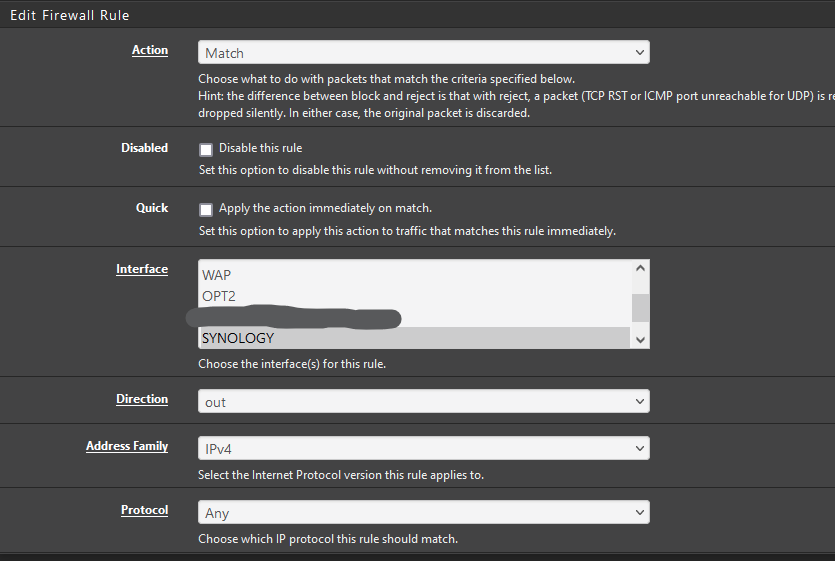
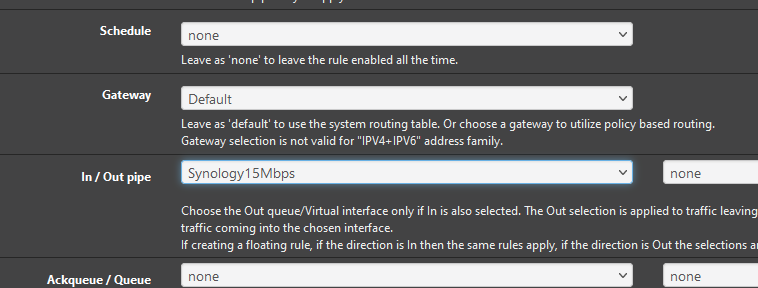
-
@blueh2o I think so. re: in/out pipes:
"In general, a limiter should mask the Source Address on Upload (In) limiters for LAN-type interfaces, and Destination Address on Download (Out) limiters on LAN-type interfaces. Similar to swapping the directionality of the limiters when applying to LAN and WAN, masking is swapped as well, so the same masked limiter set for In on LAN should be used for Out on WAN."
You mentioned a floating rule though? which I think are a bit different. Overall if it isn't being applied as you expect, check that the state is in the direction you think it is. For instance a limiter downloading from a web server needs to apply to the request going to the web server because the return is just a reply not a new connection, and "uses" the open state.
-
@steveits I checked previously with logging turned on to ensure the correct traffic is matched. For now I'll wait and see what happens at 18:59.
-
@steveits it worked. Thanks for the help.