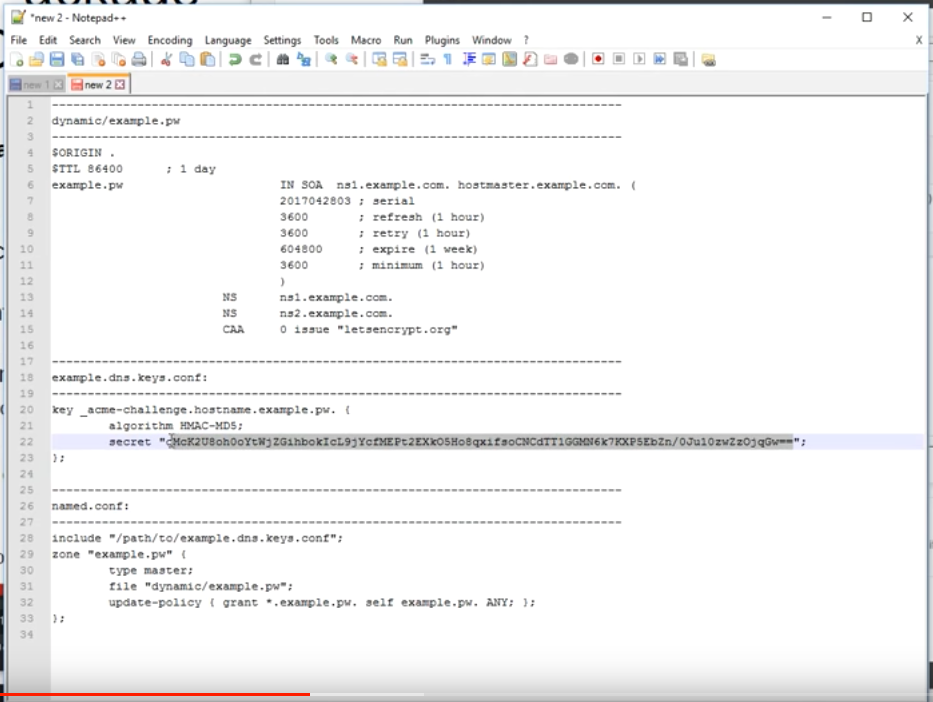
Creating WebGUI Certificate
-
@gertjan said in Creating WebGUI Certificate:
Two choices :
Add the IP in the SAN.
Visit your pfSense using https://mypfsense.local.lan/ - now the certificate matches the certificate, which is why you use a certificate the first place.
Every device you use to visit your pfSense GUI has to have the CA (chain) imported first.I had tried that, first, using both the host/FQDN (nolli.lan) then got the insult that it's not a real FQDN...then, tried the IP only to find Google wanting to resolve it and quickly switch to Duckduckgo which I use exclusively on all devices. I never visited any site using Opera as it's only for pfSense webGUI.
I gave up and registered a domain after that. Not sure why MacOS Keychain would not import the root CA certificate and instead placed the certificates (all three) in login. In fact, the original pfSense webGUI was in login as well. -
@nollipfsense said in Creating WebGUI Certificate:
atest Opera exclusively for pfSense that does not allow the root certificate to be imported...it relied on the MacOS and that also would not import that certificate.
What are you trying to import... You sure and the hell can import trusted CA.. I don't care what freaking browser or OS your using.. Failure to be able to do that would be the death of that OS or browser.. Nobody would use it that could say who or not they trust or don't trust..
My guess is you were trying to install the cert vs the CA as trusted..
-
@johnpoz said in Creating WebGUI Certificate:
@nollipfsense said in Creating WebGUI Certificate:
atest Opera exclusively for pfSense that does not allow the root certificate to be imported...it relied on the MacOS and that also would not import that certificate.
What are you trying to import... You sure and the hell can import trusted CA.. I don't care what freaking browser or OS your using.. Failure to be able to do that would be the death of that OS or browser.. Nobody would use it that could say who or not they trust or don't trust..
My guess is you were trying to install the cert vs the CA as trusted..
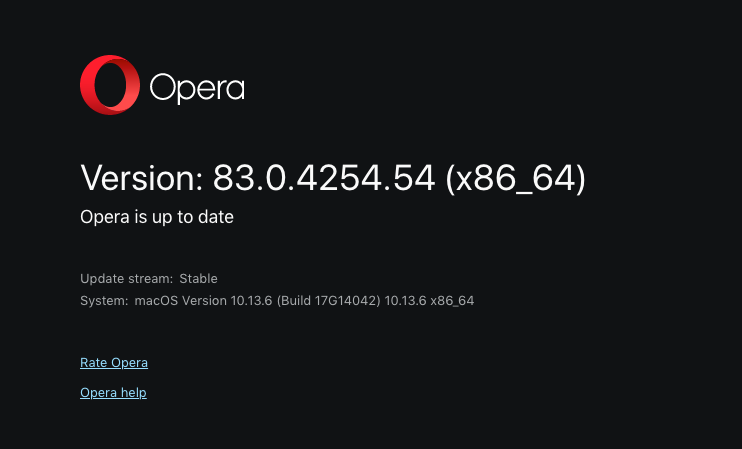
Below is Opera showing it's up-to-date and below that is a screen shot showing manage certificate (arrow point)...when one clicks on that, on a Mac, it opens Keychain Access...there is no import certificate button on that Opera page. Hope someone with a Mac can replicate; to make sure mine was not installed properly when I drag it to the application folder. Also, if one import the certificate into Keychain, it places it under login for the user and not in the root. I tried several times, even tried dragging it to root...no luck, would not go. Note: the certificates were set to always trust after importing into Keychain.
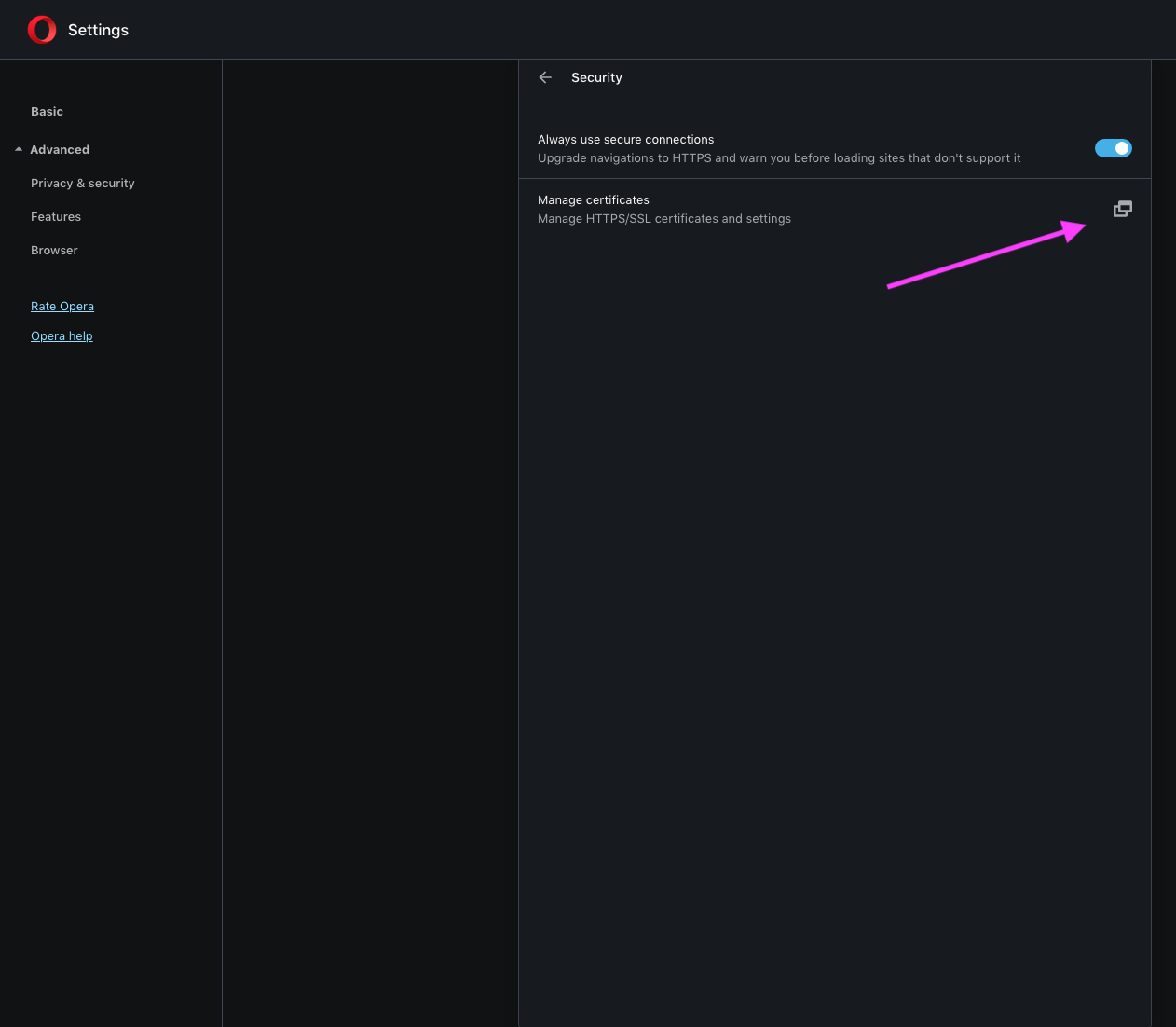
-
@nollipfsense said in Creating WebGUI Certificate:
the certificates were set to always trust after importing into Keychain.
The CA cert.. wasn't this all gone over back in 2019
https://forum.netgate.com/topic/144141/opera-not-accepting-certificate-solved
-
@johnpoz said in Creating WebGUI Certificate:
@nollipfsense said in Creating WebGUI Certificate:
the certificates were set to always trust after importing into Keychain.
The CA cert.. wasn't this all gone over back in 2019
https://forum.netgate.com/topic/144141/opera-not-accepting-certificate-solved
John, it seems that I have been a fool for awhile...haven't learn jack sh*t. I had looked earlier in Firefox and that allows one to import the certificate with a dialog box just as you showed in your Opera 60 in that thread; however, there is no such dialog box in Opera. I might use that other browser that I had mentioned and used in that thread.
-
@nollipfsense I do not have mac to play with.. But I could for sure install opera whatever the current version is on my windows box. Doesn't matter if the browser stores CA it trusts in its own store, the store for the OS.. But you need to trust the CA that signed the cert, be that public be that one you created yourself..
Along with any intermediate ca's etc. that you might of created, etc. I don't really see the point of doing intermediate CA on a home setup, on really the only reason to do any of it locally https is to stop the browser from complaining.
I mean who what would be sniffing your own local traffic over your own secure network in the first place, so what does it matter if the traffic is https or http.. Problem with http only these days is more likely your browser will balk at you that its not "secure" ;)
So personally I don't see the point of going through the extra steps of creating an intermediate CA, etc. Just create your local CA, create/sign whatever cert you want for your service with its fqdn as the CN, as the SAN and add any other SANs you might want to access the service with be it rfc1918 IP or some other fqdn... This should stop your browser from complaining..
Here I just installed Opera.. version 83.0.4254.47
Clickly clicky and there you go my home CA is now trusted.. As you can see I went to pfsense IP and error about not trusted. Install my CA and now trusted.
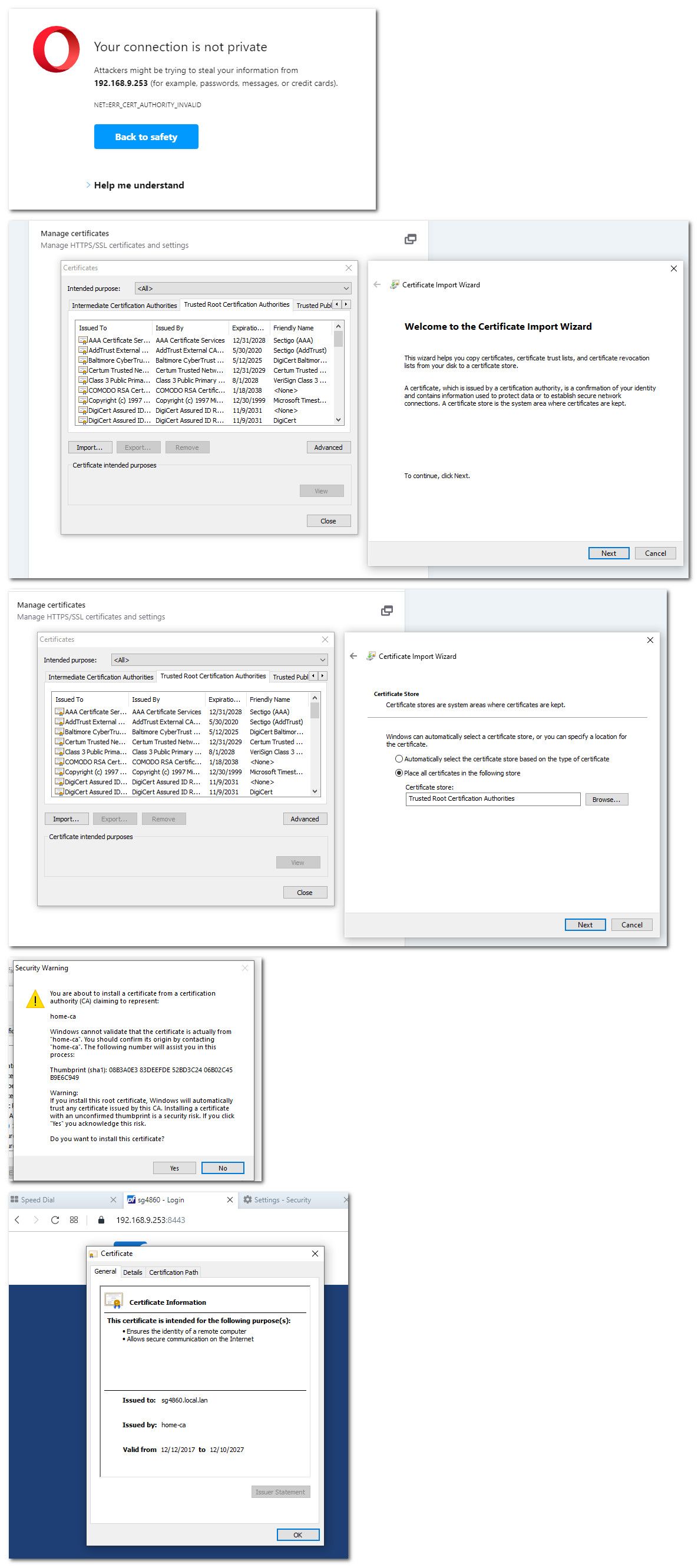
That took all of like 20 seconds to do - including the download and install of the browser.
edit: then another 10 seconds to uninstall it ;) And set firefox to be default browser again - wtf, it never asked me if opera should be default, it just did it.. Ugggh that is not nice!
-
@johnpoz John, I tried again...not sure what I am doing wrong...I give up again. I have the root CA in system for all users, and the intermediate CA as well as the certificate in user login...all marked trusted in Keychain. As you can see, the certificate marked in the screen shot.
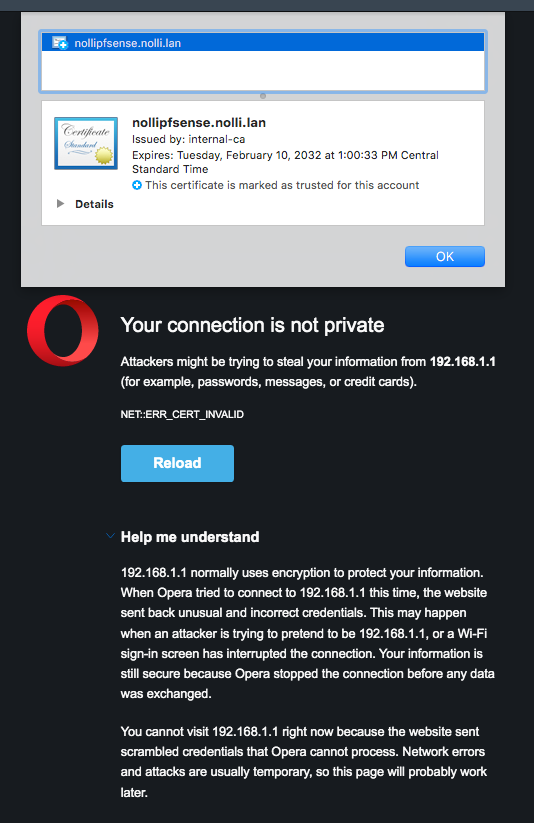
-
@johnpoz This time I know what's the problem...it's embarrassing I forgot to change the port to 443 or 4443 as I had it on port 35; so, I am locked out as I don't think restarting webGUI from the console CLI will resolve...gone take a nap. Download 2.6rc later.
-
@nollipfsense That is not a CA cert that is a cert.. And if you just issued a cert that is good til 2032 no browser is going to take it.. They can only be good for like 1 year now.. Or 398 days..
You need to install the internal-ca cert and trust it.. But even if you did browser not going to like that cert since its valid too long.. You would have to have issued it before the new limits were put in..
"after September 1, 2020 with a validity period greater than 398 days will not be trusted by Apple’s Safari browser and iOS/iPadOS/watchOS/tvOS devices."
"Thus, effective Sept. 1, 2020, Mozilla, Google, and Apple will no longer trust any newly issued certificates with a valid lifespan of longer than 398 days."
So for yoru browser to trust that cert good until 2032, it would have had to been issued quite some time ago.. Which you could prob trick by dating your system you have your CA on, etc. Back into 2019 or something.
-
@johnpoz said in Creating WebGUI Certificate:
@nollipfsense That is not a CA cert that is a cert.. And if you just issued a cert that is good til 2032 no browser is going to take it.. They can only be good for like 1 year now.. Or 398 days..
You need to install the internal-ca cert and trust it.. But even if you did browser not going to like that cert since its valid too long.. You would have to have issued it before the new limits were put in..
"after September 1, 2020 with a validity period greater than 398 days will not be trusted by Apple’s Safari browser and iOS/iPadOS/watchOS/tvOS devices."
"Thus, effective Sept. 1, 2020, Mozilla, Google, and Apple will no longer trust any newly issued certificates with a valid lifespan of longer than 398 days."
So for yoru browser to trust that cert good until 2032, it would have had to been issued quite some time ago.. Which you could prob trick by dating your system you have your CA on, etc. Back into 2019 or something.
Okay, will make the change since I'll need to reconfigure that. The fastest way to resolve the lockout was to reset to the factory then restore from backup. Now, just need the add the item that wasn't backed up since the last backup.
Didn't planned to have this sort of fun today...LOL!
-
@johnpoz I finally graduated from the University of Slow Learners after three years of repeating webGUI certificate class...wipe of sweat.