NAT Outbound not working between VLANs
-
Hi,
I have device A in the main LAN (192.168.10.4) and I want to connect to device B in VLAN IOT (192.168.30.97) and for device B to think this request came from the same subnet,
So I created the following NAT Outbound:
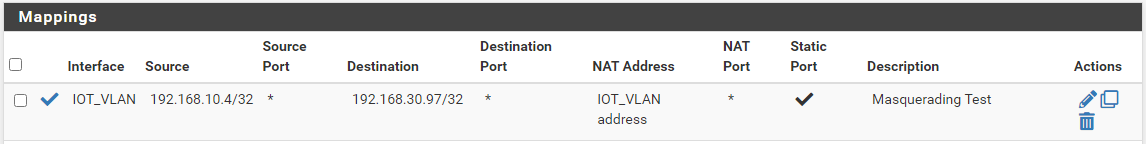
I reset the Firewall States, but this doesn't seem to work at all -
In States I see this:

And in Capture Packets I see this:
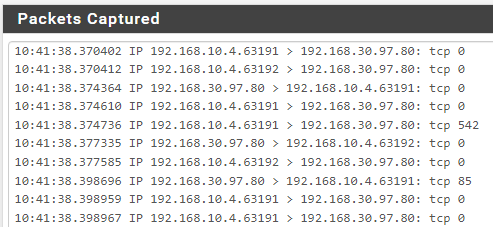
While I was expecting to see
LAN 192.168.10.4 > 192.168.30.97
IOT_VLAN 192.168.30.97 > 192.168.30.1 (192.168.10.4)Don't know if it matter much, but my NAT settings are:
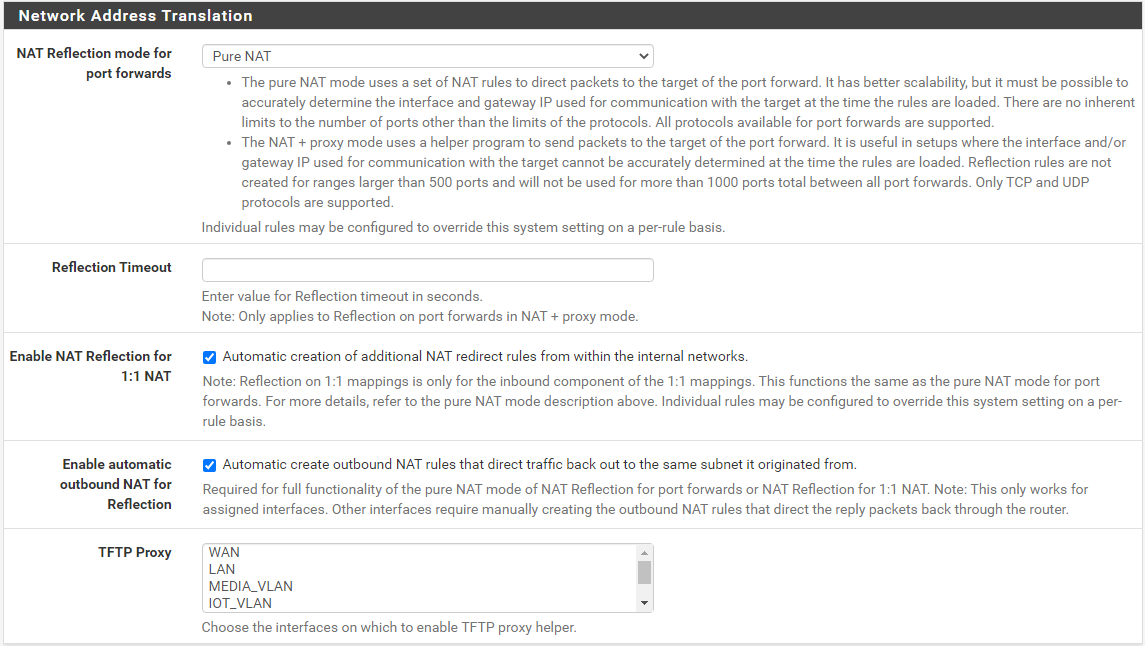
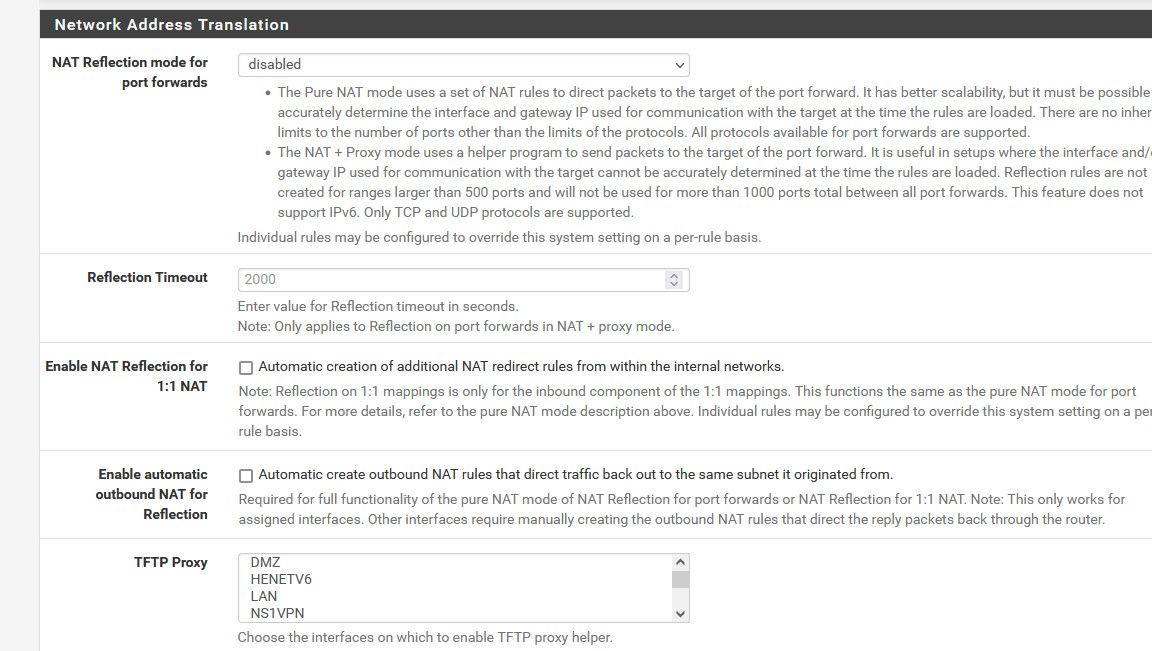
I tried to disable NAT Reflection but it didn't help.I played with it so much but nothing worked for me,
I would really like your help and expertise in this area. -
@idan37s can we see your whole outbound nat setup.. I have done this multiple times..
What version of pfsense are you running?
Example..
lan is 192.168.9/24, dmz is 192.168.3/24
If I want to make it look like connection is coming from the pfsense dmz IP 192.168.3.253 when talking to something in the dmz from my lan.
You can see my mapping and using hybrid and my nat. And then pinging you see in the state table its natted.
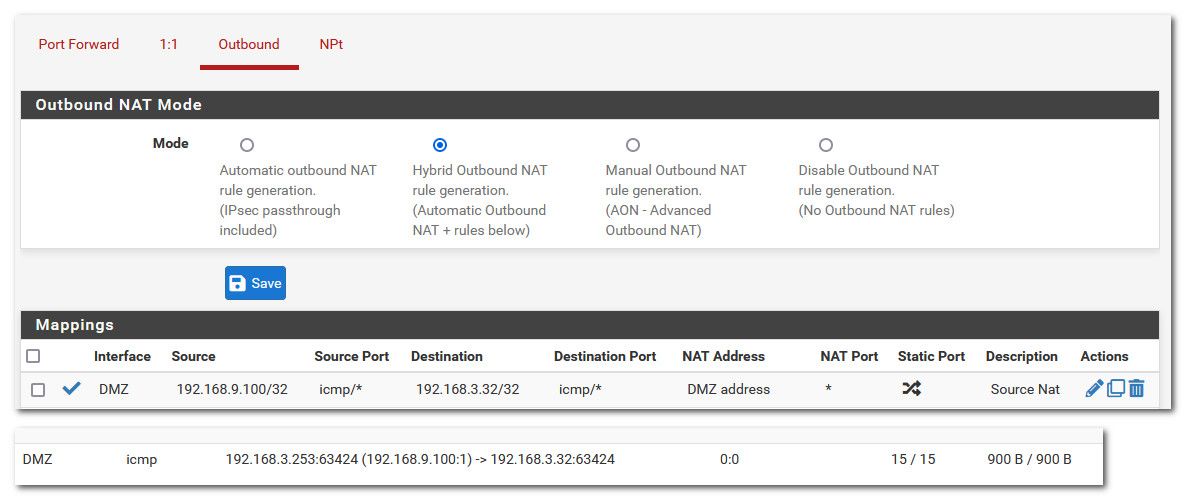
What interface did you sniff on? If you sniffed on the source interface that would be correct..
Here got constant ping going.. First sniff on the source interface (lan) and then on the dest network (dmz)
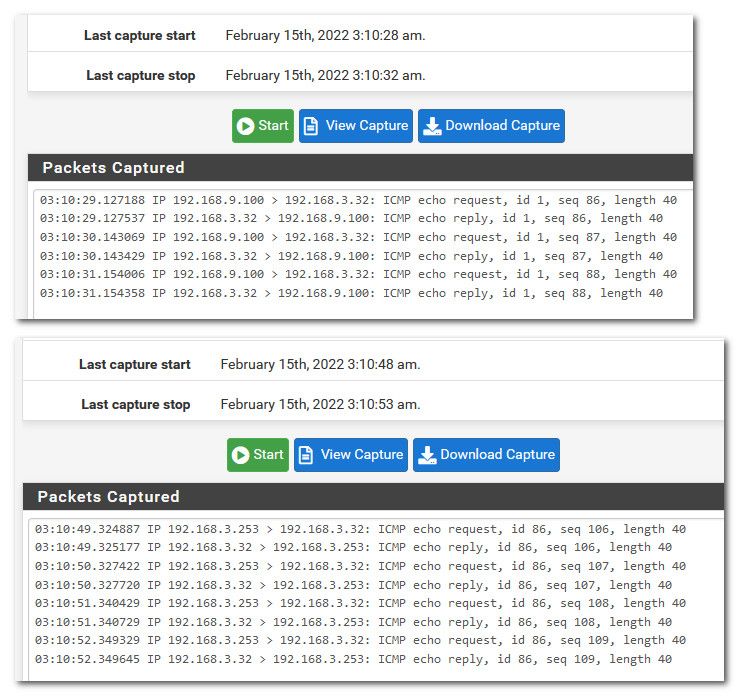
-
I'm running PfSense v2.5.2-RELEASE
I sniffed the packet capture on the IOT VLAN on the IP 196.168.30.97
Here is my full NAT Outbound:
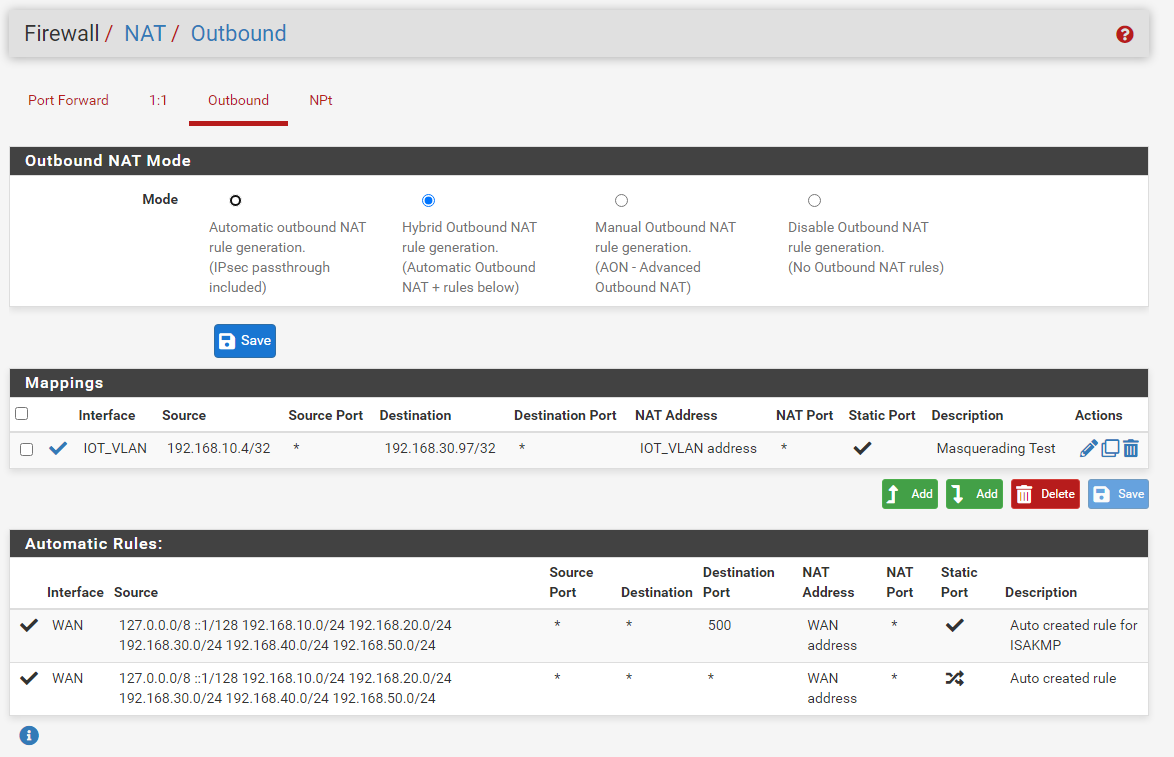
What do you see in the States when you make the connection that uses your NAT Outbound?
And what are your NAT settings under the "System \ Advanced \ Firewall & NAT"?I'm going crazy over this as it should work but for some reason doesn't no matter what I tried.
-
@idan37s I posted my state you can see it doing the nat in that state
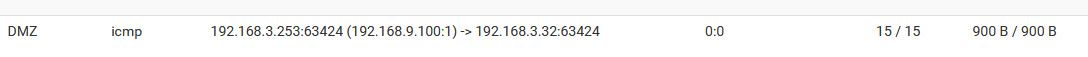
What is odd is your outbound state - there should only be the one state..
Here are all my icmp states.. You can see the state coming in from my source, and then when going out its the nat on the dmz interface.
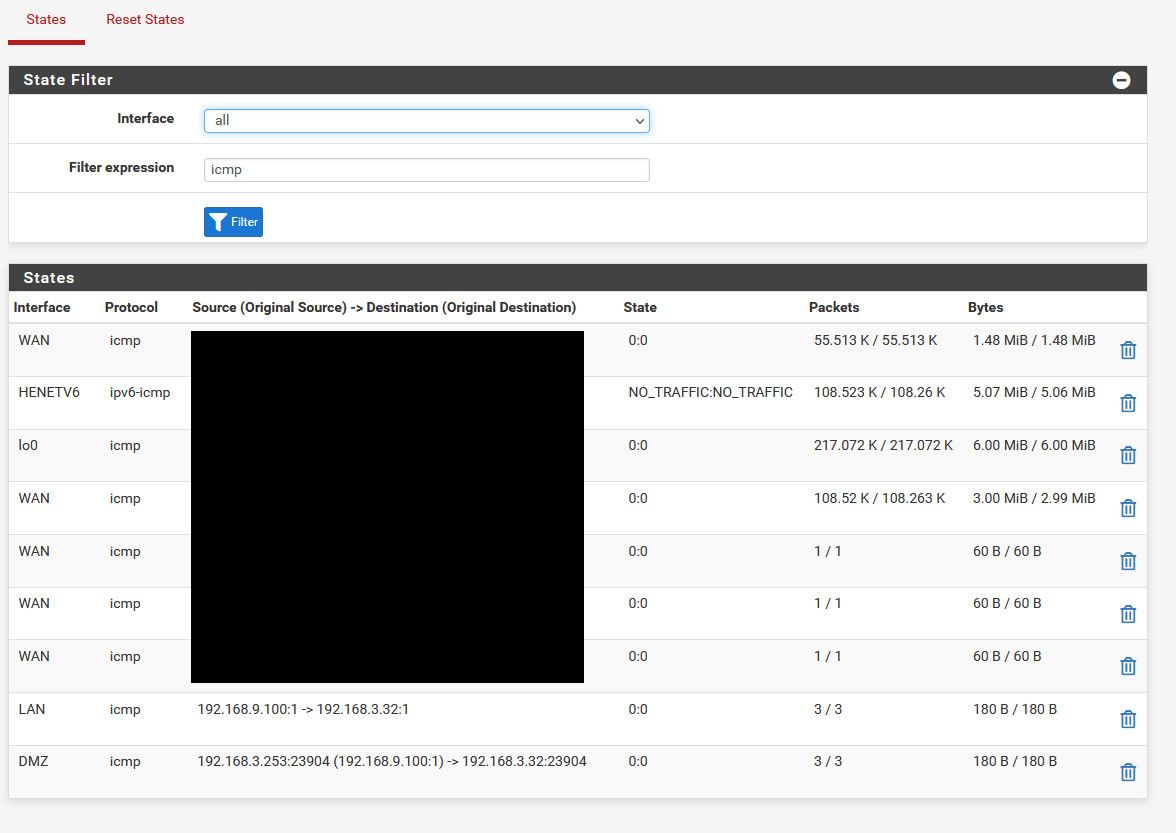
I concur the nat setting shouldn't matter but here are mine
Do you have floating rules? That allow this traffic? That is what I think would cause that oubound state on your iot interface.
-
I have disabled the NAT Reflection so my NAT settings are just like yours now, it didn't help though.
My Firewall Rules for LAN are allow all, nothing is blocked,
And for VLAN_IOT i have allow all for only test purposes for the IP related to the NAT Outbound:
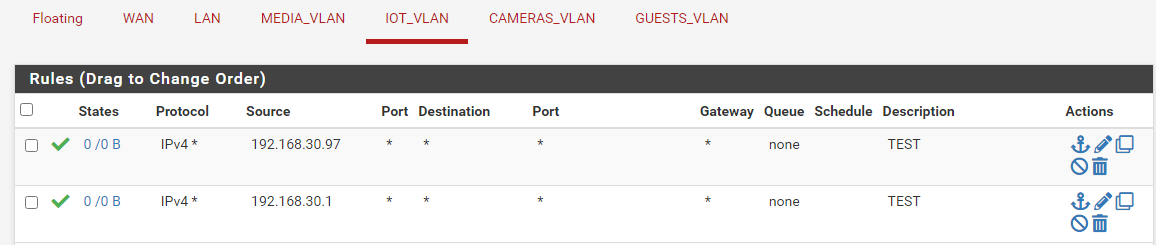
And of curse it still doesn't work for some reason.
Which PfSense version are you using?
And which outbound state did you meant?
I saw you have also 2 states regarding that traffic, one for each interface,
Like mine just that yours have the source changed by pfsense in the DMZ interface and mine didn't do that in IOT_VLAN interface, which is unclear why. -
@idan37s I am on 22.01, but have done this multiple times in the past on multiple previous versions. But since they moved to plus, I can not say specific done it on version 2.5.2
Yeah your state showing no nat was the one talking about.. You sure you cleared all your previous states?
Its odd indeed, this should be really clickly clicky to get working, like I have said done this multiple times in the past to show people how to do it.. Comes in handy talking to say a device that has no gateway set like a camera or something.. Or some old wifi router being used as AP that doesn't allow for setting a gateway on the lan.
-
@johnpoz
I just updated to PfSense 2.6 in hope there was some bug related to this that was fixed,
It's so frustrating, still not working. -
Problem Solved!
So for the people who might encounter it and see this post,
It seems that for some reason pfBlockerNG is causing the NAT Outbound to not work, not sure why,
But once I disabled pfBlockerNG everything worked as it should.@johnpoz Thanks a lot for you help, I really appreciate it!
-
@idan37s how would pfblocker have anything to do with it?? That doesn't make any sense..
I use pfblockerng for some alias, etc. I don't have it doing any sort of auto rules or anything.. But I am just not getting how pfblocker could have anything to do with your outbound nat rules??
-
@johnpoz
I'm not sure either,
I'm trying to debug it now to see which setting specifically is causing that.
The weird thing is that only new NAT Outbound rules don't work when pfBlockerNG is enabled.
If I disable and then enable pfBlockerNG then the existing NAT Outbound rules are working as expected, but then if I add a new NAT Outbound rule it doesn't work.I will update if I will find any conclusive reason to why it happens.
Note: In all my tests after each change I'm resetting the States.
-
@idan37s yeah if you can find something that can be duplicated, we for sure should put in a bug report..
Happy to try and duplicated here.. But I currently have pfblocker enabled and creating aliases, etc. and not having any issues. But I just don't see what it could be doing that would have any effect other than if you were having it create actual firewall rules maybe??
-
@johnpoz
The Geo IP and the IP block part in pfBlockerNG creates Floating FW Rules for me on the WAN interface,
Logically it shouldn't be the cause of the issue:
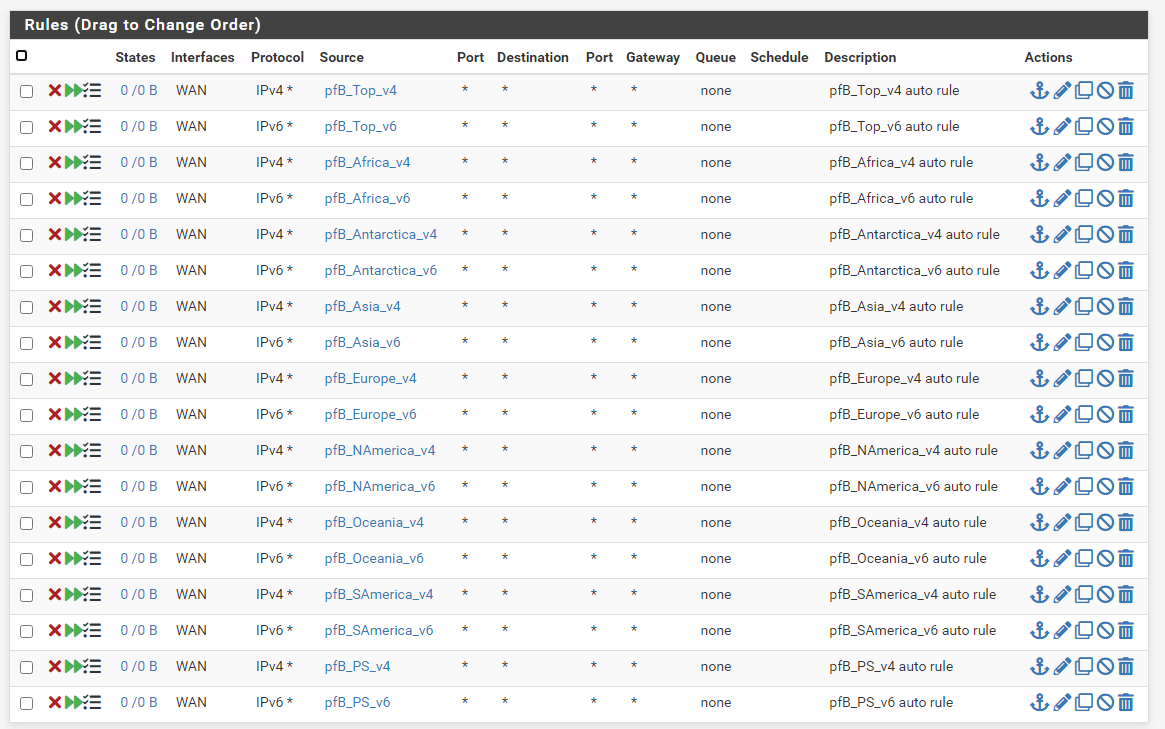
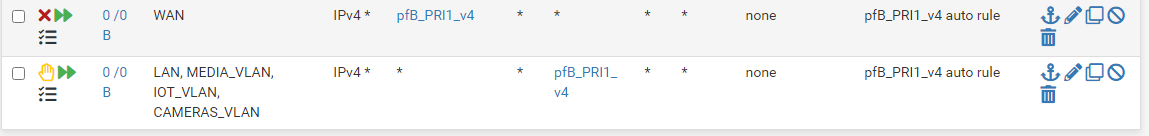
-
@idan37s yeah nothing on wan should have anything to do with your outbound nat on your iot vlan, etc.
But even that last reject rule there that has your lan and iot vlan in it.. Not sure how that would effect a nat, nats are looked at before rules, even in floating.. But you were still able to access - just not being natted..
Very strange indeed..
-
@johnpoz
It's not the Floating rules, I disabled them and saw no change.
It seems like this is happened to a few others and not a new issue,
And like me, when they disabled and enabled PfBlockerNG everything start to work.https://www.reddit.com/r/PFSENSE/comments/iiexur/nat_reflection_stopped_working_after_updating_to/
-
@idan37s I wonder if its just pfblocker keeping or causing an issue with the reload of the rules..
So for example if I look in the raw rules jsut my nats when I create that outbound I see it
[22.01-RELEASE][admin@sg4860.local.lan]/root: pfctl -sn no nat proto carp all nat-anchor "natearly/*" all nat-anchor "natrules/*" all nat on igb3 inet proto icmp from 192.168.9.100 to 192.168.3.32 -> 192.168.3.253 port 1024:65535 -
@johnpoz
After testing it seems that when PfBlockerNG is enabled this list (from your command) is being updated only after you disable PfBlockerNG.Can we open a bug on it somehow?
-
@idan37s said in NAT Outbound not working between VLANs:
when PfBlockerNG is enabled
When what exactly is enabled - like I said I am using it and not having the problem.
Are you using DNSBL? I am not.. You have it doing permit firewall rules? On floating?
-
I have DNSBL (unbound mode), GeoIP block (inbound) and IP block (inbound and outbound) all enabled in PfBlockerNG.
The GeoIP and IP Block are creating Floating Rules in the FW on the WAN interface (as seen in one of the screenshot above).- When PfBlockerNG itself is enabled, then new rules I add in NAT Outbound do not show up in the list I get from the command "pfctl -sn", and those new rules don't work.
- Once I disable PfBlockerNG (and doing only that, nothing else) the new NAT Outbound rules I added now show up in the list form the command, and they do work.
- I can now re-enable PfBlockerNG and the new rules will still be in the list from the command and everything will work as expected.
So as you said, it seems like PfBlockerNG is preventing an update on those rules list or something like that.
-
@idan37s turn off just the dnsbl stuff and or the firewall aspect, and leave pfblocker enabled.
-
I tried that,
I disabled DNSBL, IP Block, Disabled all the FW Floating Rules,
But the NAT Outbound rules still didn't work.Only disabling the PfBlockerNG itself made it work.