Upgrade 2.5.2 to 2.6.0, upgrade success, Limiters not passing
-
@pooperman If you have multiple gateways make sure the default is set as WAN there.
If it's set as automatic and you have internal gateways that can become the default route which is obviously invalid.
Most people should not have internal gateways there. You would only have that if you have an internal router with other subnets behind it.Steve
-
@tohil Can we see that limiter config from the config file?
-
@stephenw10
I have one WAN gateway from my provider, but its not default, its uses for only vpn connection. And second gateway is a VPN one, which is marked as default.
It works on 2.5.2, its works on 2.6.0, but only after reapply gateway settings by hand. But for reboot it has no internet at all. -
@pooperman Hmm, interesting. What is the default route after a reboot before you reapply the gateway? Does the VPN come up correctly?
Steve
-
@stephenw10
How I can see default route?
VPN come up correctly after reboot. Its receive ip address and marks green on dashboard.
Another thing I noticed is that after rebooting the default gateway has no globe icon. After reapply gateways settings by hand it appears.
Also its possible to restart VPN connection instead of reapply gateways settings. After that internet is also has up. -
-
It sounds like it might be trying to apply the default route before gateway is valid for some reason.
Have you editing the OpenVPN gateway at all? To set a different monitoring IP for example.
Steve
-
@bingo600
Interesting. It is no default route at all after reboot.@stephenw10
No. I did not edit OpenVPN gateway. -
Try editing and saving the OpenVPN gateway without making any changes. It will create the gateway entry in the config which will mean it's present before it connects. Though the route will still be invalid.
Steve
-
@stephenw10
No. There is no effect. Still have not internet connection after reboot. -
@steveits said in upgrade 2.5.2 to 2.6.0, upgrade success, no internet conection:
That should just remove the rule on WAN to block inbound traffic from bogons.
That's also not something I would want anyone else to do. Especially if you were behind a CGNAT...
-
@pooperman Then I would check the boot and routing log for errors.
You might also check the OpenVPN log since that can often try to set a new default route when it connects.
Steve
-
<dnshaper> <queue> <name>PublicWLANIn</name> <number>1</number> <qlimit></qlimit> <plr></plr> <description></description> <bandwidth> <item> <bw>15</bw> <burst></burst> <bwscale>Mb</bwscale> <bwsched>none</bwsched> </item> </bandwidth> <enabled>on</enabled> <buckets></buckets> <mask>none</mask> <maskbits></maskbits> <maskbitsv6></maskbitsv6> <delay>0</delay> <sched>fifo</sched> <aqm>droptail</aqm> <ecn></ecn> </queue> <queue> <name>PublicWLANOut</name> <number>2</number> <qlimit></qlimit> <plr></plr> <description></description> <bandwidth> <item> <bw>30</bw> <burst></burst> <bwscale>Mb</bwscale> <bwsched>none</bwsched> </item> </bandwidth> <enabled>on</enabled> <buckets></buckets> <mask>none</mask> <maskbits></maskbits> <maskbitsv6></maskbitsv6> <delay>0</delay> <sched>fifo</sched> <aqm>droptail</aqm> <ecn></ecn> </queue> <queue> <name>CHFreeWiFiIn</name> <number>3</number> <qlimit></qlimit> <plr></plr> <description></description> <bandwidth> <item> <bw>5</bw> <burst></burst> <bwscale>Mb</bwscale> <bwsched>none</bwsched> </item> </bandwidth> <enabled>on</enabled> <buckets></buckets> <mask>none</mask> <maskbits></maskbits> <maskbitsv6></maskbitsv6> <delay>0</delay> <sched>wf2q+</sched> <aqm>droptail</aqm> <ecn></ecn> </queue> <queue> <name>CHFreeWiFiOut</name> <number>4</number> <qlimit></qlimit> <plr></plr> <description></description> <bandwidth> <item> <bw>15</bw> <burst></burst> <bwscale>Mb</bwscale> <bwsched>none</bwsched> </item> </bandwidth> <enabled>on</enabled> <buckets></buckets> <mask>none</mask> <maskbits></maskbits> <maskbitsv6></maskbitsv6> <delay>0</delay> <sched>wf2q+</sched> <aqm>droptail</aqm> <ecn></ecn> </queue> </dnshaper> -
So all traffic using those Limiter pipes is failing or just the FreeWIFI?
-
@tohil said in upgrade 2.5.2 to 2.6.0, upgrade success, no internet conection:
Same here in my environment. Updated from 2.5.2 to 22.1
I have two networks with limiters on rules for these interfaces.all traffic which should pass these rules are not working until I remove the In / Out pipe limiters.
I'm having the same issue. The limiters have been working fine with v2.5.2.
I even tried a clean install of this v2.6.0 on different devices traffic passes fine but when I activate any rule with In/Out pipes define, traffic stops flowing and there's no internet access.I reinstalled v2.5.2 and everything works fine and limiters working as before.
I strongly believe this is a bug with the Limiters feature and it's to some degree similar to this one.
-
@stephenw10 all
-
And no unusual config there, just the default settings?
-
You see anything in Diag > Limiter Info when it's failing?
Works as expected and shows as expected for me in a simple test case:
Limiters: 00001: 50.000 Mbit/s 0 ms burst 0 q131073 50 sl. 0 flows (1 buckets) sched 65537 weight 0 lmax 0 pri 0 droptail sched 65537 type FIFO flags 0x0 0 buckets 1 active BKT Prot ___Source IP/port____ ____Dest. IP/port____ Tot_pkt/bytes Pkt/Byte Drp 0 ip 0.0.0.0/0 0.0.0.0/0 34 1768 0 0 0 00002: 50.000 Mbit/s 0 ms burst 0 q131074 50 sl. 0 flows (1 buckets) sched 65538 weight 0 lmax 0 pri 0 droptail sched 65538 type FIFO flags 0x0 0 buckets 1 active 0 ip 0.0.0.0/0 0.0.0.0/0 71499 107245606 43 64500 0 Schedulers: 00001: 50.000 Mbit/s 0 ms burst 0 sched 1 type WF2Q+ flags 0x0 0 buckets 0 active 00002: 50.000 Mbit/s 0 ms burst 0 sched 2 type WF2Q+ flags 0x0 0 buckets 0 active -
I cannot post, because akismet anti-spam engine...
-
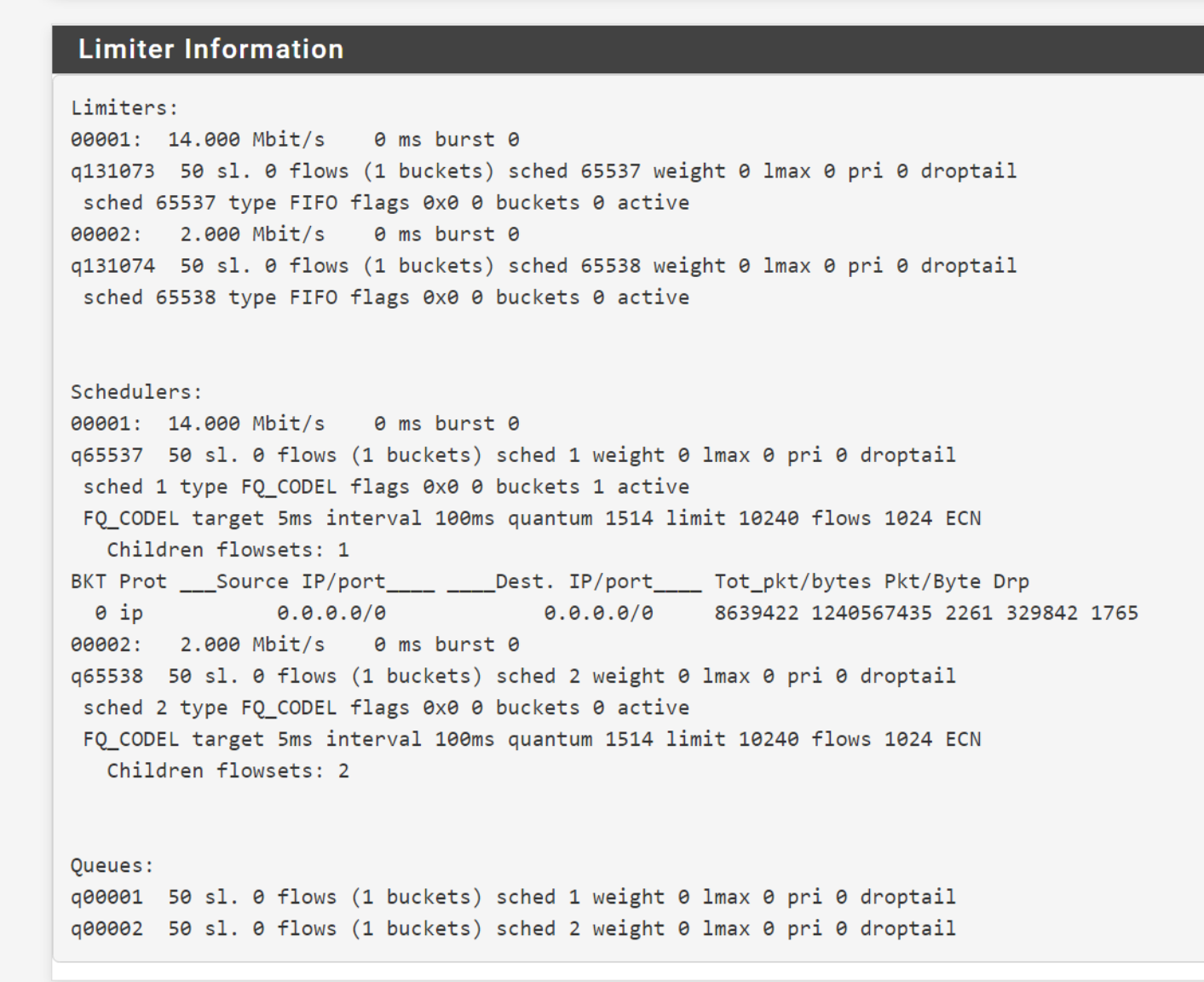
Seems like its doing some unknown packet transfer bug on a idle connection.