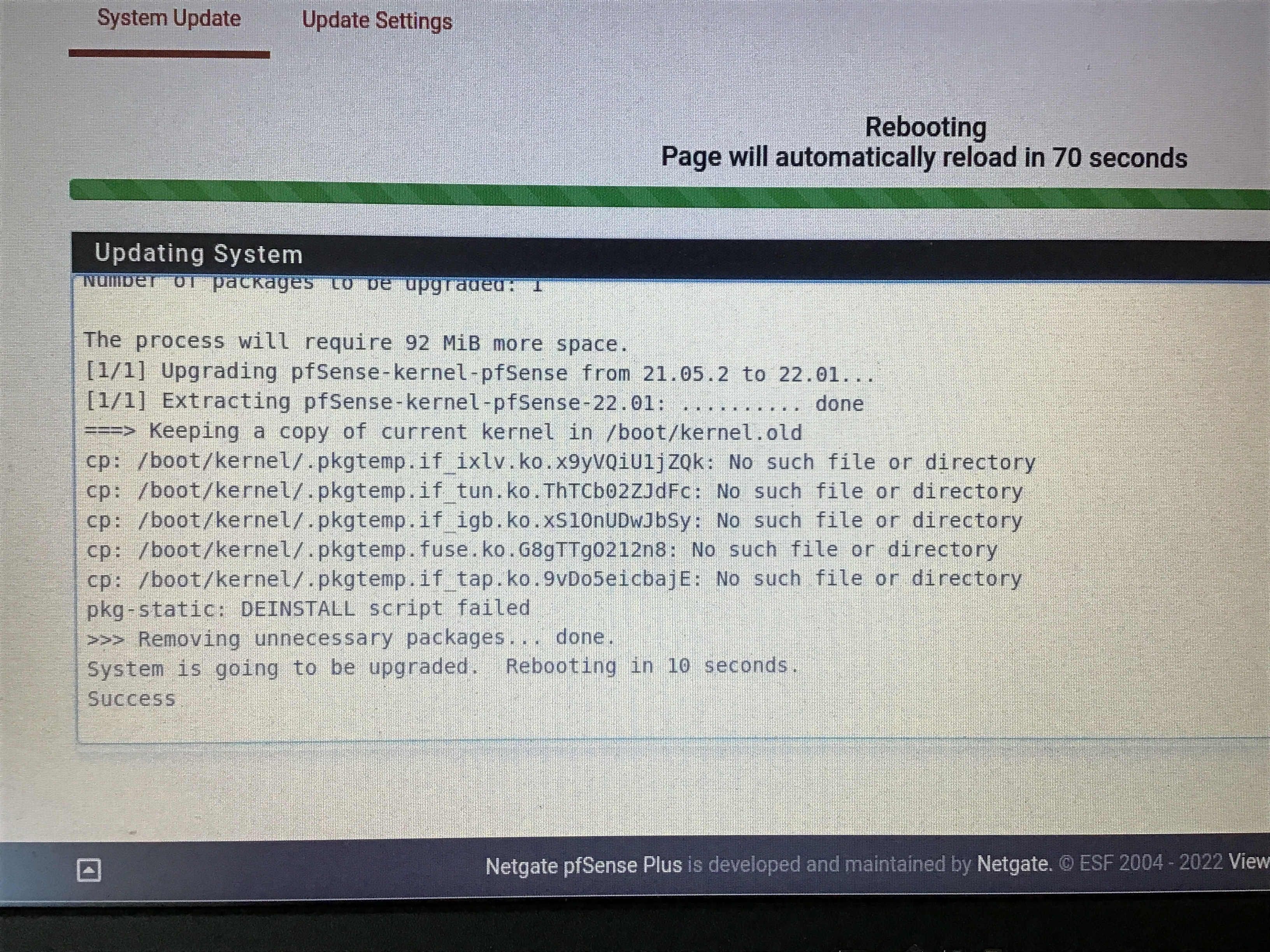
Upgrade 21.05.2 to 22.01 - no VLAN internet conection
-
I've been following the other threads regarding no internet access after upgrading to 22.01 and wanted to share my experience in hope that it might provide some additional clues as to what is going on.
Upgrade to 22.01 on a SG-5100. Install completed with the following errors (packages were not updated prior to upgrade):
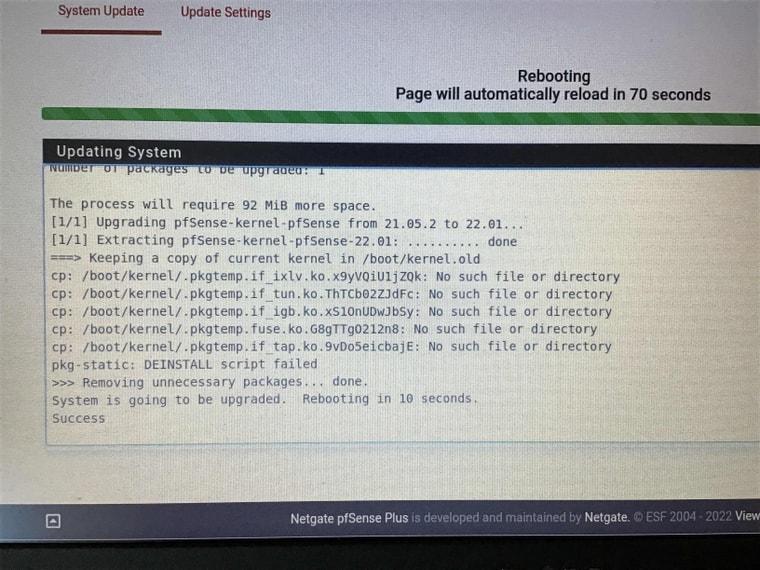
- It rebooted fine and established a VPN connection without issue.
- Internal network and VLANs out through the VPN all worked normal. However the VLANs routed to the WAN had no internet access. I could ping the gateway but no external sites.
- A port configured with WAN access (direct WAN access, not through VPN and not configured as a VLAN) worked as expected.
- No limiters are in use.
- Tried a fresh install from image with the same known good config file running fine on 21.05.2 and got the same connectivity results.
After messing with it for several days I had to get things back up so I reverted back to 21.05.2 and all is running normally.
-
Those errors shown are expected, nothing that will cause an issue.
If you can ping the WAN side gateway but nothing beyond that it's probably an outbound NAT issue. I wouldn't have expected anything to change between 21.05.2 and 22.01 there though.
Do you have Outbound NAT in automatic mode?Steve
-
@stephenw10 NAT is set to manual mode. I also tried Hybrid after the upgrade but saw no change.
-
Is there a rule being generated for the subnet you were testing from?
-
In Hybrid, automatic rules were created which were redundant with my manually created rules to the WAN. The non working VLANs had mappings in place to WAN in either mode (manual or hybrid).
-
Hmm, is your VPN set as the default system gateway?
-
Default gateway is the WAN
-
Hmm, that's.... weird!
Are the failing connections policy routed to WAN or just using the default route?
Is there a valid default route shown? That would also prevent connecting to anything beyond the gateway, which is in a directly connected subnet.
Steve
-
Have you limiters on that VLAN? Try to turn them off. This was my case. Seems like bug here, or config change needed.
-
OK after much gnashing of teeth last night I have determined the root cause - Captive portal.
I have one Zone setup with multiple interfaces and MAC addresses allowed. I have triple checked the MAC addresses (including packet capture) to verify but some are still blocked. Those blocked reside on the same VLAN(s). Only a few VLANs are affected (strange). If I IP allow them I have connectivity. If I disable Captive Portal on the interface, connectivity is restored. -
S SteveITS referenced this topic on
-
S SteveITS referenced this topic on
-
Do you have bandwidth limits set on the affected captive portal zones?
-
No bandwidth limits set now or previously.
-
OK thanks. There's definitely some issue there. We are trying to pin it down.