MAC Passthrough
-
I need some assistance.
What I have :
a LAN interface 192.168.1.0/24 with several printers.
a Captive portal interface 192.168.2.0/24I've added the LAC of my Phone to the MAC list :
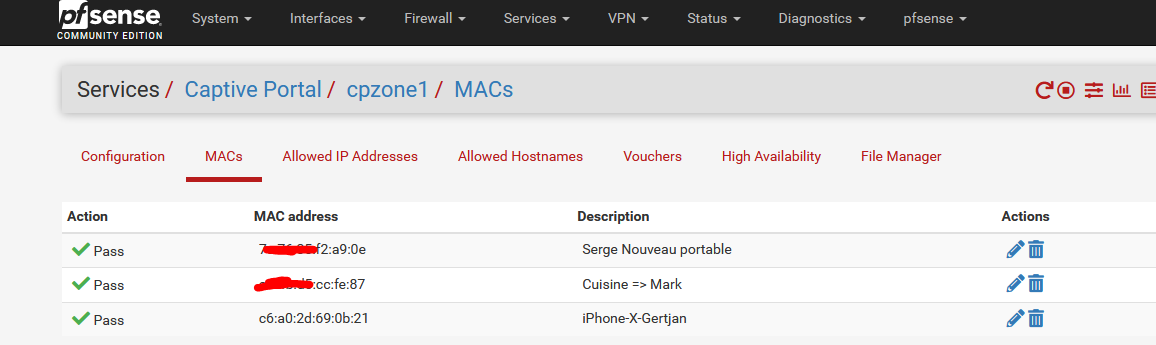
The one ending with 21 is mine.When added, I checked the ipfw table :
192.168.2.1/32 0 2396510 82990957 1645185902 --- table(cpzone1_pipe_mac), set(0) --- a4:xx:xx:cc:fe:87 any 2003 5709 2720583 1645185885 any xx:xx:xx:cc:fe:87 2002 6982 1447764 1645185887 c6:a0:2d:69:0b:21 any 2015 2895 674410 1645185776 any c6:a0:2d:69:0b:21 2014 4062 3844380 1645185699 7c:xx:35:xx:xx:0e any 2001 0 0 0 any xx:xx:xx:xx:a9:0e 2000 0 0 0Line 3 and 4 of this table are the "in" and "out" of my Phone.
This tables shows two things :
My MAC has been added
There is traffic flowing.I had "Internet" access on my Phone.
My captive portal is ment to be used by non trusted devices, so no, they have no access to my LAN. Because, if they have to use LAN trusted devices, I would connect my phone to the companie's Wifi network, not the public captive portal network.But, I've made one exception : captive portal users can 'browse' for printers, and I made these (their IP's) available with a firewall rule on the captive portal :
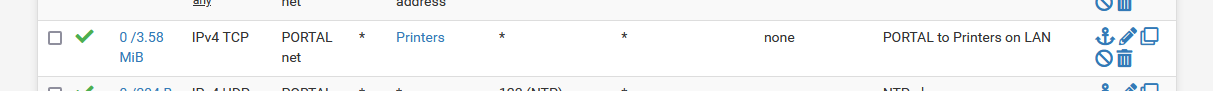
With the help on Avahi, captive portal users can now 'see' these printers.
I selected an image on my, and selected a printer (they all showed up).
I could print from my phone, connected to the captive portal, using IP 192.168.2.222 to a printer on pfSense LAN, 192.168.1.36 just fine.
No bugs - no regression - no issues for me.
So, please help me here, make me understand why my '2.6.0 pfSense' is any different compared to yours.
I'm pretty sure the code base is 100 % the same ;)
Settings are probably different, hardware (APs etc) also.
I'll be happy to share more info.@worlddrknss said in MAC Passthrough:
In version 2.6.0 once a PC is authenticated and added to the MAC list, it does not honor the firewall rules.
What kind of authentification ?
Added to the MAC list ?
Added to the classic logged-in-user tables :..... --- table(cpzone1_auth_up), set(0) --- ..... --- table(cpzone1_auth_down), set(0) --- .....For me, these two tables contain the IP and MAC of every logged in captive portal user.
Btw :if the captive portal was broken, as I'm using it for a hotel (boatloads of clients hat beocme angry when their Internet access doesn't work) I would have known that right after upgrading to 2.6.0.
No one said nothing to me. All is well.
MAC added devices still work.So, again : some info, please.
-
I can't see no differences.
I upgraded from pfSense 2.5.2. You too ? And what about your ping from the wifi?Even with this rule, I can't reach my local network:
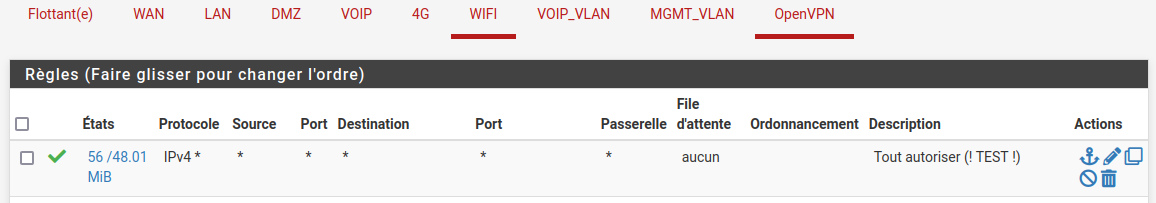
-
@leofox said in MAC Passthrough:
And what about your ping from the wifi?
Dono of my clients are actually pinging.
But the question is wrong.You saw the firewalls rule but you don't believe it ?
You don't know what you see ?It says :
For every IPv4 - using any protocol (TCP UDP ICMP, GRE etc etc etc etc etc) using any source address, using any source port using any destination address, port, whatever gateway.
Actually : just one criteria : it must be IPv4.
As there is also IPv6.So, yeah, it's written in stone : ICMP (ping) passes.
Btw : this is a copy of the same default rule that you've found on the LAN interface when you first installed pfSense.
It passes all kind of traffic, from anybody to everybody. No limits. No discrimination.The captive portal doesn't support IPv6 .... ;)
Make this as a first (top) rule :
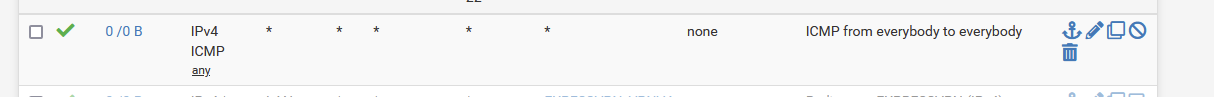
and now, ping away.
You will see these counters going up :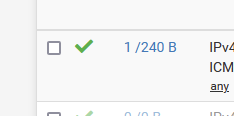
That's why these counters are shown.
-
@Gertjan
This is with captive portal on and MAC added to MAC-Passthrough List:
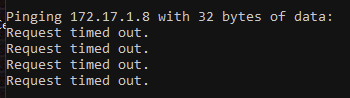
Turning off Captive Portal Results in:
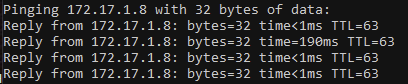
Adding an ICMP any rule still results in the same issue. The only thing CP is currently allowing is internet access.
@leofox per your ping question, same issue as you when connected to CP (Google):
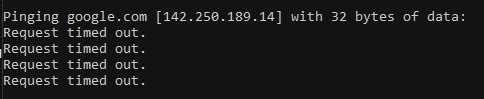
-
First image : something is missing. What about proving (yourself) that you are actually connected ?
I showed you above how you can find it out. Forget about what the GUI shows you, use the ipfw commands, that's is the real thing.All you need to know : Troubleshooting Captive Portal - with that guide you will be able to stop to say "it doesn't work" as you will know why it doesn't work.
That's right next to the solution ;)If you were not connected (authorized ) by the portal, image 2 is explained.
-
This post is deleted! -
00999 2684170 1169576448 allow tagged 1 01000 5987898 6305074767 skipto tablearg ip from any to any via table(cp_ifaces) 01100 619619402 637068854652 allow ip from any to any 02100 145294 159300202 pipe tablearg tag 1 MAC table(administrators_pipe_mac) 02101 0 0 allow pfsync from any to any 02102 0 0 allow carp from any to any 02103 16 0 allow layer2 mac-type 0x0806,0x8035 02104 0 0 allow layer2 mac-type 0x888e,0x88c7 02105 0 0 allow layer2 mac-type 0x8863,0x8864 02106 260 0 deny layer2 not mac-type 0x0800,0x86dd 02107 15954 6435982 allow ip from any to table(administrators_host_ips) in 02108 22761 2911468 allow ip from table(administrators_host_ips) to any out 02109 0 0 allow ip from any to 255.255.255.255 in 02110 0 0 allow ip from 255.255.255.255 to any out 02111 0 0 pipe tablearg ip from table(administrators_allowed_up) to any in 02112 0 0 pipe tablearg ip from any to table(administrators_allowed_down) in 02113 296 244263 pipe tablearg ip from table(administrators_allowed_up) to any out 02114 0 0 pipe tablearg ip from any to table(administrators_allowed_down) out 02115 0 0 pipe tablearg tag 1 ip from table(administrators_auth_up) to any layer2 in 02116 0 0 pipe tablearg tag 1 ip from any to table(administrators_auth_down) layer2 out 02117 29 1959 fwd 127.0.0.1,8002 tcp from any to any 80 in 02118 38693 15400035 allow tcp from any to any out 02119 1525 689525 skipto 65534 ip from any to any 65534 9820 8111146 deny ip from any to any 65535 0 0 allow ip from any to anyI commented out my MAC
--- table(cp_ifaces), set(0) --- bge1.4 2100 189541 158255829 1645293467 --- table(administrators_auth_up), set(0) --- --- table(administrators_host_ips), set(0) --- 10.0.40.1/32 0 31186 7502835 1645293467 --- table(administrators_pipe_mac), set(0) --- XX:XX:XX:XX:XX:XX any 2003 6845 2818160 1645293467 any XX:XX:XX:XX:XX:XX 2002 13520 15935201 1645293467 --- table(administrators_auth_down), set(0) --- --- table(administrators_allowed_up), set(0) --- --- table(administrators_allowed_down), set(0) ---Firewall Ruleset:
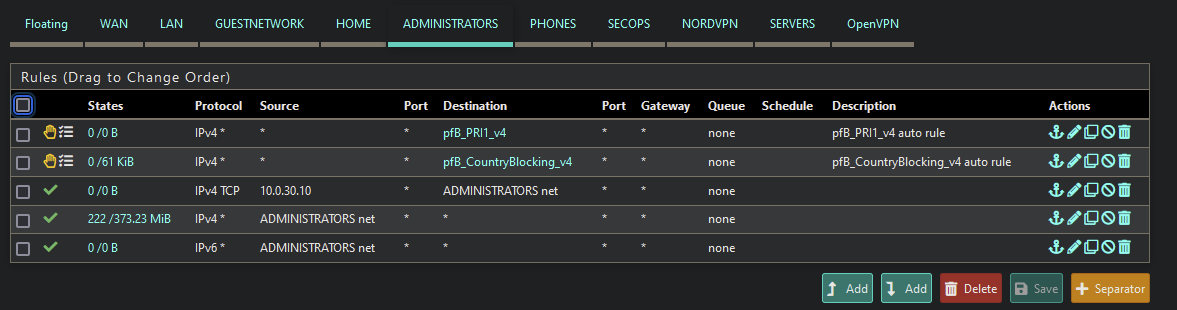
My system authenticates with NPS and then set to Auto-Add upon successful authentication.
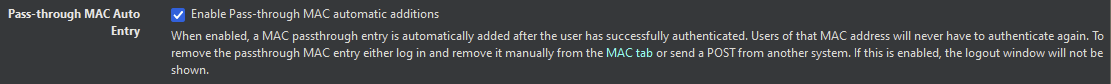
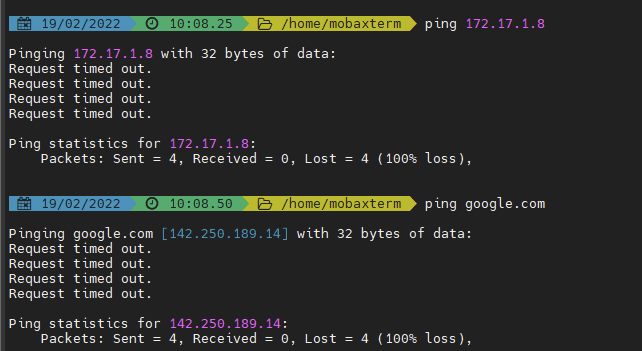
Ping Tests:
Now with Captive Portal Turned off:
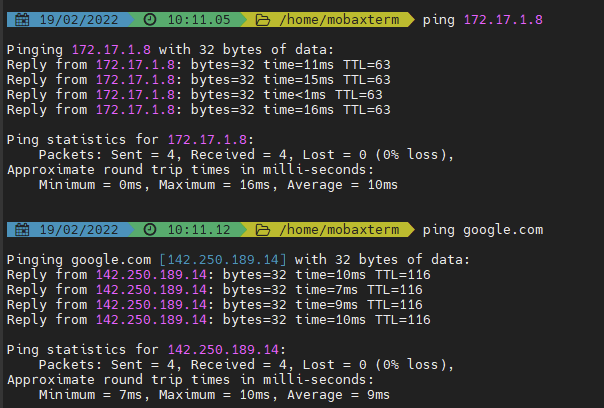
-
Your device is listed in the "MACs" table
@worlddrknss said in MAC Passthrough:
--- table(administrators_pipe_mac), set(0) ---
XX:XX:XX:XX:XX:XX any 2003 6845 2818160 1645293467
any XX:XX:XX:XX:XX:XX 2002 13520 15935201 1645293467that is, if XX:XX:XX:XX:XX:XX is the MAC being used.
Look at the numbers :
XX:XX:XX:XX:XX:XX any 2003 6845 2818160 1645293467
any XX:XX:XX:XX:XX:XX 2002 13520 15935201 16452934672003 and 2002 are the pipes, these are constants.
1645293467 and 1645293467 are probably ipfw firewall rule indexes, constants
But these : 6845 2818160 and 13520 15935201 are bytes passed.Do a ping test.
Note down the numbers - also the final block rule :
@worlddrknss said in MAC Passthrough:
65534 9820 8111146 deny ip from any to any
and re do a ping test.
What changes ?
If none of the numbers in the table administrators_pipe_macchanged, then your MAC wasn't used.Btw : when you turned of the captive portal, pings are passing, this means the the GUI firewall (pf) isn't the issue.
--- table(cp_ifaces), set(0) --- bge1.4 2100 189541 158255829 1645293467bge1.4 : Your are using VLANs ?
It's time to packets capture your portal interface, and do you see the 'ping' packets coming in ? The VLAN interface tag is "4" ? (because if not, you've your answer) -
I don't think there is a link with VLANs as I have the same problem with and without VLANs on different configurations.
On the other hand, I tested by removing the tag1 from ipfw (/etc/inc/captiveportal.inc lines 590,692,744&746) in order to return to the way it was in 2.5.2 and it's no better.
-
@leofox I might just go back to 2.5.2 where Captive Portal worked, or just wait a few releases and see if they figure out the issue. CP isn't that huge of a deal for me as I was just using it as a secondary security option to port security.
-
You did a ping test while watching the "bytes counters" ?
The final block rule - line 65534 - was incrementing ?
The xxxxx_pipe_mac table content : your MAC, the counters were incrementing ?
Another line ?edit :
Look at the last line :
65535 0 0 allow ip from any to anyThis is a "pass all traffic line".
What happens when you place the same line at position 1, like
ipfw add 1 allow ip from any to anyNow the entire captive portal "ipfw" should be transparent as everything passes right at the start ?
Try also other positions. Did the rule go hit/matched ?
Btw : if a rule like "02108" exisys, you can create second "02108".
But when you delete "02108", you delete them both. Just restart the portal to recreate all the rules. -
Adding the following (excluding the Administrator Network):
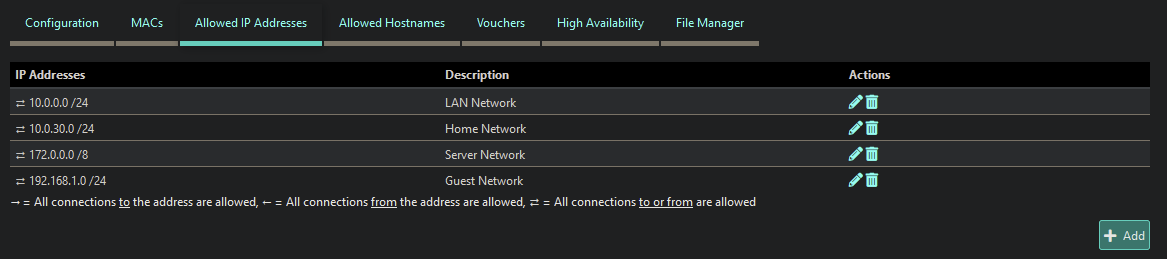
Fixed the internal ping issues, but ping over the internet is still being blocked. Eg: google, msn, yahoo, etc. -
This is related to: https://forum.netgate.com/topic/169879/udp-icmp-is-not-working-after-upgrade-to-2-6-0/2 and https://redmine.pfsense.org/issues/12834
-
Good point about these links. Indeed, my Windows clients can no longer reach the AD domain either, which is the problem with the UDP protocol.
-
I can also confirm this issue. I recently upgraded to 22.01 on my Netgate 1100 appliance.
Users authenticate via a freeradius server with Pass-through MAC automatic additions enabled. Before, once a user authenticated and got past captive portal, nothing was blocked as the only firewall rule on that interface was to allow any IPv4 traffic, anywhere.
After the upgrade, those with authenticated MAC addresses are only allowed basic web traffic. I can no longer connect to a VPN, ping DNS servers outside the network, or even ping the WAN address or gateway address. The only fix is to disable Captive Portal which I obviously don't want to do.
The network diagram is:
Modem >> Netgate 1100 >> UniFi Switch >> UniFi Access Points
The UniFi switch is connected to the OPT1 (192.168.10.1/24) interface on the router that captive portal is active on. I've got a dumb switch connected to the LAN (192.168.1.1/24) interface that connects all the wired PC's in our office.
-
@all
I wouldn't believe it.
I've installed the App of my Expr*ss VPN ISP to my phone, and Pad, and connected both to my captive portal.
I fired up the VPN App.
Initially, no connection could be made. That's new .... because it was falling back to a TCP tunnel, it connected.I'm using my portal for hotel client, and no one, complained .... yet. I guess most clients use the wifi just to check mails, update FB, and watch Netflix anyway.
II think the "pipes" used by the portal connections have an issue.
You can see them here : Diagnostics > Limiter Info
These "pipes" are also used for the bugger bloat limiters I was using before, this is not possible any more with 2.6.0. I can live with that. But the captive portal partially broken .... hummm. Never saw that before.When I remove all connected clients.
And I de activate the captive portal, all limiters and schedulers should be removed, right ?
Wrong :These stay in place :
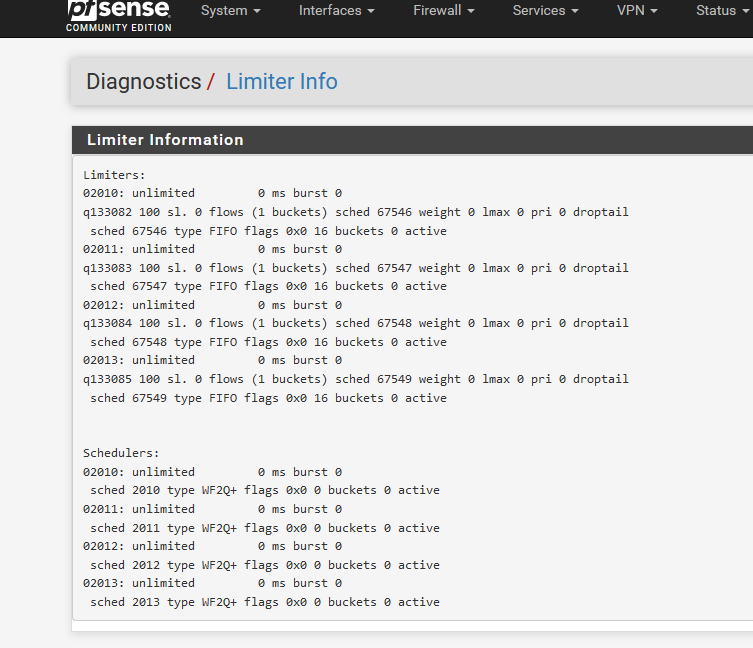
This should also be 'empty' :
[2.6.0-RELEASE][admin@pfsense.mynetwork.net]/root: ipfw table all list --- table(cp_ifaces), set(0) ---[2.6.0-RELEASE][admin@pfsense.mynetwork.net]/root: ipfw table all list --- table(cp_ifaces), set(0) --- [2.6.0-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root: ipfw show 00999 1093652 159826765 allow tagged 1 01000 3334509 3552256101 skipto tablearg ip from any to any via table(cp_ifaces) 01100 25766627 20440009158 allow ip from any to any 65534 51291 14897634 deny ip from any to any 65535 144 33784 allow ip from any to anyas the captive portal is de activated.
I rebooted pfSense :
[2.6.0-RELEASE][admin@pfsense.mynetwork.net]/root: ipfw show ipfw: retrieving config failed: Protocol not available [2.6.0-RELEASE][admin@pfsense.mynetwork.net]/root: ipfw ipfw table all list ipfw: bad command `ipfw'this is normal, no portal == no ipfw loaded.
I have a pfSEnse home setup @home. I'll do some testing this weekend.
edit 2022-03-01 :
Pipes or limiters are probably another issue, or not the issue at all
When I introduce a '00998' rule like this :
2.6.0-RELEASE][admin@pfsense.portalbroken.net]/root: ipfw show 00998 94719259 85479897044 allow ip from any to any 00999 5485259 1007470890 allow tagged 1 01000 11615464 11431517900 skipto tablearg ip from any to any via table(cp_ifaces) 01100 93906271 71988908641 allow ip from any to any .....00999 and further are default captive portal ipfw rules.
My captive portal becomes 100% transparent, that is : still no UDP neither ICMP, just TCP.
Looks like the issue is ipfw ....
-
I ended up just reinstalling the firmware on my Netgate 1100 until this gets resolved. I followed this guide and requested access to version 21.05 in a support ticket. Install went fine and after restoring my config, everything works as it should.
-
Read https://forum.netgate.com/topic/170300/new-system-patches-v2-0?_=1646343673426 - Apply patch (Redmine #12834) and ICMP/UDP will be handled just fine.
-
It's ok for me. The patch has fixed the issue. Thanks.