OpenVPN Not working after update
-
Hello,
I've been using OpenVPN for the past few years without any issues until now. I'm using local user auth and nothing was changed in my setup.
Everything is up-to-date. 2.6.0-RELEASE (amd64)
Any ideas ?
Error log when someone tries to connect :Feb 22 11:52:05 openvpn 57202 :42155 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication Feb 22 11:52:05 openvpn 57202 :42155 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication Feb 22 11:52:05 openvpn 57202 :42155 TLS: Initial packet from [AF_INET]:42155, sid=be02686e 5e359dab Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_VER=2.5.2 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_PLAT=win Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_PROTO=6 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_NCP=2 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_LZ4=1 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_LZ4v2=1 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_LZO=1 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_COMP_STUB=1 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_COMP_STUBv2=1 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_TCPNL=1 Feb 22 11:52:05 openvpn 57202 :42155 peer info: IV_GUI_VER=OpenVPN_GUI_11 Feb 22 11:52:05 openvpn 57202 :42155 PLUGIN_CALL: POST /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so/PLUGIN_AUTH_USER_PASS_VERIFY status=2 Feb 22 11:52:05 openvpn 57202 :42155 TLS: Username/Password authentication deferred for username 'lcs' [CN SET] Feb 22 11:52:05 openvpn 57202 :42155 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384 Feb 22 11:52:05 openvpn 57202 :42155 [lcs] Peer Connection Initiated with [AF_INET]:42155 Feb 22 11:52:05 openvpn 45427 user 'lcs' authenticated Feb 22 11:52:07 openvpn 57202 :42155 PUSH: Received control message: 'PUSH_REQUEST' Feb 22 11:52:07 openvpn 57202 :42155 Delayed exit in 5 seconds Feb 22 11:52:07 openvpn 57202 :42155 SENT CONTROL [lcs]: 'AUTH_FAILED' (status=1) -
One more thing I've noticed. The firewall is crashing when I try to export OpenVPN Client config and I have to manually reboot.
-
I'm also having problems. I had a previously working configuration to my ThinkPad running OpenSUSE Linux 15.3. After updated I made the changes described in the sticky note at the top of the forum. Now, OpenVPN no longer connects. Here is the log, but I'm not sure of what I'm looking at. I assume those "TLS Error: cannot locate HMAC in incoming packet from" line are caused by someone trying to connect, as I don't recognize the addresses nor the times they occurred.
Here's the log:
Feb 18 04:55:19 openvpn 41411 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]38.132.109.175:35479
Feb 18 09:54:21 openvpn 41411 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]109.235.58.241:18058
Feb 18 13:08:00 openvpn 41411 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]109.235.58.248:35187
Feb 18 13:21:27 openvpn 41411 event_wait : Interrupted system call (code=4)
Feb 18 13:21:27 openvpn 41411 /usr/local/sbin/ovpn-linkdown ovpns1 1500 1622 172.16.255.1 255.255.255.0 init
Feb 18 13:21:27 openvpn 41411 SIGTERM[hard,] received, process exiting
Feb 18 13:21:28 openvpn 64748 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022
Feb 18 13:21:28 openvpn 64748 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10
Feb 18 13:21:28 openvpn 64825 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Feb 18 13:21:28 openvpn 64825 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 18 13:21:28 openvpn 64825 Initializing OpenSSL support for engine 'rdrand'
Feb 18 13:21:28 openvpn 64825 WARNING: experimental option --capath /var/etc/openvpn/server1/ca
Feb 18 13:21:28 openvpn 64825 TUN/TAP device ovpns1 exists previously, keep at program end
Feb 18 13:21:28 openvpn 64825 TUN/TAP device /dev/tun1 opened
Feb 18 13:21:28 openvpn 64825 /sbin/ifconfig ovpns1 172.16.255.1 172.16.255.2 mtu 1500 netmask 255.255.255.0 up
Feb 18 13:21:28 openvpn 64825 /sbin/ifconfig ovpns1 inet6 2607:fea8:4c82:59ff::1/64 mtu 1500 up
Feb 18 13:21:29 openvpn 64825 /sbin/ifconfig ovpns1 inet6 -ifdisabled
Feb 18 13:21:29 openvpn 64825 /usr/local/sbin/ovpn-linkup ovpns1 1500 1621 172.16.255.1 255.255.255.0 init
Feb 18 13:21:29 openvpn 64825 UDPv4 link local (bound): [AF_INET]99.246.125.121:1194
Feb 18 13:21:29 openvpn 64825 UDPv4 link remote: [AF_UNSPEC]
Feb 18 13:21:29 openvpn 64825 NOTE: IPv4 pool size is 252, IPv6 pool size is 65536. IPv4 pool size limits the number of clients that can be served from the pool
Feb 18 13:21:29 openvpn 64825 Initialization Sequence Completed
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_VER=2.4.3
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_PLAT=linux
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_PROTO=2
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_NCP=2
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_LZ4=1
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_LZ4v2=1
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_LZO=1
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_COMP_STUB=1
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_COMP_STUBv2=1
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 peer info: IV_TCPNL=1
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1557', remote='link-mtu 1541'
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 WARNING: 'keysize' is used inconsistently, local='keysize 256', remote='keysize 128'
Feb 18 13:37:05 openvpn 64825 24.114.64.80:14275 [E520] Peer Connection Initiated with [AF_INET]24.114.64.80:14275
Feb 18 13:37:05 openvpn 64825 E520/24.114.64.80:14275 MULTI_sva: pool returned IPv4=172.16.255.2, IPv6=2607:fea8:4c82:59ff::1000
Feb 18 13:37:05 openvpn 68991 openvpn server 'ovpns1' user cert CN 'E520' address '24.114.64.80' - connected
Feb 18 13:42:05 openvpn 64825 E520/24.114.64.80:14275 [E520] Inactivity timeout (--ping-restart), restarting
Feb 18 13:42:05 openvpn 22070 openvpn server 'ovpns1' user cert CN 'E520' address '24.114.64.80' - disconnected
Feb 18 14:31:50 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]223.71.167.165:48133
Feb 18 15:16:47 openvpn 92273 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022
Feb 18 15:16:47 openvpn 92273 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10
Feb 18 15:16:47 openvpn 92528 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Feb 18 15:16:47 openvpn 92528 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 18 15:16:47 openvpn 92528 Initializing OpenSSL support for engine 'rdrand'
Feb 18 15:16:47 openvpn 92528 WARNING: experimental option --capath /var/etc/openvpn/server3/ca
Feb 18 15:16:47 openvpn 92528 TUN/TAP device ovpns3 exists previously, keep at program end
Feb 18 15:16:47 openvpn 92528 TUN/TAP device /dev/tun3 opened
Feb 18 15:16:47 openvpn 92528 ioctl(TUNSIFMODE): Device busy (errno=16)
Feb 18 15:16:47 openvpn 92528 /sbin/ifconfig ovpns3 172.16.254.1 172.16.254.2 mtu 1500 netmask 255.255.255.0 up
Feb 18 15:16:47 openvpn 92528 /sbin/ifconfig ovpns3 inet6 2607:fea8:4c82:59fe::1/64 mtu 1500 up
Feb 18 15:16:48 openvpn 92528 /sbin/ifconfig ovpns3 inet6 -ifdisabled
Feb 18 15:16:48 openvpn 92528 /usr/local/sbin/ovpn-linkup ovpns3 1500 1623 172.16.254.1 255.255.255.0 init
Feb 18 15:16:48 openvpn 92528 Listening for incoming TCP connection on [AF_INET]99.246.125.121:80
Feb 18 15:16:48 openvpn 92528 TCPv4_SERVER link local (bound): [AF_INET]99.246.125.121:80
Feb 18 15:16:48 openvpn 92528 TCPv4_SERVER link remote: [AF_UNSPEC]
Feb 18 15:16:48 openvpn 92528 NOTE: IPv4 pool size is 252, IPv6 pool size is 65536. IPv4 pool size limits the number of clients that can be served from the pool
Feb 18 15:16:48 openvpn 92528 Initialization Sequence Completed
Feb 18 16:23:11 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.116.40:60308
Feb 18 19:07:12 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]162.142.125.137:39300
Feb 18 21:56:36 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]198.199.113.192:52009
Feb 18 22:16:07 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]146.88.240.4:35403
Feb 19 04:09:11 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.116.58:41304
Feb 19 04:30:55 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]167.248.133.132:24929
Feb 19 05:36:12 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]167.94.138.105:18732
Feb 19 16:04:37 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]38.132.109.99:45769
Feb 19 22:16:50 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]146.88.240.4:40111
Feb 20 01:47:46 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]183.136.225.9:23297
Feb 20 03:19:41 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]198.199.105.16:53211
Feb 20 03:52:16 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]38.132.109.182:40208
Feb 20 09:32:24 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]45.137.23.252:46784
Feb 20 16:47:50 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.82:36930
Feb 20 22:24:42 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]146.88.240.4:46055
Feb 21 03:27:12 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]192.241.204.115:44211
Feb 21 04:00:08 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.84:57836
Feb 21 15:02:39 openvpn 92528 /usr/local/sbin/ovpn-linkdown ovpns3 1500 1623 172.16.254.1 255.255.255.0 init
Feb 21 15:02:39 openvpn 92528 SIGTERM[hard,] received, process exiting
Feb 21 15:04:33 openvpn 64825 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]45.79.145.102:51598
Feb 21 15:06:31 openvpn 39213 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022
Feb 21 15:06:31 openvpn 39213 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10
Feb 21 15:06:31 openvpn 39398 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Feb 21 15:06:31 openvpn 39398 GDG: problem writing to routing socket
Feb 21 15:06:31 openvpn 39398 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 21 15:06:31 openvpn 39398 Initializing OpenSSL support for engine 'rdrand'
Feb 21 15:06:31 openvpn 39398 WARNING: experimental option --capath /var/etc/openvpn/server1/ca
Feb 21 15:06:31 openvpn 39398 TUN/TAP device ovpns1 exists previously, keep at program end
Feb 21 15:06:31 openvpn 39398 TUN/TAP device /dev/tun1 opened
Feb 21 15:06:31 openvpn 39398 ioctl(TUNSIFMODE): Device busy (errno=16)
Feb 21 15:06:31 openvpn 39398 /sbin/ifconfig ovpns1 172.16.255.1 172.16.255.2 mtu 1500 netmask 255.255.255.0 up
Feb 21 15:06:31 openvpn 39398 /sbin/ifconfig ovpns1 inet6 2607:fea8:4c82:59ff::1/64 mtu 1500 up
Feb 21 15:06:32 openvpn 39398 /sbin/ifconfig ovpns1 inet6 -ifdisabled
Feb 21 15:06:32 openvpn 39398 /usr/local/sbin/ovpn-linkup ovpns1 1500 1621 172.16.255.1 255.255.255.0 init
Feb 21 15:06:32 openvpn 39398 UDPv4 link local (bound): [AF_INET]99.246.125.121:1194
Feb 21 15:06:32 openvpn 39398 UDPv4 link remote: [AF_UNSPEC]
Feb 21 15:06:32 openvpn 39398 NOTE: IPv4 pool size is 252, IPv6 pool size is 65536. IPv4 pool size limits the number of clients that can be served from the pool
Feb 21 15:06:32 openvpn 39398 Initialization Sequence Completed
Feb 21 15:43:44 openvpn 38677 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022
Feb 21 15:43:44 openvpn 38677 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10
Feb 21 15:43:44 openvpn 38882 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Feb 21 15:43:44 openvpn 38882 GDG: problem writing to routing socket
Feb 21 15:43:44 openvpn 38882 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 21 15:43:44 openvpn 38882 Initializing OpenSSL support for engine 'rdrand'
Feb 21 15:43:44 openvpn 38882 WARNING: experimental option --capath /var/etc/openvpn/server1/ca
Feb 21 15:43:44 openvpn 38882 TUN/TAP device ovpns1 exists previously, keep at program end
Feb 21 15:43:44 openvpn 38882 TUN/TAP device /dev/tun1 opened
Feb 21 15:43:44 openvpn 38882 ioctl(TUNSIFMODE): Device busy (errno=16)
Feb 21 15:43:44 openvpn 38882 /sbin/ifconfig ovpns1 172.16.255.1 172.16.255.2 mtu 1500 netmask 255.255.255.0 up
Feb 21 15:43:44 openvpn 38882 /sbin/ifconfig ovpns1 inet6 2607:fea8:4c82:59ff::1/64 mtu 1500 up
Feb 21 15:43:45 openvpn 38882 /sbin/ifconfig ovpns1 inet6 -ifdisabled
Feb 21 15:43:45 openvpn 38882 /usr/local/sbin/ovpn-linkup ovpns1 1500 1622 172.16.255.1 255.255.255.0 init
Feb 21 15:43:45 openvpn 38882 UDPv4 link local (bound): [AF_INET]99.246.125.121:1194
Feb 21 15:43:45 openvpn 38882 UDPv4 link remote: [AF_UNSPEC]
Feb 21 15:43:45 openvpn 38882 NOTE: IPv4 pool size is 252, IPv6 pool size is 65536. IPv4 pool size limits the number of clients that can be served from the pool
Feb 21 15:43:45 openvpn 38882 Initialization Sequence Completed
Feb 21 15:47:21 openvpn 40938 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022
Feb 21 15:47:21 openvpn 40938 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10
Feb 21 15:47:21 openvpn 41239 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Feb 21 15:47:21 openvpn 41239 GDG: problem writing to routing socket
Feb 21 15:47:21 openvpn 41239 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 21 15:47:21 openvpn 41239 Initializing OpenSSL support for engine 'rdrand'
Feb 21 15:47:21 openvpn 41239 WARNING: experimental option --capath /var/etc/openvpn/server1/ca
Feb 21 15:47:21 openvpn 41239 TUN/TAP device ovpns1 exists previously, keep at program end
Feb 21 15:47:21 openvpn 41239 TUN/TAP device /dev/tun1 opened
Feb 21 15:47:21 openvpn 41239 ioctl(TUNSIFMODE): Device busy (errno=16)
Feb 21 15:47:21 openvpn 41239 /sbin/ifconfig ovpns1 172.16.255.1 172.16.255.2 mtu 1500 netmask 255.255.255.0 up
Feb 21 15:47:21 openvpn 41239 /sbin/ifconfig ovpns1 inet6 2607:fea8:4c82:59ff::1/64 mtu 1500 up
Feb 21 15:47:22 openvpn 41239 /sbin/ifconfig ovpns1 inet6 -ifdisabled
Feb 21 15:47:22 openvpn 41239 /usr/local/sbin/ovpn-linkup ovpns1 1500 1622 172.16.255.1 255.255.255.0 init
Feb 21 15:47:22 openvpn 41239 UDPv4 link local (bound): [AF_INET]99.246.125.121:1194
Feb 21 15:47:22 openvpn 41239 UDPv4 link remote: [AF_UNSPEC]
Feb 21 15:47:22 openvpn 41239 NOTE: IPv4 pool size is 252, IPv6 pool size is 65536. IPv4 pool size limits the number of clients that can be served from the pool
Feb 21 15:47:22 openvpn 41239 Initialization Sequence Completed
Feb 21 15:51:57 openvpn 41239 event_wait : Interrupted system call (code=4)
Feb 21 15:51:57 openvpn 41239 /usr/local/sbin/ovpn-linkdown ovpns1 1500 1622 172.16.255.1 255.255.255.0 init
Feb 21 15:51:58 openvpn 41239 SIGTERM[hard,] received, process exiting
Feb 21 15:51:58 openvpn 86073 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022
Feb 21 15:51:58 openvpn 86073 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10
Feb 21 15:51:58 openvpn 86088 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Feb 21 15:51:58 openvpn 86088 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 21 15:51:58 openvpn 86088 Initializing OpenSSL support for engine 'rdrand'
Feb 21 15:51:58 openvpn 86088 WARNING: experimental option --capath /var/etc/openvpn/server1/ca
Feb 21 15:51:58 openvpn 86088 TUN/TAP device ovpns1 exists previously, keep at program end
Feb 21 15:51:58 openvpn 86088 TUN/TAP device /dev/tun1 opened
Feb 21 15:51:58 openvpn 86088 /sbin/ifconfig ovpns1 172.16.255.1 172.16.255.2 mtu 1500 netmask 255.255.255.0 up
Feb 21 15:51:58 openvpn 86088 /sbin/ifconfig ovpns1 inet6 2607:fea8:4c82:59ff::1/64 mtu 1500 up
Feb 21 15:51:59 openvpn 86088 /sbin/ifconfig ovpns1 inet6 -ifdisabled
Feb 21 15:51:59 openvpn 86088 /usr/local/sbin/ovpn-linkup ovpns1 1500 1622 172.16.255.1 255.255.255.0 init
Feb 21 15:51:59 openvpn 86088 UDPv4 link local (bound): [AF_INET]99.246.125.121:1194
Feb 21 15:51:59 openvpn 86088 UDPv4 link remote: [AF_UNSPEC]
Feb 21 15:51:59 openvpn 86088 NOTE: IPv4 pool size is 252, IPv6 pool size is 65536. IPv4 pool size limits the number of clients that can be served from the pool
Feb 21 15:51:59 openvpn 86088 Initialization Sequence Completed
Feb 21 16:06:32 openvpn 86088 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]38.132.109.182:60422
Feb 21 16:45:23 openvpn 36963 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022
Feb 21 16:45:23 openvpn 36963 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10
Feb 21 16:45:23 openvpn 37260 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Feb 21 16:45:23 openvpn 37260 GDG: problem writing to routing socket
Feb 21 16:45:23 openvpn 37260 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 21 16:45:23 openvpn 37260 Initializing OpenSSL support for engine 'rdrand'
Feb 21 16:45:23 openvpn 37260 WARNING: experimental option --capath /var/etc/openvpn/server1/ca
Feb 21 16:45:23 openvpn 37260 TUN/TAP device ovpns1 exists previously, keep at program end
Feb 21 16:45:23 openvpn 37260 TUN/TAP device /dev/tun1 opened
Feb 21 16:45:23 openvpn 37260 ioctl(TUNSIFMODE): Device busy (errno=16)
Feb 21 16:45:23 openvpn 37260 /sbin/ifconfig ovpns1 172.16.255.1 172.16.255.2 mtu 1500 netmask 255.255.255.0 up
Feb 21 16:45:23 openvpn 37260 /sbin/ifconfig ovpns1 inet6 2607:fea8:4c82:59ff::1/64 mtu 1500 up
Feb 21 16:45:24 openvpn 37260 /sbin/ifconfig ovpns1 inet6 -ifdisabled
Feb 21 16:45:24 openvpn 37260 /usr/local/sbin/ovpn-linkup ovpns1 1500 1622 172.16.255.1 255.255.255.0 init
Feb 21 16:45:24 openvpn 37260 UDPv4 link local (bound): [AF_INET]99.246.125.121:1194
Feb 21 16:45:24 openvpn 37260 UDPv4 link remote: [AF_UNSPEC]
Feb 21 16:45:24 openvpn 37260 NOTE: IPv4 pool size is 252, IPv6 pool size is 65536. IPv4 pool size limits the number of clients that can be served from the pool
Feb 21 16:45:24 openvpn 37260 Initialization Sequence Completed
Feb 21 22:22:40 openvpn 37260 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]146.88.240.4:46733
Feb 22 03:47:13 openvpn 37260 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.84:33055
Feb 22 04:18:25 openvpn 37260 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]162.142.125.136:10130
Feb 22 05:43:50 openvpn 37260 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]183.136.225.9:21717
Feb 22 06:17:27 openvpn 37260 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]192.241.203.18:40222 -
I just noticed something. On the server, the Auth digest algorithm is sha1 160 bit. On the client, HMAC Authentication is sha1, but 128 bit and while it can be changed to 160, it doesn't stick because I don't have permission.
-
" repair " these :
@jknott said in OpenVPN Not working after update:
Feb 21 15:06:31 openvpn 39398 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Feb 21 15:06:31 openvpn 39398 GDG: problem writing to routing socketthat is, make them go away.
Or explain why you need them - show your openvpn server file.This one :
Feb 21 16:45:23 openvpn 37260 ioctl(TUNSIFMODE): Device busy (errno=16)dono what that is.
Some stray socket ?Feb 21 16:45:23 openvpn 37260 /sbin/ifconfig ovpns1 inet6 2607:fea8:4c82:59ff::1/64 mtu 1500 up Feb 21 16:45:24 openvpn 37260 /sbin/ifconfig ovpns1 inet6 -ifdisabledInterface settings about IPv6 are set.
And the the interface is disabled .... ?! What about not setting any IPv6 stuff ?This :
WARNING: experimental option --capath /var/etc/openvpn/server1/cais a warning that's shown since way way back. Probably not "experimental" anymore, but bthey forgot to remove the message.
Btw : my OpenVPN server bootup sequence :
2022-02-22 17:30:37.304551+01:00 openvpn 44221 SIGTERM[hard,] received, process exiting 2022-02-22 17:30:37.615519+01:00 openvpn 47337 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022 2022-02-22 17:30:37.615772+01:00 openvpn 47337 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10 2022-02-22 17:30:37.616831+01:00 openvpn 47684 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts 2022-02-22 17:30:37.618389+01:00 openvpn 47684 WARNING: experimental option --capath /var/etc/openvpn/server1/ca 2022-02-22 17:30:37.618744+01:00 openvpn 47684 TUN/TAP device ovpns1 exists previously, keep at program end 2022-02-22 17:30:37.618869+01:00 openvpn 47684 TUN/TAP device /dev/tun1 opened 2022-02-22 17:30:37.618984+01:00 openvpn 47684 /sbin/ifconfig ovpns1 192.168.3.1 192.168.3.2 mtu 1500 netmask 255.255.255.0 up 2022-02-22 17:30:37.624620+01:00 openvpn 47684 /sbin/ifconfig ovpns1 inet6 2001:470:dead:beef::1/64 mtu 1500 up 2022-02-22 17:30:38.630243+01:00 openvpn 47684 /sbin/ifconfig ovpns1 inet6 -ifdisabled 2022-02-22 17:30:38.637215+01:00 openvpn 47684 /usr/local/sbin/ovpn-linkup ovpns1 1500 1621 192.168.3.1 255.255.255.0 init 2022-02-22 17:30:38.645222+01:00 openvpn 47684 UDPv4 link local (bound): [AF_INET]192.168.10.3:1194 2022-02-22 17:30:38.645285+01:00 openvpn 47684 UDPv4 link remote: [AF_UNSPEC] 2022-02-22 17:30:38.645372+01:00 openvpn 47684 NOTE: IPv4 pool size is 252, IPv6 pool size is 65536. IPv4 pool size limits the number of clients that can be served from the pool 2022-02-22 17:30:38.645466+01:00 openvpn 47684 Initialization Sequence CompletedI cleaned up my config with these instructions : HEADS UP: OpenVPN deprecating shared key mode, requires TLS, deprecating cipher selection.
I'm pretty sure a future pfSense ( == OpenVPN core) update won't break my OpenVPN server access ... again ;) -
Other than making the changes described in that sticky article, I did nothing else, so I have no idea what's causing those errors. I'm thinking about running the wizard again from scratch. I had tried restoring, but it still had the same ciphers as after I made the changes, not the ones that were there originally.
BTW, disabling IPv6 is not an option, ever.
-
@jknott said in OpenVPN Not working after update:
I'm thinking about running the wizard again from scratch.
Don't.
OpenVPN, like a web or mail server can not, and will never really integrate with a web GUI to collect the settings.
This is pfSense, so you have to use the GUI. But always keep an eye on this file :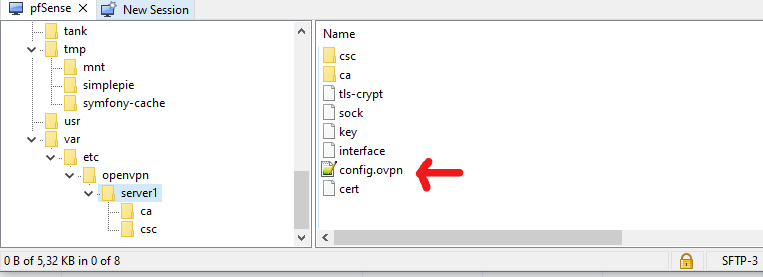
This file contains the OpenVPN server settings.
Like :dev ovpns1 verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 192.168.10.3 tls-server server 192.168.3.0 255.255.255.0 server-ipv6 2001:dead:beef:3::/64 client-config-dir /var/etc/openvpn/server1/csc tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'xxx-yyy-vvv.net' 1" lport 1194 management /var/etc/openvpn/server1/sock unix max-clients 10 push "dhcp-option DOMAIN xxx-yyy-vvv.net" push "dhcp-option DNS 192.168.3.1" push "block-outside-dns" push "register-dns" push "dhcp-option NTP 192.168.1.1" push "redirect-gateway def1" push "redirect-gateway ipv6" client-to-client remote-cert-tls client capath /var/etc/openvpn/server1/ca cert /var/etc/openvpn/server1/cert key /var/etc/openvpn/server1/key dh /etc/dh-parameters.2048 tls-crypt /var/etc/openvpn/server1/tls-crypt data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 data-ciphers-fallback AES-256-GCM allow-compression asym persist-remote-ip float topology subnet status /var/log/openvpn.status status-version 1The last two line are part of the custom config.
My open config file is what is considered at an 'off the mill' basic OpenVPN server file.
One exception : because I have a working IPv6, I create an IPv4 and IPv6 tunnel - because 'why not'.No need to know what all the option mean, but their usage can now be explained with the help of the OpenVPN server FAQ. Their doc doesn't care about 'pfSense GUI'.
Some option are mutual exclusive, or don't work well together.
Some are depreciated , some are right from the bleeding dev edge.
OpenVPN is daunting. The typical example of an open source project where everybody wanted his options and gadgets. I understand why the No knobs and Wheels "Wireguard" was created.Example : this one : "Auth digest algorithm" :
auth SHA256is needed - if it's not there, a warnings shows up :
******* WARNING *******: '--auth none' was specified. This means no authentication will be performed on received packets, meaning you CANNOT trust that the data received by the remote side have NOT been manipulated. PLEASE DO RECONSIDER THIS SETTING!But when it's present
WARNING: 'auth' is used inconsistently, local='auth [null-digest]', remote='auth SHA256'Because the default AES-25-CGM crypto has already a ""Auth digest algorithm" build in.
Just to name one.
Another one, when connected :
WARNING: 'keysize' is used inconsistently, local='keysize 256', remote='keysize 128'or, the keysize option isn't even present in my OpenVPN server config neither client config file. I use AES-25-CGM on both sides ....
Its usage is part of the [Deprecated Options in OpenVPN] list.(https://community.openvpn.net/openvpn/wiki/DeprecatedOptions).
Still, OpenVPN 2.5.4 is complaining it's there - or not there. Whatever. -
I am trying to completely remove the OpenVPN config, so that I can start completely from scratch. However, I keep running into "Cannot disable an OpenVPN instance while the interface is assigned. Remove the interface assignment first." Where is it assigned? I have removed the assignment under rules/openvpn.
After all this frustration, I'm getting to the point where I am seriously considering Wireguard.
-
@jknott Is it assigned in Interfaces/Interface Assignments?
-
No, that's for actual interfaces, such as NICs, VLANs, etc. No mention at all of VPNs in there.
-
My mistake. I was looking under the wrong area.
-
Yeah, that's (2.6.0) new.
When you want to disable an OpenVPN server instance : check the disable box you get this :
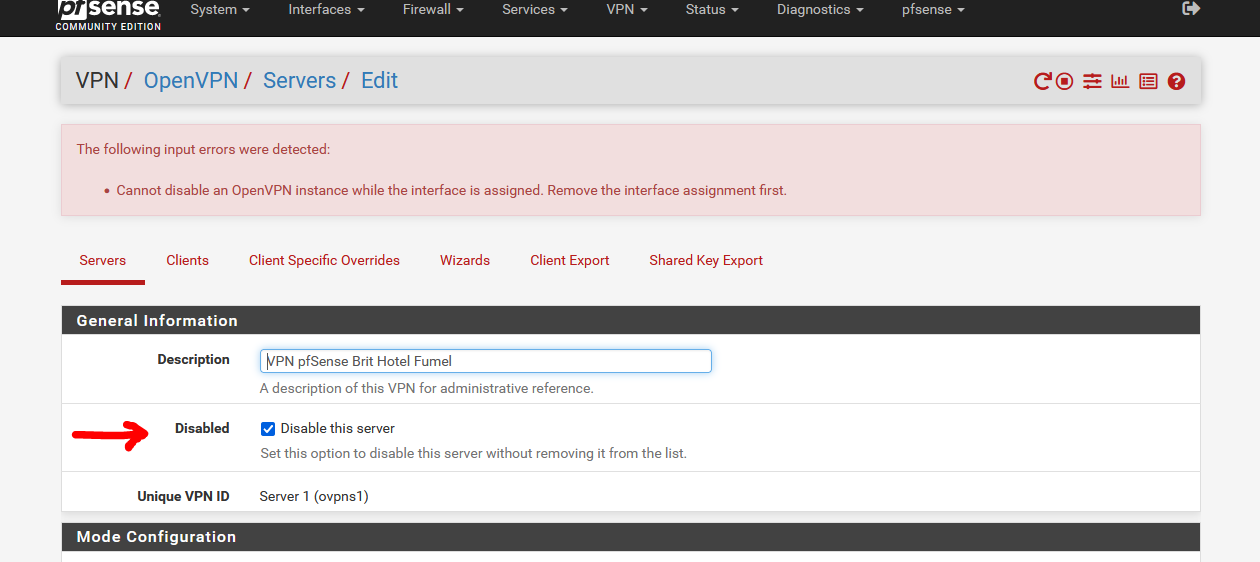
Now, you have to delete or re assign the interface first :
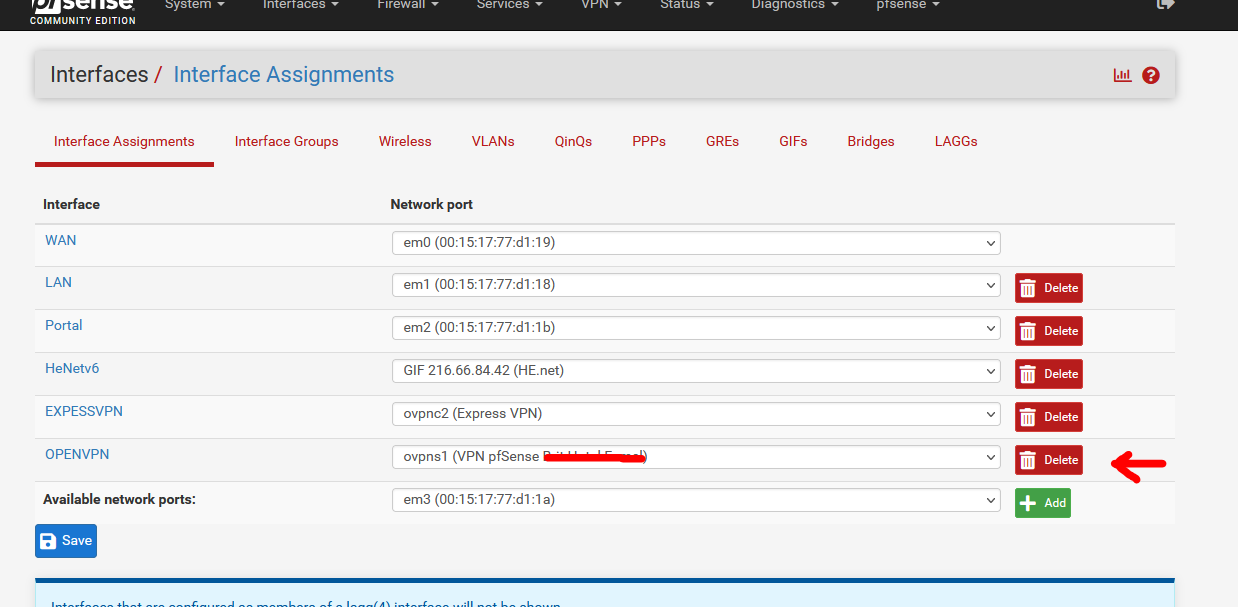
and when done (and saved) you can go back to OpenVPN server instance an shutting it down.
Btw, strange, how little do I know.
More logic, for me, is :
First I stop all processes that uses an interface. (dns mail server web server whatever server)
Then I remove the interface.
This is the other way around.
There must be a reason why it evolved like this. -
I know about disabling a server. However, I have completely stripped out all OpenVPN config and will try again today, if I have time. After making those changes, even restoring a previous pfsense config didn't resolve the problem. This is the second time a pfsense upgrade caused me problems with OpenVPN. What made the first time even more "fun" was I could no longer use my second Internet connection for testing. It's through the same modem and works fine, unless I want to do much more than ping my firewall. So, I now have to test by tethering with my phone. However, I can or at least could get pfsense working by connecting my ThinkPad to my LAN. I pfsense configured to allow OpenVPN connections on any interface.
-
@jknott said in OpenVPN Not working after update:
So, I now have to test by tethering with my phone
All I have to do, is switching the Wifi on my phone to Off.
At that moment I use my 4G/5G data carrier, and with the help of : OpenVPN Connect I connect to my pfSense as a "road warrior".
Lately, it isn't the IPv4 port 1194 UDP that kicks in, it's the IPv6 UDP port 1194 that is used.
This way, I will know it works from an 'unknown' distant IP address, which means I can access my pfSense from everywhere.I'm pretty sure you know all this, why should you have to tether ?
No mobile network available where you are ? -
@gertjan said in OpenVPN Not working after update:
I'm pretty sure you know all this, why should you have to tether ?
No mobile network available where you are ?My Internet connection is via cable modem. For testing, I use my cell phone. I can tether using either WiFi or USB. I don't know what is causing the problem with using my 2nd connection through the cable modem. It used to work fine. Then, after an update, I could no longer use it. When my laptop is connected to the 2nd port on the modem, I have a usual connection to the Internet, but now neither OpenVPN nor ssh work. Ping still does though. I can see the incoming connections, but get no response from pfsense. The IPv4 addresses are on a similar, but different subnet. Given I see the incoming traffic, it's obvious my ISP is not blocking it. My cell and Internet are with the same company, but the cell subnet is completely different from that on my Internet connections. Regardless, I should still be able to set up an OpenVPN connection, when both pfsense and my notebook are on the same LAN. That still worked after that update that killed my usual test connection.
-
I'm about ready to give up. I completely removed all the OpenVPN settings and recreated it. I also removed all the config on my ThinkPad and recreated the connection. All the certificates and keys are correct. When I try to connect, this is what I get in the log:
Feb 24 16:34:01 openvpn 36285 Initialization Sequence Completed
Feb 24 16:36:56 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:36:56 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)
Feb 24 16:36:58 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:36:58 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)
Feb 24 16:37:02 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:37:02 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)
Feb 24 16:37:10 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:37:10 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)
Feb 24 16:37:26 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:37:26 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)On the client, Wireshark shows only 5 lines of "P_CONTROL_HARD_RESET_CLIENT_V2" and nothing in reply from the server.
Again, I had working OpenVPN prior to this week. However, since the last time it worked, I upgraded to 2.6.0 and made the changes listed in the sticky at the top, so I'm not sure what the issue is.
-
@jknott
Compared to my openvpn server settings - see above - how is your different ?I use Remote Access TLS/SSL ( no user password, just certs).
I have a IPv4 and a IPv6 tunnel, because, why not.
The certs are created ..... way back, as per jimp's Netgate OpenVPN server.
I use pfSense 2.6.0, so my OpenVPN server vertsion is 2.5.4. Assure jourself your OpenVPN client are also recent, not some 2.4.x series.
The cyphers should be : HEADS UP: OpenVPN deprecating shared key mode, requires TLS, deprecating cipher selection
Btw :
These :2022-02-25 04:17:41.830847+01:00 openvpn 37962 tls-crypt unwrap error: packet too short 2022-02-25 04:17:41.830878+01:00 openvpn 37962 TLS Error: tls-crypt unwrapping failed from [AF_INET]146.88.240.4:37537 2022-02-25 10:03:34.546556+01:00 openvpn 37962 tls-crypt unwrap error: packet too short 2022-02-25 10:03:34.546594+01:00 openvpn 37962 TLS Error: tls-crypt unwrapping failed from [AF_INET]185.200.116.50:40380are just IP's that connected to my IPv4 and don't use the correct tls ... so harmless.
Was this you :
[AF_INET6]::ffff:172.16.0.40:44802?
Coming in over some IPv4 converted to IPv6 ....
My WAN is IPv4 only, and :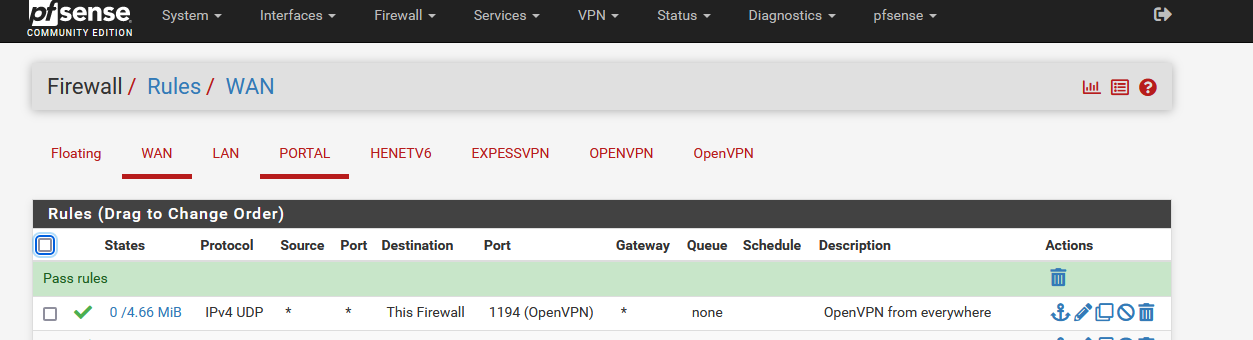
which is the default WAN firewall rule I guess.
-
@gertjan said in OpenVPN Not working after update:
I use Remote Access TLS/SSL ( no user password, just certs).
I have a IPv4 and a IPv6 tunnel, because, why not.Same here. Actually SSL/TLS.
I use pfSense 2.6.0, so my OpenVPN server vertsion is 2.5.4. Assure jourself your OpenVPN client are also recent, not some 2.4.x series.
This may be the problem.
openvpn-2.4.3-5.7.1.x86_64This is the current version in OpenSUSE. Are there changes in the new version (again) that cause earlier versions to fail?
-
@jknott said in OpenVPN Not working after update:
Are there changes in the new version (again) that cause earlier versions to fail?
There are always some pesky minor changes, that's why "just updating" pfSense == updating OpenVPN creates "OpenVPN Not working after update".
The "OpenVPN server" is just a process that listens on a port, typically UDP/1194. That's just a firewall rule, no nat needed.
When the connection doesn't work, that is because the 'client' doesn't understand the 'server', or the other way around.
-
 J JKnott referenced this topic on
J JKnott referenced this topic on