OpenVPN Not working after update
-
No, that's for actual interfaces, such as NICs, VLANs, etc. No mention at all of VPNs in there.
-
My mistake. I was looking under the wrong area.
-
Yeah, that's (2.6.0) new.
When you want to disable an OpenVPN server instance : check the disable box you get this :
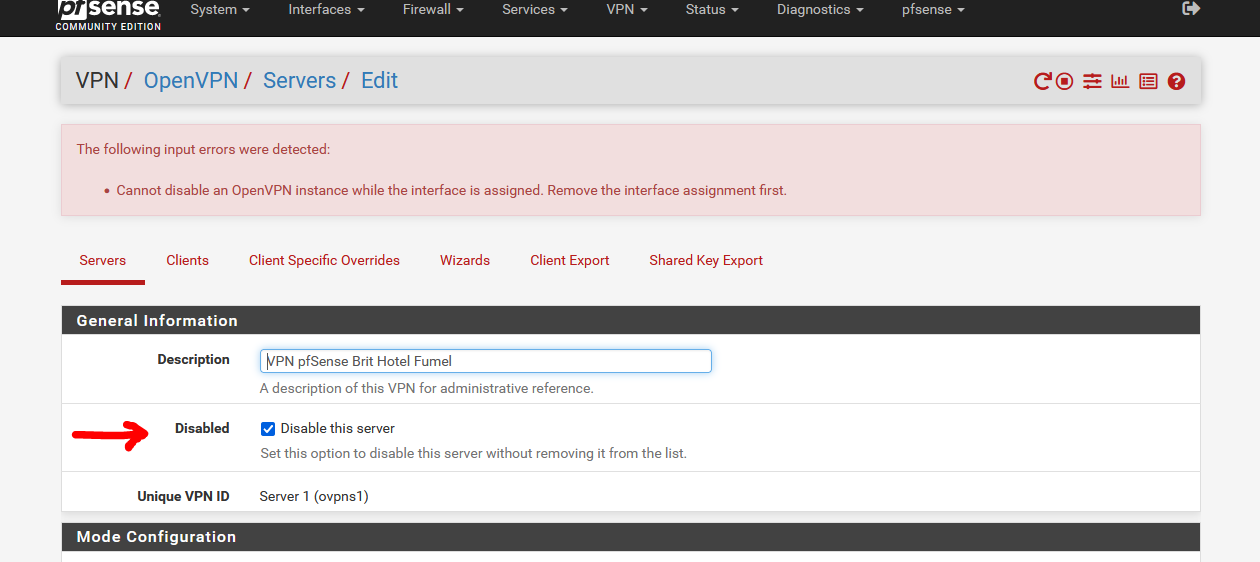
Now, you have to delete or re assign the interface first :
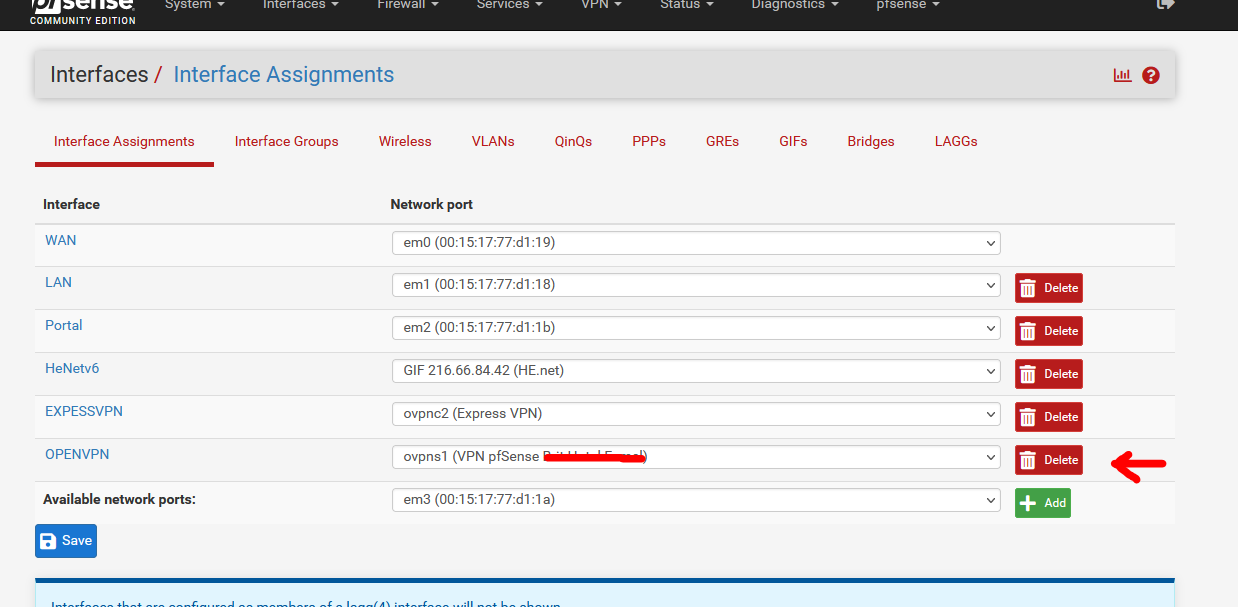
and when done (and saved) you can go back to OpenVPN server instance an shutting it down.
Btw, strange, how little do I know.
More logic, for me, is :
First I stop all processes that uses an interface. (dns mail server web server whatever server)
Then I remove the interface.
This is the other way around.
There must be a reason why it evolved like this. -
I know about disabling a server. However, I have completely stripped out all OpenVPN config and will try again today, if I have time. After making those changes, even restoring a previous pfsense config didn't resolve the problem. This is the second time a pfsense upgrade caused me problems with OpenVPN. What made the first time even more "fun" was I could no longer use my second Internet connection for testing. It's through the same modem and works fine, unless I want to do much more than ping my firewall. So, I now have to test by tethering with my phone. However, I can or at least could get pfsense working by connecting my ThinkPad to my LAN. I pfsense configured to allow OpenVPN connections on any interface.
-
@jknott said in OpenVPN Not working after update:
So, I now have to test by tethering with my phone
All I have to do, is switching the Wifi on my phone to Off.
At that moment I use my 4G/5G data carrier, and with the help of : OpenVPN Connect I connect to my pfSense as a "road warrior".
Lately, it isn't the IPv4 port 1194 UDP that kicks in, it's the IPv6 UDP port 1194 that is used.
This way, I will know it works from an 'unknown' distant IP address, which means I can access my pfSense from everywhere.I'm pretty sure you know all this, why should you have to tether ?
No mobile network available where you are ? -
@gertjan said in OpenVPN Not working after update:
I'm pretty sure you know all this, why should you have to tether ?
No mobile network available where you are ?My Internet connection is via cable modem. For testing, I use my cell phone. I can tether using either WiFi or USB. I don't know what is causing the problem with using my 2nd connection through the cable modem. It used to work fine. Then, after an update, I could no longer use it. When my laptop is connected to the 2nd port on the modem, I have a usual connection to the Internet, but now neither OpenVPN nor ssh work. Ping still does though. I can see the incoming connections, but get no response from pfsense. The IPv4 addresses are on a similar, but different subnet. Given I see the incoming traffic, it's obvious my ISP is not blocking it. My cell and Internet are with the same company, but the cell subnet is completely different from that on my Internet connections. Regardless, I should still be able to set up an OpenVPN connection, when both pfsense and my notebook are on the same LAN. That still worked after that update that killed my usual test connection.
-
I'm about ready to give up. I completely removed all the OpenVPN settings and recreated it. I also removed all the config on my ThinkPad and recreated the connection. All the certificates and keys are correct. When I try to connect, this is what I get in the log:
Feb 24 16:34:01 openvpn 36285 Initialization Sequence Completed
Feb 24 16:36:56 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:36:56 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)
Feb 24 16:36:58 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:36:58 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)
Feb 24 16:37:02 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:37:02 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)
Feb 24 16:37:10 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:37:10 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)
Feb 24 16:37:26 openvpn 36285 tls-crypt unwrap error: packet too short
Feb 24 16:37:26 openvpn 36285 TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:172.16.0.40:44802 (via ::ffff:172.16.0.1%igb1)On the client, Wireshark shows only 5 lines of "P_CONTROL_HARD_RESET_CLIENT_V2" and nothing in reply from the server.
Again, I had working OpenVPN prior to this week. However, since the last time it worked, I upgraded to 2.6.0 and made the changes listed in the sticky at the top, so I'm not sure what the issue is.
-
@jknott
Compared to my openvpn server settings - see above - how is your different ?I use Remote Access TLS/SSL ( no user password, just certs).
I have a IPv4 and a IPv6 tunnel, because, why not.
The certs are created ..... way back, as per jimp's Netgate OpenVPN server.
I use pfSense 2.6.0, so my OpenVPN server vertsion is 2.5.4. Assure jourself your OpenVPN client are also recent, not some 2.4.x series.
The cyphers should be : HEADS UP: OpenVPN deprecating shared key mode, requires TLS, deprecating cipher selection
Btw :
These :2022-02-25 04:17:41.830847+01:00 openvpn 37962 tls-crypt unwrap error: packet too short 2022-02-25 04:17:41.830878+01:00 openvpn 37962 TLS Error: tls-crypt unwrapping failed from [AF_INET]146.88.240.4:37537 2022-02-25 10:03:34.546556+01:00 openvpn 37962 tls-crypt unwrap error: packet too short 2022-02-25 10:03:34.546594+01:00 openvpn 37962 TLS Error: tls-crypt unwrapping failed from [AF_INET]185.200.116.50:40380are just IP's that connected to my IPv4 and don't use the correct tls ... so harmless.
Was this you :
[AF_INET6]::ffff:172.16.0.40:44802?
Coming in over some IPv4 converted to IPv6 ....
My WAN is IPv4 only, and :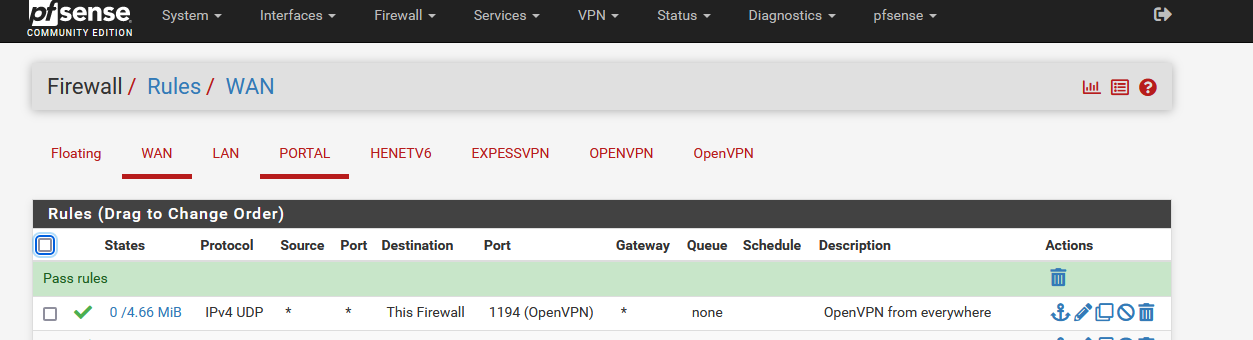
which is the default WAN firewall rule I guess.
-
@gertjan said in OpenVPN Not working after update:
I use Remote Access TLS/SSL ( no user password, just certs).
I have a IPv4 and a IPv6 tunnel, because, why not.Same here. Actually SSL/TLS.
I use pfSense 2.6.0, so my OpenVPN server vertsion is 2.5.4. Assure jourself your OpenVPN client are also recent, not some 2.4.x series.
This may be the problem.
openvpn-2.4.3-5.7.1.x86_64This is the current version in OpenSUSE. Are there changes in the new version (again) that cause earlier versions to fail?
-
@jknott said in OpenVPN Not working after update:
Are there changes in the new version (again) that cause earlier versions to fail?
There are always some pesky minor changes, that's why "just updating" pfSense == updating OpenVPN creates "OpenVPN Not working after update".
The "OpenVPN server" is just a process that listens on a port, typically UDP/1194. That's just a firewall rule, no nat needed.
When the connection doesn't work, that is because the 'client' doesn't understand the 'server', or the other way around.
-
 J JKnott referenced this topic on
J JKnott referenced this topic on