Firewall UDP ? Attack !! Or Normal ?
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
@silence why did you truncate the capture.. can not see full payload - so really hard to tell what that is.. But from the ttl on the packets, they are very low, and seem to increment - but they also seem out of order? when a traceroute would count down, or up etc.. depending on where your capturing etc..
On the tracewrangler make sure you uncheck everything other than changing the IP..
So either these are after many many hops.. Or what is sending them is changing the ttl, like in traceroute..
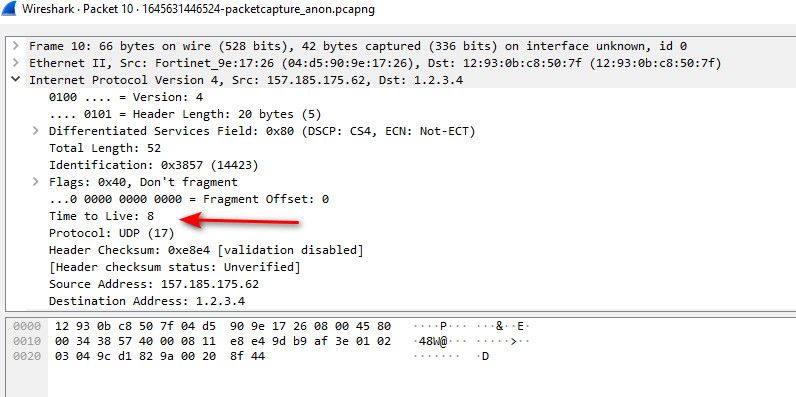
But as mentioned - other than a curiosity, you can't really stop someone from sending you traffic.. Unless you control the sender.. So while trying to figure out what this is - not much you can do about it.. So you could just drop it without logging it if its causing you grief in seeing it in the logs..
Normally traceroute - see how the ttl is changing..
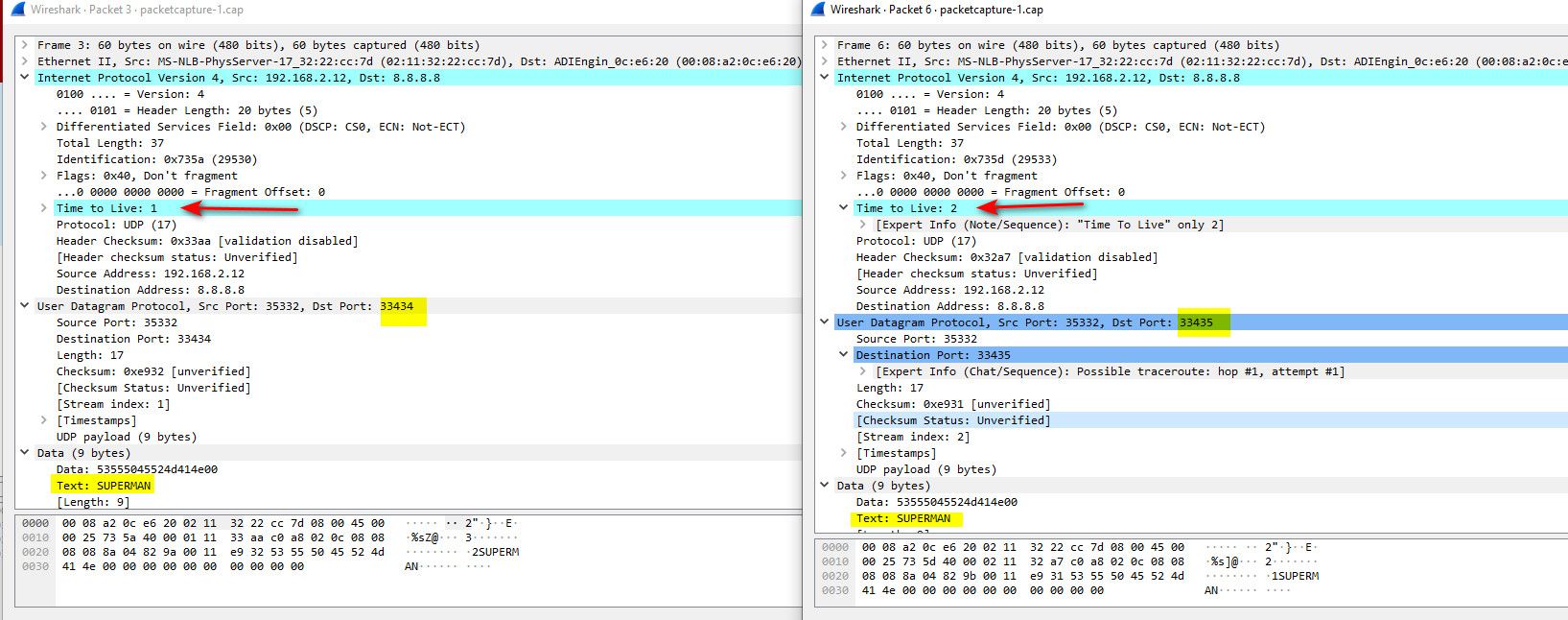
See how the data is specific.. different traceroute programs might send different text.. Also normally the source port would be same
see how source port is the same, and the port is increasing..
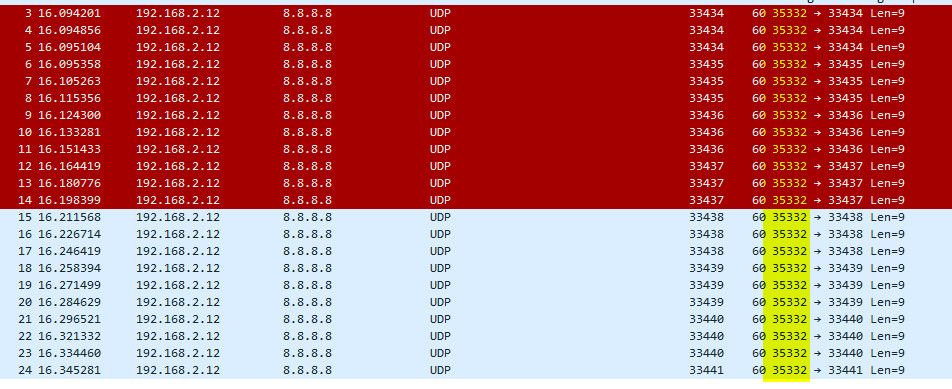
And sent in groups of 3..
update
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
Normally traceroute - see how the ttl is changing..
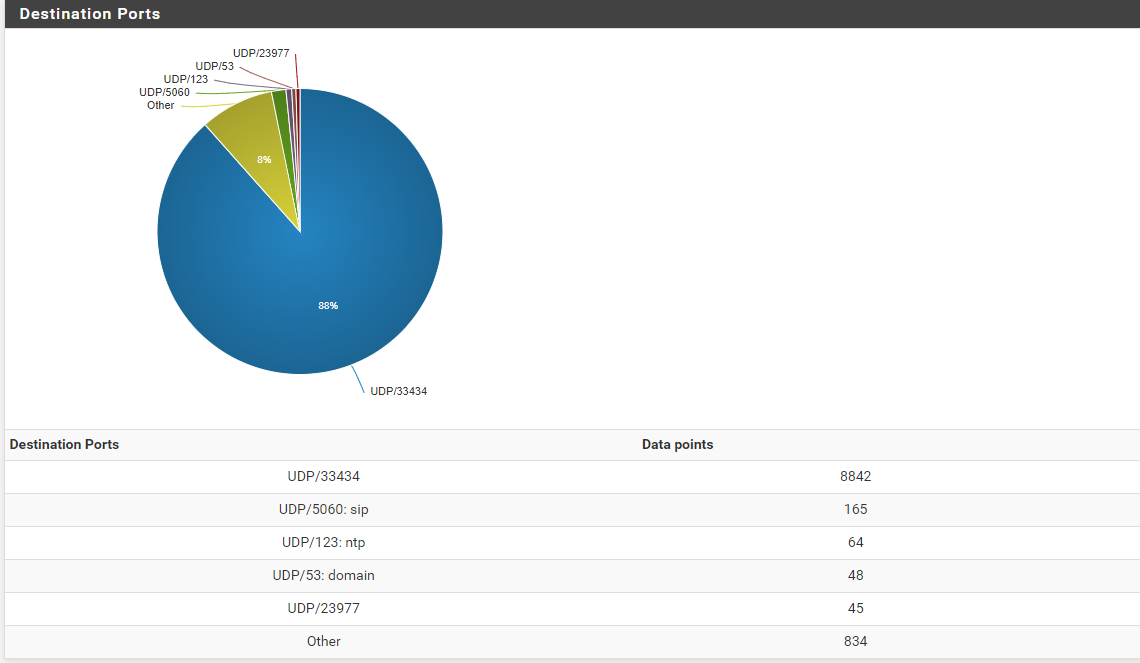
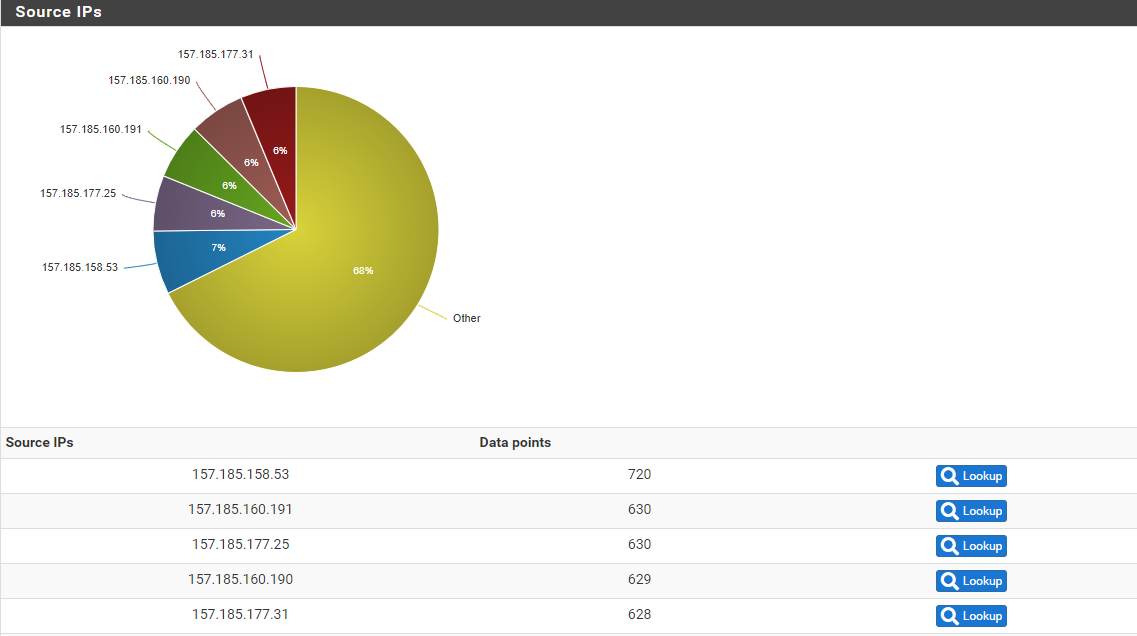
So, should I just ignore that a Network 0/16 is sending traffic to port 33434 to my wan?
simply because you can not determine your goal ?
Also the port is always 33434 I don't think it's a simple traceroute.
rather it seems to me that someone with access to this entire /16 network tries to execute something against my wan
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
@silence why did you truncate the capture.. can not see full payload - so really hard to tell what that is.. But from the ttl on the packets, they are very low, and seem to increment - but they also seem out of order? when a traceroute would count down, or up etc.. depending on where your capturing etc..
On the tracewrangler make sure you uncheck everything other than changing the IP..
So either these are after many many hops.. Or what is sending them is changing the ttl, like in traceroute..

But as mentioned - other than a curiosity, you can't really stop someone from sending you traffic.. Unless you control the sender.. So while trying to figure out what this is - not much you can do about it.. So you could just drop it without logging it if its causing you grief in seeing it in the logs..
Normally traceroute - see how the ttl is changing..

See how the data is specific.. different traceroute programs might send different text.. Also normally the source port would be same
see how source port is the same, and the port is increasing..

And sent in groups of 3..
@johnpoz I think I found something that could be the error, but I need a little of your help to determine or confirm my theory.
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
rather it seems to me that someone with access to this entire /16 network tries to execute something against my wan
That seems to be a bit tight on the tinfoil hat ;)
Now that port range could also be older SIP calls 33434-33598
Many of the packets are sending the same data.. But can not make out what it is exactly
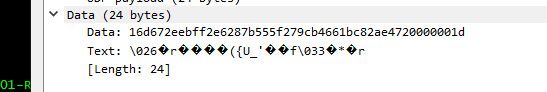
There are some others that are duplicated as well.
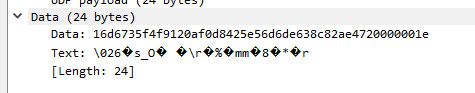
It just a guess of mine that 33434 UDP was traceroute - doesn't mean it actually is that.. Other stuff could use that port.. webex teams, Noction version of bgp I think..
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
Now that port range could also be older SIP calls 33434-33598
Do a tracert from another ISP
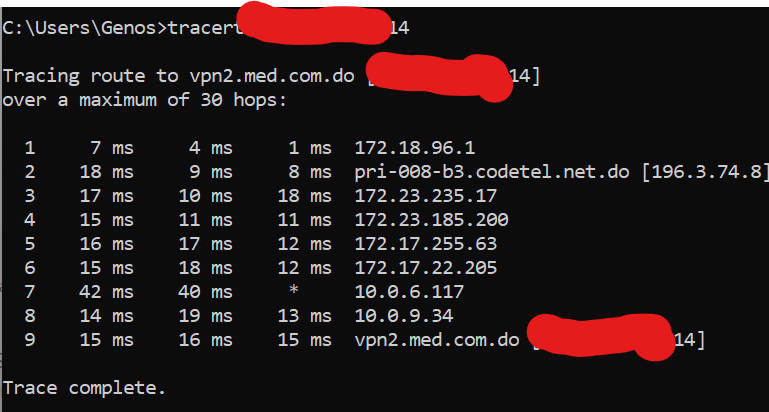
And I found this at the end next to my wan ip 13 ms vpn2.med.com.do [1.2.3.4]but if I do tracert to this domain it shows 179.51.66.42
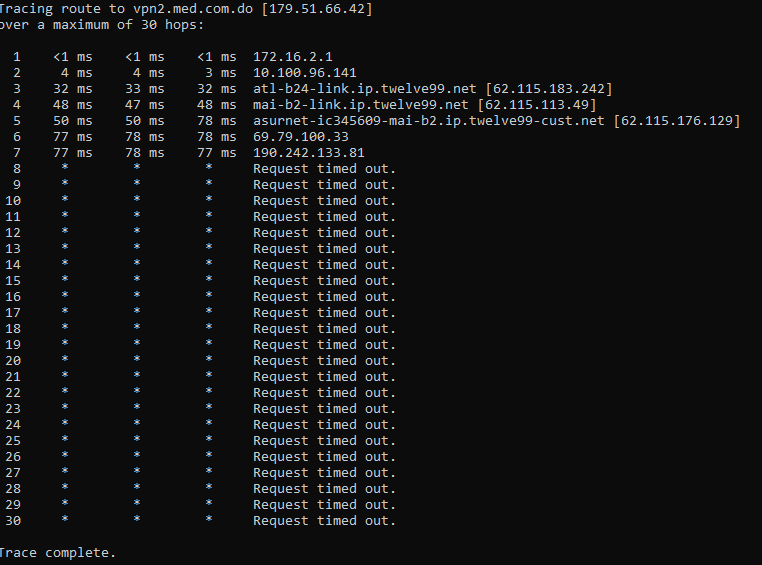
179.51.66.42 no is my ip
I think it is a problem with our ISP Report immediately.
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
should I just ignore that a Network 0/16 is sending traffic to port 33434 to my wan
I would. I'm not trying to be difficult, but it seems like figuring out each connection is like playing whack-a-mole. I would assume the entire Internet is hostile territory, and block all inbound traffic (the default on pfSense). If it was your IP block, or a "known" IP then that might be worth pursuing. Otherwise bots doing the scanning will just move on eventually.
When we first set up Suricata years ago its default is to use WAN, and in reality that just wastes a lot of time scanning packets that will be dropped by the firewall anyway. I would guess alerts dropped 90-95% by moving Suricata's scanning to LAN, even though we had a couple of web servers and other open ports.
-
@steveits said in Firewall UDP ? Attack !! Or Normal ?:
but it seems like figuring out each connection is like playing whack-a-mole
exactly - especially when there is really nothing you can do about it. Its blocked anyway - so other than curiosity there isn't much in the way of doing anything.
While it might be annoying, unless it was some serious amount of traffic that would/could cause you grief in bandwidth there isn't a lot of reason to spend too many cycles on it - other than just plain old curiosity of what it is, or what they are looking for, etc.
It can be really easy to go down a crazy rabbit hole trying to put some reason behind what amounts to "noise" ;)
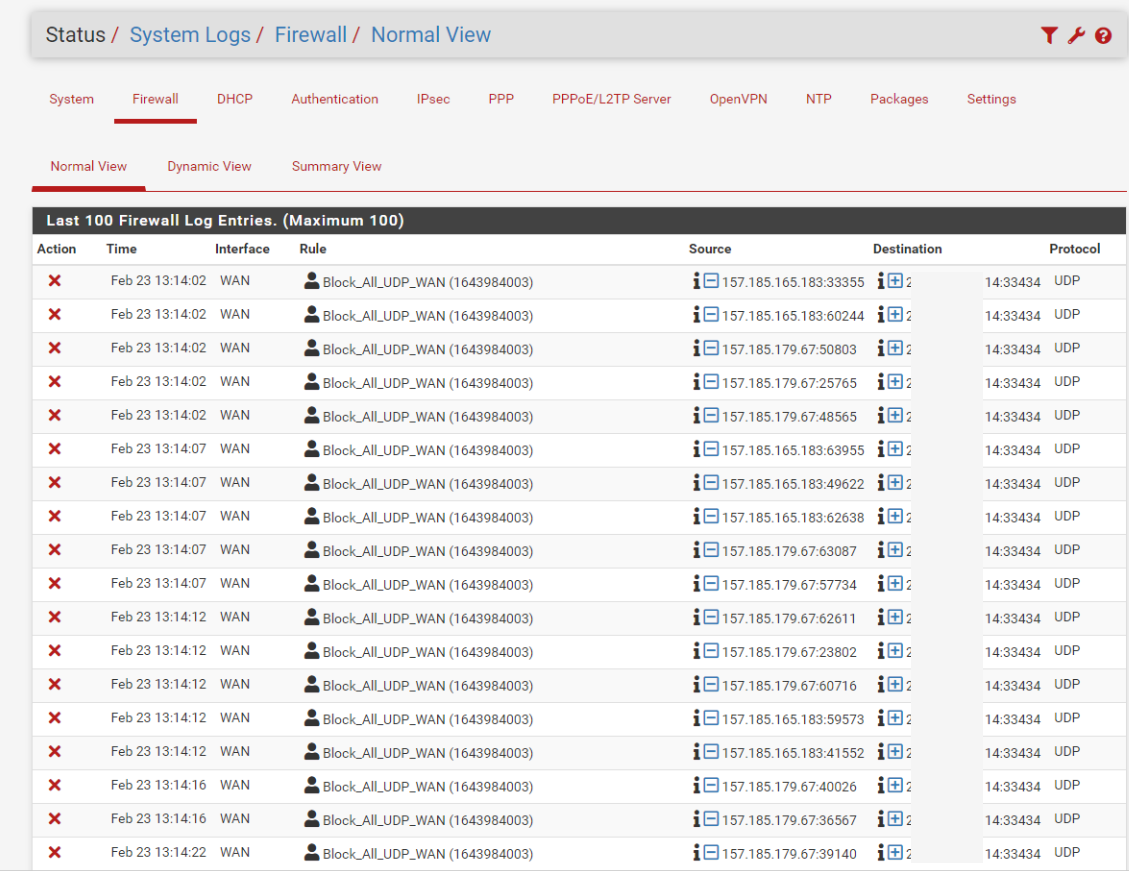
I looked for any traffic to my wan on that port 33434.. but I don't log that, I have added that port to my udp ports I log.. And see if see anything on it the next couple of days. But I don't log most noise - because for one my curiosity gets me spending cycles that go nowhere..
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
I looked for any traffic to my wan on that port 33434.. but I don't log that, I have added that port to my udp ports I log.. And see if see anything on it the next couple of days. But I don't log most noise - because for one my curiosity gets me spending cycles that go nowhere..
did you see the previous picture?
This is already the case of my isp, they are repairing it right now.
But I'm still curious how this could happen.
and by the way the noise is so great that 10k logs are received in less than 5 - 10 minutes
-
@silence you must of posted the wrong thing because I see nothing in there that says 13 ms on it or the name, etc. Not sure what your trying to show..
-
@johnpoz The "tracing route to" in the first line.
Here, vpn2.med.com.do resolves to 179.51.66.42.
-
@steveits ok maybe I just being dense.. What does that have to do with anything?
There are plenty of places can not do a full traceroute too on the internet ;)
user@NewUC:~$ traceroute vpn2.med.com.do traceroute to vpn2.med.com.do (179.51.66.42), 64 hops max 1 192.168.2.253 0.667ms 0.413ms 0.179ms 2 69.47.60.1 10.371ms 9.718ms 8.949ms 3 10.52.33.194 11.818ms 9.025ms 14.059ms 4 76.73.164.154 12.929ms 11.570ms 13.042ms 5 75.76.101.196 13.852ms 14.949ms 11.736ms 6 24.96.2.57 31.869ms 31.934ms 31.785ms 7 75.76.35.115 34.612ms 32.049ms 35.030ms 8 * 198.32.132.75 42.022ms 32.846ms 9 184.105.223.234 43.966ms 43.807ms 42.766ms 10 209.51.168.70 46.741ms 45.828ms 44.903ms 11 216.66.15.254 57.785ms 49.680ms 73.956ms 12 * * * 13 * * * 14 190.242.133.81 73.989ms 75.487ms 74.031ms 15 * * * 16 * * * 17 * * * 18 * * *Oh know that fails - better call my isp? Not sure what that is suppose to show?
-
@johnpoz I think he was expecting an IP that isn't 179.51.66.42.
@Silence it also could be the reverse DNS is showing the wrong hostname. I see that more than one would expect.
-
tracert from other ISP To my IP WAN
I think I did not explain myself well, sorry, when my ip wan is traced, a domain vpn2.med.com.do is shown like this
So when I do a tracer to this domain vpn2.med.com.do it shows a wan ip 179.51.66.42
this domain and this ip wan are not mine I do not recognize it!
at the end of the day thanks to my curiosity I found a bug, I already knew that it was not normal to see this traffic sent to 33434 in my wan.
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
when my ip wan is traced, a domain vpn2.med.com.do is shown
That's the reverse DNS (PTR record) and is up to the ISP to set a hostname. I've seen several cases over the years where a client gets an IP from an ISP and it has an old hostname. Heck, I've forgotten to update the PTR record once or twice on servers we host.
Run "nslookup -type x.x.x.x" with your WAN IP and if I understand your posts correctly it will return the vpn2.med.com.do name. Not much you can do about it other than ask your ISP to remove it. Most either do without or put in something generic by default.
-
@silence @SteveITS ok I get a PTR or forward being wrong.. But now this 2nd trace is all rfc1918 address space?
Other than hop 2 and hop 9? your hiding.. So now even more confused ;) hehehe
Would you mind sharing what your public IP is via a message to me? So its not public - but if they fix that fqdn, you understand anyone will be able to lookup your IP.. So maybe you want to hide that as well?
-
This is just traffic received without any client using this wan, so all this comes from the noise in 33434.
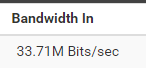
-
@silence 33Mbps - yeah that sure seems quite excessive..
Still trying to understand your setup and your mention of some fqdn which I take is yours not resolving to your IP? If its not resolving to yours.. Then how could it generate traffic to you?
179.51.66.42 no is my ip
Then your latest traceroute is all rfc1918 address space? Other maybe 2 hops?
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
trace is all rfc1918 address space
Maybe "within" the VPN service?
@silence said in Firewall UDP ? Attack !! Or Normal ?:
traffic received without any client using this wan
Oh, that's noticeable then. The original log image was a handful of packets every few seconds. 33 Mbit/s has to be way more than that... (and I definitely wouldn't log it)
Are you using a VPN to connect out from/on pfSense? If you disconnect that what happens?
Here's a wild theory, did your WAN IP belong to a VPN company? And this is something/someone still trying to connect to it? If that's the case there may not be much you can do except contact your ISP to block the traffic. If it's all on one port that shouldn't be that hard, if they can/will do it. Lead with the 33 Mbit/s. :) Or maybe they can give you a new IP and let this one sit on the shelf for a while.
-
@steveits said in Firewall UDP ? Attack !! Or Normal ?:
Are you using a VPN to connect out from/on pfSense
In that case, the case is closed.
The IP you get from a VPN is never .... "not new, made for you, and has no usage history".
IP are recycled among users, have a history, and because it's from an VPN ISP, it has been used for horrible things, or worse.
If your IP was used just before you got it by you by some bad-ass 'let's go attack all 3 letter agencies" hacker-wannabee, then yeah, you will see a lot of activity on your IP. Some one want to know where you are, as they didn't figured out yet some one else is hiding behind the IP.If you want a clean(er) IP from a VPN ISP ? That's possible. I bet the more expensive ones proposes more proposes (read : less abused) IP's.
If you use a VPN IP, then follow this excellent advise :
@steveits said in Firewall UDP ? Attack !! Or Normal ?:
(and I definitely wouldn't log it)
Btw : I'm still curious about what the traffic actually is, what it contains. But if its TLS wrapped up, or, has no payload at all, again, ditch it. Live is already to short.
-
@gertjan said in Firewall UDP ? Attack !! Or Normal ?:
I'm still curious about what the traffic actually is
Yeah same here - he did post a pcap with the payload.. I posted what I saw in some of them.. It is odd traffic to be sure. And the TTLs on the packets are also odd.. From the TTLs you would think traceroute, but they don't seem to be changing correctly, and the port not changing - unless he was missing the parts of the traffic in his sniff.