Firewall UDP ? Attack !! Or Normal ?
-
@silence you must of posted the wrong thing because I see nothing in there that says 13 ms on it or the name, etc. Not sure what your trying to show..
-
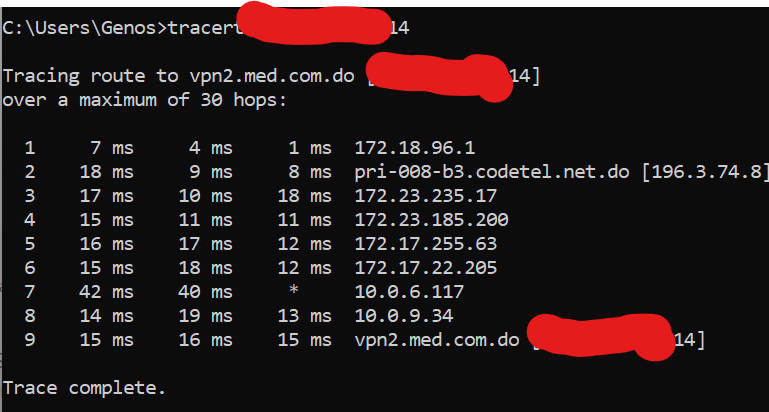
@johnpoz The "tracing route to" in the first line.
Here, vpn2.med.com.do resolves to 179.51.66.42.
-
@steveits ok maybe I just being dense.. What does that have to do with anything?
There are plenty of places can not do a full traceroute too on the internet ;)
user@NewUC:~$ traceroute vpn2.med.com.do traceroute to vpn2.med.com.do (179.51.66.42), 64 hops max 1 192.168.2.253 0.667ms 0.413ms 0.179ms 2 69.47.60.1 10.371ms 9.718ms 8.949ms 3 10.52.33.194 11.818ms 9.025ms 14.059ms 4 76.73.164.154 12.929ms 11.570ms 13.042ms 5 75.76.101.196 13.852ms 14.949ms 11.736ms 6 24.96.2.57 31.869ms 31.934ms 31.785ms 7 75.76.35.115 34.612ms 32.049ms 35.030ms 8 * 198.32.132.75 42.022ms 32.846ms 9 184.105.223.234 43.966ms 43.807ms 42.766ms 10 209.51.168.70 46.741ms 45.828ms 44.903ms 11 216.66.15.254 57.785ms 49.680ms 73.956ms 12 * * * 13 * * * 14 190.242.133.81 73.989ms 75.487ms 74.031ms 15 * * * 16 * * * 17 * * * 18 * * *Oh know that fails - better call my isp? Not sure what that is suppose to show?
-
@johnpoz I think he was expecting an IP that isn't 179.51.66.42.
@Silence it also could be the reverse DNS is showing the wrong hostname. I see that more than one would expect.
-
tracert from other ISP To my IP WAN
I think I did not explain myself well, sorry, when my ip wan is traced, a domain vpn2.med.com.do is shown like this
So when I do a tracer to this domain vpn2.med.com.do it shows a wan ip 179.51.66.42
this domain and this ip wan are not mine I do not recognize it!
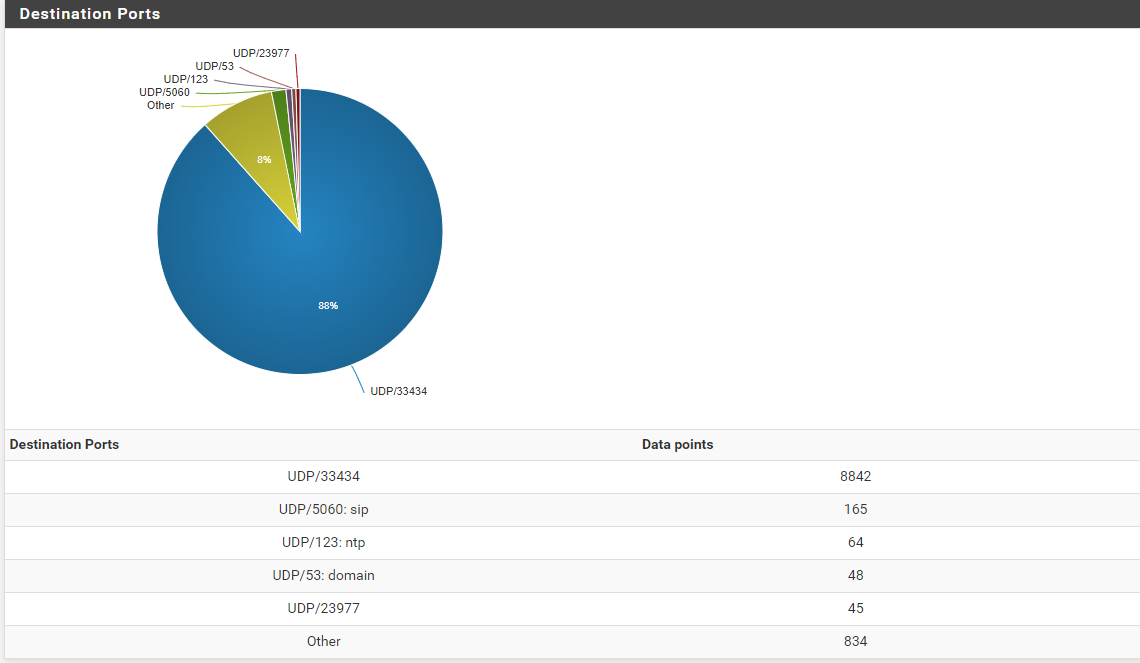
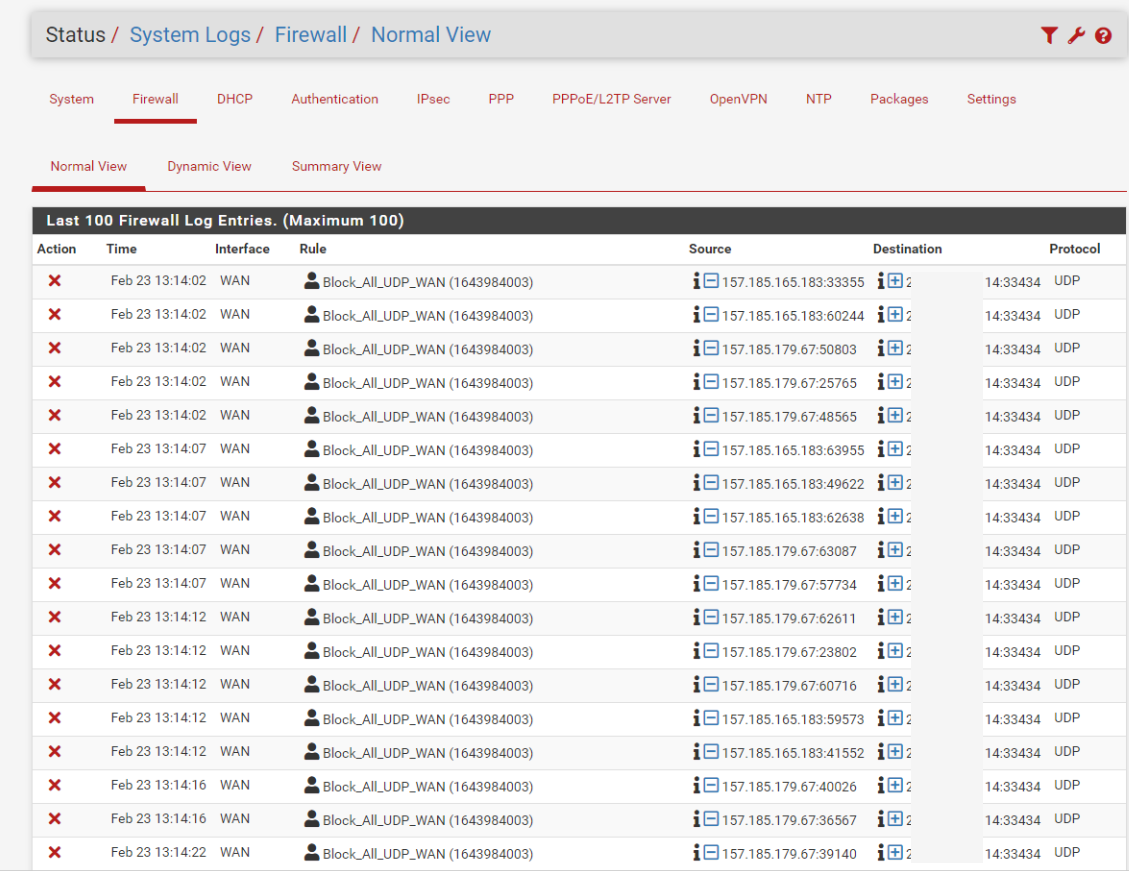
at the end of the day thanks to my curiosity I found a bug, I already knew that it was not normal to see this traffic sent to 33434 in my wan.
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
when my ip wan is traced, a domain vpn2.med.com.do is shown
That's the reverse DNS (PTR record) and is up to the ISP to set a hostname. I've seen several cases over the years where a client gets an IP from an ISP and it has an old hostname. Heck, I've forgotten to update the PTR record once or twice on servers we host.
Run "nslookup -type x.x.x.x" with your WAN IP and if I understand your posts correctly it will return the vpn2.med.com.do name. Not much you can do about it other than ask your ISP to remove it. Most either do without or put in something generic by default.
-
@silence @SteveITS ok I get a PTR or forward being wrong.. But now this 2nd trace is all rfc1918 address space?
Other than hop 2 and hop 9? your hiding.. So now even more confused ;) hehehe
Would you mind sharing what your public IP is via a message to me? So its not public - but if they fix that fqdn, you understand anyone will be able to lookup your IP.. So maybe you want to hide that as well?
-
This is just traffic received without any client using this wan, so all this comes from the noise in 33434.
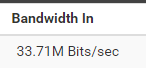
-
@silence 33Mbps - yeah that sure seems quite excessive..
Still trying to understand your setup and your mention of some fqdn which I take is yours not resolving to your IP? If its not resolving to yours.. Then how could it generate traffic to you?
179.51.66.42 no is my ip
Then your latest traceroute is all rfc1918 address space? Other maybe 2 hops?
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
trace is all rfc1918 address space
Maybe "within" the VPN service?
@silence said in Firewall UDP ? Attack !! Or Normal ?:
traffic received without any client using this wan
Oh, that's noticeable then. The original log image was a handful of packets every few seconds. 33 Mbit/s has to be way more than that... (and I definitely wouldn't log it)
Are you using a VPN to connect out from/on pfSense? If you disconnect that what happens?
Here's a wild theory, did your WAN IP belong to a VPN company? And this is something/someone still trying to connect to it? If that's the case there may not be much you can do except contact your ISP to block the traffic. If it's all on one port that shouldn't be that hard, if they can/will do it. Lead with the 33 Mbit/s. :) Or maybe they can give you a new IP and let this one sit on the shelf for a while.
-
@steveits said in Firewall UDP ? Attack !! Or Normal ?:
Are you using a VPN to connect out from/on pfSense
In that case, the case is closed.
The IP you get from a VPN is never .... "not new, made for you, and has no usage history".
IP are recycled among users, have a history, and because it's from an VPN ISP, it has been used for horrible things, or worse.
If your IP was used just before you got it by you by some bad-ass 'let's go attack all 3 letter agencies" hacker-wannabee, then yeah, you will see a lot of activity on your IP. Some one want to know where you are, as they didn't figured out yet some one else is hiding behind the IP.If you want a clean(er) IP from a VPN ISP ? That's possible. I bet the more expensive ones proposes more proposes (read : less abused) IP's.
If you use a VPN IP, then follow this excellent advise :
@steveits said in Firewall UDP ? Attack !! Or Normal ?:
(and I definitely wouldn't log it)
Btw : I'm still curious about what the traffic actually is, what it contains. But if its TLS wrapped up, or, has no payload at all, again, ditch it. Live is already to short.
-
@gertjan said in Firewall UDP ? Attack !! Or Normal ?:
I'm still curious about what the traffic actually is
Yeah same here - he did post a pcap with the payload.. I posted what I saw in some of them.. It is odd traffic to be sure. And the TTLs on the packets are also odd.. From the TTLs you would think traceroute, but they don't seem to be changing correctly, and the port not changing - unless he was missing the parts of the traffic in his sniff.
-
Ok I will try to explain as best as possible, and sorry for my bad English (I really only speak Spanish)
Well I have a year running everything fine in pfsense using an internet provider.
but 1 month ago I decided to add a new internet provider for redundancy purposes.
Well, this is the situation, the fiber that I receive from this Internet provider is directly connected to Proxmox (I have several Pfsense here)
I created a new pfsense for this new internet provider, they offer me the ip 1.2.3.4/29, I configured everything and everything was fine, the service went up without problem... I created the firewall rule normally as I am used to...
I started noticing strange traffic to the same port 33434 but I ignored it.
when it came time to actually use this redundancy and my ISP 1 Failed.
I moved about 200 clients to My New Pfsense with the new wan/29 as they started telling me they felt a bit slow.
which was very strange because in the previous pfsense with the previous isp they had the exact same internet speed and it was never slow.
Well, in the end I moved all this client to the old pfsense with my old Wan and everything works great.
Now Monitoring the incoming traffic of my WAN interface (TO MY MAIN IP) a lot of packets arrive at port 33434 UDP As you could see in the previous photo abc exceeds 30mbps which is very high for normal internet traffic.
Well, I investigated, I used my other WAN to do an nslookup to my New IP And I discovered the following in name: it shows vpn2.med.com.do
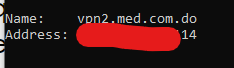
so I did another nslookup to this name vpn2.med.com.do and it shows me the following IP 179.51.66.42
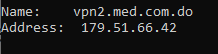
As you can see, something is not right, so I told my new isp about this, but I still haven't gotten a response.
the thing is that this service is impossible to use in this way.
That's why at the beginning of the publication I asked this, is it normal? or am I under a ddos attack?
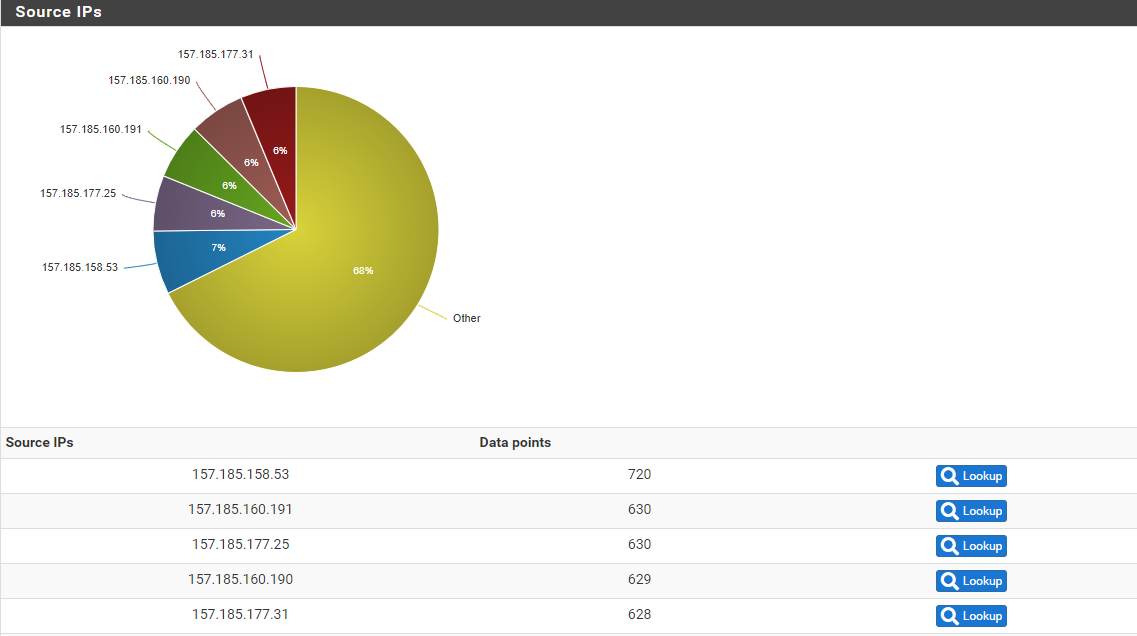
In case you are wondering, where does this traffic come from because they come from everywhere, at the beginning I only saw a network 157.185.0.0/16 now I see any IP pointing to 33434 or 33224
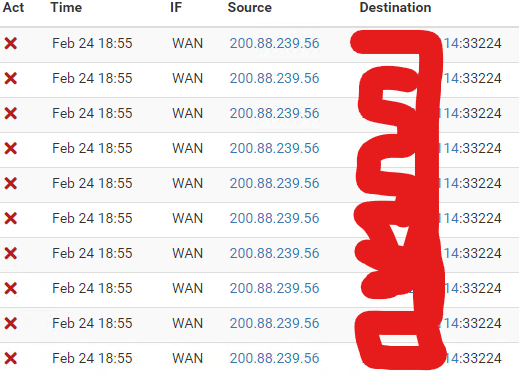
By the way, here I leave my dashboard in case it is important.
@stephenw10 I would like to hear your opinion on this.
I did a nat just to capture this on my pc directly.
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
am I under a ddos attack?
A DoS attack is usually much higher volume and I would think be on other ports like 80/443. Normally a DoS attack's goal is to connect to some service (like a web server or DNS server) and make the service respond, to keep the server busy.
I think your ISP needs to answer the questions:
- can they block the traffic?
- was your IP being used by someone else, perhaps a VPN provider?
A similar example is that most phone companies won't immediately re-use a phone number. They wait a while so the new customer doesn't get calls for the old customer.
Random traffic probing any IP connected to the Internet is normal; they are scanning all IPs on the Internet looking for servers to exploit. A high volume of traffic coming to one specific port is not normal.
I would definitely not log each packet, that's just unnecessary CPU time and SSD write life wear.
-
@steveits said in Firewall UDP ? Attack !! Or Normal ?:
was your IP being used by someone else, perhaps a VPN provider?
Investigating myself, it seems to me that if the old owner of the IP offered vpn service and apparently all his clients try to connect.
-
@steveits said in Firewall UDP ? Attack !! Or Normal ?:
can they block the traffic?
I am more interested in the case of nslookup
I did the same process with the other ip of my service of /29 and there are only 2 ip of this that show this behavior when I do nslookup
I am sure that if you solve this... I should no longer receive this type of traffic and it is much better than canceling my rule, because I am really interested in registering all types of UDP in my wan
-
@silence The incorrect reverse DNS/PTR record isn't going to hurt you though, it is just incorrect. Unless you have a mail server on your LAN, in which case some/many mail servers on the Internet demand the forward and reverse DNS lookups match, in an effort to block spammers.
To log other UDP, you could make a rule above that rule:
block UDP on WAN:33224, do not log
block UDP on WAN, log -
@silence
Yupp
Something seems a bit fishy with the PTR's
$ host 1.2.3.4 4.3.2.1.in-addr.arpa domain name pointer vpn2.med.com.do. $ host 179.51.66.42 42.66.51.179.in-addr.arpa domain name pointer vpn2.med.com.do. $ host vpn2.med.com.do vpn2.med.com.do has address 179.51.66.42Do you own (use) both of these ip's , i mean primary line vs secondary ?
-
@bingo600 said in Firewall UDP ? Attack !! Or Normal ?:
1.2.3.4
This is my real wan ip can you put 1.2.3.4 please? XD
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
@bingo600 said in Firewall UDP ? Attack !! Or Normal ?:
1.2.3.4
This is my real wan ip can you put 1.2.3.4 please? XD
Done ...
It wasn't me that posted a tonn of those "real" IP's in the pict here
https://forum.netgate.com/post/1028590