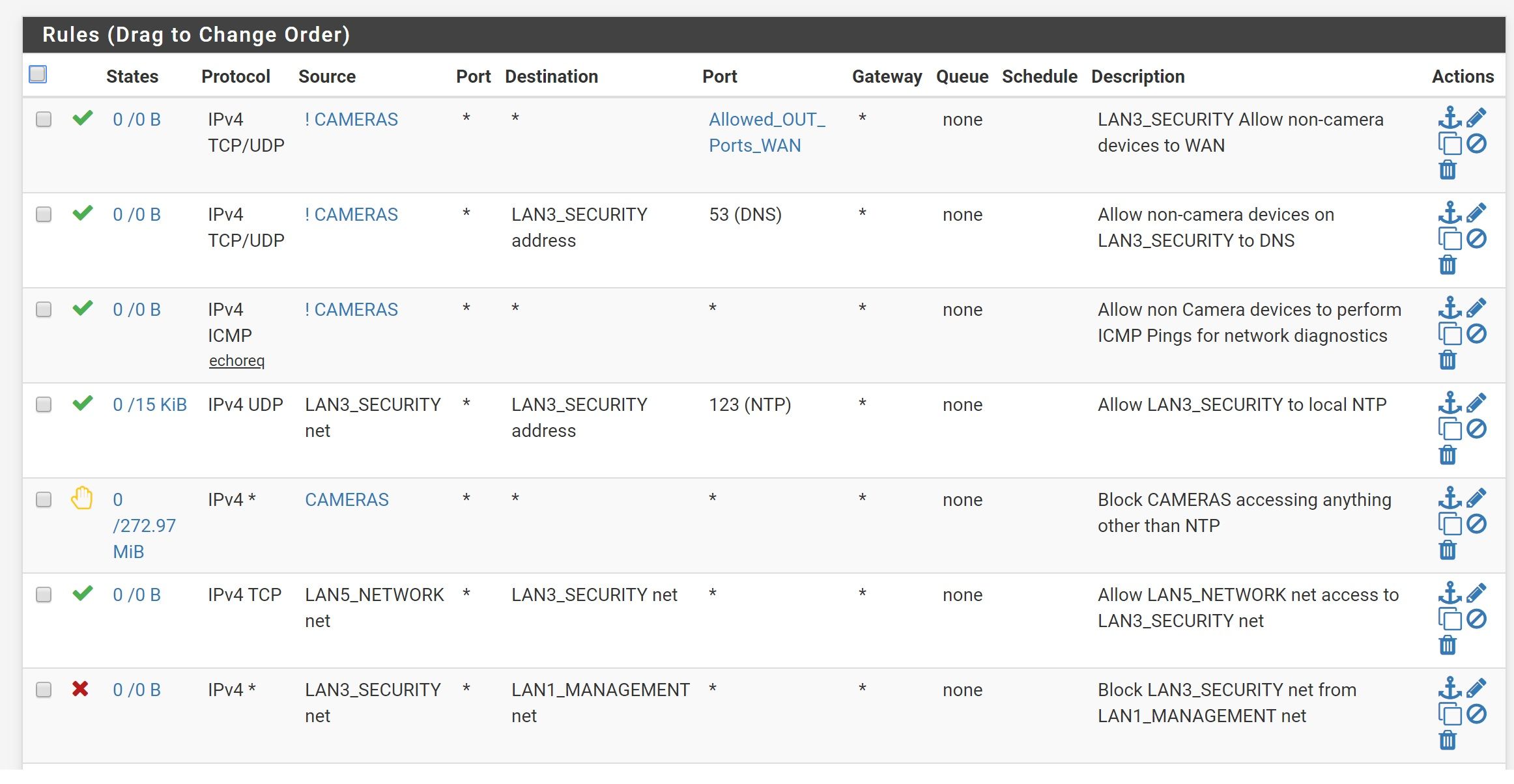
Problem...Graph Shows Traffic Crossing VLANs
-
And what are you trying to do with the pass rules for ! CAMERAS?
Put the reject rule for source CAMERAS above those and just pass to any after that.
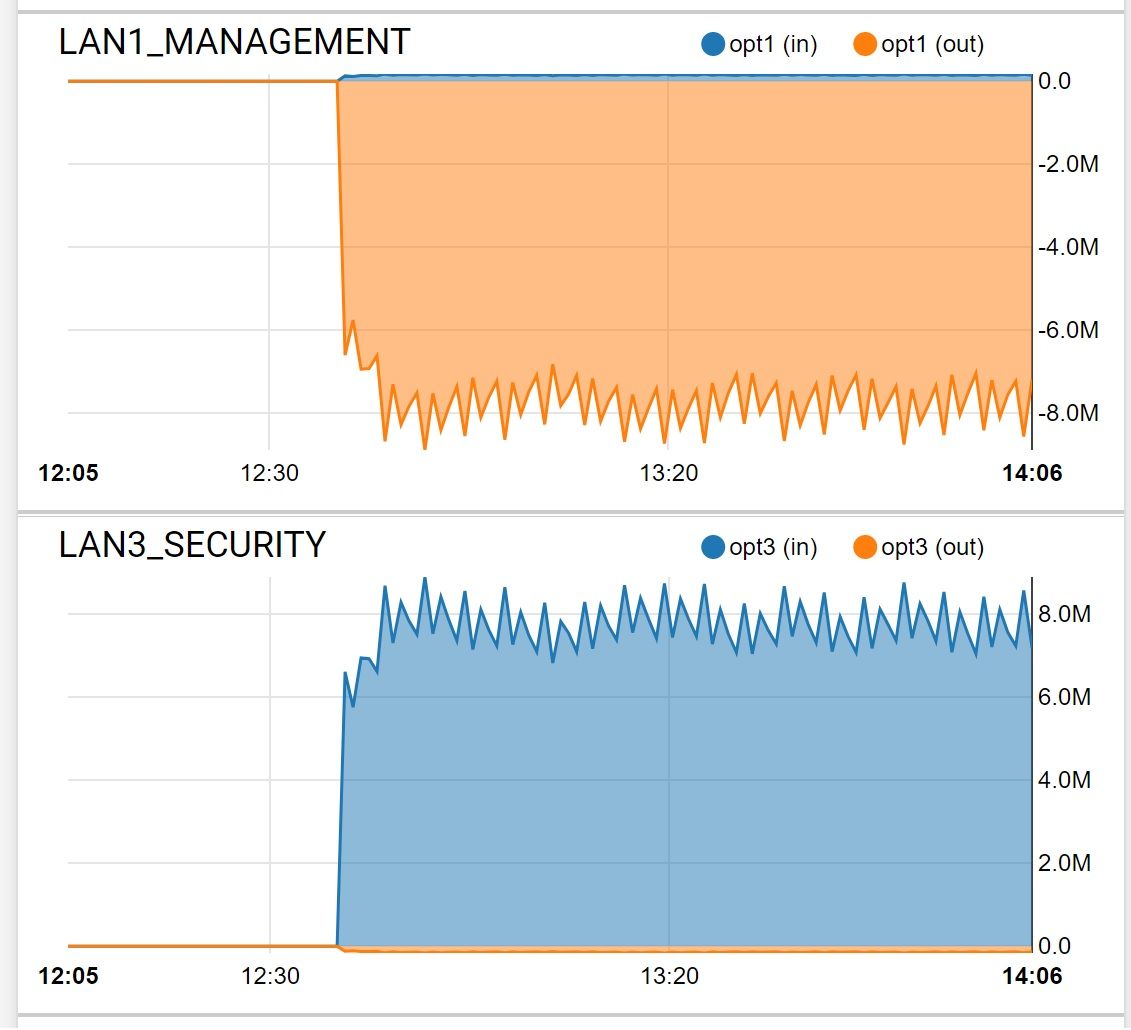
But either way, it's VLAN1 that I'm wondering about and why it every so often will randomly mirror VLAN3 in the traffic graph. I just reset pfSense and it's back to normal.
Something on LAN3 sending to something on LAN1? If the port matches the Allowed_OUT_Ports_WAN alias, it will be passed to LAN1 destinations because you are not blocking those.
-
how can put this .
-
@johnpoz said in Problem...Graph Shows Traffic Crossing VLANs:
@ARAMP1 said in Problem...Graph Shows Traffic Crossing VLANs:
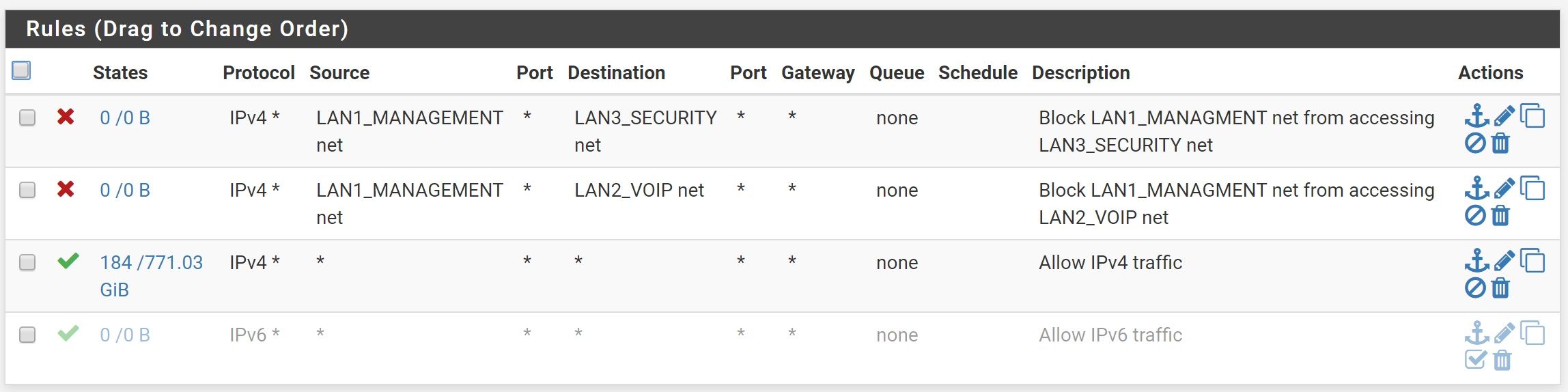
That rule is there to allow all traffic from VLAN5 to access VLAN3
Doesn't work that way!!! If you want vlan 3 to talk to vlan 5, then the rule would be on vlan 3 interface with vlan 5 ad the dest.. Vlan 5 could never be a source into vlan 3 interface.
Yeah. I actually had the same rule over in VLAN5's rules. I went ahead and deleted it under VLAN3. Appreciate you pointing it out.
-
@Derelict said in Problem...Graph Shows Traffic Crossing VLANs:
And what are you trying to do with the pass rules for ! CAMERAS?
All the pass rules for for invert match CAMERAS, so it should pass those rules for everything but the cameras, correct? Basically, I want to allow my Blue Iris computer to access to WAN and DNS without allowing the cameras.
The only pass rule I have for the whole net is for port 123 to allow the cameras to have access to NTP.
Put the reject rule for source CAMERAS above those and just pass to any after that.
I'll rewrite.
But either way, it's VLAN1 that I'm wondering about and why it every so often will randomly mirror VLAN3 in the traffic graph. I just reset pfSense and it's back to normal.
Something on LAN3 sending to something on LAN1? If the port matches the Allowed_OUT_Ports_WAN alias, it will be passed to LAN1 destinations because you are not blocking those.
Looking at my Allowed_OUT_Ports_WAN alias list now. Thanks.
-
Its real simple to figure out what will pass and what will not..
You know the source, you know the dest and port..
Walk down your rules from the top on the interface the source is going to first hit pfsense on.. So vlan 3 device, on vlan 3, if vlan 1 device then vlan 1..
To down walk through your rules.. First rule to trigger wins, no other rules are evaluted.. If you get through all the rules - and nothing passed it then the the default deny will block it.
Your inverse camera rules, the top 3 have zero hits on them..
Seems odd to be honest that you let cameras do anything your 5th rule, but non cameras can only go use specific ports and dns?
-
@Derelict said in Problem...Graph Shows Traffic Crossing VLANs:
Put the reject rule for source CAMERAS above those and just pass to any after that.
Maybe I'm not looking at this right. Will this work for my first rule? Block cameras from all except port 123.
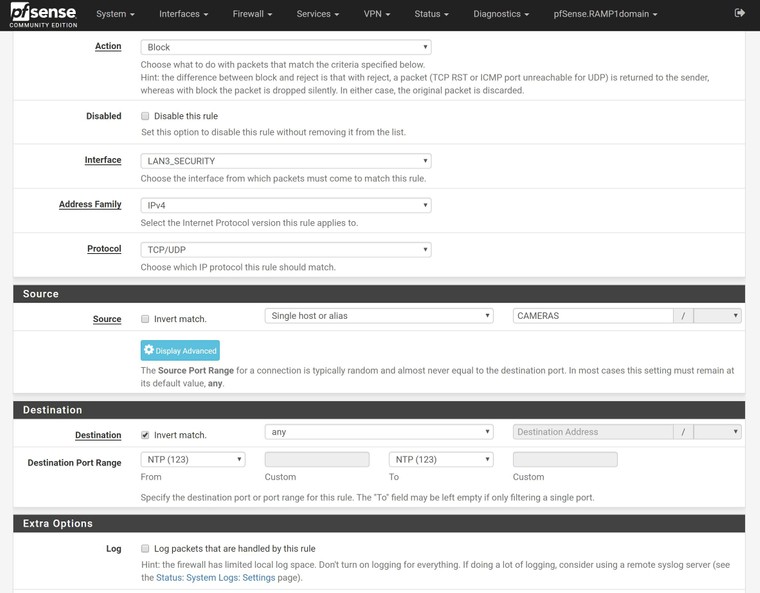
Might need to set this aside for a bit and then come back to it.
-
Don't check invert match. That checkbox is, in my opinion, almost never the proper solution and there is almost always a more positive, easier to understand rule set that can be created.
-
How do I block everything except NTP? Use two separate rules?
-
pass NTP. Block everything else.
-
-
This post is deleted! -
 S stephenw10 locked this topic on
S stephenw10 locked this topic on