How to add wireless VLANs through additional router
-
I'm new to pfSense and am struggling to add Wi-fi to my pfSense setup.
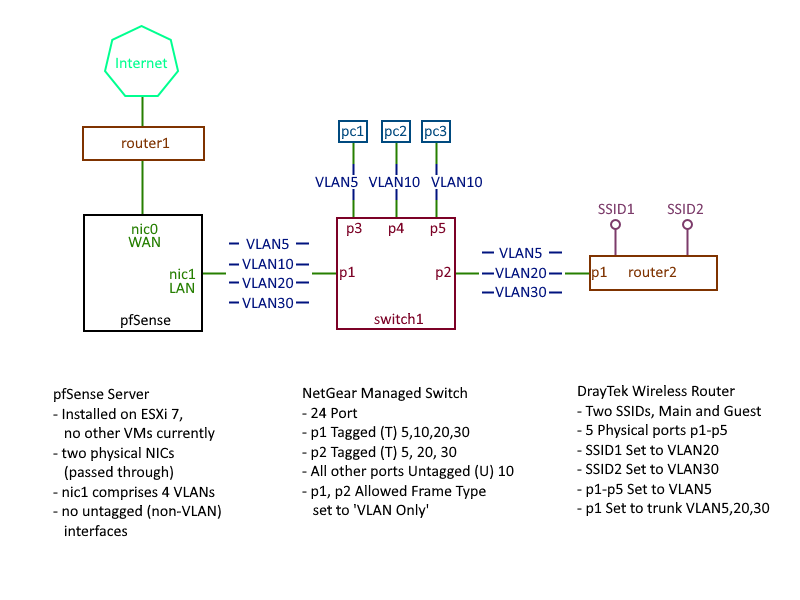
I have my pfSense box set to provide 4 VLAN interfaces (see network topology below), two for wired networks, two for a pair of wireless networks (personal and guest). The wireless networks are to be provided by a DrayTek router.
I have been following this guide, as well as looking at many other similar examples, in which the author simply plugs their Wi-fi device (access point or router) into a trunked port on their switch, configures a VLAN for each SSID on the router, and has instant operational connectivity with pfSense.
My own experience of trying this, as well as my rudimentary understanding of IP routing, contradicts this. With no dynamic routing protocol (BGP etc.) configured between pfSense and the router, and no static routes defined, how would either device (pfSense or the router) know how to forward packets between network segments?
My Goal
To configure two wireless subnets, physically hosted on a DrayTek router, with DHCP and DNS provided by pfSense.In Practice
When deploying my hardware and configuring pfSense in the manner described here I get partial success.
-Wi-fi devices on either subnet are correctly assigned IPs by the DHCP server and have good DNS/Internet access through pfSense.
-Tracert from wireless devices to pfSense interfaces is good.
-Tracert from wireless devices to wired devices generally succeeds, with unusually high (and variable) hop times (500ms+).
-Wired devices cannot access anything on the Wi-fi router side including the router web GUI or any devices connected wirelessly. Tracert/ping does not work at all, with the last successful hop being the inbound pfSense interface.I think there must be a fundamental gap in my knowledge here. Any and all advice would be very gratefully received.
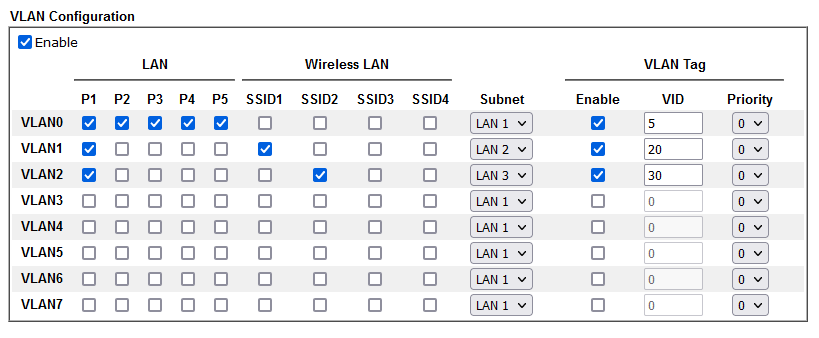
Network topology image attached below, plus the VLAN settings on the DrayTek router. If any more information is required I will do my best to provide it.
Thank you.
Network Topology
DrayTek VLAN settings
-
@reg_ed said in How to add wireless VLANs through additional router:
how would either device (pfSense or the router) know how to forward packets between network segments?
Why would you think your downstream wifi is routing these? If your assigning vlans, these should all be routed at pfsense. And your wifi is just an AP. If your actually routing/natting at this router 2 then yes you would have problems.
But I don't see how this is the case since you state your wifi are getting dhcp from pfsense?
assigned IPs by the DHCP server and have good DNS/Internet access through pfSense.
Are they getting IPs from some other dhcpd?
Pfsense would know how to route between any networks it is directly attached to without need of adding any routing or use of routing protocol.
What you have left off is any of your firewall rules you have placed on these vlans you have created on pfsense.
-
@johnpoz said in How to add wireless VLANs through additional router:
Why would you think your downstream wifi is routing these?
My knowledge of routing is apparently quite lacking. But if the flow is:
pfSense(192.168.20.1) > Switch > Router (192.168.20.3) > Wireless device (192.168.20.80)
Then how does pfSense know to route packets for the wireless device through the router?@johnpoz said in How to add wireless VLANs through additional router:
Are they getting IPs from some other dhcpd?
They are not, there is only one DHCP active on the network, that's the pfSense DHCP.
@johnpoz said in How to add wireless VLANs through additional router:
What you have left off is any of your firewall rules you have placed on these vlans you have created on pfsense.
For the purposes of testing, I have put all of the LAN/WLAN interfaces into allow all, no filtering or blocking at all.
-
@reg_ed said in How to add wireless VLANs through additional router:
pfSense(192.168.20.1) > Switch > Router (192.168.20.3) > Wireless device (192.168.20.80)
Your device is on the same network there 192.168.20/24 - why would it talk to 20.3 in getting off that network. AP have IPs so you can manage them - they don't route.
Are you saying your traceroute hits 20.3 and then 20.1? That would be huge problem in stuff working because it would seem you have the same network on both sides of that wifi device if it was routing..
Your wifi device should really not be routing, it should just be an AP (access point).. If you actual want to route at it, then there would be no vlans setup in pfsense for that network, and you would use a transit network between that downstream router and pfsense.'
Did you change your dhcp to point to this 20.3 address in pfsense - that would be wrong.. Devices on the 20/24 network should be talking to 20.1 (pfsense) as their gateway to get off that network.
-
@johnpoz said in How to add wireless VLANs through additional router:
AP have IPs so you can manage them - they don't route.
The device is technically a router but with the WAN, DHCP and NAT turned off. I had assumed that the device was routing between the subnets/VLANs you can create on it but I think you're saying that all it's really doing is switching? That would make a lot of sense given the fact that traffic is flowing freely out of the router at least.
In respect to the tracert question the returned hops are:
From wireless device to wired device -
20.1 (pfSense WLAN interface) > 10.5 (wired device)From wired device to wireless device -
10.1 (pfSense LAN interface) > nothingI'm really not sure what this implies. I've just double checked that the firewall is allowing all traffic through (it is) so I can't fathom why the LAN traffic is stalling at pfSense.
-
@reg_ed so you say your rules are any any.. But are you forcing a gateway?
And you sure they are not just tcp (this is what rules default to)..
Common problem seen is users policy routing traffic out say wan_dhcp or vpn connection. This would prevent access to other vlans/networks on pfsense because that gateway can not get to the actual destination.
Your gateway in your rules should be the * - example
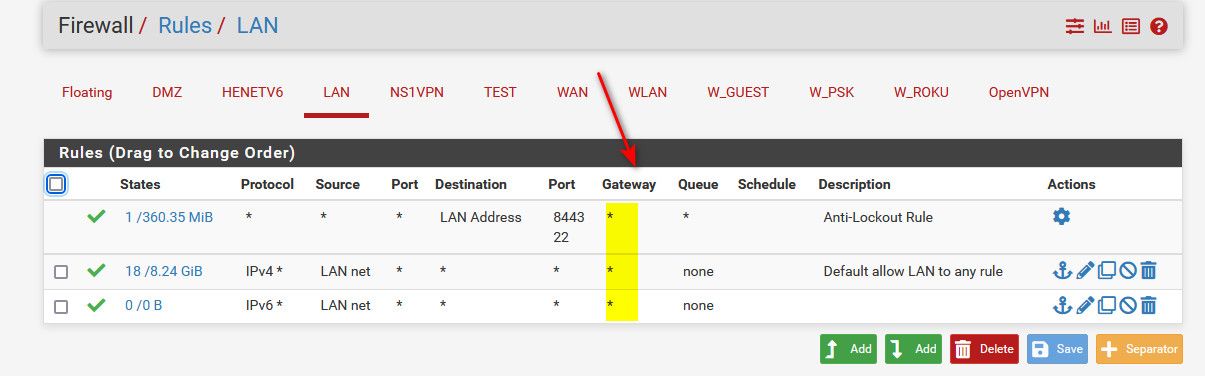
This allows pfsense to use its internal routing to know where to send the traffic. Another common issue is forgetting the host filewall.. Its quite possible destination device isn't going to answer your traffic because its not from the local network. For example windows out of the box would not answer ping from other than its local network.
If your not policy routing, you can validate for your own sanity that pfsense is sending on the traffic by just doing a simple ping to the other network device, and sniffing on the dest network interface (diagnostic menu, packet capture)... You would see pfsense sending the pings, but getting no answer. This means the device is not answering due to firewall.. Or its not using pfsense as is its gateway, but if they all have internet access.. The policy route or host firewall seem the most likely reasons for your problems
-
You're absolutely right, it was in part a firewall issue.
On the laptop I was using to test the wireless side of the network I had added my LAN scopes to the Windows firewall for (I thought) all of the relevant rules but I must have missed one. Temporarily turning the firewall completely off yields successful pings/tracert to the device.
I am still unable to access the router GUI (or ping it) through any of its access IPs (5.3, 20.3, 30.3) except from devices who are themselves on that particular subnet. This also applies to the pfSense UI tracert/ping tools.
For example:
Ping 5.3 from 5.1 interface > Success
Ping 5.3 from 20.1 interface > Failure
Ping 20.3 from 5.1 interface > Failure
etc.The DrayTek router has three access IPs because it creates one for each VLAN.
-
@reg_ed said in How to add wireless VLANs through additional router:
it creates one for each VLAN.
Yeah that prob hold over from its "routing" function that you are not really using in the mode your in.
Why you can prob not get to it from other network is their is no gateway set. Not sure it allows adding that, but if it doesn't and you want to be able to get to gui of it from another network, you could always source nat the traffic so it looks like its coming from pfsense IP on that network.
This would be done in the outbound nat section..
-
I added an outbound NAT rule and now have access to the router from my other subnets. I am indebted to you. Thank you. Can I buy you a beer?
For my own future understanding, is this because the router (really) needs to know the gateway in the same way that other hosts do and are assigned the gateway by the DHCP?
-
@reg_ed said in How to add wireless VLANs through additional router:
Can I buy you a beer?
While I would love that if you happen to be in the chicagoland area ;) Best way is just pay it forward, if you can help someone in anyway - please do so, be it tech help here on the forums or other forums, or even buying a homeless guy a coffee or sandwich.. (or beer - which they prob enjoy more)! ;)
Any device needs a gateway or a specific route on how to talk to something that is not on its local network. Or it just don't know where to send the traffic to get back to that network. If the device doesn't know how to get to the source network of the traffic, you can just kind of trick it via the nat, that device wanting to talk to it is local.
Just like internet wouldn't know how to talk to your rfc1918 and your router nats it to what your public IP is that you get from your isp.