NAT source
-
@j-lanham No, we have some working with aliases by country/geoIP, which have subnets. You created it as Alias Native format in pfBlocker? You're certain there's not another rule?
-
@steveits As in another NAT Rule? And No, it's not native because the AWS list is json. It has to be translated.
-
@j-lanham Hm, it doesn't let you choose Alias Native here:
 ?
?
That's how we have it create aliases to use in NAT and other rules.And yes I meant another NAT rule.
If you hover over the alias name on the NAT page does it show the subnets correctly?
-
@steveits I have several nat rules for different destinations for different internal servers providing services to external customers and vendors. The nat list just shows the list, because it's being provided by PFBLOCKERNG. So no, it doesn't show the individual network segments.
-
@j-lanham If you hover over an alias and it doesn't show the contents there's something wrong with the alias. It should look like:
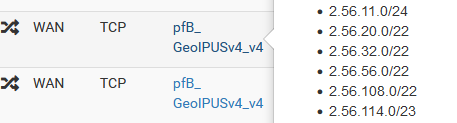
Long shot, but could a state be open for a connection, from before you added the alias as the source on the NAT rule?
You might need to post your NAT rules.
In a few cases on slower routers or connections we've even done it the other way, since it can take a long time to load the page with the large aliases...create several NAT rules with no source, with no linked firewall rule, and add one firewall rule allowing to a list of targets:port from the source alias.
-
@steveits It could be showing a residual connection. Did a refresh on the logs showing only pass (as this is the only rule I have logging on) and it's now showing only AWS servers connecting.
While we're on the subject of aliases, I finally understood what you were referencing in the PFBLOCKNG display. I had originally installed what I thought was the production version and then was corrected in another unrelated post and I was going to wait until this weekend to setup PFBLOCKERNG. After you pointing out another thing that I needed the devel version for I reinstalled PFBLOCKERNG and changed the list to your suggestion. Seems to be working right now, so thanks for that. However I can't use the pfb_AWS_v4 list as alias under another alias like I was allowed to under the older version of PFBLOCKERNG. Is that by design or was truly never allowed to begin with? If it isn't allowed, how do you used the PFBLOCKERNG address list along with manually defined list to allow additional IP addresses access based on the list?
-
@j-lanham Yeah use the -devel. Not sure why there are two. A couple years ago I saw the maintainer post to use -devel. I could never get the other to work with MaxMind after the license key requirement a few years ago, so have been using -devel for a while at all clients. It's been so long I forget to ask, or what is "new" in the dev version.
re: aliases, if you set the action to Alias Native, pfB creates the alias but doesn't create anything else. So you can use it in your own rules. Click the "Click here for more info --> " when editing the IPv4/IPv6 list:
'Alias' rules create an alias for the list (and do nothing else). This enables a pfBlockerNG list to be used by name, in any firewall rule or pfSense function, as desired. Options - Alias Deny, Alias Permit, Alias Match, Alias Native 'Alias Deny' can use De-Duplication and Reputation Processes if configured. 'Alias Permit' and 'Alias Match' will be saved in the Same folder as the other Permit/Match Auto-Rules 'Alias Native' lists are kept in their Native format without any modifications.I am pretty sure you can't otherwise use an alias in your own rules...?
-
@steveits Actually I want to use the pfb alias list on an alias list along with a list of ip addresses that are allowed to access that nat rule.
I was informed that -devel is the production version of the package. Asked the question why both packages are still there if the non-devel package is a dead end and I didn't quite get an answer. No one seems to know why.
-
@SteveITS The old alias list that I had the old pfb list on wouldn't let me pull it up. When I setup a new list, it allowed me to add the pfb_AWS_v4 list. So, that's the answer. It will allow you to, just have to setup a new alias after reinstalling pfblockerng.
Thanks for all your help, btw. And the responsiveness of your answers. I really appreciate it.
-
@j-lanham You're welcome. Also after (re)installing pfB you might need to run an update to generate the aliases.
I am not sure why there are two packages. I suspect the -devel started out as "beta" but then everyone started using it, and now people would have to uninstall it to install the original. -devel version 2.x existed long before 3. The author has a Patreon site at http://pfblockerng.com/ but it doesn't really explain that.