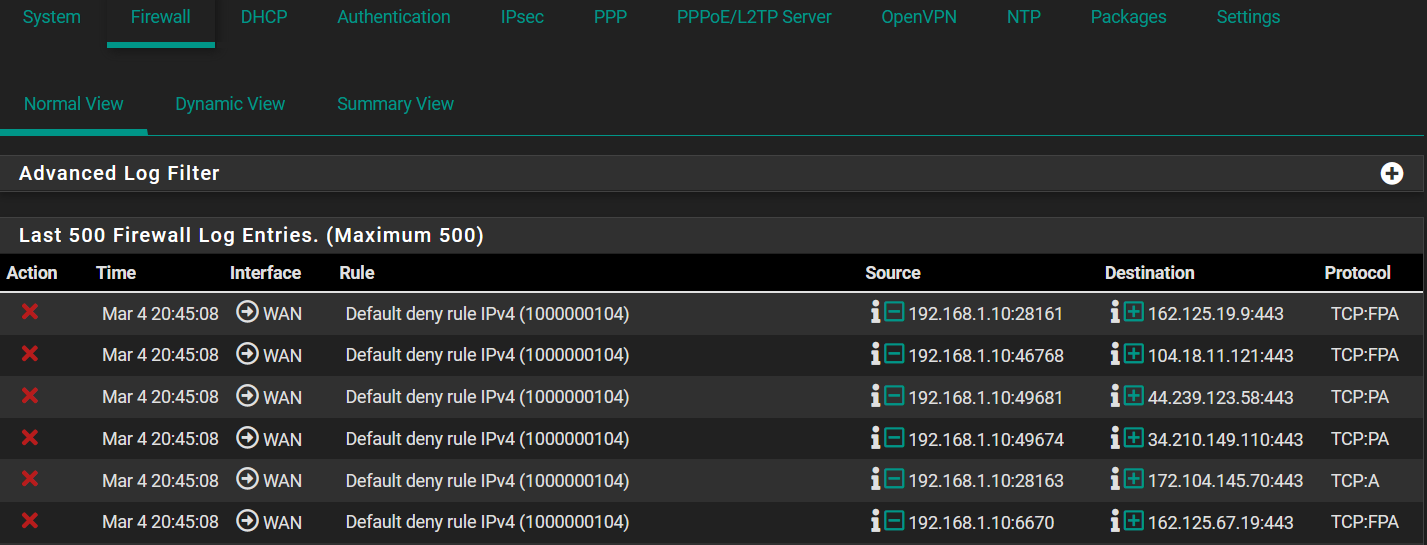
TCP:A, TCP:PA ... dropped
-
@johnpoz Hi,
Sorry, I miss clicked so I sent the topic earlier
I completed the description -
@johnpoz I also do have drops on TCP:S but the dest is my pfsense interface (192.168.1.2) while I'm requesting with my PC (192.168.1.10) :
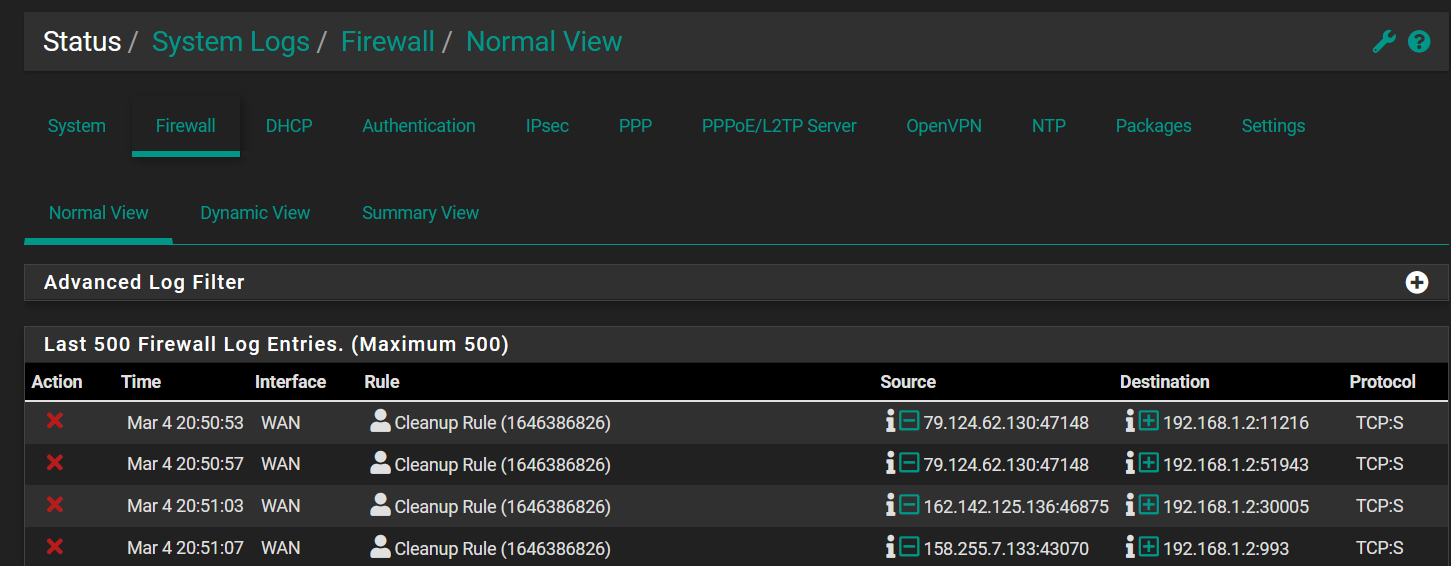
-
@hugzer yeah those syn blocks would be normal, are you wanting to allow traffic from the internet to that IP? If so then you would have to setup a port forward.
While blocks on just A are normal as well for a stateful firewall, But means something different, a state can only be opened via a syn, and to allow that you need firewall rule to allow it. While non syn traffic would be blocked and wouldn't be able to open the state even if you wanted to allow the traffic.
What is odd about those blocks is how would some public IP know how to get to your wan to try and get to 192.168.1.2? Seems like you have a port forward setup, but no wan rule to allow that traffic..
-
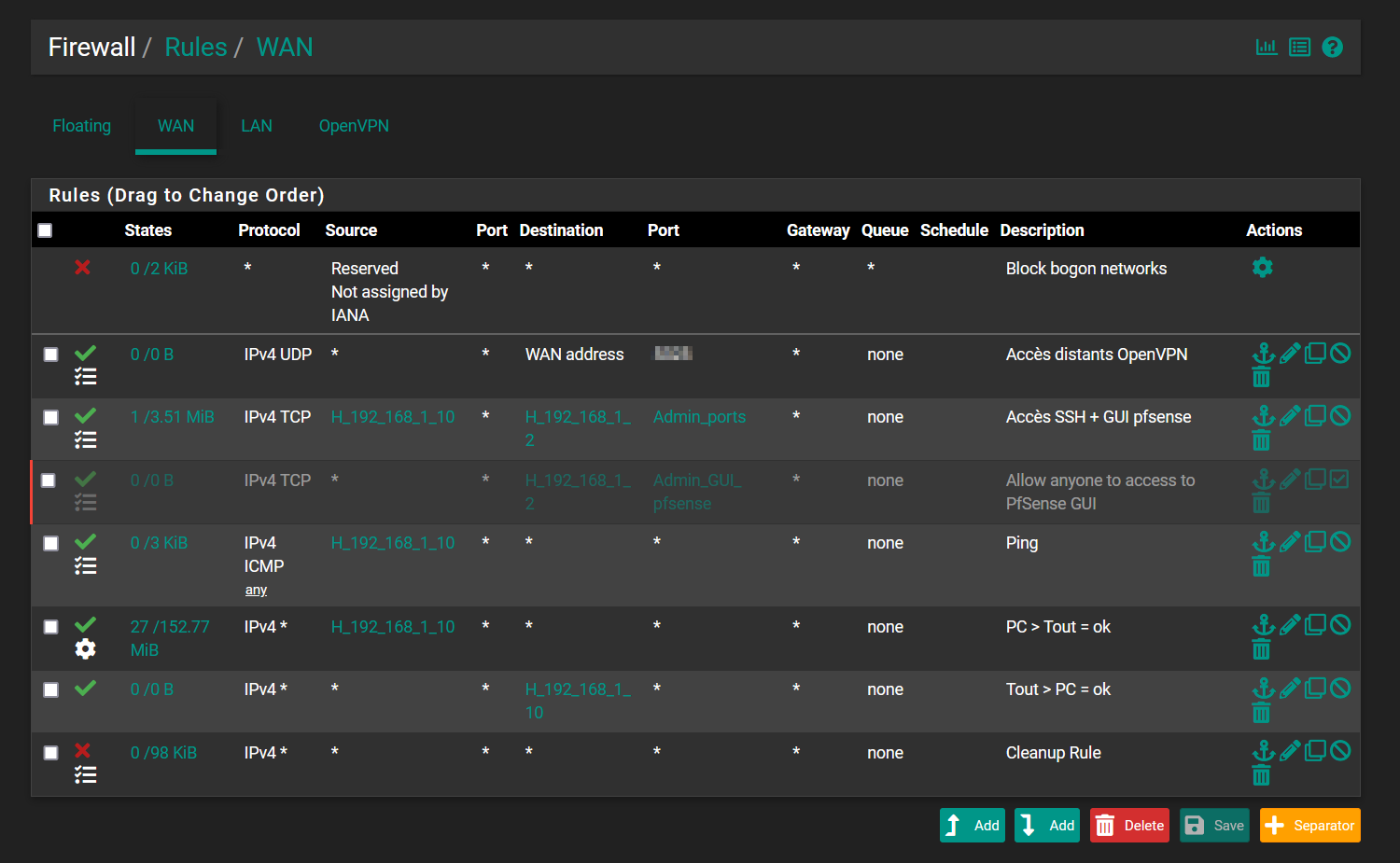
@johnpoz I'd like to make something like that :
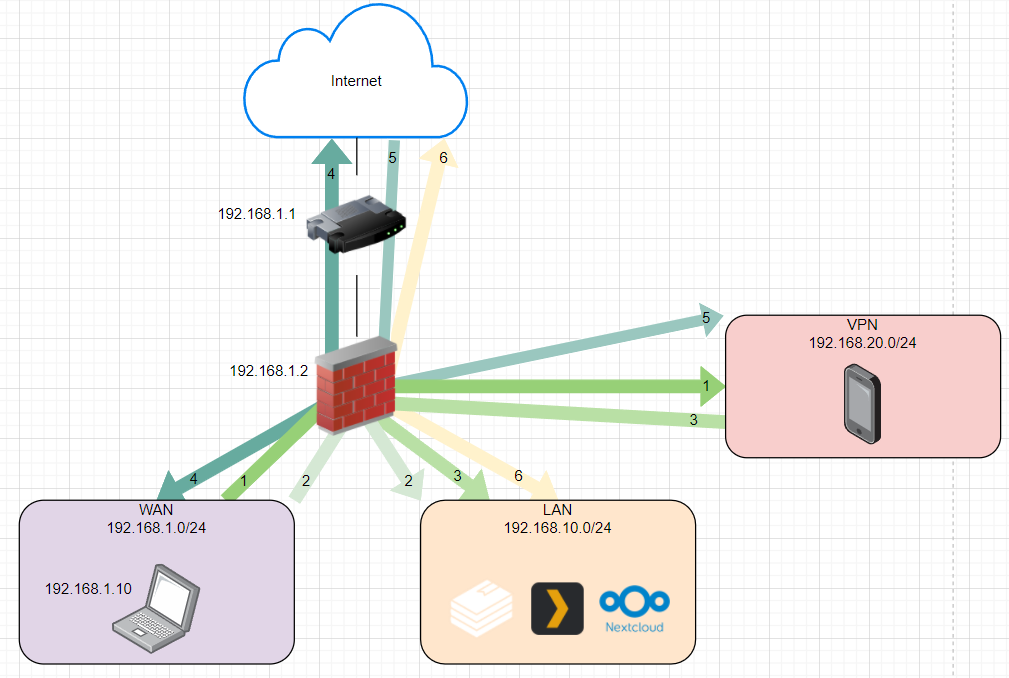
I don't understand how can I setup a port forwarding while the second port is not defined by me
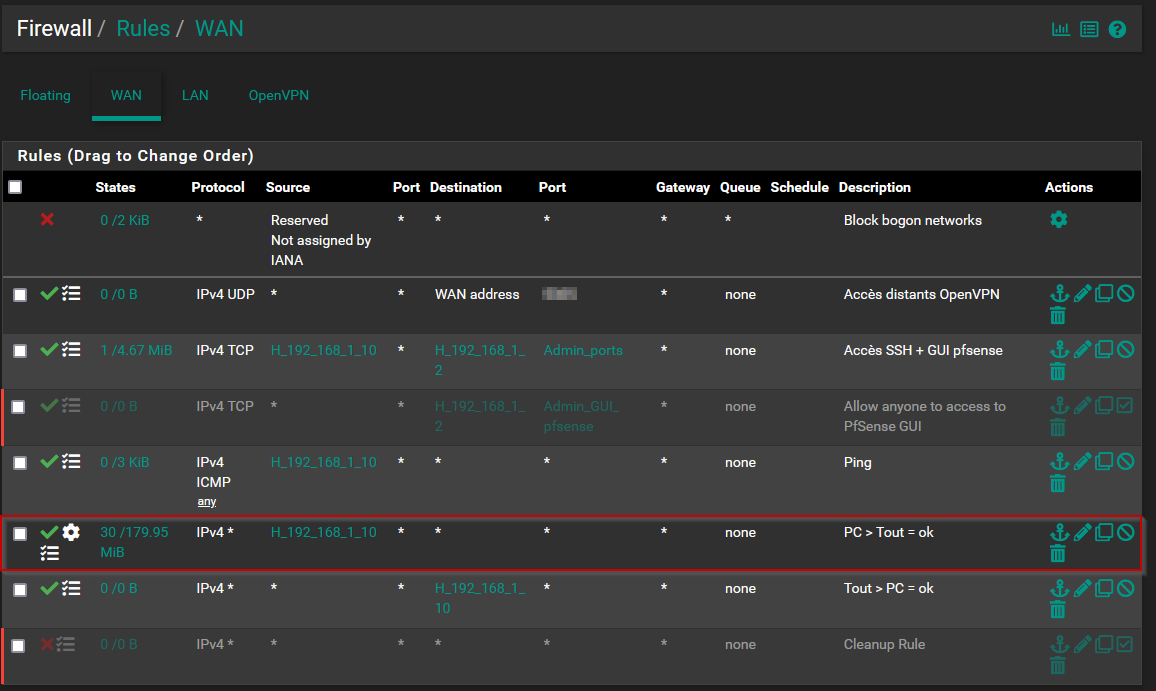
On the WAN interface, I do have a rule :
src 192.168.1.0/24
dst any
port any
(protocol any)
It does match with my traffic 4 (in the draw)
On the LAN interface, I do have a rule :
src 192.168.10.0/24
dst any
port any
(protocol any)
It does match with my traffic 6 (in the draw)
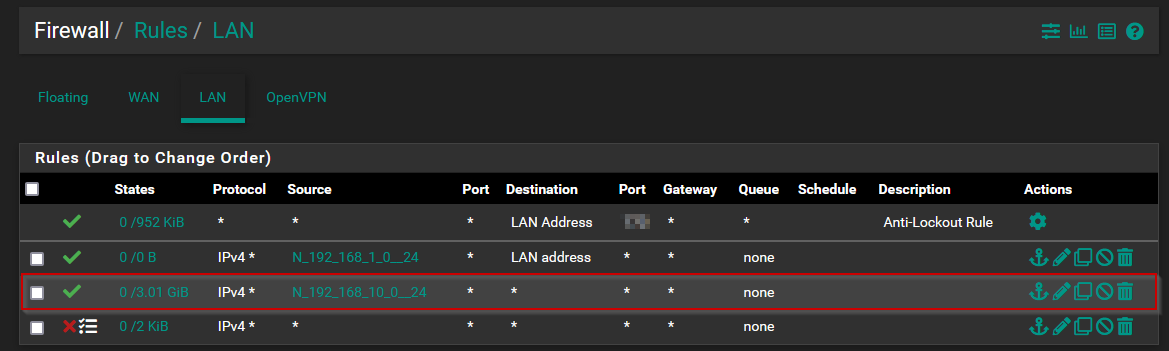
For the LAN interface, I didn't make port forwarding and traffic does work without any drops
-
@hugzer said in TCP:A, TCP:PA ... dropped:
I setup a port forwarding while the second port is not defined by me
Huh.. You don't know what service your trying to access? The source port is almost always going to be any, because the source port would be some random high port above 1024.
But to get to plex for example that port would be 32400, nextcloud has a known port it listens on.. All services have ports they listen on.
Normally you would put all "your" networks behind pfsense.. So the only thing on wan of pfsense would be internet, or the transit network to get to internet if your not able to put your isp device in bridge mode. And your going to double nat.
-
@johnpoz I do know what service I need to access but as I said, this is a new FW and I had no FW before so I created a rule which allow all the traffic to pass (logged rule) during like a week and after that, I will reduce the ports opened.
Physically, my PC is plugged to my router and pfsense is a VM
My ESXi is plugged to my router too and it has only one network cardSo my PC has to be on the same network as my ESXi (and so my PfSense WAN interface)
-
@hugzer said in TCP:A, TCP:PA ... dropped:
created a rule which allow all the traffic to pass (logged rule) during like a week and after that, I will reduce the ports opened.
That is not going to work if your natting..
So my PC has to be on the same network as my ESXi
No just needs to be on a network behind pfsense, and not pfsense WAN..
-
The traffic in the first post is classic asymmetric routing.
It looks like you have set pfSense as the default gateway on the PC generating the asymmetric route for those external addresses.
If the PC must be in the pfSense WAN subnet it must use the ISP router as it's gateway to avoid that.
Steve
-
@johnpoz said in TCP:A, TCP:PA ... dropped:
That is not going to work if your natting..
I'm currently not using NAT. Do you think I should ? I cannot be connected behind PfSense
@johnpoz said in TCP:A, TCP:PA ... dropped:
No just needs to be on a network behind pfsense, and not pfsense WAN..
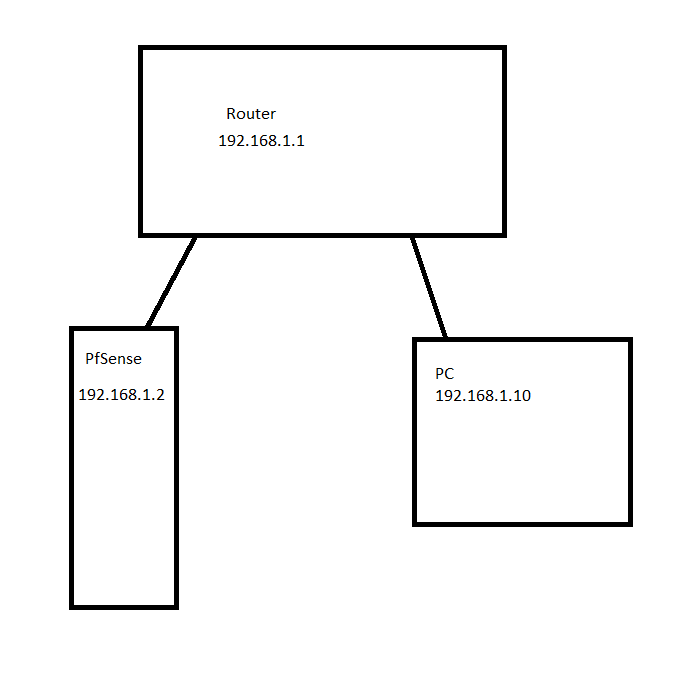
I only have my 192.168.1.0 when I'm plugged to my router that's physically like that :
-
@stephenw10 Hi,
I just tried to use 192.168.1.1 (router) in GW but I now can't access to my LAN network (192.168.10.0/24)
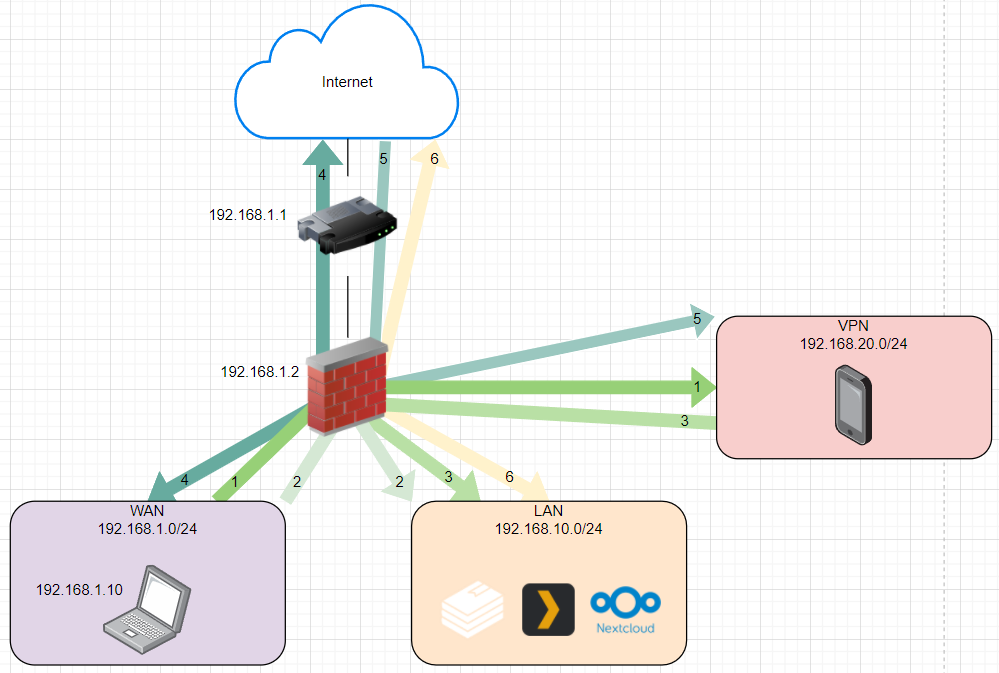
I'm talking about traffic 2 -
You would have to access the subnet behind pfSense using port forwards.
Or you could add a static route to the client PC for the 192.168.10.0/24 via 192.168.1.2.
Steve