Why assign an OpenVPN connection as its own interface?
-
My goal is to have 2 OpenVPN connections on my SG1100, a server for my remote clients and a netgate client to an external VPN service (ExpressVPN, Nord, etc). I also have 2 different internal LANs on my netgate a "secure" one (LAN) and an "insecure" one (OPT), where I wish the secure one to route out to the internet via the WAN connection and for the insecure one to route to the internet via the external OpenVPN connection.
I created the local OpenVPN server first, and my remote clients connected fine and can access anywhere they need to, local resources as well as through to the internet via local WAN. I allowed any/any on the OpenVPN section under Firewall but Ive not assigned any OpenVPN connection to be its own interface yet.
Then I set up the external OpenVPN connection and it came up fine to the provider, but then my remote clients of the netgate OpenVPN server could connect but couldnt route anywhere.
Would assigning interfaces for each OpenVPN connection fix this? If so, what should I do with that "allow any/any" rule that is sitting under Firewall->OpenVPN right now? Delete that or change it to something else or just delete it?
Finally, where do I configure things to make the OPT network users route to the internet via the OpenVPN external service?
TIA!
-
@oldschoolrouterjockey said in Why assign an OpenVPN connection as its own interface?:
Would assigning interfaces for each OpenVPN connection fix this? If so, what should I do with that "allow any/any" rule that is sitting under Firewall->OpenVPN right now? Delete that or change it to something else or just delete it?
Hi,
As I can see there are a lot of wounds in this setup or you need to work on your pfSense knowledge and everything will be fine...

1. point: for the OVPN server, use this guide and you won't need to get an interface for.....: https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-ra.html
(but I think this is pretty much done, it just needs to be refined)2. point: for the external VPN provider(s) use this description(s), they are all pretty much the same:
- https://support.surfshark.com/hc/en-us/articles/360010789259-How-to-set-up-pfSense-2-4-4-with-Surfshark
-https://support.nordvpn.com/Connectivity/Router/1626958942/pfSense-2-5-Setup-with-NordVPN.htm
-https://www.expressvpn.com/support/vpn-setup/pfsense-with-expressvpn-openvpn/
here you need to assign an interface to route the traffic this is also the answer to point 3.
- something like this (GW on SSVPN):
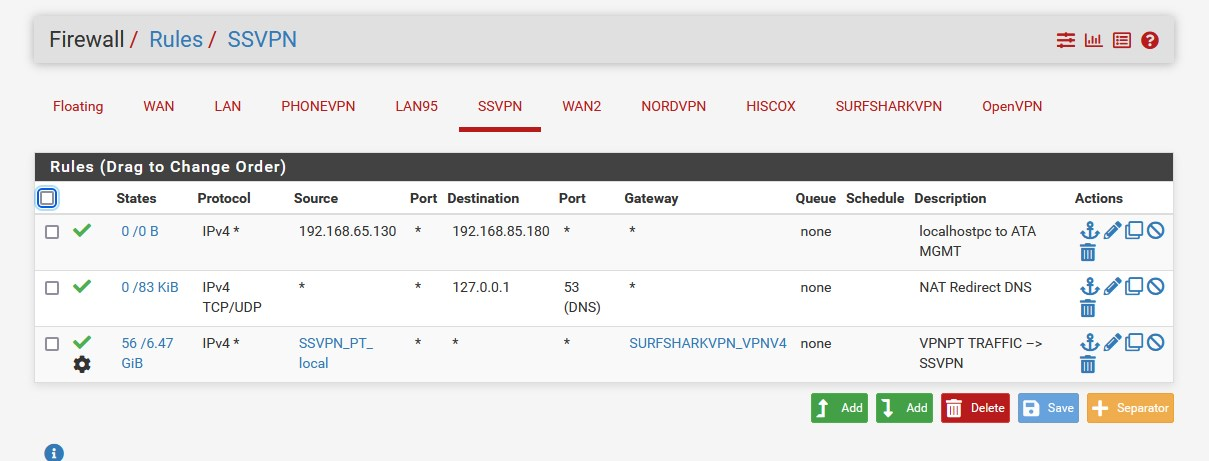
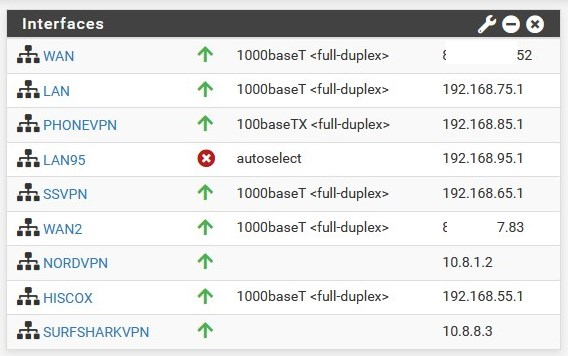
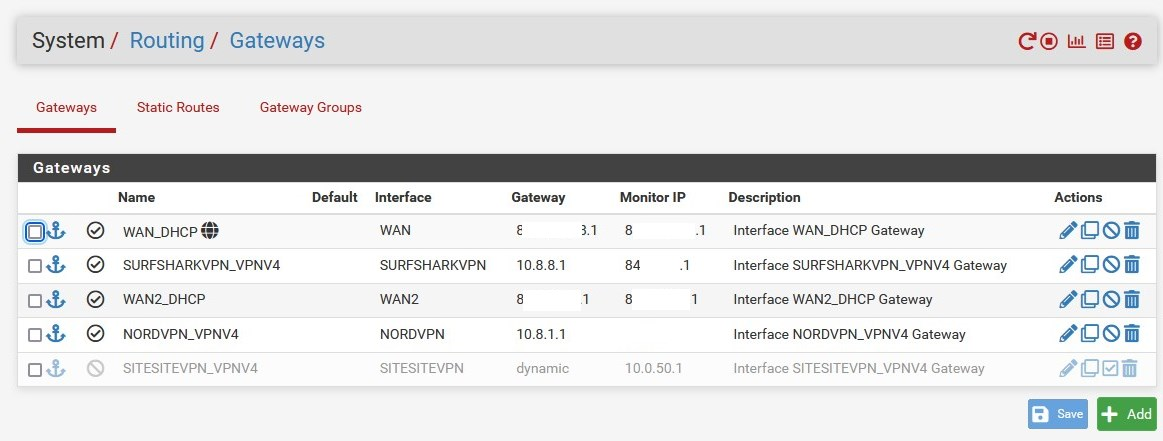
- https://support.surfshark.com/hc/en-us/articles/360010789259-How-to-set-up-pfSense-2-4-4-with-Surfshark
-
@daddygo ah oh thanks. as you said, I already had points 1 and 2 completed.
BUT as soon as I activated the OpenVPN client in my Step 2 to connect to my external service, then my remote clients that I had working after step 1, all stop routing. Even by adding the interface to the external OpenVPN service doesnt help those remote clients to start working again. They can connect OK, but just cannot route to anywhere.
-
@oldschoolrouterjockey said in Why assign an OpenVPN connection as its own interface?:
They can connect OK, but just cannot route to anywhere.
on the server, configure the local networks you want to reach....
(or where you want to route clients exactly?)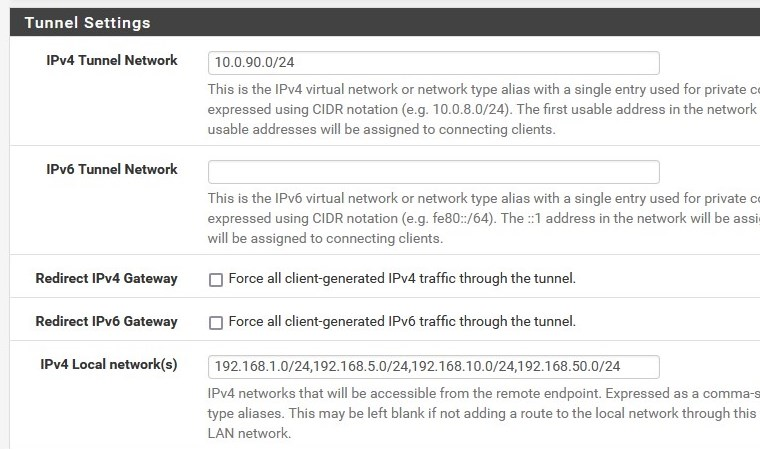
-
@daddygo what I have done is check that "Redirect IPv4 Gateway" box so as to force all client-generated IPv4 traffic through the tunnel. When I do that the "IPv4 Local network(s)" option disappears (for good reason).
-
OK so I figured out the last parts to make this all work:
- disable automatic route entries under the external VPN provider's OVPN config
- had to add an outbound nat entry for the internal network that I want to use the VPN provider
thanks for the guidance on setting the external ovpn provider as its own interface, and leaving the local server w/o an interface, that was another part I was missing.
-
@oldschoolrouterjockey said in Why assign an OpenVPN connection as its own interface?:
OK so I figured out the last parts to make this all work:
I knew it was all there in the descriptions, but if you work hard to succeed, you'll know how to do it next time


