Zoom Blocked, Completely Stumped.
-
@dma_pf said in Zoom Blocked, Completely Stumped.:
ouldn't get address for 'b.cctld.us': not found
couldn't get address for 'f.cctld.us': not found
couldn't get address for 'k.cctld.us': not found
couldn't get address for 'w.cctld.us': not found
couldn't get address for 'x.cctld.us': not found
couldn't get address for 'y.cctld.us': not foundThere is where you failing - you can not talk to the next gtld servers the ones that know where the ns are for anything .us
I would say you are not able to talk to roots to get that... For example you should be able to query root servers and ask for the IP of any of those cctld.us servers.. example
$ dig @h.root-servers.net b.cctld.us ; <<>> DiG 9.16.26 <<>> @h.root-servers.net b.cctld.us ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10358 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 6, ADDITIONAL: 13 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;b.cctld.us. IN A ;; AUTHORITY SECTION: us. 172800 IN NS b.cctld.us. us. 172800 IN NS f.cctld.us. us. 172800 IN NS k.cctld.us. us. 172800 IN NS w.cctld.us. us. 172800 IN NS x.cctld.us. us. 172800 IN NS y.cctld.us. ;; ADDITIONAL SECTION: b.cctld.us. 172800 IN A 156.154.125.70 f.cctld.us. 172800 IN A 209.173.58.70 k.cctld.us. 172800 IN A 156.154.128.70 w.cctld.us. 172800 IN A 37.209.192.15 x.cctld.us. 172800 IN A 37.209.194.15 y.cctld.us. 172800 IN A 37.209.196.15 b.cctld.us. 172800 IN AAAA 2001:502:ad09::29 f.cctld.us. 172800 IN AAAA 2001:500:3682::11 k.cctld.us. 172800 IN AAAA 2001:503:e239::3:1 w.cctld.us. 172800 IN AAAA 2001:dcd:1::15 x.cctld.us. 172800 IN AAAA 2001:dcd:2::15 y.cctld.us. 172800 IN AAAA 2001:dcd:3::15 ;; Query time: 50 msec ;; SERVER: 198.97.190.53#53(198.97.190.53) ;; WHEN: Tue Mar 15 17:03:43 Central Daylight Time 2022 ;; MSG SIZE rcvd: 397If you can not talk to roots - then really you wouldn't be able to resolve anything..
-
@dma_pf said in Zoom Blocked, Completely Stumped.:
No other servers listed here. Only using the root servers.
Your not pointing directly to roots in your dns config on pfsense are you?? out of the box pfsense resolves, you should not point anywhere.. You should only point to 127.0.0.1 (unbound) and it knows the root servers..
If you can not talk to roots, you wouldn't be able to resolve anything - but you can not query them recursive... You can only ask them for NSs of the tld, If your like forwarding to roots - that would never work..
-
@johnpoz Here's what I get:
; <<>> DiG 9.16.23 <<>> @h.root-servers.net b.cctld.us ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 3117 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 6, ADDITIONAL: 13 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;b.cctld.us. IN A ;; AUTHORITY SECTION: us. 172800 IN NS b.cctld.us. us. 172800 IN NS f.cctld.us. us. 172800 IN NS k.cctld.us. us. 172800 IN NS w.cctld.us. us. 172800 IN NS x.cctld.us. us. 172800 IN NS y.cctld.us. ;; ADDITIONAL SECTION: b.cctld.us. 172800 IN A 156.154.125.70 f.cctld.us. 172800 IN A 209.173.58.70 k.cctld.us. 172800 IN A 156.154.128.70 w.cctld.us. 172800 IN A 37.209.192.15 x.cctld.us. 172800 IN A 37.209.194.15 y.cctld.us. 172800 IN A 37.209.196.15 b.cctld.us. 172800 IN AAAA 2001:502:ad09::29 f.cctld.us. 172800 IN AAAA 2001:500:3682::11 k.cctld.us. 172800 IN AAAA 2001:503:e239::3:1 w.cctld.us. 172800 IN AAAA 2001:dcd:1::15 x.cctld.us. 172800 IN AAAA 2001:dcd:2::15 y.cctld.us. 172800 IN AAAA 2001:dcd:3::15 ;; Query time: 35 msec ;; SERVER: 198.97.190.53#53(198.97.190.53) ;; WHEN: Tue Mar 15 18:05:47 EDT 2022 ;; MSG SIZE rcvd: 397Question is why is it failing? And only for that domain? I haven't had any issues with anything else resolving all day.
I'm 20 miles from the University Of Maryland....and I'm an alumni. You'd think they'd give me more respect!
Does this mean that I will need to go to forwarding mode in resolver?
-
Doh!
Does it also work against that server Unbound is trying:[2.6.0-RELEASE][admin@cedev-3.stevew.lan]/root: dig @205.251.195.120 zoom.us ; <<>> DiG 9.16.23 <<>> @205.251.195.120 zoom.us ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 57270 ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;zoom.us. IN A ;; ANSWER SECTION: zoom.us. 60 IN A 170.114.10.89 ;; AUTHORITY SECTION: zoom.us. 172800 IN NS ns-1137.awsdns-14.org. zoom.us. 172800 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 172800 IN NS ns-387.awsdns-48.com. zoom.us. 172800 IN NS ns-888.awsdns-47.net. ;; Query time: 15 msec ;; SERVER: 205.251.195.120#53(205.251.195.120) ;; WHEN: Tue Mar 15 22:15:00 GMT 2022 ;; MSG SIZE rcvd: 192 -
@dma_pf ok so that looks fine... So can you actually query any of the cctld.us server for zoom.us?
From your trace it said it could not get an IP for any of the cctld.us servers. But maybe it just couldn't talk to them - try doing a directed query to any of those IPs asking for zoom.us ns..
example
$ dig @37.209.192.15 zoom.us NS ; <<>> DiG 9.16.26 <<>> @37.209.192.15 zoom.us NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58274 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;zoom.us. IN NS ;; AUTHORITY SECTION: zoom.us. 7200 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 7200 IN NS ns-1137.awsdns-14.org. zoom.us. 7200 IN NS ns-387.awsdns-48.com. zoom.us. 7200 IN NS ns-888.awsdns-47.net. ;; Query time: 36 msec ;; SERVER: 37.209.192.15#53(37.209.192.15) ;; WHEN: Tue Mar 15 17:23:04 Central Daylight Time 2022 ;; MSG SIZE rcvd: 176 -
@stephenw10 said in Zoom Blocked, Completely Stumped.:
Does it also work against that server Unbound is trying:
I'm not quite sure if you're asking me to find out which server my Unbound is using or run the query in your example. If it's the IP that my Unbound is using, how do I find it? As far as I know it just queries the 13 roots.
If it's the query you provided here what I get:
; <<>> DiG 9.16.23 <<>> @205.251.195.120 zoom.us ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 65232 ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;zoom.us. IN A ;; ANSWER SECTION: zoom.us. 60 IN A 170.114.10.85 ;; AUTHORITY SECTION: zoom.us. 172800 IN NS ns-1137.awsdns-14.org. zoom.us. 172800 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 172800 IN NS ns-387.awsdns-48.com. zoom.us. 172800 IN NS ns-888.awsdns-47.net. ;; Query time: 7 msec ;; SERVER: 205.251.195.120#53(205.251.195.120) ;; WHEN: Tue Mar 15 18:18:41 EDT 2022 ;; MSG SIZE rcvd: 192 -
@johnpoz said in Zoom Blocked, Completely Stumped.:
try doing a directed query to any of those IPs asking for zoom.us ns..
Here you go...I ran a query for each of the IPv4 servers.
; <<>> DiG 9.16.23 <<>> @156.154.125.70 zoom.us NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23918 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: ae492118dabb530301000000623112e53cdc60e78d6495b9 (good) ;; QUESTION SECTION: ;zoom.us. IN NS ;; AUTHORITY SECTION: zoom.us. 7200 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 7200 IN NS ns-888.awsdns-47.net. zoom.us. 7200 IN NS ns-387.awsdns-48.com. zoom.us. 7200 IN NS ns-1137.awsdns-14.org. ;; Query time: 9 msec ;; SERVER: 156.154.125.70#53(156.154.125.70) ;; WHEN: Tue Mar 15 18:27:49 EDT 2022 ;; MSG SIZE rcvd: 204; <<>> DiG 9.16.23 <<>> @209.173.58.70 zoom.us NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 64421 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: 46c30a9773371738010000006231134cc91442fbc9c0d52b (good) ;; QUESTION SECTION: ;zoom.us. IN NS ;; AUTHORITY SECTION: zoom.us. 7200 IN NS ns-387.awsdns-48.com. zoom.us. 7200 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 7200 IN NS ns-1137.awsdns-14.org. zoom.us. 7200 IN NS ns-888.awsdns-47.net. ;; Query time: 7 msec ;; SERVER: 209.173.58.70#53(209.173.58.70) ;; WHEN: Tue Mar 15 18:29:32 EDT 2022 ;; MSG SIZE rcvd: 204; <<>> DiG 9.16.23 <<>> @156.154.128.70 zoom.us NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42094 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: 013ba9c4121d43120100000062311378b7be69e034c0357e (good) ;; QUESTION SECTION: ;zoom.us. IN NS ;; AUTHORITY SECTION: zoom.us. 7200 IN NS ns-1137.awsdns-14.org. zoom.us. 7200 IN NS ns-387.awsdns-48.com. zoom.us. 7200 IN NS ns-888.awsdns-47.net. zoom.us. 7200 IN NS ns-1772.awsdns-29.co.uk. ;; Query time: 21 msec ;; SERVER: 156.154.128.70#53(156.154.128.70) ;; WHEN: Tue Mar 15 18:30:16 EDT 2022 ;; MSG SIZE rcvd: 204; <<>> DiG 9.16.23 <<>> @37.209.192.15 zoom.us NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4321 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;zoom.us. IN NS ;; AUTHORITY SECTION: zoom.us. 7200 IN NS ns-1137.awsdns-14.org. zoom.us. 7200 IN NS ns-387.awsdns-48.com. zoom.us. 7200 IN NS ns-888.awsdns-47.net. zoom.us. 7200 IN NS ns-1772.awsdns-29.co.uk. ;; Query time: 9 msec ;; SERVER: 37.209.192.15#53(37.209.192.15) ;; WHEN: Tue Mar 15 18:30:50 EDT 2022 ;; MSG SIZE rcvd: 176; <<>> DiG 9.16.23 <<>> @37.209.194.15 zoom.us NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 24122 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;zoom.us. IN NS ;; AUTHORITY SECTION: zoom.us. 7200 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 7200 IN NS ns-387.awsdns-48.com. zoom.us. 7200 IN NS ns-888.awsdns-47.net. zoom.us. 7200 IN NS ns-1137.awsdns-14.org. ;; Query time: 9 msec ;; SERVER: 37.209.194.15#53(37.209.194.15) ;; WHEN: Tue Mar 15 18:31:20 EDT 2022 ;; MSG SIZE rcvd: 176; <<>> DiG 9.16.23 <<>> @37.209.196.15 zoom.us NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 28567 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 4, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;zoom.us. IN NS ;; AUTHORITY SECTION: zoom.us. 7200 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 7200 IN NS ns-387.awsdns-48.com. zoom.us. 7200 IN NS ns-888.awsdns-47.net. zoom.us. 7200 IN NS ns-1137.awsdns-14.org. ;; Query time: 7 msec ;; SERVER: 37.209.196.15#53(37.209.196.15) ;; WHEN: Tue Mar 15 18:31:46 EDT 2022 ;; MSG SIZE rcvd: 176 -
@johnpoz said in Zoom Blocked, Completely Stumped.:
Your not pointing directly to roots in your dns config on pfsense are you?? out of the box pfsense resolves, you should not point anywhere.. You should only point to 127.0.0.1 (unbound) and it knows the root servers..
If you can not talk to roots, you wouldn't be able to resolve anything - but you can not query them recursive... You can only ask them for NSs of the tld, If your like forwarding to roots - that would never work..Sorry, I missed this earlier. What I meant to say is that I am using Unbound in it's default state. Unbound only resolves through the 13 root servers via its default settings. There is no forwarding in resolver settings. Everything with internet access is pointed to pfsense for its dns server except for 1 client. There is a AD domain controller which that 1 client points (via DHCP settings) to for its dns. The AD DNS then forwards to pfsense. It's been this way for years without issues.
But the inability to get to zoom.us is universal to all devices on the network, regardless of whether or not it uses unbound directly or if it being forwarded from the AD domain controller.
-
Try bumping up the logging level on Unbound. It must be seeing an error somewhere.
-
@stephenw10 I bumped the log level up to 5 (from 3). Waited until the clock turned to 7:41 and did a DNS lookup. In the log I filtered by Mar 15 19:41:0 and here's what I got:
Mar 15 19:41:03 unbound 25496 [25496:2] info: send_udp over interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: receive_udp on interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: send_udp over interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: receive_udp on interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: send_udp over interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: receive_udp on interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: send_udp over interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: receive_udp on interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: send_udp over interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: receive_udp on interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] debug: cache memory msg=257779 rrset=679453 infra=181905 val=165184 Mar 15 19:41:03 unbound 25496 [25496:2] info: 2.000000 4.000000 2 Mar 15 19:41:03 unbound 25496 [25496:2] info: 1.000000 2.000000 2 Mar 15 19:41:03 unbound 25496 [25496:2] info: 0.524288 1.000000 11 Mar 15 19:41:03 unbound 25496 [25496:2] info: 0.262144 0.524288 15 Mar 15 19:41:03 unbound 25496 [25496:2] info: 0.131072 0.262144 22 Mar 15 19:41:03 unbound 25496 [25496:2] info: 0.065536 0.131072 12 Mar 15 19:41:03 unbound 25496 [25496:2] info: 0.032768 0.065536 19 Mar 15 19:41:03 unbound 25496 [25496:2] info: 0.016384 0.032768 30 Mar 15 19:41:03 unbound 25496 [25496:2] info: 0.008192 0.016384 8 Mar 15 19:41:03 unbound 25496 [25496:2] info: 0.000000 0.000001 6 Mar 15 19:41:03 unbound 25496 [25496:2] info: lower(secs) upper(secs) recursions Mar 15 19:41:03 unbound 25496 [25496:2] info: [25%]=0.0260779 median[50%]=0.0682667 [75%]=0.251718 Mar 15 19:41:03 unbound 25496 [25496:2] info: histogram of recursion processing times Mar 15 19:41:03 unbound 25496 [25496:2] info: average recursion processing time 0.217590 sec Mar 15 19:41:03 unbound 25496 [25496:2] info: mesh_run: end 0 recursion states (0 with reply, 0 detached), 0 waiting replies, 127 recursion replies sent, 0 replies dropped, 0 states jostled out Mar 15 19:41:03 unbound 25496 [25496:2] debug: query took 0.000000 sec Mar 15 19:41:03 unbound 25496 [25496:2] info: send_udp over interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] debug: mesh_run: validator module exit state is module_finished Mar 15 19:41:03 unbound 25496 [25496:2] debug: val handle processing q with state VAL_FINISHED_STATE Mar 15 19:41:03 unbound 25496 [25496:2] info: chased extract ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr ra ; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: logfiles.zoom.us. IN A ;; ANSWER SECTION: logfiles.zoom.us. 3194 IN CNAME us01-logfiles-va.zoom.us. ;; AUTHORITY SECTION: ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 65 Mar 15 19:41:03 unbound 25496 [25496:2] info: no signer, using logfiles.zoom.us. TYPE0 CLASS0 Mar 15 19:41:03 unbound 25496 [25496:2] debug: validator classification cname Mar 15 19:41:03 unbound 25496 [25496:2] debug: val handle processing q with state VAL_INIT_STATE Mar 15 19:41:03 unbound 25496 [25496:2] debug: validator: nextmodule returned Mar 15 19:41:03 unbound 25496 [25496:2] info: validator operate: query logfiles.zoom.us. A IN Mar 15 19:41:03 unbound 25496 [25496:2] debug: validator[module 0] operate: extstate:module_wait_module event:module_event_moddone Mar 15 19:41:03 unbound 25496 [25496:2] debug: mesh_run: iterator module exit state is module_finished Mar 15 19:41:03 unbound 25496 [25496:2] debug: prepending 2 rrsets Mar 15 19:41:03 unbound 25496 [25496:2] info: finishing processing for logfiles.zoom.us. A IN Mar 15 19:41:03 unbound 25496 [25496:2] debug: iter_handle processing q with state FINISHED RESPONSE STATE Mar 15 19:41:03 unbound 25496 [25496:2] debug: returning answer from cache. Mar 15 19:41:03 unbound 25496 [25496:2] debug: msg ttl is 3506, prefetch ttl 3146 Mar 15 19:41:03 unbound 25496 [25496:2] info: msg from cache lookup ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr ra ; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 0 ;; QUESTION SECTION: us01-logfiles-va-9.zoom.us. IN A ;; ANSWER SECTION: us01-logfiles-va-9.zoom.us. 3445 IN A 170.114.15.223 ;; AUTHORITY SECTION: zoom.us. 85858 IN NS ns-888.awsdns-47.net. zoom.us. 85858 IN NS ns-1137.awsdns-14.org. zoom.us. 85858 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 85858 IN NS ns-387.awsdns-48.com. ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 200 Mar 15 19:41:03 unbound 25496 [25496:2] debug: request has dependency depth of 0 Mar 15 19:41:03 unbound 25496 [25496:2] info: resolving logfiles.zoom.us. A IN Mar 15 19:41:03 unbound 25496 [25496:2] debug: iter_handle processing q with state INIT REQUEST STATE Mar 15 19:41:03 unbound 25496 [25496:2] debug: returning CNAME response from cache Mar 15 19:41:03 unbound 25496 [25496:2] debug: msg ttl is 3570, prefetch ttl 3213 Mar 15 19:41:03 unbound 25496 [25496:2] info: msg from cache lookup ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr ; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: us01-logfiles-va.zoom.us. IN A ;; ANSWER SECTION: us01-logfiles-va.zoom.us. 3570 IN CNAME us01-logfiles-va-9.zoom.us. ;; AUTHORITY SECTION: ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 75 Mar 15 19:41:03 unbound 25496 [25496:2] debug: request has dependency depth of 0 Mar 15 19:41:03 unbound 25496 [25496:2] info: resolving logfiles.zoom.us. A IN Mar 15 19:41:03 unbound 25496 [25496:2] debug: iter_handle processing q with state INIT REQUEST STATE Mar 15 19:41:03 unbound 25496 [25496:2] debug: returning CNAME response from cache Mar 15 19:41:03 unbound 25496 [25496:2] debug: msg ttl is 3194, prefetch ttl 2875 Mar 15 19:41:03 unbound 25496 [25496:2] info: msg from cache lookup ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr ; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: logfiles.zoom.us. IN A ;; ANSWER SECTION: logfiles.zoom.us. 3194 IN CNAME us01-logfiles-va.zoom.us. ;; AUTHORITY SECTION: ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 65 Mar 15 19:41:03 unbound 25496 [25496:2] debug: request has dependency depth of 0 Mar 15 19:41:03 unbound 25496 [25496:2] info: resolving logfiles.zoom.us. A IN Mar 15 19:41:03 unbound 25496 [25496:2] debug: iter_handle processing q with state INIT REQUEST STATE Mar 15 19:41:03 unbound 25496 [25496:2] debug: process_request: new external request event Mar 15 19:41:03 unbound 25496 [25496:2] debug: iterator[module 1] operate: extstate:module_state_initial event:module_event_pass Mar 15 19:41:03 unbound 25496 [25496:2] debug: mesh_run: validator module exit state is module_wait_module Mar 15 19:41:03 unbound 25496 [25496:2] debug: validator: pass to next module Mar 15 19:41:03 unbound 25496 [25496:2] info: validator operate: query logfiles.zoom.us. A IN Mar 15 19:41:03 unbound 25496 [25496:2] debug: validator[module 0] operate: extstate:module_state_initial event:module_event_new Mar 15 19:41:03 unbound 25496 [25496:2] debug: mesh_run: start Mar 15 19:41:03 unbound 25496 [25496:2] debug: udp request from ip4 192.168.165.2 port 56469 (len 16) Mar 15 19:41:03 unbound 25496 [25496:2] debug: answer from the cache failed Mar 15 19:41:03 unbound 25496 [25496:2] debug: Cache reply: cname chain broken Mar 15 19:41:03 unbound 25496 [25496:2] info: receive_udp on interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: send_udp over interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:2] info: receive_udp on interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:0] info: send_udp over interface: 192.168.163.1 Mar 15 19:41:03 unbound 25496 [25496:0] info: receive_udp on interface: 192.168.163.1 Mar 15 19:41:00 unbound 25496 [25496:1] debug: close fd 24 Mar 15 19:41:00 unbound 25496 [25496:1] debug: comm_point_close of 24: event_del Mar 15 19:41:00 unbound 25496 [25496:1] debug: close of port 39760 Mar 15 19:41:00 unbound 25496 [25496:1] debug: serviced_delete Mar 15 19:41:00 unbound 25496 [25496:1] debug: svcd callbacks end Mar 15 19:41:00 unbound 25496 [25496:1] debug: cache memory msg=257779 rrset=679453 infra=181905 val=165184 Mar 15 19:41:00 unbound 25496 [25496:1] info: 2.000000 4.000000 1 Mar 15 19:41:00 unbound 25496 [25496:1] info: 1.000000 2.000000 1 Mar 15 19:41:00 unbound 25496 [25496:1] info: 0.524288 1.000000 3 Mar 15 19:41:00 unbound 25496 [25496:1] info: 0.262144 0.524288 10 Mar 15 19:41:00 unbound 25496 [25496:1] info: 0.131072 0.262144 16 Mar 15 19:41:00 unbound 25496 [25496:1] info: 0.065536 0.131072 4 Mar 15 19:41:00 unbound 25496 [25496:1] info: 0.032768 0.065536 4 Mar 15 19:41:00 unbound 25496 [25496:1] info: 0.016384 0.032768 5 Mar 15 19:41:00 unbound 25496 [25496:1] info: 0.008192 0.016384 1 Mar 15 19:41:00 unbound 25496 [25496:1] info: 0.000000 0.000001 2 Mar 15 19:41:00 unbound 25496 [25496:1] info: lower(secs) upper(secs) recursions Mar 15 19:41:00 unbound 25496 [25496:1] info: [25%]=0.063488 median[50%]=0.192512 [75%]=0.347341 Mar 15 19:41:00 unbound 25496 [25496:1] info: histogram of recursion processing times Mar 15 19:41:00 unbound 25496 [25496:1] info: average recursion processing time 0.270629 sec Mar 15 19:41:00 unbound 25496 [25496:1] info: mesh_run: end 0 recursion states (0 with reply, 0 detached), 0 waiting replies, 47 recursion replies sent, 0 replies dropped, 0 states jostled out Mar 15 19:41:00 unbound 25496 [25496:1] debug: mesh_run: validator module exit state is module_finished Mar 15 19:41:00 unbound 25496 [25496:1] debug: val handle processing q with state VAL_FINISHED_STATE Mar 15 19:41:00 unbound 25496 [25496:1] info: no signer, using zoom.us. TYPE0 CLASS0 Mar 15 19:41:00 unbound 25496 [25496:1] debug: validator classification nodata Mar 15 19:41:00 unbound 25496 [25496:1] debug: val handle processing q with state VAL_INIT_STATE Mar 15 19:41:00 unbound 25496 [25496:1] debug: validator: nextmodule returned Mar 15 19:41:00 unbound 25496 [25496:1] info: validator operate: query zoom.us. CNAME IN Mar 15 19:41:00 unbound 25496 [25496:1] debug: validator[module 0] operate: extstate:module_wait_module event:module_event_moddone Mar 15 19:41:00 unbound 25496 [25496:1] debug: mesh_run: iterator module exit state is module_finished Mar 15 19:41:00 unbound 25496 [25496:1] info: finishing processing for zoom.us. CNAME IN Mar 15 19:41:00 unbound 25496 [25496:1] debug: iter_handle processing q with state FINISHED RESPONSE STATE Mar 15 19:41:00 unbound 25496 [25496:1] info: query response was nodata ANSWER Mar 15 19:41:00 unbound 25496 [25496:1] debug: iter_handle processing q with state QUERY RESPONSE STATE Mar 15 19:41:00 unbound 25496 [25496:1] info: incoming scrubbed packet: ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr aa ; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0 ;; QUESTION SECTION: zoom.us. IN CNAME ;; ANSWER SECTION: ;; AUTHORITY SECTION: zoom.us. 3600 IN SOA ns-1137.awsdns-14.org. awsdns-hostmaster.amazon.com. 1 7200 900 1209600 86400 ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 110I immediately copied and pasted it into notepad. Then I tried to filter the log by Mar 15 19:41:1 but I got nothing. I presume the log file had already been written over. If you need more than what I got I'll have to up the size of the log file. Let me know.
-
@stephenw10 I'm digging into this a bit farther and I'm finding a bunch of stuff. I'm finding multiple entries like these:
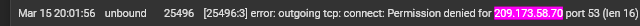
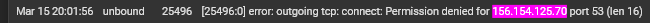
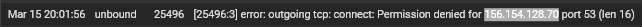
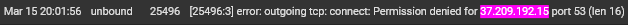
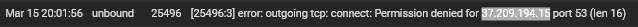
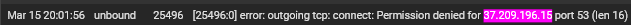
These IPs are all the cctld.us. root servers we identified as authoritative for zoom.us. I'm not sure if this would be the correct syntax for a grep command but I tried to run this command:
grep xxx.xxx.xxx.xxx /var/db/pfblockerng/original/*at the command prompt, for each IP, to see if the IPs were in a pfblocker feed. All of the searches returned nothing.
-
Outbound permission denied like that is usually a local firewall rule. And that is almost always Snort/Suricata or pfBlocker.
-
Yeah if your blocking outbound traffic to the networks or IPs the gtld servers are in your going to have problems!!!
Keep in mind the root and gtlds (ns for tlds) just below the root servers in the hierarchy are globally based.. So they could really be anywhere across the globe.
Blocking the planet is really BAD idea and practice. You should block only specifics.. Or only allow specifics to your inbound traffic.
pbflocker and IPS are both very powerful tools - and quite often users shoot themselves in the foot with them. Like handing a loaded gun to a teenager that has been in your liquor cabinet if you ask me... Yeah they might hit a few targets, but let them play with it long enough and they will end up in the hospital or the morgue..
I only block couple of things outbound.. rfc1918 being a good netizen, and known doh servers IPs. And dot (853).. I do not use doh, I do not use dot - and I want none of my devices using it behind my back... These rules are logged, and any hits I will look into why!! Rest of the internet is open outbound... I never know what I might need to talk to..
-
@stephenw10 @johnpoz I don't have Snort or Suratica installed the system. As far as I can tell, pfblocker is completely shut down. I just filtered both the firewall logs and the pfblocker logs against every one of the 6 IPs and I got no blocks whatsoever. On the firewall I log everything except the default block rule on WAN and as far as I know pfblocker logs every block. I only have 1 geo_ip block alias (some selected Top 40 spammers) but I have it disabled in the firewall on the Lan interface where I've done some of my testing today. I also see in the pfsense logs that the top 40 Spammers feed was last updated March 10. We've definitely been on zoom since then.....this all started today....so I doubt it's an update to that feed. I don't block the planet.
I really grateful and appreciate of your guy's help today. I've learned so much from you guys over the years and continue to learn more and more each day. It's very comforting to know that you guys are out there for when I'm really lost with no direction home!
Right now I'm going to get some dinner and a stiff drink and dig into this again in the morning with a big cup of coffee. I'll let you guys know what, if anything, I find out. Thanks again!
-
@dma_pf so you have no rules in floating?
What is odd unbound wouldn't try tcp unless udp failed normally.. So its odd your permission denied there are all tcp.. Are you not getting an answer via UDP so its trying TCP and that is being denied?
root servers we identified as authoritative for zoom.us
Those are not the authoritative NS for zoom.us, those are the authoritative name servers for the .us tld..
Can you lookup say www.state.il.us, or your state all states should really resolve.. Now that site might might redirect you to a .gov site for that state, etc. but really all states should resolve via the format www.state.XX.us
There are many gov sites that have such a format that should resolve.. I just can think of any other popular.us sites off the top of my head.. But if your having a problem with the us tld servers then you should be having problems looking up anything.us
example
$ dig www.state.il.us +short 216.124.54.83 $ dig www.state.oh.us +short 66.144.73.125 $ dig www.state.ca.us +short www.ca.gov. www.ca.gov.edgekey.net. e65017.dscb.akamaiedge.net. e65017.dscb.akamaiedge.net.0.1.cn.akamaiedge.net. 23.56.237.108 23.56.237.124 $ dig www.state.wv.us +short 129.71.224.134 $ dig www.state.nd.us +short state.nd.us. 165.234.159.23 $ dig www.state.wy.us +short 192.146.215.91What about say apple.us or google.us those should resolve
$ dig google.us +short 142.250.190.100 $ dig apple.us +short 17.253.142.4You can also look to unbound on where it would go look for any domain. So for example ask unbound - hey what were would you go ask for zoom.us I get.
[22.01-RELEASE][admin@sg4860.local.lan]/root: unbound-control -c /var/unbound/unbound.conf lookup zoom.us The following name servers are used for lookup of zoom.us. ;rrset 61601 4 0 8 3 zoom.us. 61601 IN NS ns-1137.awsdns-14.org. zoom.us. 61601 IN NS ns-1772.awsdns-29.co.uk. zoom.us. 61601 IN NS ns-387.awsdns-48.com. zoom.us. 61601 IN NS ns-888.awsdns-47.net. ;rrset 56026 1 0 8 3 ns-888.awsdns-47.net. 56026 IN A 205.251.195.120 ;rrset 56026 1 0 8 3 ns-888.awsdns-47.net. 56026 IN AAAA 2600:9000:5303:7800::1 ;rrset 11466 1 0 8 3 ns-387.awsdns-48.com. 11466 IN A 205.251.193.131 ;rrset 11466 1 0 8 3 ns-387.awsdns-48.com. 11466 IN AAAA 2600:9000:5301:8300::1 ;rrset 52745 1 0 8 3 ns-1772.awsdns-29.co.uk. 52745 IN A 205.251.198.236 ;rrset 52745 1 0 8 3 ns-1772.awsdns-29.co.uk. 52745 IN AAAA 2600:9000:5306:ec00::1 ;rrset 61601 1 0 8 3 ns-1137.awsdns-14.org. 61601 IN A 205.251.196.113 ;rrset 61602 1 0 8 3 ns-1137.awsdns-14.org. 61602 IN AAAA 2600:9000:5304:7100::1 Delegation with 4 names, of which 0 can be examined to query further addresses. It provides 8 IP addresses. 2600:9000:5304:7100::1 not in infra cache. 205.251.196.113 not in infra cache. 2600:9000:5306:ec00::1 not in infra cache. 205.251.198.236 not in infra cache. 2600:9000:5301:8300::1 expired, rto 3426080 msec, tA 0 tAAAA 0 tother 0. 205.251.193.131 expired, rto 3426080 msec, tA 0 tAAAA 0 tother 0. 2600:9000:5303:7800::1 not in infra cache. 205.251.195.120 expired, rto 3426080 msec, tA 0 tAAAA 0 tother 0. [22.01-RELEASE][admin@sg4860.local.lan]/root:If I ask it where it would find the NS for any us. domain
[22.01-RELEASE][admin@sg4860.local.lan]/root: unbound-control -c /var/unbound/unbound.conf lookup us. The following name servers are used for lookup of us. ;rrset 41190 6 0 2 0 us. 41190 IN NS k.cctld.us. us. 41190 IN NS x.cctld.us. us. 41190 IN NS b.cctld.us. us. 41190 IN NS y.cctld.us. us. 41190 IN NS w.cctld.us. us. 41190 IN NS f.cctld.us. ;rrset 41190 2 1 11 5 us. 41190 IN DS 21364 8 1 260D0461242BCF8F05473A08B05ED01E6FA59B9C us. 41190 IN DS 21364 8 2 B499CFA7B54D25FDE1E6FE93076FB013DAA664DA1F26585324740A1E6EBDAB26 us. 41190 IN RRSIG DS 8 1 86400 20220328050000 20220315040000 9799 . gP5Vt4cLr/5t/NsWZaB7v+T5jYVWTbkzitGUFCzI+0EdLQvaZ2Tk06sBaxXeV+B69R7rjv8UD8grD0v4Db3c0udjzPf/zaND/aHK0t+UvNZIc+s57DLriJkh7mhdM8WwKB2XyJxiFfMIpRurLQNCiI8sA0L/0nkRHdQ9u5ZMMOXyMHODoQ7l2JZy5WHPjmvqkFj2zjkB7a7f1AdblYp4Eh/ngYRNxRShFwHBMJCoYaaw067e/JHZSCFEh9Dlgy1JWW9oIvEsc7yIo8KtR1vsc3ZEj1TKQ9QcJiS8FdLEBGwAGDmTZrFxRbDFIKR8p8pthLzcqAiIBOyVdcK8pSh/zw== ;{id = 9799} ;rrset 61668 1 1 11 5 f.cctld.us. 61668 IN A 209.173.58.70 f.cctld.us. 61668 IN RRSIG A 8 3 86400 20220408144101 20220309140106 53985 us. JBNdg17AOx4FnRMwCfCpQLc56OQu8uqyFfTb4HZCHW3DC0Lz6vQ5YDCC5AY9j64QD7SAsf4Ys21Yfjuw9oFoo/oUc/t77BgNfWu5yp1FfErQ4dlFb8ad0meqdc3HxiB0MToqk2TiJqf77dmJrglBMe2qsBZXBLdbJTf2lg52yev1JhZ6jqjgtu7ck0xjS5pITOyLqfnzbaJ/rhlwmQ0a5Q== ;{id = 53985} ;rrset 61668 1 1 11 5 f.cctld.us. 61668 IN AAAA 2001:500:3682::11 f.cctld.us. 61668 IN RRSIG AAAA 8 3 86400 20220408144101 20220309140106 53985 us. kGm+EQqTNs95rihLFCtjW93EgORZFsARKs6uosoY5+16Xfx+iTuTF8bCrK5t/APDlSqeP9BmQrLsQ4IT9loyZClL4euquPizSyPs+EuDetsW/stmbiOyOYB9tk8vLNlLpGWqjTm+fLLdVM3dnXlMy+J/kqKav6Y7QZ+oXLLPMzfCx8jCpn2+CPuOUK2N/LXkVayl5HLLI20+JnnVX0gzaw== ;{id = 53985} ;rrset 61668 1 1 11 5 w.cctld.us. 61668 IN A 37.209.192.15 w.cctld.us. 61668 IN RRSIG A 8 3 86400 20220408151325 20220309144008 53985 us. l3jIDgU9PTHCoNmsSvcAf9dzPe/m+XwrZQoWesnejXWMUt9hIhzw/OWDA/wwx5BlHwUY7xguqFngKLRt+rSQ+Owv5J7cwLBtdfj93Ba1aopdu6SIuHDqUq5J2IArHnZSVSl1/M8eNF/nM4eHoW5FqLudRRWajW+ZG0//DQlz+rAL60nlhedY9HqqoGWzC4boCx2+imaxW8fox91y+mwqsw== ;{id = 53985} ;rrset 61668 1 1 11 5 w.cctld.us. 61668 IN AAAA 2001:dcd:1::15 w.cctld.us. 61668 IN RRSIG AAAA 8 3 86400 20220408151325 20220309144008 53985 us. xdgesCQdB3c5DtkAx3uKTtjduC9o9XzUnH4jRdTQvxckKhd3VhSqIzJz3o9VfhQXSGTCIN0OkwSeXR1sI+61N6p5R3wXROmfWPZTQcaNW01+AokE/kWZelw0n7nn5NS/+ko4+WtoF/snlbfPpJOeQhlNZMKR0LFMukKxd0paQNr8Gd+ygP3VOYkP9X9V1RV4G9hUOKuWZKHBnR++Pfkviw== ;{id = 53985} ;rrset 61668 1 1 11 5 y.cctld.us. 61668 IN A 37.209.196.15 y.cctld.us. 61668 IN RRSIG A 8 3 86400 20220408144101 20220309140106 53985 us. opF4x8u+PRnzbC76K39HF/Yvv4DtUoR9MgQvMqCFnXUnaw2VunGvfbgkSOnJsaspO/+uW2dfyJIChgbIPPCuMWBC1h1LCdaMgVE3BX0Mn/MTilZLBUpHh4SHZMCIYRVOSwW4kD5czo/eOsp+kxBKVQ4Fj7whtiHJzfFNBGdHRNBizfCQzKNPVc5Ap+7uJEmG7/ctAmVNid/dfIq+LmQlwQ== ;{id = 53985} ;rrset 61668 1 1 11 5 y.cctld.us. 61668 IN AAAA 2001:dcd:3::15 y.cctld.us. 61668 IN RRSIG AAAA 8 3 86400 20220408144101 20220309140106 53985 us. KKJb13+9LzpZCOQCJarKyYpTkHqDz5Gt0e2k2Ufsw68uQPVOI9/mPcti8s9QplK57xL9xBpqOI0XXgaYoyJcg0O3swLLQEdxWJrvSoxWFosuvWHk+2lD1mhlbHxWctkGY3FRf/aamxFOI3F72MeFmVjkSeGNNQlXJ43iexYZ7cNnab8WrgHJV4mG9aCVlFqIqxF2YR7shfp9TXxZLP/0qg== ;{id = 53985} ;rrset 61668 1 1 11 5 b.cctld.us. 61668 IN A 156.154.125.70 b.cctld.us. 61668 IN RRSIG A 8 3 86400 20220408144101 20220309140106 53985 us. UHm1VQTRrWMObX5BKnfnxeUt12Lt3Tjhe98a88kamAhHqOiRNYnMPiy5cv1XStX3Ahsy6WkqPZWDCIbh9VB+vovbq+zDf3knGMVwWM8jUYdn0sDAqtTvc5ta/zUSpD4IAN/m06/6FDX7qMPjNYlIBklJO0Rs4OO61LwWKxsKaVg4ytqfbv8zETMNLzANI2ReyNlekmkaOwmh1q788fjI3w== ;{id = 53985} ;rrset 61668 1 1 11 5 b.cctld.us. 61668 IN AAAA 2001:502:ad09::29 b.cctld.us. 61668 IN RRSIG AAAA 8 3 86400 20220408144101 20220309140106 53985 us. YYF79W6LuKWMGCaWU4tmTeBCdVgmXIsm5f3zAQXcm2HEGL9ee8qB3CdLusmsXX1TMFlWBRtzd1EtrA6n1HeqWH6XxctrwHfqb5pa7dyUyjqNzEfzdu5tzMbBlsZhQ2u+Gw1lYsQrZmVCaoVMR1xWCZ5+cMhsly5FaK5K6CRgLayjj8caCyoGEwehBfbO61pUnjssuxqBB5uqbIbKzvSpXg== ;{id = 53985} ;rrset 61668 1 1 11 5 x.cctld.us. 61668 IN A 37.209.194.15 x.cctld.us. 61668 IN RRSIG A 8 3 86400 20220408144101 20220309140106 53985 us. behf21LmbISS+5Rio3bs8AZ+MLtKphX8NmA54/Lp66Xphmv2uVtgGeAyMth0ZtOXJxjsdUvutB5HDdvEfHDs8SB2aVvV7bZWVmst+Z/yCMg1T6rBS9iud75mBKo1eZYGCQmkg4plC1nVXWBohvHXBIGTJo/Glf+p45tDLnHUnjV3oqeqdipi4ttsejkOTz4H6lbuLkN09lUOTThnY5/oYQ== ;{id = 53985} ;rrset 61668 1 1 11 5 x.cctld.us. 61668 IN AAAA 2001:dcd:2::15 x.cctld.us. 61668 IN RRSIG AAAA 8 3 86400 20220408144101 20220309140106 53985 us. fvEmdE8Ml2QxBzDSgyx00/VjmT0hTj2DfVYTZnU+SzuYcfKyouxEQiq0ki6VWBdQrG+njct7o3dcqfTDRAuIO56xFMbRaqAY6KBTz9A2QoyAAUQYuKn/3Nh3uPql1zfrZXykxKxkxEE/p1nyibBEmCGGgeiZdjZcRtciMEx3X4jJfZ+ln0i2AdUhZo0iGfm2fpMvTxCpu5ePl26FQSb3gQ== ;{id = 53985} ;rrset 61668 1 1 11 5 k.cctld.us. 61668 IN A 156.154.128.70 k.cctld.us. 61668 IN RRSIG A 8 3 86400 20220408144101 20220309140106 53985 us. kBqXLarawEcIsC7kkCXWRPH1gOvNqPWu7R4NdTtqmBw/YUrsW08ay8qDEEiwxxUwSf0aNYfs9s8axMdRbwBQus5QqrFHYbpMpM0I9nzERGyVuAR/oQvVB26pSbxZmnV90ArxwCQw9bo2jiNsUo7MfZFKvNBeT9BfGUQ+ZbqHe6smhBf7cGAKdE9kf7EvgaS6d6yBFFh8PzZfTpnD0NAiqg== ;{id = 53985} ;rrset 61668 1 1 11 5 k.cctld.us. 61668 IN AAAA 2001:503:e239::3:1 k.cctld.us. 61668 IN RRSIG AAAA 8 3 86400 20220408144101 20220309140106 53985 us. s+WQGNcSZUpTGGfo8ZGMy3NQmaxKXG8ic0iNWjXPPHiC51sF0UIjJEZYao4Dq482KxKz+RPvWQX8V5Bcj4BSCkTq1Jw53N5DaTURK73oVOTPUbDwHTLzygr9oXMEbRWXHfc/Io7GP3PJU+Yod7Jqqmi5+atLlG3CnG0C3Lw0yCUjA5XFKK8pozVbASRX8x4xvYEH2Yg2PZ+PT29JPr2NLw== ;{id = 53985} Delegation with 6 names, of which 0 can be examined to query further addresses. It provides 12 IP addresses. 2001:503:e239::3:1 rto 376 msec, ttl 454, ping 0 var 94 rtt 376, tA 0, tAAAA 0, tother 0, EDNS 0 assumed. 156.154.128.70 rto 164 msec, ttl 661, ping 4 var 40 rtt 164, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2001:dcd:2::15 rto 376 msec, ttl 666, ping 0 var 94 rtt 376, tA 0, tAAAA 0, tother 0, EDNS 0 assumed. 37.209.194.15 rto 89 msec, ttl 377, ping 9 var 20 rtt 89, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2001:502:ad09::29 rto 376 msec, ttl 454, ping 0 var 94 rtt 376, tA 0, tAAAA 0, tother 0, EDNS 0 assumed. 156.154.125.70 rto 138 msec, ttl 454, ping 6 var 33 rtt 138, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2001:dcd:3::15 rto 376 msec, ttl 666, ping 0 var 94 rtt 376, tA 0, tAAAA 0, tother 0, EDNS 0 assumed. 37.209.196.15 rto 195 msec, ttl 666, ping 3 var 48 rtt 195, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2001:dcd:1::15 rto 376 msec, ttl 377, ping 0 var 94 rtt 376, tA 0, tAAAA 0, tother 0, EDNS 0 assumed. 37.209.192.15 rto 191 msec, ttl 653, ping 15 var 44 rtt 191, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2001:500:3682::11 rto 376 msec, ttl 666, ping 0 var 94 rtt 376, tA 0, tAAAA 0, tother 0, EDNS 0 assumed. 209.173.58.70 rto 115 msec, ttl 377, ping 7 var 27 rtt 115, tA 0, tAAAA 0, tother 0, EDNS 0 probed. [22.01-RELEASE][admin@sg4860.local.lan]/root:That bottom info there when you ask unbound is information on it talking to those different NS, rto, response time, etc.. This is how it figures out the best NS to talk to for any domain.. The ones that answer the fastest, is who is going to ask first next time it gets a query for that domain that isn't cached, etc.
while those other domains like apple.us and google.us will end up pointing to their own NS, to find those name servers you have to go ask cctld servers..
If your having issues talking to cctld servers you would have looking up really any CC domain that use them - like cloudflare.us for example - does that resolve?
$ dig cloudflare.us +short 104.21.80.121 172.67.181.11 -
@johnpoz @stephenw10 Sorry about my delay getting back to you today. In my preoccupation with everything going on yesterday I forgot that I had a root canal scheduled this morning so I wasn't able to get an early jump on this issue today.....nothing related to roots is working for me right now!
I got back a little while ago and read through John's post. Regarding floating rules this is the only one I have:
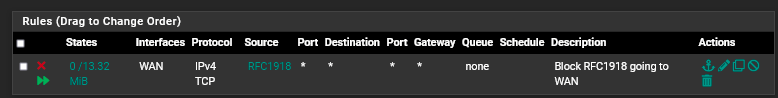 It shouldn't be an issue for what I have going on.
It shouldn't be an issue for what I have going on.I can confirm that in running the tests from John's last post I was not able to resolve any .us domain. However, (drum roll) I think I have figured out the issue.
I've been using a VPN provider, IVPN, for about the last 5-6 years. I have unbound set up to route all the DNS request out through 3 simultaneous wireguard connections to 3 of their servers located in different states and housed in differently owned datacenters. It has worked perfectly over all these years (originally via OpenVPN and then via wireguard when the wireguard package came out (v2.5.2 ?)
I remember reading on these forums about another VPN provider that does DNS hijacking. So I thought that I would route my DNS requests out of unbound through my ISP just in case they implemented some new DNS policy that was blocking me.
As soon as I switched the routing out through my ISP, Verizon, everything works perfectly. I can surf to, and resolve, any .us domain.
I've reached out to IVPN and asked them if they were aware of any DNS issues with .us roots or if they had implemented any type of DNS hijacking. The said they are not aware of any .us roots issues and do not implement any blocking of any king unless you use their DNS with adblocking (which I don't.)
The suggested that it was probably something in my pfsense config. I told them that I didn't believe was the case based on our in-depth troubleshooting. I referred them to this post so they could see what we have done and suggested that they look at the servers that I've been using to see if they can find any issues.
The funny thing is, I have a remote site that is also using unbound through IVPN on a pfsense box. However, unlike my setup I've never upgraded the connections to IVPN to wireguard, they are still OpenVPN. That site is not experiencing any .us issues at all.
In looking back at the DNS error log screenshots they all indicated that the DNS queries that failed were TCP packets. That's got me wondering why that would be if I was using wireguard, which is all UDP, to route all those DNS queries? It seems like unbound didn't get a response back in time to the UDP query so unbound then tried to send a TCP query out. But that query would have been routed out the IVPN wireguard tunnels and wireguard was the thing that denied the request because it was TCP. So what happened to the original UDP query?
Not sure if that means there may be an issue/bug between unbound and wireguard, or something else. That's way above me. But I'm happy to help in any way that I can if you need me to.
Thanks again to both of you. I never would have figured this out on my own unless I would have stumbled on it by dumb luck.
-
@dma_pf said in Zoom Blocked, Completely Stumped.:
wireguard was the thing that denied the request because it was TCP
huh? Wireguard would be completely useless if didn't allow tcp.. While the tunnel itself is UDP, and it doesn't support TCP tunnel. Same goes with openvpn default tunnel is UDP.. But you can run a TCP tunnel connection if you want. That has nothing to do with the traffic and protocol of the traffic inside the tunnel.
So did you validate that you actually did get a response to your UDP queries - they were just too late? It could be that the VPN isn't blocking anything but its possible the cctld servers are blocking the VPN IP?
Glad you got it sorted in the long run.. Sure wish you were running vpn early in the thread, would of for sure had you check without that really early.. Would of saved time - reminder to self!! First question to ask on any thread - are you using vpn ;) If so turn it off for testing..
-
Mmm, are you routing only UDP DNS queries via VPN maybe?
Anyway, yeah, glad you were able to 'resolve' it!

-
@johnpoz @stephenw10 I've done some more troubleshooting and have an update on this issue.
When using unbound in pfsense with its default settings (not in forwarding mode) the inability to resolve the .us sites is directly related to the use of DNSSEC. If I toggle DNSSEC on (default setting) I can't resolve any .us domain when unbound is set to route those DNS queries through the IVPN wireguard vpn tunnel. With DNSSEC off they all resolve correctly.
As I mentioned previously, this is only an issue when unbound is routed out through IVPN's servers. It works perfectly when routed out through my ISP. I've also noticed that the same issue is happening with .biz sites. Why it was working before last Tuesday is beyond me.
If I have DNSSEC enabled and configure a custom option in unbound for a specific site like this:
domain-insecure: "zoom.us"
then that particular site will resolve correctly while all other .us and .biz sites will fail.
In reviewing these (b.cctld.us & a.gtld.biz are one of the roots for .us & .biz):
https://dnsviz.net/d/b.cctld.us/dnssec/
https://dnsviz.net/d/a.gtld.biz/dnssec/There are some warnings about the DNSSEC using a SHA-1 digest algorithm which is prohibited. But there is also a SHA-2 digest algorithm available which should work.
I'm continuing to work through this issue with IVPN's tech support but thought I'd update you guys in case you had any ideas. I'll keep you posted.
-
@dma_pf they really should clean up the sha1 stuff, but your right they really mean nothing with the other algo available and setup.