Authentication Server (LDAP) Missing Client Certificate Option
-
pfSense CE version 2.5.2.
I'm following the guide here, and also watched the video here to add a Google Workspace LDAP authentication mechanism.
Now, when I try to Diagnose the Authentication, it fails, and I don't quite see any reason in the logs, other than possibly the missing authentication.
Mar 15 11:31:15 stunnel 87717 LOG5[ui]: Switched to chroot directory: /var/tmp/stunnel Mar 15 11:31:15 stunnel 87717 LOG5[ui]: Configuration successful Mar 15 11:31:15 stunnel 87717 LOG4[ui]: Service [Google Workspace LDAP] needs authentication to prevent MITM attacks Mar 15 11:31:15 stunnel 87717 LOG5[ui]: UTF-8 byte order mark not detected Mar 15 11:31:15 stunnel 87717 LOG5[ui]: Reading configuration from file /usr/local/etc/stunnel/stunnel.conf Mar 15 11:31:15 stunnel 87717 LOG5[ui]: Threading:PTHREAD Sockets:POLL,IPv6 TLS:ENGINE,OCSP,PSK,SNI Mar 15 11:31:15 stunnel 87717 LOG5[ui]: Running with OpenSSL 1.1.1k-freebsd 25 Mar 2021 Mar 15 11:31:15 stunnel 87717 LOG5[ui]: Compiled with OpenSSL 1.1.1l-freebsd 24 Aug 2021 Mar 15 11:31:15 stunnel 87717 LOG5[ui]: stunnel 5.60 on amd64-portbld-freebsd12.3 platform Mar 15 11:31:15 stunnel 9765 LOG5[main]: Service threads terminated Mar 15 11:31:15 stunnel 9765 LOG5[main]: Terminating 1 service thread(s) Mar 15 11:31:15 stunnel 9765 LOG5[main]: TerminatedI suspect this issue has to do with the fact that it's not using the certificate.
Both of guides I noted above shows that I can choose a certificate when setting up a new Authentication server, but I do not see this option. See below:
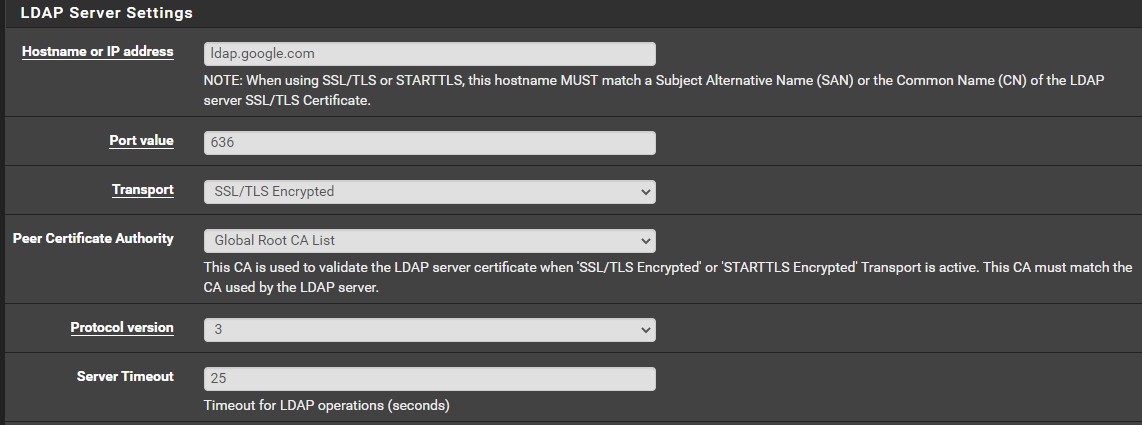
Example from the video guide shows a section called Client Certificate:
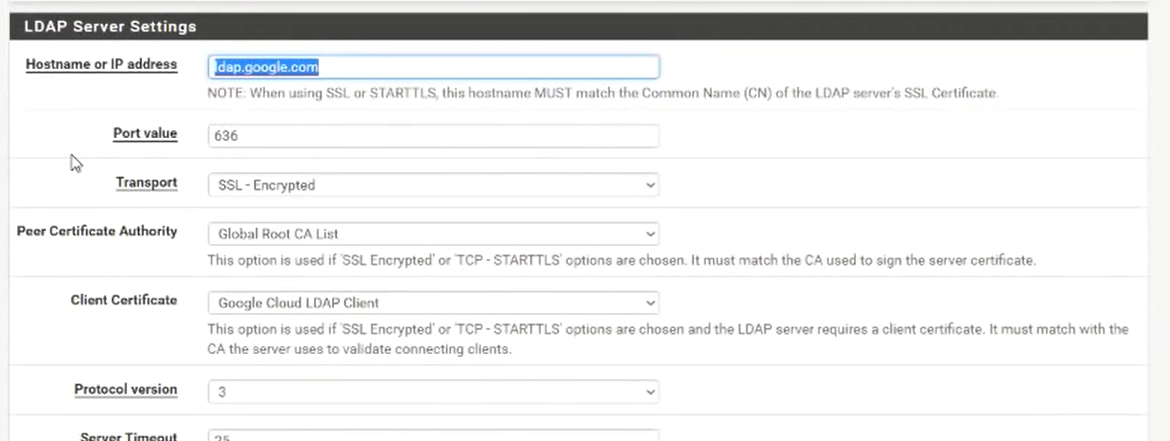
-
Because like is says there the client cert option in the GUI is only in Plus (Factory).
If you're running CE you need to use Stunnel:
https://docs.netgate.com/pfsense/en/latest/recipes/auth-google-gsuite.html#install-the-stunnel-pfsense-package-ce-or-2-4-4-releaseBut you can now also update to 2.6 and then upgrade 22.01 on your existing hardware. You will then have that option.
Steve
-
@stephenw10
Hi Stephen,I did also set up STunnel and I can choose the Certificate there.
I understand now that STunnel will talk to Google and respond locally.
The issue must be something different then, thanks!
-
You have to use local Stunnel port in the LDAP config then, 1636 in the doc, and unencrypted LDAP. Stunnel doe the encryption between itself and Google.
Steve
-
@stephenw10
I was able to get a successful authentication. Thank you!I have another quick question, I hope.
After I switch over the Authentication Server to the LDAP, can I still use the local database as a backup login? How can I switch back if something happens and the LDAP server is no longer reachable (example: expired certificate)? Or how can both be used concurrently.
-
For logging into pfSense itself the authentication will fall back to the local database if the LDAP server is unreachable.
For some types of login, like OpenVPN, you can select multiple authentication backends and it will try each in turn.
Steve
-
We have a HA Stack setup.
I was able to successfully change the authentication server to LDAP and login using LDAP credentials.
However, after doing this, I was no longer able to login to the secondary pfsense with LDAP or local credentials (which I expected).
Then I went to the primary router and changed from LDAP to Local Database authentication, to see if switching back will resolve the issue, but I am still unable to log in to the secondary router.
I am unable to log in to the secondary pfsense with any authentication mechanism now.
Any idea what I did wrong and what I can do to fix this issue?
P.S. I had been checking the settings on the secondary server frequently to compare to the primary server and it looked like the configuration was being transferred properly.
-
Was LDAP authentication working on the secondary before you enabled it for local login?
You should still be able to login as root/admin on the secondary. Been a while but I'm pretty sure that's always local.
Steve
-
I did the LDAP Authentication test on both routers prior to switching and it was successful on both.
At this time, both authentication mechanisms work on the primary router, but none work anymore on the secondary router. I assume when I switch the authentication mechanism on the primary, the secondary switches as well. Regardless of what I set on the primary, none of the mechanisms works on the secondary, even with the admin credential.
-
Hmm, it may have broken the sync user auth if that was not using admin.
You should be able to revert that change at the console on the seocndary.
Steve
-
Sorry about my constant questioning, but you are you suggesting to choose option 3) Rest webConfigurator password?
Will that also reset the authentication server to local database?
-
@stephenw10
Reset webConfigurator password did not work. I am still unable to log in.However, restarting webConfigurator after the reset did work.
Okay thanks, now I know how to recover from this issue. I'll see what I can do about getting this to work.
-
I don't know what happened before, but I think something goes wrong when changing the Authentication server from the primary and allowing the configuration to sync.
I enabled LDAP authentication on the secondary FIRST, and tested it, then on the primary SECOND, and tested it and now both work just fine.
-
Well I was actually suggesting using option 15 to roll back the last changes but knowing it can be fixed by restarting the web service is a better result!
If you see it again you might also try restarting php since the LDAP config is highly dependent on that. It's recommended to the restart php after making changes to LDAP to remove any cached values for example.Steve
-
Ahh, I see, good to know, thanks!