Multiple LANs versus VLANS?
-
@double00kevin said in Multiple LANs versus VLANS?:
do I setup another gateway under STATUS/GATEWAYS?
No. You would only add another gateway to pfSense if you were adding a second WAN connection.
Devices on a second internal subnet will still be routed via your existing WAN, so the same gateway.Steve
-
@stephenw10 Gotcha, so no gateway listing here as well? under Services DHCP/LAN:
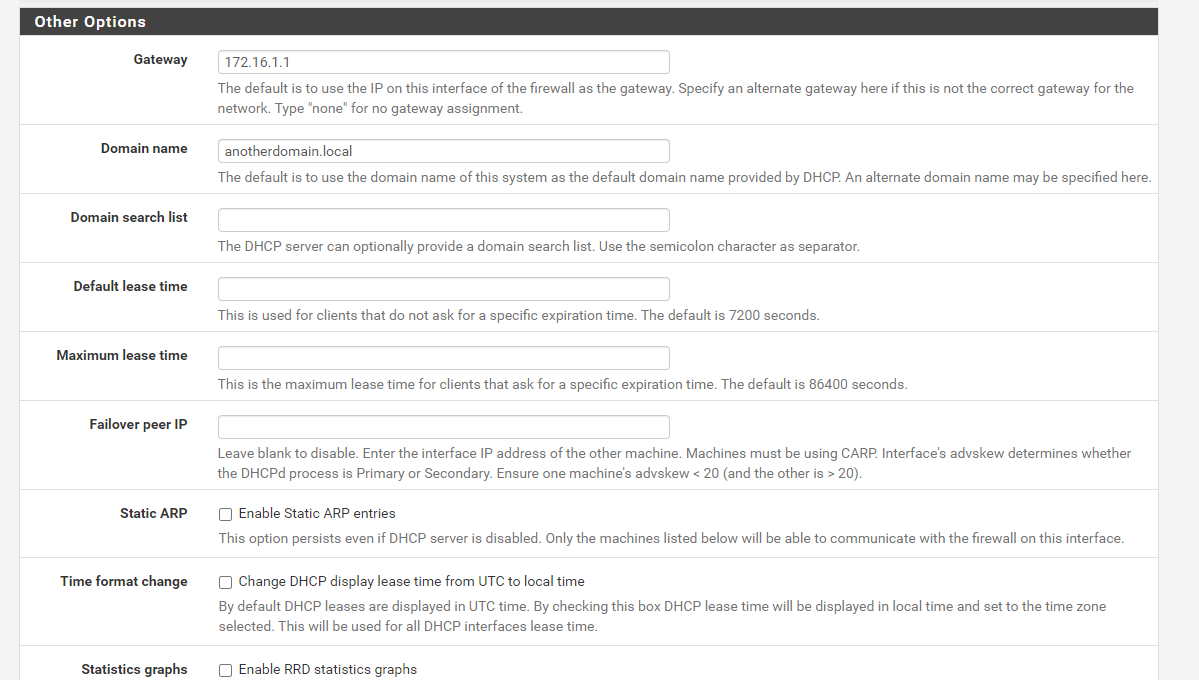
-
That's the gateway you are passing to clients in the new subnet to use. So usually that would be the pfSense interface IP address in that subnet which it uses by default if you don't add anything there.
So don't put anything there unless you need clients to use some other gateway as their default route. Typically that would only be for HA setups where clients use the shared IP.Steve
-
@stephenw10 Roger that, thanks for the explanation!
-
So what would be the benefit of having multiple networks originating from different PHYSICAL ports of pfSense router versus having all of them in separate VLANs that are tied up to one physical port? I thought I read somewhere that having multiple VLANs does impact the overall bandwidth for each network but that may not necessarily be an issue if you are utilizing different physical ports in pfSense. You could still create the same types of rules to control internet access for devices in each network/interface as well as other ones to control access between networks as in interVLAN routing.
My pfSense box also has 6 physical ports too and I guess I am wondering if it would be best to utilize those extra ports somehow or just go the VLAN route to segregate networks. Will my overall internet speed be significantly impacted if I go the VLAN route?
Appreciate your advice.
-
@marinsnb said in Multiple LANs versus VLANS?:
Will my overall internet speed be significantly impacted if I go the VLAN route?
Depends on what your internet speed is.. If your internet speed is 100mbps, and your sharing vlans on physical 1 gig port, prob not.
But if your internet is say gig, and you have a bunch of vlans on the lan side physical 1 gig interface - and you have a bunch of intervlan traffic going on that is using up that 1 gig physical bandwidth - then yes some client going to the internet could be limited.
When you share a physical interface with vlans - the physical interface is going to be the limit.
Lets say you have 4 vlans on 1 physical gig interface.. And you have devices in these 4 vlans all talking to devices in another vlan. They will be limited by the physical interfaces ability.
If you do not have any or much intervlan traffic and your physical interface is same or greater than your internet speed. Then no it shouldn't be much of an issue.
All comes down to traffic flow.. Here maybe a simple drawing will help.
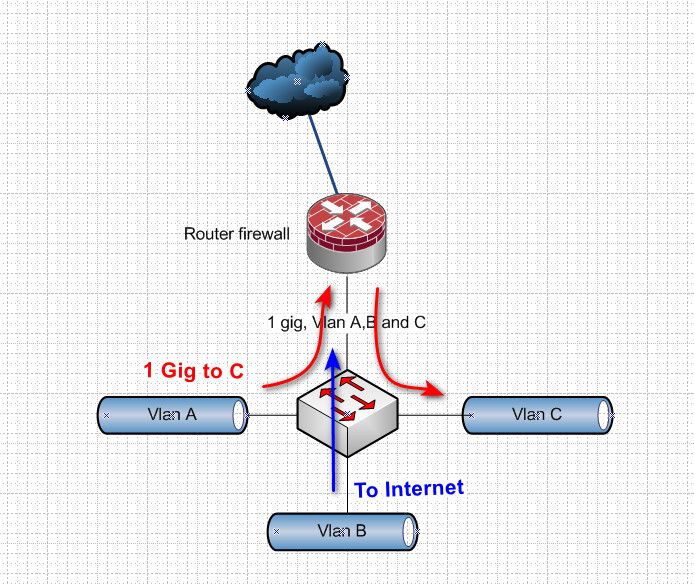
If your interface is 1 gig, and your sharing it with vlans. And A is moving 1 gbps to C (file copy, streaming media, etc.) how could vlan B get 1 gig to internet? They are both using the physical 1 gig interface.
Now if you had it like this..
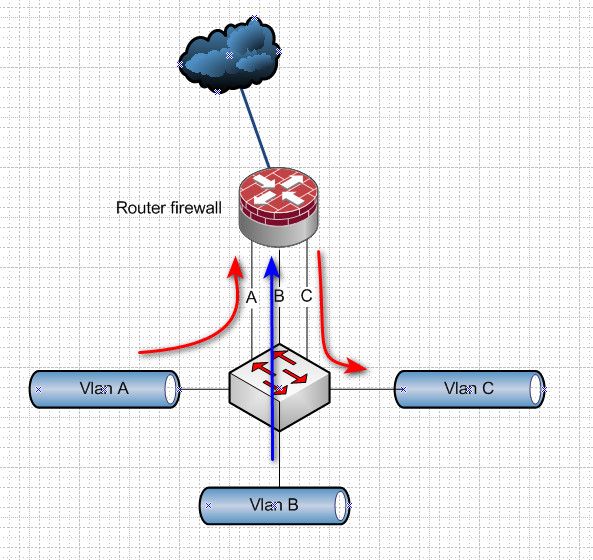
Then the A to C traffic would not have to share physical interface bandwidth with traffic B.
Or if A and C vlans shared physical, and B was on a different interface.
Putting vlans on a physical interface - you will be limited by that physical interfaces speed, they are "sharing" it.. Will that matter? Depends on your traffic flow.
If you have the physical interfaces to spare both on your router and your switch or switches. Then using multiple interfaces for the different network can provide more bandwidth between your vlans or to the interenet that is "not shared"
I have plenty of interfaces on my sg4860, and my switch. So I break out the networks/vlans across multiple physical interfaces.
My wireless vlans all share 1 physical interface to pfsense. They have really no intervlan traffic going between them. And since they are wireless they can't really do full gig anyway.. So even if devices on 2 different wireless vlans talking to stuff in my other vlans, they really can not do gig anyway.. The wireless is their bottleneck.
I'm using the 2nd scenario - my wireless traffic is on the B physical interface. While for example I am moving files to my nas from my pc on vlan A to C.
-
Thanks so much! I have 1Gb internet and not a whole lot of devices so I have been debating on whether to use up the extra pfSense box ports or just the LAN one and segment everything via VLAN.
Marin
-
@marinsnb if your devices don't talk to each other across vlan, then it really doesn't matter - you can only share 1 gig to the internet anyway. So doesn't really matter if they also share 1 gig limit on the lan side of pfsense.
Where it would matter is if you had a lot of intervlan traffic..
-
Good to know - this makes a lot of sense. And the pics you included definitely do help. I do like the 2nd scenario too.
Thanks again!
-
Now that I actually have a little free time, I'm starting to play with my pfsense box like this:
-10.1.1.1/24=management LAN
-10.20.30.0/24=LAB env., have a few poweredge servers with vsphere 7, TrueNAS Scale, unRAID, might get lucky and learn something configuring Microsoft server 2022 ADDNS/DHCP within vSphere on this LAN.
-172.16.1.1/24=Personal, or basic home network for laptops, etc.
-192.168.20.1/24=IOT devices I guess
May try to figure out using the other two ports for the home and lab LANS.....future endeavor maybe.
Directing traffic via firewall rules.
Management LAN will have access to ALLOW ALL and ofcourse pfsense GUI
All other networks, BLOCKED from each other and also blocked to pfsense GUII dunno.......it all sounds right in my head. I'm sure I'm missing some things. You guys foresee any issues?
Is all this needed? I dunno....
Will I break something? All signs point to yes.....
Will I learn something? Fosho!!
Will the kids if and when I shut this mother down with some jacked up configs? Ofcourse but.......I grew up without internet, they can go without on it occasion.