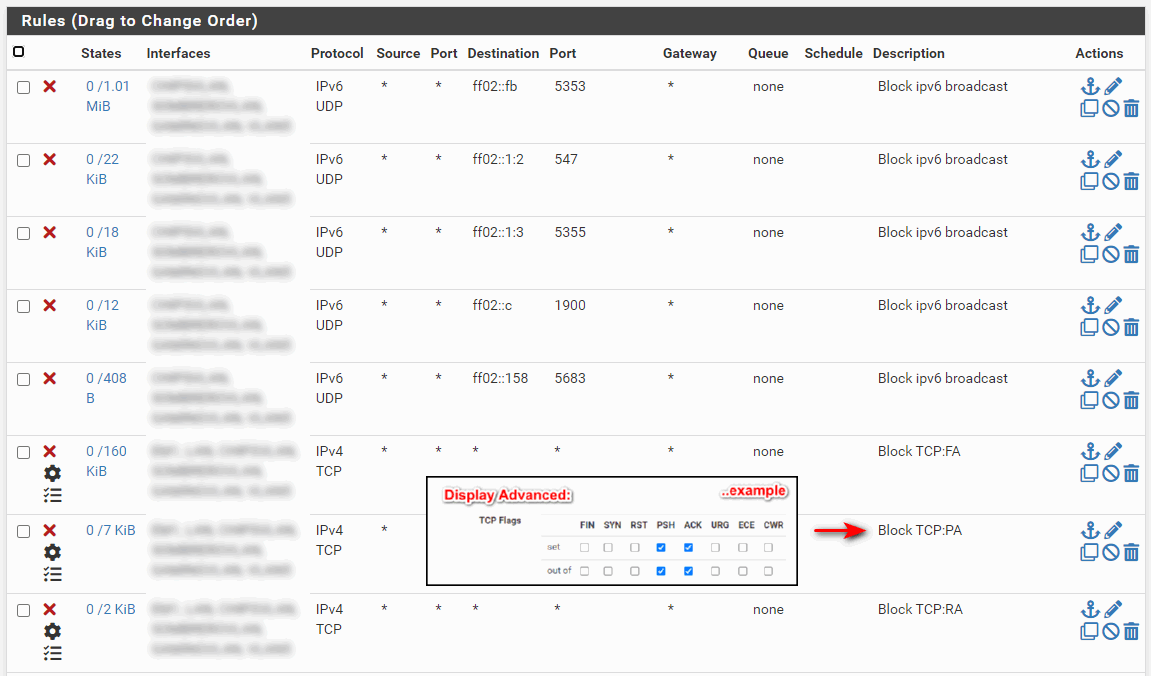
Default deny rule IPv4 (1000000104) - from Firewall to Internet
-
@bingo600 yeah see my edit, added my rule for clarity. Then forced the log by generating some traffic to some rfc1918 that is not local.
what is odd, is the let anything out from the firewall rule should allow the traffic, unless there was no state - maybe the traffic syn went out a different interface - odd why its showing em1 vs wan for example.
-
Version 2.5.2-RELEASE showing this direction triangle.
(I just haven't upgraded yet.. due to uptime ;)) -
@johnpoz
@stiga said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:em1 is the outside interface. I have several network interfaces on the machine.
I wish I could set the WAN as a alias - and point it to the outside interface been used. :)I think OP might have multiple WAN IF's
So maybe the Syn went astray ...
But i fail to see NTOPNG causing that traffic ...
Maybe the Akamai (update check) .. But the M$ traffic ???
M$ = Github ... Hmmm .... Would they have relocated GH to their ip's ?NTOPNG might put the IF's in promiscius , but it shouldn't cause any influence on states or data
-
@bingo600 said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
So maybe the Syn went astray ...
That would explain the block, but would bring about the ? of why? If state was on interface X, and then traffic tried to go out Y (where there was no state) that would kick off the default deny.
Why would the syn go out X, but at some other point would rest of the traffic try to go out Y?
-
@johnpoz said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
@bingo600 said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
So maybe the Syn went astray ...
Why would the syn go out X, but at some other point would rest of the traffic try to go out Y?
You're right , and since OP talks about switching , it seems that it is a manual task , to change WAN IF's.
-
I have several interfaces, but they are not in use..
But I only use one interface for "WAN" - I use the em1. -
This post is deleted! -
-
@stiga said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
how is rfc1918 defined?
What do you mean?
https://datatracker.ietf.org/doc/html/rfc1918
I just created an alias with the rfc1918 space in it.
I still do not see how that is happening to be honest.. There should be no reason for those rules, because traffic shouldn't be leaving from pfsense out some different interface it didn't create the state via..
-
@johnpoz
I disabled all the interfaces that are not in use.
But still I keep getting these messages;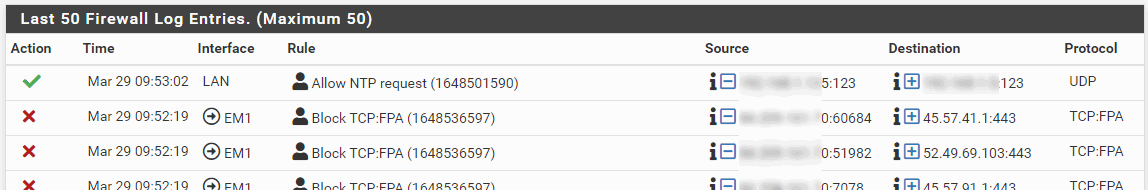
So only thing is that these stops, when I disable/stopp using ntopng.
(and I have reinstalled ntopng and upgraded pfsense 2.6) -
@stiga what is that source IP? Is that your public IP? For this interface?
Are you using any vlans on your em1 interface?
What interface do you have ntop listening on? It shouldn't be even really be on your wan interface - only your lan side.. This is where it will see your devices and what they are talking too...
-
All vlans are on: igb1 (lan). No vlans connected to em1.
ntopng is set to listen to only the lan interface.
-
@stiga Well I have enabled ntopng 0.8.13_10 on my 22.01 pfsense. Been running for like 15 minutes, and not seeing any such blocks.
I even turned logging of default blocks again. I can not seem to duplicate this at all.
Out of curiosity, do you have telemetry enabled? That might explain why its trying to talk to MS and Akami IPs..
I could turn that on and see what happens in like 10-15 minutes..
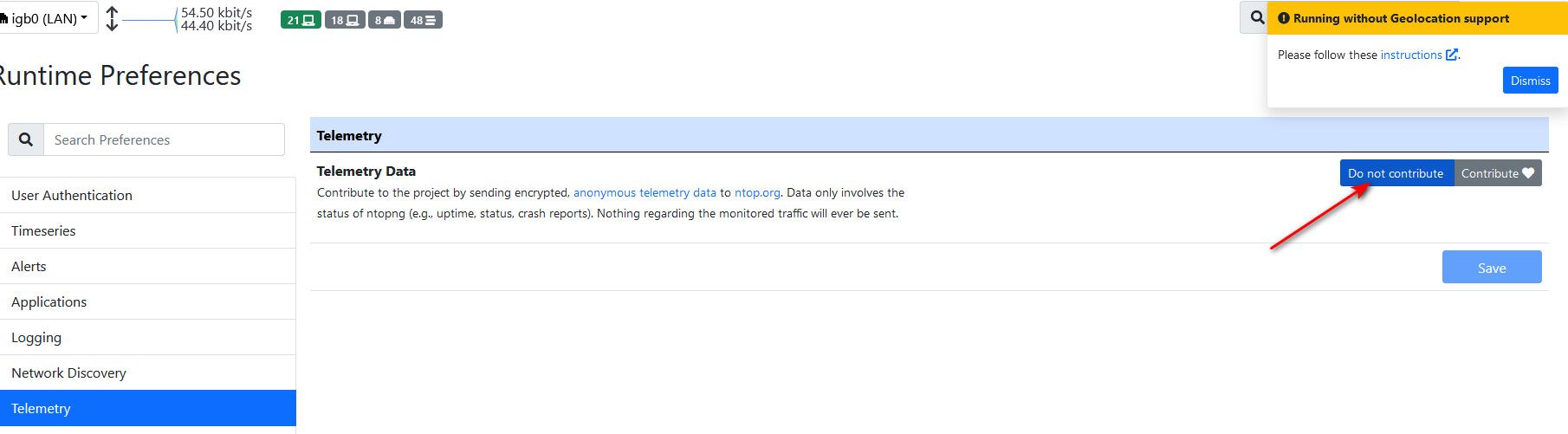
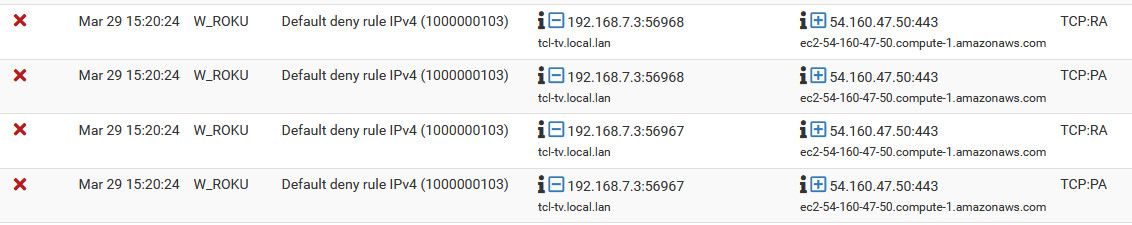
Ok, I have telemetry enabled now, and even got my geoip setup and working.. Will let it run for awhile.. But so far no such blocks, even though now that have default logging back on seeing some other stuff that I didn't use to see ;)
Like my stupid roku tv trying to reuse sessions, etc.
-
I did try to turn on an off Telemetry - it was off default. see if it helps.
Does ntopng does checkup of every IP it sees to see what off application it blongs too ?
-
@stiga no it shouldn't do that, it would understand the application based on the port used, or the protocol, etc.
So have had mine running for like 24 hours now - not seeing any such blocks.. So I have no idea what sort of config you have that is causing such blocks - it makes zero sense.
If application X is using interface A with IP 1234 to talk to something for whatever reason.. Why would it then use a different interface with no state?
Your saying this happens within minutes of turn on ntop.. So not sure how it could be just no keep alives and states went away, etc.
You sure your states are just not being flushed? You can check the age of your current states with pftop.. under the diagnostic menu, and you can see when they are listed to expire, etc.
I for the life of me can not duplicate your issue.. I even have ntop listening on all my local lan side interfaces, etc..
You say the blocks show up in a few minutes. I would take a look at your state table with pftop, filter for say one of the specific IPs your seeing it talk to the MS or alkami ones - and see what happens with them as you see the blocks..
-
I have not been able to replicate this problem either. It seems to have gone away.
Only difference is that Im now using another network card.. Wondering if the other card had some issues/driver issues..
 )
)