Noob q: why can't endpoints ping6 google, nor go further than a close-in outside router?
-
@jknott Thanks for your help!
IMPORTANT: the original Q may have been a red herring. Not this endpoint link-local, and that endpoint did NOT obtain a global addr, so all bets off.
However, I have the same bottom line issue: endpoints can't reach the internet.
As noted, I'm using an HE tunnel; I have a /48 block, and do have v6 address.
Everything works fine from pfSense (I can ping6, traceroute6, etc)
From endpoints, wired or wireless, no.
- Can't ping -6 google
- Can't ping -6 the global address of subnet gateway
- If ping -6 the link-local of subnet gate, the first ping gets destination unreachable, then it works
- if ping -6 the near end address of the HE tunnel, it works (....::1)
- if ping -6 the far end addr of HE tunnel, it fails (....::2)
-
@mrpete so what exactly did you setup?
If you are using a /48 from HE, you would of setup the /64 given in the tunnel details, then another you would pick a /64 out of your /48 for your lan..
That you have to setup... Its more than just setting up the tunnel.
https://docs.netgate.com/pfsense/en/latest/recipes/ipv6-tunnel-broker.html
if ping -6 the far end addr of HE tunnel, it fails (....::2)
Did you setup the gateway in routing?
-
@johnpoz yep. followed all instructions.
Gateway is up, passing data.
gif0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1280
description: WANv6_tun
options=80000<LINKSTATE>
tunnel inet 207.xxx.211 --> 184.xxx.46
inet6 2001:xxx:3c7::2 --> 2001:xxx:3c7::1 prefixlen 128
inet6 fe80::...:fd55%gif0 prefixlen 64 scopeid 0x10
groups: gif
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>And it works100% from inside pfsense.
For testing, I've installed firewall rules allowing ALL ipv6 from WAN, and ALL from all LAN interfaces (I have several VLANs)
I do have CARP. Perhaps there are tricks there. But since it works from pfSense, seems that ought not be an issue.
I thought perhaps my wifi (unifi)... but same with wired.
I'm trunking all LAN through a Netgear GSS108e -- they claim it does ipv6 pass through. No smart switch commands to show me its tables unfortunately...
-
@johnpoz
Note that the failures only exist from endpoints.From pfSense I can ping6 both ends of the tunnel, as well as the outside world...
-
You do pass IPv6 traffic on LAN :
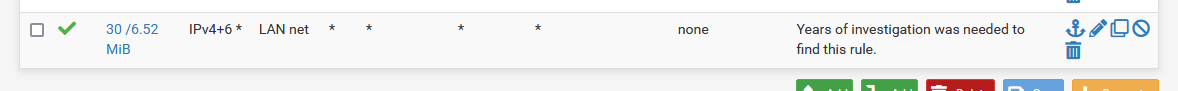
No rules are needed on WAN.
I'm using the DHCPv6 server,
My he.net settings :

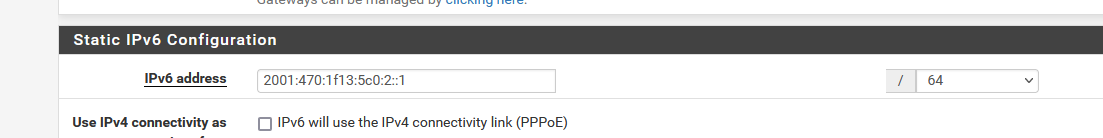
This is my LAN IPv6 setup - note that it's using the single /64 from from he.net, not a /64 block from the the /48 :
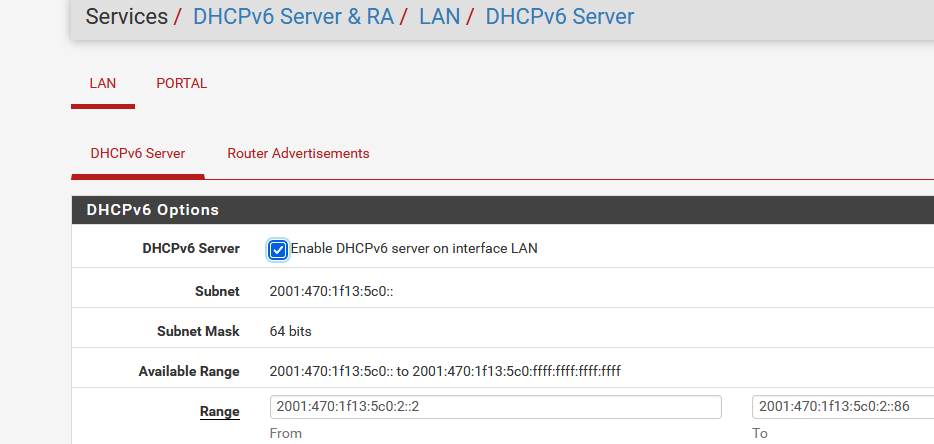
The DHCPv6 server setup with pool :
and
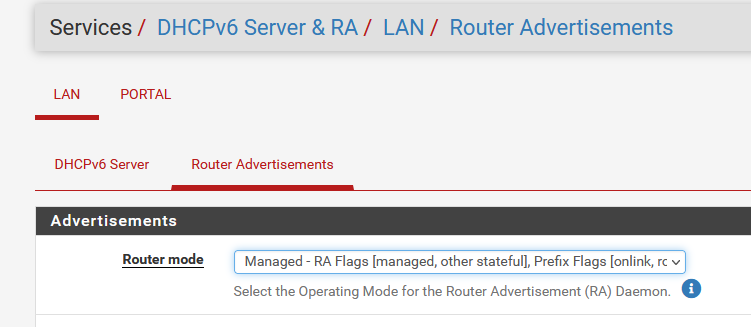
Now you should see "DHCP" IPv6 traffic in the DHCP logs.
I also set up a of of static DHCPv6 assignments so my devices have 'static' IPv6 every where, without assigning anything on the LAN devices.
Have the device connect ones, it will get an IPv6 from the pool. With the DUID obtained, you can assign it an IPv6 outside of the pool. This is of course optional.
Some LAN devices need to be made DHCPv6 aware. Windows PC's : activate IPv6 protocol if it wasn't already activated, and done.edit : The DHCPv6 server probably doesn't work with Android Phone devices, I can't tell, I do not have one of them. Apple stuff works out of the box, the have their Ipv6 and use it.
Same for Microsoft products. -
@mrpete said in Noob q: why can't endpoints ping6 google, nor go further than a close-in outside router?:
From pfSense I can ping6 both ends of the tunnel,
Which says nothing about your lan /64 you assigned, or the firewall rules might not have setup. Or that your end point actually got an IPv6 out of your /64 you setup, etc.
-
@johnpoz said:
Which says nothing about your lan /64 you assigned, or the firewall rules might not have setup. Or that your end point actually got an IPv6 out of your /64 you setup, etc.
Thanks heaps for sticking with me on this.
I have a more complex setup than yours: multiple VLANs, a bunch of Unifi AP's, and CARP. For now I'm ignoring CARP (hopefully doesn't matter) and Unifi (may want to do its own DHCPv6 via PD.)
So, I am using the /48 since I can't pass on /64's without it.
Other than that, quite similar setups:
From HE: 2001:470:432a::/48
Here's my firewall rule in my "All_Internal" group:
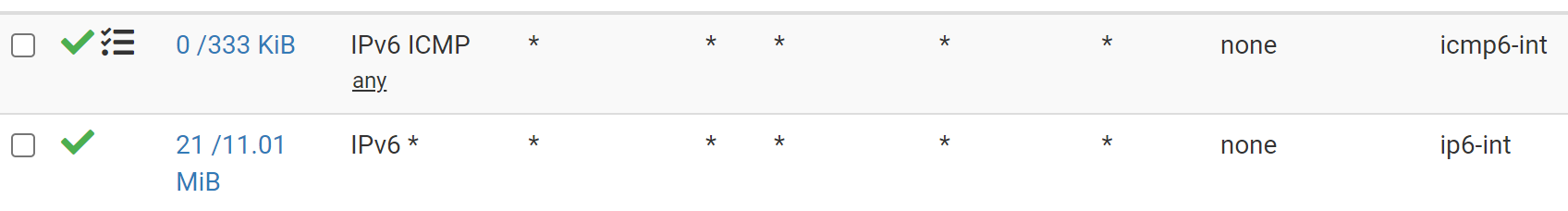
And here's my main VLAN that I'm working on...
A static IPv6 block (similar to v4 subnet number to keep me sane ;) )
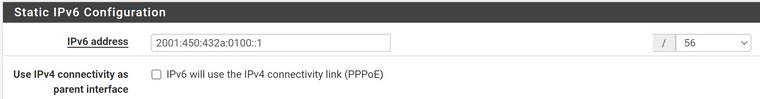
And DHCPv6...
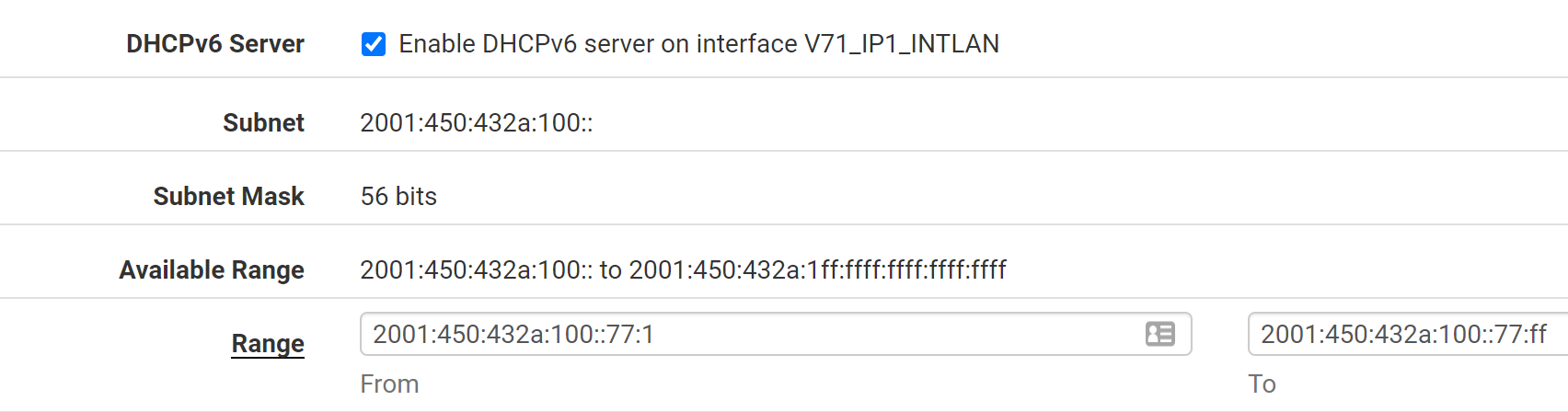
I'm using "Assisted" RA because we do have Android and other devices that don't like DHCPv6I too have a bunch of static DHCPv6 assignments.**
Endpoints do get IP's.
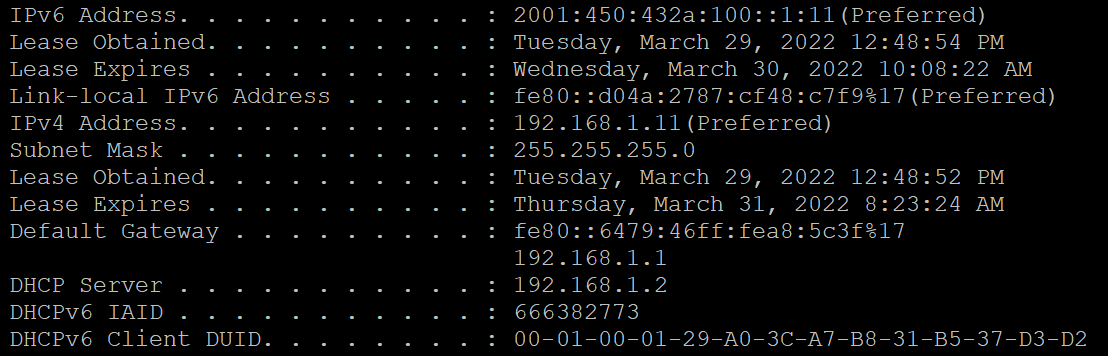
Interestingly the wired Win10 endpoints get immediate result from "ipconfig /renew6" but on wifi it often takes a minute or longer. Sometimes immediate. No idea why at this point.Huh. Just had a thought: do I need to open explicit firewall holes, in pfSense and/or endpoints, for fe80* 2001* etc???
That seems crazy, but bugs abound.
(**Side issue, HPDL: For now I've avoided touching my main email server. The Web/VirtualMin environment does NOT want to grab IP from DHCP but have it manually assigned, and I've not worked out how to extract a DUID from the underlying Debian setup. And anyway, can't break email so ipv6 is fully disabled there for now ;) )
HPDL: Hard Part, Do Later
-
@mrpete said in Noob q: why can't endpoints ping6 google, nor go further than a close-in outside router?:
and I've not worked out how to extract a DUID from the underlying Debian setup
Thats why you activate the DHCPv6 client on a device.
Have it grab an IPv6 from the pool.
You see the lease, you have the dude.
Now you can make a static lease.@mrpete said in Noob q: why can't endpoints ping6 google, nor go further than a close-in outside router?:
in pfSense and/or endpoints, for fe80* 2001* etc???
Hummm.
jimp said ones, way back, that I should add these rules :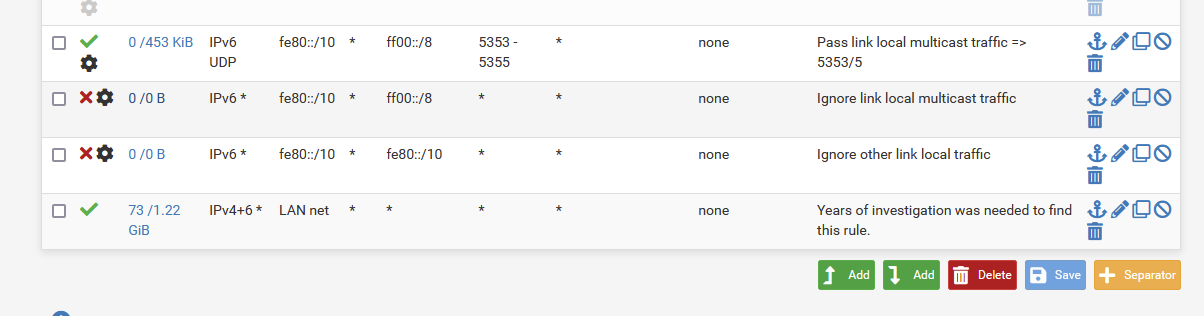
The last one is mine. You saw it already.
The 3 above (two of them are not used) are added later, dono if they are really needed, as the last one pass all IPv6 traffic (IMHO).These are all my LAN rules.
Don't like to block myself. -
@mrpete tell you right now this is wrong!
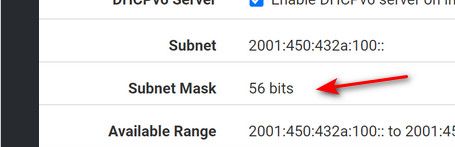
You would not set anything other than /64 here.. Only time you really wouldn't be using /64 in IPv6 is when your doing prefix delegation, or in a firewall rule cidr, etc. or like a p2p link with say a /128
If your actually going to assign an interface an IPv6 address - promise you the prefix is going to be /64 or your asking for issues! And you sure wouldn't be handing anything other than /64 with your dhcpd..
-
@johnpoz
Actually, /56 is just fine... I am (planning to) do prefix delegation etc.GOOD NEWS!!! I found the issue. It was hiding in material on this thread all along.
I decided to go back to basics, and reviewed some material other people have out there.
Here's a key step NOT in the pfSense Tunnel instructions:
- Once you have an IPv6 address on your LAN interface, test it, and your end of the tunnel, from HE: User Functions-> IPv6 Portscan

- This will verify that HE can reach you, and that you have no firewall issues.
In my case, when I pasted the IPv6 of my .1 VLAN in, HE noticed a little issue

- My /48 is 2001:470:432a::/48
- My LAN was 2001:450:432a:0100::1
Picky picky picky, only off by one character LOL
Fixed that (and all of this implications in my DHCPv6 etc) and pretty much everything is working!
Debriefing:
- Everything worked from pfSense because it doesn't actually use any of my IP's. It uses the near end of the tunnel.
- Note too: I also had to solve the MTU default issue (bug?)... no idea why pfSense defaults to 1280 for my tunnel?!!!
- Once you have an IPv6 address on your LAN interface, test it, and your end of the tunnel, from HE: User Functions-> IPv6 Portscan
-
@mrpete said in Noob q: why can't endpoints ping6 google, nor go further than a close-in outside router?:
Actually, /56 is just fine... I am (planning to) do prefix delegation etc.
I don't think so. Your interface should have a /64 on it... What you delegate would be under the delegation pool range.
Your downstream device for example would grab an IP out of the /64 range, and then request a delegation for networks for it to use and hand out behind it.. Its wan would have an IP out of the /64, and it would get a say a /56 that it would use for delegation for stuff behind it.
-
@johnpoz said...
I don't think so. Your interface should have a /64 on it... What you delegate would be under the delegation pool range.
Your downstream device for example would grab an IP out of the /64 range, and then request a delegation for networks for it to use and hand out behind it.. Its wan would have an IP out of the /64, and it would get a say a /56 that it would use for delegation for stuff behind it.
Meaning, what it delegates would not overlap with what it has itself... which is not allowed.
Try it for yourself; I just did:
-
Whatever the size you provide to the interface...
-
Is the TOTAL range available to that interface, including all delegated ranges.
-
If /64, then only /64 or smaller is available for any use under that interface.
By using /56:
- I can set a /64 range for DHCPv6 of the interface
- AND I can allocate a lot of space for delegation (say, /60)
In practical terms...
if /48 is aaaa:bbbb:cccc::
and /56 for an interface is aaaa:bbbb:cccc:9900::Then for that ifce DHCPv6, it has ...9900 through ...99ff available.
- So I can use ...9900 for my own /64 dhcp
- and ...9910-991f would be a nice /60 delegation
- etc.
(BTW, I've learned to allocate from the left in a quad (abcd)... because :1: means :0001: not :1000: ... that took me a few moments to realize!)
-