NTP woes
-
Hi,
I was thinking in the terms letting pfSense tell time on my networks, but read that would be a bad idea? After having read about NTP for a while I am reluctant to let NTP traffic out... What is the best thinking around that? Setting up a stratum is a bit overkill for my needs perhaps. Ideas? Thanks -
The big hand is on the...

Actually, I have my NTP server set up to use 4 public sources, 2 stratum 1 and 2 stratum 2. From a practical perspective, it makes little difference whether you have one common server or not, as NTP is supposed to be traceable back to International Atomic Time, so one source it pretty much as good as another, unless you're worried about extreme precision. If you run your own server and want redundant sources, you should have at least 3 and maybe 5 or 6. One advantage to having more is your own server becomes more accurate due to averaging.
-
I am not sure why letting NTP out is bad. If you want to go that route you will need another method of getting the time.
-
I've been running NTP servers on pfSense for a while. I have an internal LeoNTP GPS stratum 1 server and my pfSense firewalls across multiple sites use it and a couple of other public servers as backup sources.
I've sent DHCP to provide NTP servers to clients and configured everything local to get time from pfSense.
You can also make really low cost stratum 1 server with a Raspberry PI and a GPS you'll get +/- 20us or so accuracy which is about as good as you can expect without a thermally compensated system.
For the vast majority of people using the public pool or https://www.cloudflare.com/time/ is fine. If you don't mind leap smearing time.google.com is also good.
-
-
@stephenw10 said in NTP woes:
I am reluctant to let NTP traffic out...
From clients or from pfSense itself?
Either would be fine though I'm not sure why you think it would be a bad idea.Steve
Yes, I have probably found some "worry about everything treads". These days much focus is on secure protocols, where NTP is not exactly one of them. My only aim is to make the best possible use of the Netgate/pfSense. I really love it in comparison to what I have used over the years.
If NTP indeed is considered harmless, I should allow that, but I would then like to limit what NTP resources clients can get time from. Out of the box, they want to connect to their own ones. Can this be done in a reasonable easy way?
Thanks
-
-
The big hand is on the...

Actually, I have my NTP server set up to use 4 public sources,
Thanks, perhaps a NTP server of my own is what I need to get what I want? I basically want to control where my clients go to get their time. Your setup sounds neat, but a bit complicated for simpler needs perhaps?
-
For the vast majority of people using the public pool or https://www.cloudflare.com/time/ is fine. If you don't mind leap smearing time.google.com is also good.
Agreed, this is probably what I should go for, keeping a stratum server going is a bit much for my needs, I was just concerned about security of the protocol. But as said below, I probably over-thinked this a bit... :)
-
For the vast majority of people using the public pool or https://www.cloudflare.com/time/ is fine. If you don't mind leap smearing time.google.com is also good.
Agreed, this is probably what I should go for, keeping a stratum server going is a bit much for my needs, I was just concerned about security of the protocol. But as said below, I probably over-thinked this a bit... :)
A nice addition would be to use NTPv3, but for some reason cant find where to get the auth keys... will continue looking :)
-
A NTP server is built into pfsense. You just have to configure it. It's not difficult. You just select some public servers to use and enable the NTP server. It's really that simple. You only need one server, but can use multiple for redundancy. If nothing else, you could just use pool.ntp.org. I even created a DNS alias for it, so that my portable devices will use my server at home and the real pool.ntp.org when I'm away.
BTW, my Asus tablet wants to use some server in Asia, so I also created an alias for that server to point it to mine. If manufacturers insist on hard coding an NTP server, they should be using pool.ntp,org, which will geolocate the best server.
-
Agreed, this is probably what I should go for, keeping a stratum server going is a bit much for my needs
Every NTP server is a stratum server. If you use a stratum 1 source, yours becomes stratum 2, with 15 the maximum. Sources such as a GPS receiver are stratum 0, so the NTP server connected to it becomes stratum 1.
Here's some NTP info.
-
-
@viragomann said in NTP woes:
BTW, my Asus tablet wants to use some server in Asia, so I also created an alias for that server to point it to mine.
I simply redirect any NTP requests from my networks to pfSense LAN address, as well as DNS.
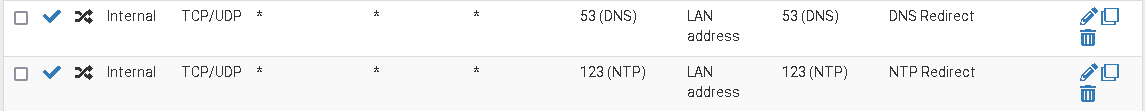
Should also work with localhost as target.
Well, simple when you know it :) Much appreciated, will try to configure this. I suppose I could use destination "This firewall" instead of any LAN Address? Thanks!
-
Agreed, this is probably what I should go for, keeping a stratum server going is a bit much for my needs
Every NTP server is a stratum server. If you use a stratum 1 source, yours becomes stratum 2, with 15 the maximum. Sources such as a GPS receiver are stratum 0, so the NTP server connected to it becomes stratum 1.
Here's some NTP info.
Oh! Will read some. I thought "stratum" was when you had your own GPS. Thanks for the link! :)
-
A NTP server is built into pfsense. You just have to configure it. It's not difficult. You just select some public servers to use and enable the NTP server. It's really that simple. You only need one server, but can use multiple for redundancy. If nothing else, you could just use pool.ntp.org. I even created a DNS alias for it, so that my portable devices will use my server at home and the real pool.ntp.org when I'm away.
BTW, my Asus tablet wants to use some server in Asia, so I also created an alias for that server to point it to mine. If manufacturers insist on hard coding an NTP server, they should be using pool.ntp,org, which will geolocate the best server.
That was the part I was qondering a bit about, but saw @viragomann had already shared his redirect rule for this. Will give it a go! Thanks! :)
-
I suppose I could use destination "This firewall" instead of any LAN Address?
I don't think, that "This firewall" will work, since it covers multiple IPs. As far as I know, that's not working in redirect targets.
As I mentioned, localhost or even single address > 127.0.0.1 should work as well."Internal" is a interface group in my setup, including all internal interfaces I want to rule apply to.
Edit localhost thx to @Bob-Dig

-
Here are my rules, working so far.
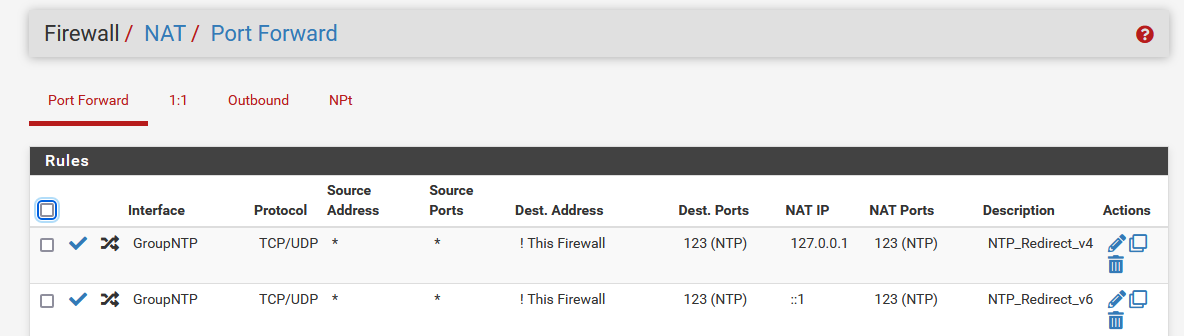
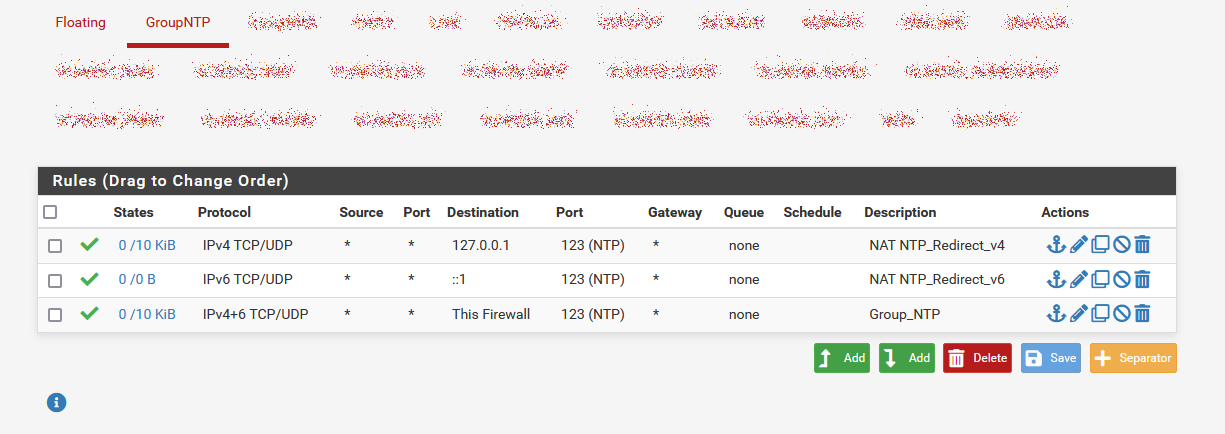
-
@viragomann said in NTP woes:
"Internal" is a interface group in my setup, including all internal interfaces I want to rule apply to.
Had no idea these existed! This makes things a bit easier, thanks!
-