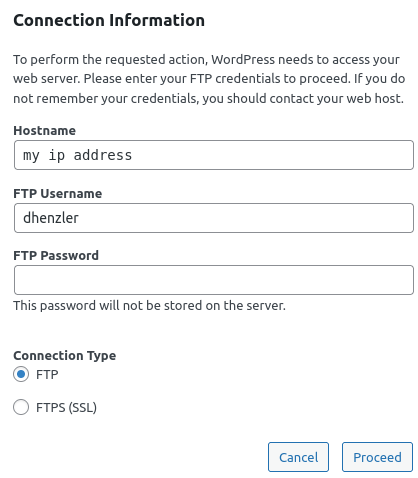
FTP for WordPress - How ?
-
@dhenzler
Sound like you need to port forward to your web server.
Enable the rule when you need access.
Include IP access restrictions if you only need to allow access from a limited number of IP addresses or want to stop access from known bad players.Alternatively limit access via vpn such as
OpenVPN Remote Access Configuration Example
or WireGuard VPN Client Configuration Example -
@patch
According to documentation on FTP... port forwarding won't work. And before I read that, I tried it... and it doesn't work.Tried a few ways, but it looks like the simple ones don't work.
-
@dhenzler said in FTP for WordPress - How ?:
port forwarding won't work.
Not sure where you read that. It for sure works just fine.. But you need to understand what ftp your doing be it active or passive.
https://slacksite.com/other/ftp.html
If your passive, and the ftp server is behind pfsense. You would need to make sure the ftp server actually hands out your public IP.. And you would need to forward the passive ports the server would use as well as the control port 21
This can normally be configured in your ftp server software..
example
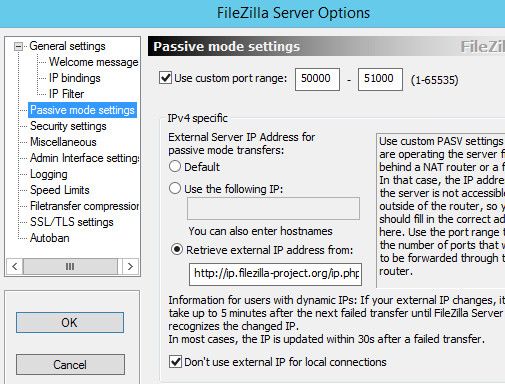
If active ftp, the server would be making the data connection to the client. And you would need to make sure the clients firewall allows for that, and that your not filtering the outbound ports that the server would be connecting to the client via, etc.
I would really suggest you use sftp, ie ftp via ssh. This uses just 1 port, and is way more secure. And is really supported on any OS, even windows now provides for ssh/sftp etc. FTP should of died off 10 some years ago, but finally its support is being removed from browsers, and long standing ftp servers are being shut down, etc.
-
@johnpoz
Thank you John... I'll give that a try. I did see wheree sftp was preferred. And I use that extensively elsewhere. Just port 22 instead of 21. -
@dhenzler said in FTP for WordPress - How ?:
Just port 22 instead of 21.
True - but 21 is just the control port. With ftp there is also the data channel, and the direction that this connection is made from is determined be active or passive. This is where the problem comes in with nats, especially if on both ends, etc. etc..
In ftp the username and password is sent int he clear over the control channel.
Sftp is much simpler to use across natting firewalls for sure since its just the 1 port (normally 22) for both auth and data transfer and everything is encrypted through this connection.
-
This post is deleted! -
@johnpoz
have new other problem...Filter Reload -- what do I do ?
There were error(s) loading the rules: /tmp/rules.debug:22: cannot define table pfB_Top_v4: Cannot allocate memory - The line in question reads [22]: table <pfB_Top_v4> persist file "/var/db/aliastables/pfB_Top_v4.txt" @ 2022-04-25 15:37:59 There were error(s) loading the rules: /tmp/rules.debug:22: cannot define table pfB_Top_v4: Cannot allocate memory - The line in question reads [22]: table <pfB_Top_v4> persist file "/var/db/aliastables/pfB_Top_v4.txt" @ 2022-04-25 15:43:43 There were error(s) loading the rules: /tmp/rules.debug:22: cannot define table pfB_Top_v4: Cannot allocate memory - The line in question reads [22]: table <pfB_Top_v4> persist file "/var/db/aliastables/pfB_Top_v4.txt" @ 2022-04-25 15:45:18 -
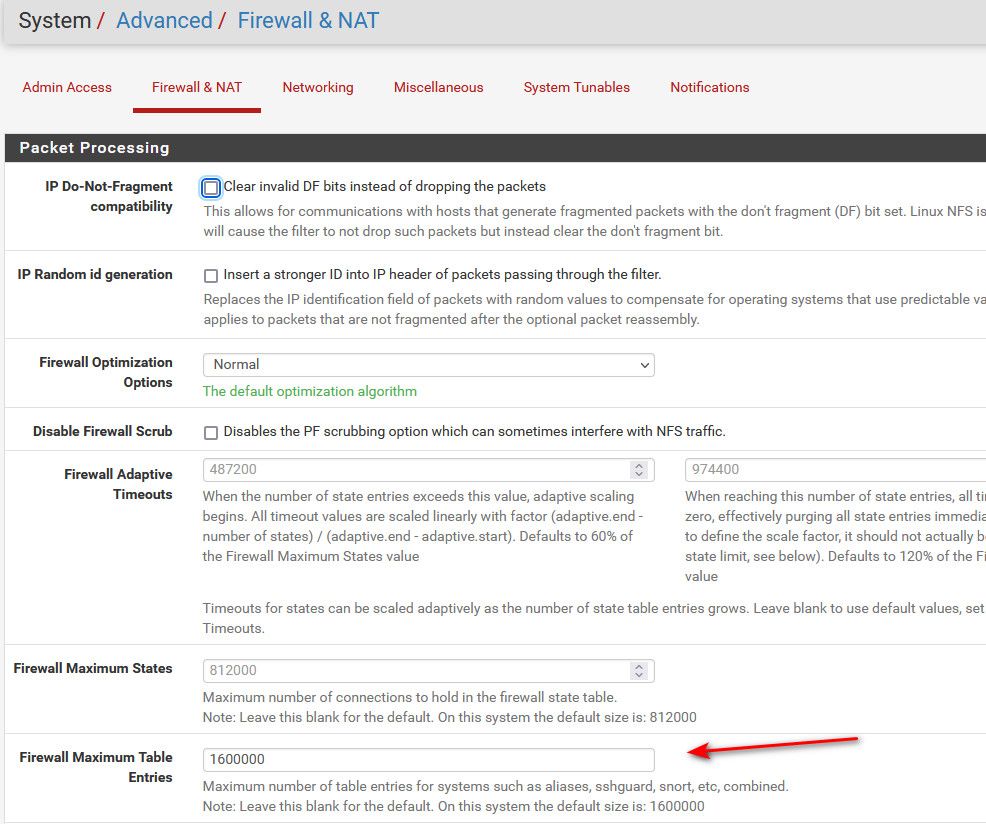
@dhenzler that is related to table size - bump it up..
-
Will resume the FTP issues later...
just did it... we'll see. Hopefully I don't have to do moreThe error message I got was from a failed attempt to load ntopng from command line. It loaded, but didn't show up in Installed packages. Then got a error message:
Apr 25 12:42:04 php-fpm 56175 /rc.filter_configure_sync: New alert found: There were error(s) loading the rules: /tmp/rules.debug:17: cannot define table bogons: Cannot allocate memory - The line in question reads [17]: table <bogons> persist file "/etc/bogons"
Just got my pfSense up and running well yesterday. Thankfully a backup saved me I think... maybe some lefotvers in the database. Ugh !
-
@dhenzler How much RAM is installed, and used/free per the dashboard? Advice here from long ago for pfBlocker was to use a minimum of 2 million table entries, or double the default, whichever was higher. Though, note pfSense has a bug that "on this system the default size is" is whatever was saved in the field, so it's not really valid after it's been adjusted once.
-
@steveits said in FTP for WordPress - How ?:
is whatever was saved in the field, so it's not really valid after it's been adjusted once.
Yeah very true - 1.6mil sure isn't the default ;) Which is what mine shows. I had set that.
-
This post is deleted! -
Being cautious I ran freebsd-version first thinking an update meant for 13 would certainly cause havoc. It's 12.2
But no sooner was it up and running that I discovered I couldn't control it from within pfSense.
deleted the packages carefully
oh well ! live n learn -
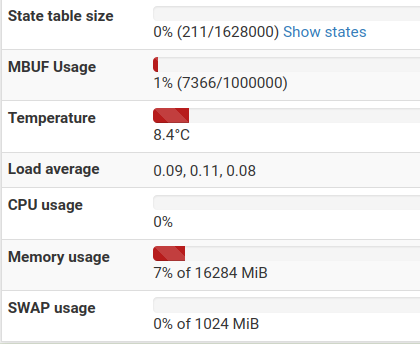
I built my system on a DL360pGen8 with one e5-2650L & 16G memory. Four 73G drives in RAID6 yeilding a pair of 146G mirrored. I figured that things might get used up if I tried to start small. I have plenty of power and the system is just another DL380 in the rack...

-
@dhenzler 16 GB is plenty so it's very likely the table size limit per the above. If you still have issues you can go to Diagnostics/Tables and try to add up the counts of each table but you could also just increase the limit as shown. I suspect the limit is just meant to block a runaway process or crazy list usage from exhausting RAM.
-
Got the system working again, but had to turn off pfBlockerNG
 It was working yesterday, but the episode with trying to load a version not on the list must have left some scars.
It was working yesterday, but the episode with trying to load a version not on the list must have left some scars.My system cannot get duckduckgo.com when it's operating. I've reviewed the Geo lists and tried disabling some of the countries in addition to disabling US and no good has come from those efforts. I have a previous save that was working and won't now. I suppose I could blow the whole thing off and start over. I might !
Frustrating.. !

-
this works...
UPDATE PROCESS START [ v3.1.0_4 ] [ 04/25/22 23:24:42 ]
===[ DNSBL Process ]================================================
Loading DNSBL Statistics... completed
Loading DNSBL SafeSearch... disabled
Loading DNSBL Whitelist... completed[ StevenBlack_ADs ] exists.
===[ GeoIP Process ]============================================
[ pfB_Top_v4 ] exists. [ 04/25/22 23:24:44 ]
[ pfB_Top_v6 ] exists. [ 04/25/22 23:24:45 ]===[ IPv4 Process ]=================================================
[ Abuse_Feodo_C2_v4 ] exists.
[ Abuse_SSLBL_v4 ] exists.
[ CINS_army_v4 ] exists.
[ ET_Block_v4 ] exists.
[ ET_Comp_v4 ] exists.
[ ISC_Block_v4 ] exists.
[ Spamhaus_Drop_v4 ] exists.
[ Spamhaus_eDrop_v4 ] exists.
[ Talos_BL_v4 ] exists.===[ Aliastables / Rules ]==========================================
No changes to Firewall rules, skipping Filter Reload
No Changes to Aliases, Skipping pfctl UpdateUPDATE PROCESS ENDED
-
Now -- Back to making some kind of FTP work on Wordpress for updating Plugins
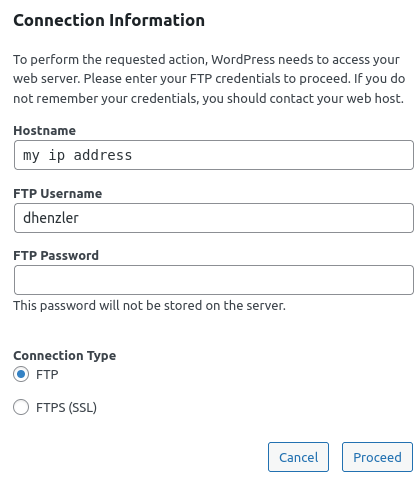
I am not sending in to Wordpress, it requests info from The Great OZ on the Internet !
-
More confused than ever...
Client Behind pfSense
FTPS, or encrypted FTP, is not affected. The proxy could not have affected its traffic before.
A client on a LAN or other internal interface behind a pfSense firewall will likely not notice any difference. Most clients, aside from the Microsoft command line FTP program, default to passive (PASV) FTP, where clients make outbound connections to servers.
Passive mode on the client will require access to random/high ports outbound, which could run afoul of a strict outbound ruleset. Environments with a security policy that requires strict outbound firewall rules likely would not be using FTP anyhow, as it transmits credentials without encryption.
Active mode FTP through NAT will not function as that relies on a proxy or similar mechanism. Use Passive mode instead. Another option is the recently added FTP Client Proxy package which leverages in FreeBSD to allow clients on local interfaces to reach remote FTP servers with active FTP.
Active mode FTP for a client that does not involve NAT (Client has a public IP address) should work so long as WAN rules pass the appropriate traffic back to the client. The client may have a configurable active port range to make that simpler.
Server Behind pfSenseFTPS, or encrypted FTP, is not affected. The proxy could not have affected its traffic before.
A server behind pfSense would work fine with active mode, there would be no difference here. In active mode the server would make outbound connections back to the client, so as long as the firewall rules on the interface containing the server allow outbound connections, it will work.
A server behind pfSense running in Passive mode will function but requires a few items to be configured:
Port forwards or 1:1 NAT to forward not only port 21, but also the passive port range in to the server The passive port range must be configured on the server, corresponding to the range of ports forwarded in the previous step. The server may also need to be configured to account for NAT. Some clients will ignore private addresses in passive responses so this may not be necessary.Sample Configuration for vsftpd
In vsftpd.conf:
Do not allow the client to use PORT
port_enable=NO
Use the hostname in the PASV response (DNS must be setup and match!)
pasv_addr_resolve=YES
Enable Passive Mode
pasv_enable=YES
Set the passive port range (1000 ports)
pasv_min_port=20000
pasv_max_port=20999 -
Client Behind pfSense
FTPS, or encrypted FTP, is not affected. The proxy could not have affected its traffic before.
A client on a LAN or other internal interface behind a pfSense firewall will likely not notice any difference. Most clients, aside from the Microsoft command line FTP program, default to passive (PASV) FTP, where clients make outbound connections to servers.
Passive mode on the client will require access to random/high ports outbound, which could run afoul of a strict outbound ruleset. Environments with a security policy that requires strict outbound firewall rules likely would not be using FTP anyhow, as it transmits credentials without encryption.
Active mode FTP through NAT will not function as that relies on a proxy or similar mechanism. Use Passive mode instead. Another option is the recently added FTP Client Proxy package which leverages in FreeBSD to allow clients on local interfaces to reach remote FTP servers with active FTP.
Active mode FTP for a client that does not involve NAT (Client has a public IP address) should work so long as WAN rules pass the appropriate traffic back to the client. The client may have a configurable active port range to make that simpler.
Server Behind pfSenseFTPS, or encrypted FTP, is not affected. The proxy could not have affected its traffic before.
A server behind pfSense would work fine with active mode, there would be no difference here. In active mode the server would make outbound connections back to the client, so as long as the firewall rules on the interface containing the server allow outbound connections, it will work.
A server behind pfSense running in Passive mode will function but requires a few items to be configured:
Port forwards or 1:1 NAT to forward not only port 21, but also the passive port range in to the server The passive port range must be configured on the server, corresponding to the range of ports forwarded in the previous step. The server may also need to be configured to account for NAT. Some clients will ignore private addresses in passive responses so this may not be necessary.Sample Configuration for vsftpd
In vsftpd.conf:
Do not allow the client to use PORT
port_enable=NO
Use the hostname in the PASV response (DNS must be setup and match!)
pasv_addr_resolve=YES
Enable Passive Mode
pasv_enable=YES
Set the passive port range (1000 ports)
pasv_min_port=20000
pasv_max_port=20999