'arp: writing to routing socket: Operation not permitted'
-
Hello I have been seeing alot of 0.0.0.0 requests for dhcp 0.0.0.0:68 -> 255.255.255.255:67

I wanted to test adding in the firewalls IP address and MAC as a static entry so it stops doing this located here.
I added it in however I received errors 'arp: writing to routing socket: Operation not permitted'
Are we suppose to add in the firewalls IP and MAC? If this is done automatically why is it not listed as an address in the DHCP server already?
-
Your first image shows packets that come into the WAN interface.
This means two things :- You have another device in the WAN network that broadcasts "DHCP requests". pfSense doesn't have a DHCP server on it's WAN. not to be mistaken by a DHCP client. These requests will not be handled by pfSense - and will get dropped, as shown.
- You are logging traffic blocked by the default block (WAN) firewall rule. So now you see them, so you 'should' understand them ;)
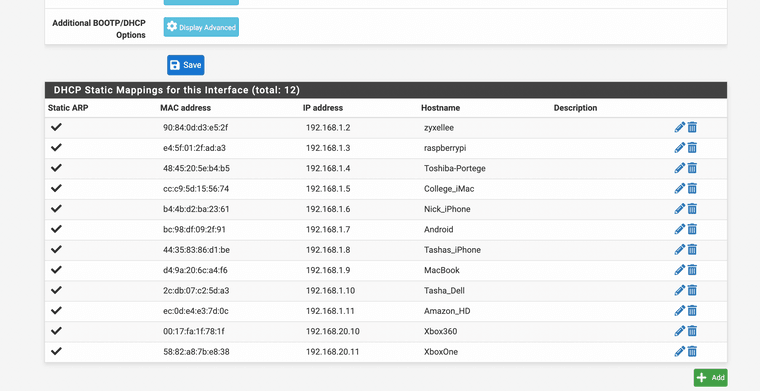
The second images shows your static DHCP leases, use by a DHCP server that servers your LAN(s).
The pfSense GUI firewall doesn't permit you to use MAC addresses.
@jonathanlee said in 'arp: writing to routing socket: Operation not permitted':
I added it in
Added what ?
-
@gertjan I tried to change my layer 2 address of the pfsense wan port to be the same address as the modem to see if this could resolve my problem. However, this course of action killed the WAN connection. I have resolved this with a different post, thank you for your reply. I was told to contact my ISP to report this and turn off logging same as what you recommended.
The I added it was I added a static entry to try to resolve this within the DHCP server on the firewall itself for this post.
-
@jonathanlee said in 'arp: writing to routing socket: Operation not permitted':
turn off logging same as what you recommended.
There is a better solution.
Turning off logging :
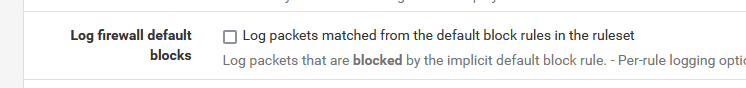
is a sledge hammer approach.
You can keep logging for the default rule activated.
Just added a block rule that doesn't log, and it should block UDP port 68 (DHCP stuff) as you know it exists, but you 'trust' it as it can do no harm except eating up a very small fraction of your WAN band width.
Other non solicited WAN traffic will still get logged.