Pfsense Admin Portal Protocol
-
Dear all, I had setup pfsense long ago but it webpage on browser is loading on http protocol instead of https after I set the https protocol on admin portal. Why is it like this?
Can I force it to use https after installation? Or can it use any secure certificate to it? Please help. Appreciate it. Thanks.
-
Yes, you can change that any time:
https://docs.netgate.com/pfsense/en/latest/config/advanced-admin.html#protocolSteve
-
@stephenw10 My problem is I set it to HTTPS already but it still fall to http protocol on browser. It display not secure on browser.
-
What exactly is it showing? The cert error when you try to connect?
-
@stephenw10 said in Pfsense Admin Portal Protocol:
What exactly is it showing? The cert error when you try to connect?
This is the screenshot of the pfsense certificates?
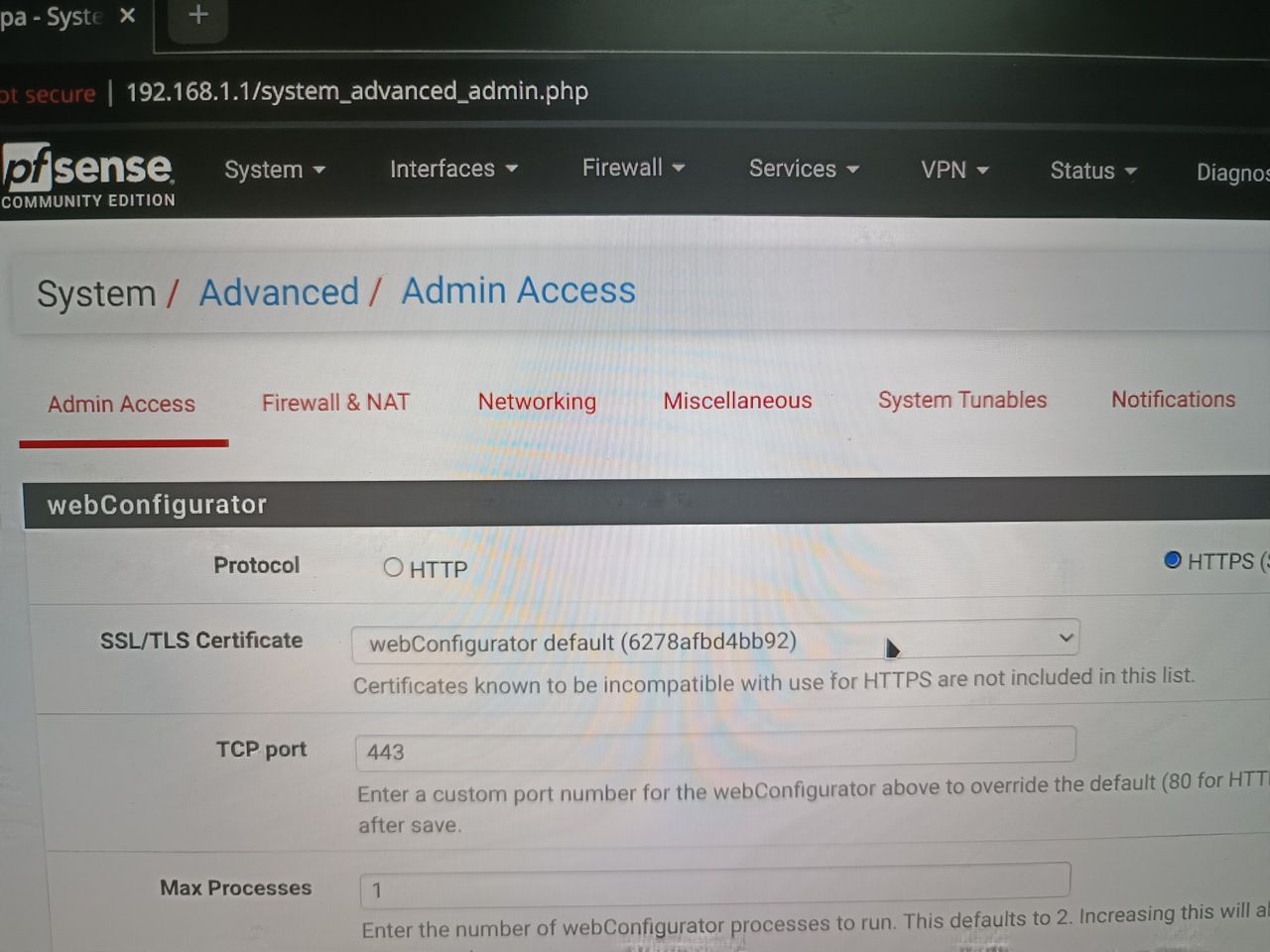
Another questions is how to allow only certain ip address(192.168.1.100) can access the pfsense admin portal (MAC Address)?
Please help. Thanks.
-
Does it show that in all browsers? It's probably showing that because of the self-signed certificate it uses.
You can restrict access to the webgui using firewall rules.
pf is a layer 3 filter, there is currently no ability to filter by MAC address.
Steve
-
@stephenw10 said in Pfsense Admin Portal Protocol:
Does it show that in all browsers? It's probably showing that because of the self-signed certificate it uses.
You can restrict access to the webgui using firewall rules.
pf is a layer 3 filter, there is currently no ability to filter by MAC address.
Steve
I tried with different browsers and all shows the same results.Please share what are the firewall rules use to filter the web configurator by IP.
Please help me on this. I really need to sort this out.
-
How are you trying to manage it? A list of allowed IPs? A list of blocked IPs? On all interfaces or do you have a specific management interface?
-
@stephenw10 said in Pfsense Admin Portal Protocol:
How are you trying to manage it? A list of allowed IPs? A list of blocked IPs? On all interfaces or do you have a specific management interface?
I try to manage by one IP address only and others are block by default.
-
On all interfaces?
-
@stephenw10 said in Pfsense Admin Portal Protocol:
On all interfaces?
Yes, On all interfaces Lan or Opt1, I only allow one IP address to access the web configurator.
-
Ok, so you could do something like this:
Disable the anti-lockout rule on LAN.
Add a floating rule:
Pass, IN, all interfaces, TCP, source: <the_IP_to_allow>, destination: This firewall, port 443.Add a floating rule below that:
Block, IN, all interfaces, TCP, source: any, destination: This firewall, port 443.Make sure you have console access so you can roll back that change if you get locked out!
Steve
-
@stephenw10 said in Pfsense Admin Portal Protocol:
Ok, so you could do something like this:
Disable the anti-lockout rule on LAN.
Add a floating rule:
Pass, IN, all interfaces, TCP, source: <the_IP_to_allow>, destination: This firewall, port 443.Add a floating rule below that:
Block, IN, all interfaces, TCP, source: any, destination: This firewall, port 443.Make sure you have console access so you can roll back that change if you get locked out!
Steve
Dear Steve, Thanks a lot for your explanation.