Google LDAP cert question
-
Hi there. I've been follow these directions:
https://docs.netgate.com/pfsense/en/latest/recipes/auth-google-gsuite.html#gsuite-ldap-serverI have a Netgate with pfSense + ...
I've used Google LDAP a lot. But not with a Netgate. (Also, it's been a while since I've used it)
When I test the authentication, it fails.
Is there a way to see why it failed?
On the Google side of things, For "read group information" I have disabled. Everything else is enabled.
Do I need that enabled?
I'm hoping to use this for L2TP VPN auth. I really don't need to restrict it at all..
Thank you!!
-
Run the test from Diag > Auth
Then check the logs. Is it just failing to auth or failing bind? Some other error?
Steve
-
It fails at bind.
I triple checked everything and it all looks right.
However, I might have done the pfSense CA cert part in correctly?
So I deleted the CA cert I created so now I'm seeing this again:
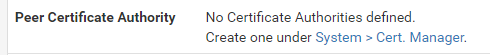
When in the cert manager, What specifically should I be doing or creating? I just created any CA cert there. But I did see a notice "This CA is used to validate the LDAP server certificate when 'SSL/TLS Encrypted' or 'STARTTLS Encrypted' Transport is active. This CA must match the CA used by the LDAP server."
So I'm not quite sure what to do?I know the google cert is imported properly in the cert manager.
Thanks!
-
What pfSense version is that?
I expect to see an option there for 'Global Root CA List'
-
@stephenw10 22.01-RELEASE (amd64)
That what it says if there's no CA certs. Once I add one, it displays "Global Root CA List".
But there were no CA certs by default when I booted the system up. -
Ah! Hmm, that seems like a bug.
Well it should be set to that because Google use a real CA to sign their cert.
Steve
-
@stephenw10 Possibly I imported Google's cert incorrectly? It's in the "Certificates" area, not the CA area.
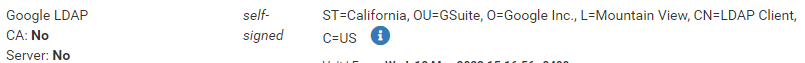
As you can see "CA: No" is part of it? Not sure if that matters.
-
Right, that's expected because it's not a CA. You don't need to import a CA cert for that because Google use a CA that should already be in the Global Root CA List.
pfSense should be able to verify the server cert using one of the root CA certs it already has.
Steve
-
Thanks to Netgate support.
To close this loop, it was this bug:
https://redmine.pfsense.org/issues/11626For now, an stunnel is required.
It should be fixed in 22.09.
Thanks again!