How to restrict Wi-Fi sharing via Mobile Hotspot ?
-
I had a play with snort earlier and set up an Aruba 11D that will act as a wi-fi router up to a test subnet.
Managed to get it to pick up packets with a ttl of 63 with the following:-
alert ip 172.16.7.0/24 any -> !$HOME_NET any (msg: "Possible hotspot TTL 63"; \ threshold:type limit, track by_src, count 1, seconds 300; \ ttl:63; sid:2000001;rev:1;classtype:misc-activity;)Where 172.16.7.0/24 is the test subnet and .100 the AP wan interface.
05/26/22-17:54:06.556058 ,1,2000001,1,"Possible hotspot TTL 63",UDP,172.16.7.100,56324,1.1.1.1,53,43720,Misc activity,3,alert,Allow 05/26/22-18:00:16.619257 ,1,2000001,1,"Possible hotspot TTL 63",TCP,172.16.7.100,63410,17.57.146.150,443,0,Misc activity,3,alert,Allow 05/26/22-18:05:16.633911 ,1,2000001,1,"Possible hotspot TTL 63",TCP,172.16.7.100,63466,17.250.80.105,443,0,Misc activity,3,alert,Allow 05/26/22-18:13:49.475980 ,1,2000001,1,"Possible hotspot TTL 63",TCP,172.16.7.100,63446,17.57.146.154,5223,0,Misc activity,3,alert,Allow 05/26/22-18:18:55.113972 ,1,2000001,1,"Possible hotspot TTL 63",TCP,172.16.7.100,63504,17.250.80.166,443,0,Misc activity,3,alert,Allow 05/26/22-18:26:19.196454 ,1,2000001,1,"Possible hotspot TTL 63",UDP,172.16.7.100,61270,1.1.1.1,53,8327,Misc activity,3,alert,Allow 05/26/22-18:33:57.497050 ,1,2000001,1,"Possible hotspot TTL 63",UDP,172.16.7.100,52221,1.1.1.1,53,24179,Misc activity,3,alert,Allow 05/26/22-18:39:43.342478 ,1,2000001,1,"Possible hotspot TTL 63",TCP,172.16.7.100,63512,23.39.125.62,443,0,Misc activity,3,alert,Allow 05/26/22-18:46:12.775066 ,1,2000001,1,"Possible hotspot TTL 63",UDP,172.16.7.100,54730,1.1.1.1,53,26485,Misc activity,3,alert,Allow 05/26/22-18:53:49.443239 ,1,2000001,1,"Possible hotspot TTL 63",TCP,172.16.7.100,63501,17.57.146.5,5223,0,Misc activity,3,alert,Allow 05/26/22-18:59:20.057976 ,1,2000001,1,"Possible hotspot TTL 63",UDP,172.16.7.100,49909,1.1.1.1,53,49598,Misc activity,3,alert,Allow 05/26/22-19:04:24.584700 ,1,2000001,1,"Possible hotspot TTL 63",TCP,172.16.7.100,63518,17.57.146.6,5223,0,Misc activity,3,alert,Allow 05/26/22-19:09:24.569438 ,1,2000001,1,"Possible hotspot TTL 63",TCP,172.16.7.100,63527,17.57.146.87,5223,0,Misc activity,3,alert,AllowAnd yes wrong direction

-
@nogbadthebad no that is really the right direction.. You would want to stop traffic going out, not let it go out pfsense to the internet, just to stop it from going to the client after it has already come back through pfsense.
Best to stop it before it even passes through pfsense in the outbound direction.
I take it snort would notice all ttls that are not standard, like 64 or 128 or 256, etc..
-
Mmm, that could work if Snort can detect it. If you enabled blocking on that though I could imagine it becoming quite... high maintenance!

-
@stephenw10 yeah but this would be a good solution because it gives you control, if there is something you need to allow out that has an odd ball ttl, like maybe you have your own downstream router, etc.
The thing is 64 is just one of the standards, different oses and even different applications could use different ttls, but they should all be even
-
@johnpoz yep snort is looking at all the packets and only alerting when the ttl is 63.
Basically the rule only lists 1 match every 300 seconds otherwise the logs would fill.
I've set my snort to block in both directions but it seems only to block the dst addresses.
-
@stephenw10 said in How to restrict Wi-Fi sharing via Mobile Hotspot ?:
Mmm, that could work if Snort can detect it. If you enabled blocking on that though I could imagine it becoming quite... high maintenance!

If you do it enough to p**s off the users they'll stop

-
@nogbadthebad well for example browser on windows going somewhere would set ttl of 128, so it wouldn't catch that traffic. You need more rules looking for say odd ball 127 ttl etc.
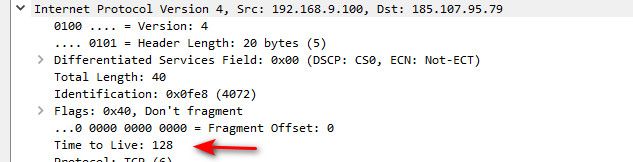
-
I wonder if you could set up a traffic limiter on the interface and get ipfw to rewrite the ttl?
-
@nogbadthebad there is no real reason to rewrite the ttl, unless you were going to limit to 1 on the return traffic to the client.
The best solution if you ask me is as traffic enters pfsense if the ttl is not a standard ttl like 64 or 128 or 254, drop it.. I am not aware of any applications what would use an odd ball ttl out of the gate..
There are lists out that - here is a sample one
https://subinsb.com/default-device-ttl-values/
Since these are most likely tables or phones doing it - need to figure out what their standard ttl is.. Problem one is 255, if you look for 254, that could be a standard one.. etc..
but looking for say 63 and 127 would be quite common..
-
Mmm, you want to block the source address really, the rogue router.
-
@stephenw10 yup that is what I would do, you notice some IP that is sharing its connect - kick the whole thing off.. He will come and ask why not working - say stop sharing!
But just blocking the traffic that is shared - would prob have them scratching their heads to why ;)
-
@johnpoz said in How to restrict Wi-Fi sharing via Mobile Hotspot ?:
@stephenw10 yup that is what I would do, you notice some IP that is sharing its connect - kick the whole thing off.. He will come and ask why not working - say stop sharing!
But just blocking the traffic that is shared - would prob have them scratching their heads to why ;)
You could run snort in non blocking mode and you'd just see the alerts:-
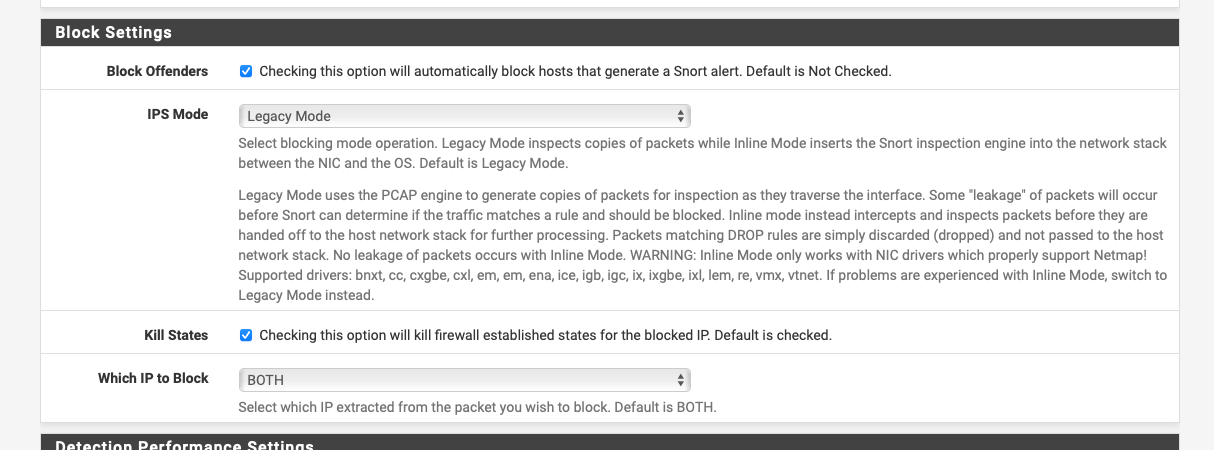
-
@johnpoz said in How to restrict Wi-Fi sharing via Mobile Hotspot ?:
The best solution if you ask me is as traffic enters pfsense if the ttl is not a standard ttl like 64 or 128 or 254, drop it.. I am not aware of any applications what would use an odd ball ttl out of the gate..
Why not set the incoming TTL to 1?. Then the traffic won't reach the devices behind the hotspot.
-
@jknott
How it is configure it ? -
That I couldn't tell you, as I've never done it. But if that's done, it will immediately kill DHCP, DNS and everything else. Others here can tell you more about adjusting TTL.
-
@jknott said in How to restrict Wi-Fi sharing via Mobile Hotspot ?:
Why not set the incoming TTL to 1?.
incoming to where? Pfsense?
This board is about pfsense - incoming would mean to what we are here talking about pfsense.
Setting the ttl to 1 would be leaving pfsense back to the client..
clients to internet ttl 127---> pfsense --> out to isp ttl 126
return traffic some ttl by time it gets to pfsense ---> to client ttl 1
When it hits the sharing device, it should not pass it on to the client..
But in that setup pfsense processed all the traffic.. Why not just block it here
client to internet ttl 127 ---> pfsense = DROP..
Neither option is full proof, and can lead to issues. You don't know, the sharing device might already mangle the ttl, so you don't see an odd ttl, they might set it to 255 as it leaves.
Or maybe the sharing devices says hey I don't care if the ttl is 1, Im going to pass it on to my client anyway..
Either way there is really no way to do this currently in pfsense. You could do some dropping of traffic in snort when you see odd ttl, or you could alert so you know hey this IP might be sharing the connection. This would the lease likely to cause any issues. But let you know IP is possible sharing the connection.
But I am not aware of way you could do anything with the traffic as it is returning to the client from pfsense.
There for sure is no way to do this easy in the gui. If the request is to be able to mangle ttls, or drop ttls that don't meet some criteria - that should be a feature request or a bounty..
-
We have never seriously considered adding this in the past because most people who come here asking about it are really asking: 'please help me break my providers terms of service so I can avoid paying them'. That's hard to support!
Charging per device has always seem pretty pointless to me anyway. Just set data and bandwidth limits and let people use that however they want.
Steve
-
@stephenw10 Something like this would be enough if the TTL from devices reaching my pfsense interface is 64, and my network is 192.168.10.0/27 ?
alert tcp 192.168.10.0/27 any -> any any (ttl:"63"; msg: "connection share"; sid:1; rev:1;)
I wouldn't download any other rules, Snort would run with custom rules only.
-
Incoming from the 'net and being forwarded to the LAN. If it leaves pfsense with TTL 1, it can't be forwarded to hotspot devices, as the TTL will decrement to 0.
-
@mcury said in How to restrict Wi-Fi sharing via Mobile Hotspot ?:
@stephenw10 Something like this would be enough if the TTL from devices reaching my pfsense interface is 64, and my network is 192.168.10.0/27 ?
alert tcp 192.168.10.0/27 any -> any any (ttl:"63"; msg: "connection share"; sid:1; rev:1;)
I wouldn't download any other rules, Snort would run with custom rules only.
Your snort logs will fill up with that, have a look at the rule I posted further up.
It logs 1 occurance every 5 mins.