Intenet is not accessible using PFsense
-
 @stephenw10
@stephenw10
Hi Steve
For NAT , I left it as default
For static route , I did that after many attempts to route the data to ISP , Why I did that because I had an old cisco router and everything was ok until I decided to change it with pfsense, then I tried to add the default route ((0.0.0.0 0.0.0.0) which was existed on Cisco router))to pfsesne, based on that, I did it via GUI of pfsense but I did not find the prefix 0 , so i selected 1In other words , how can I add a default route (0.0.0.0 0.0.0.0) like in cisco to pfsense (edge router) via GUI .
Moreover, I used ospf because the network is very large and I dont want to change anything in the network, just want to exchang the old cisco device (ospf was enabled on it) to pfsense router. Because as I mentioned before , the network was working and internet was available but I decided to put a pfsense router instead of the old cisco router , and when I did that I lost the internet but all the subnets can ping the wan IP of pfsense and ospf is working fine between the subnets and the two nexus swithces and pfsense router.
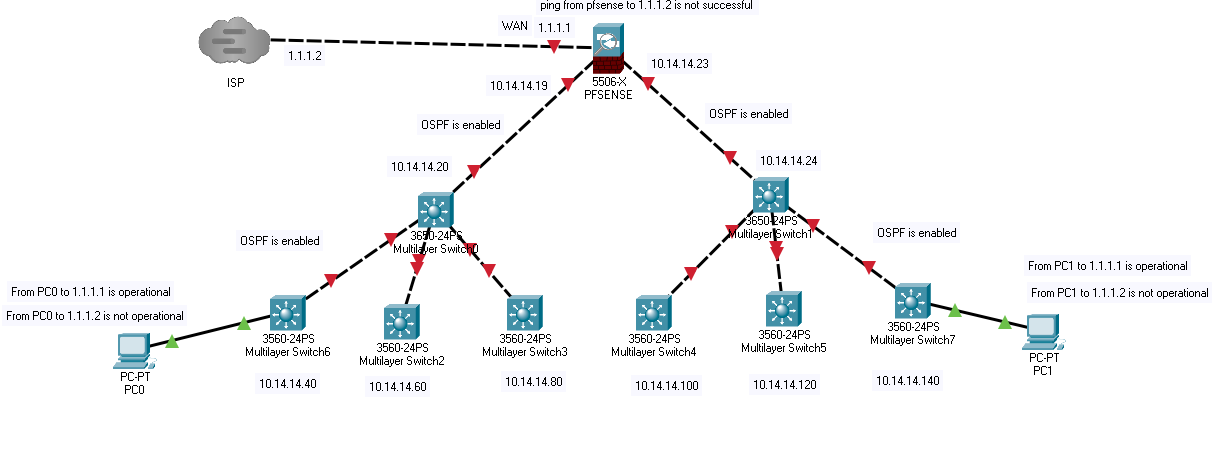
Finally , please find a sample of the attached network design I am talking about.
Thank you again for helping me -
So to be clear none of this is public routed subnets? Everything is using private IPs and requires NAT at the edge?
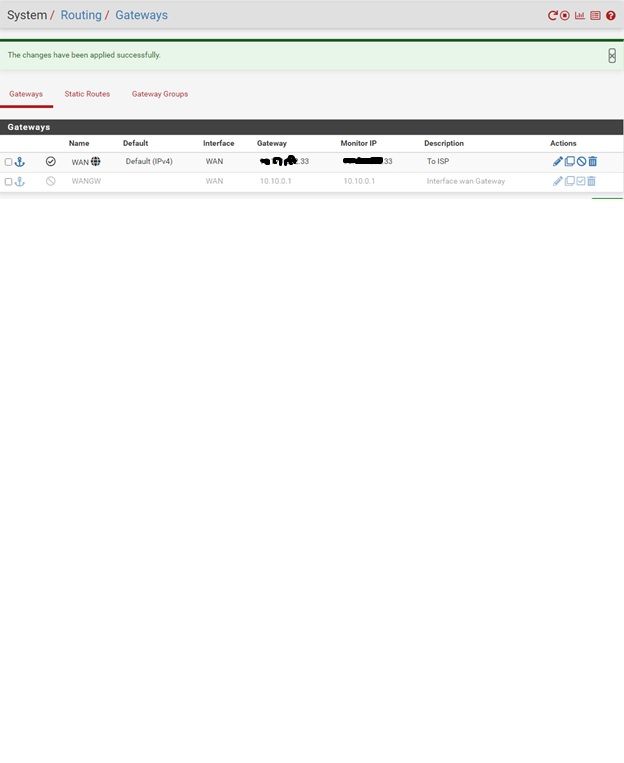
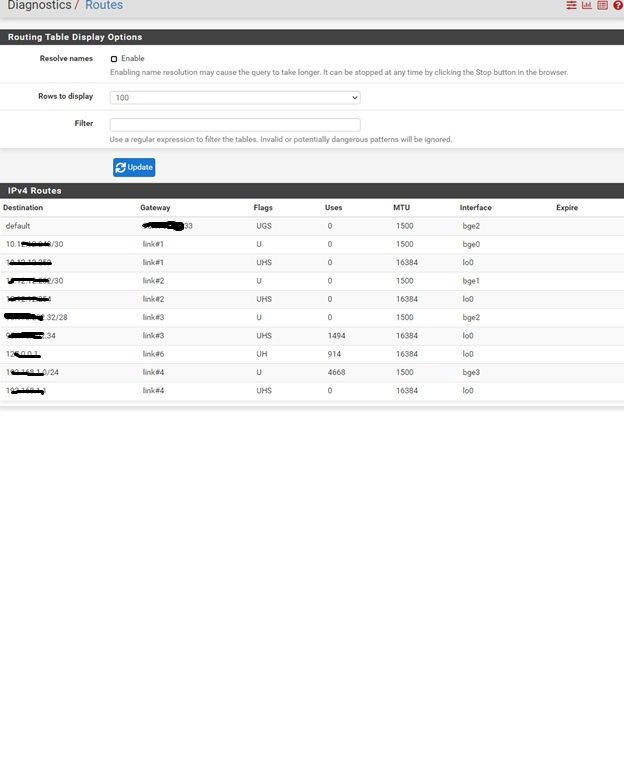
Check the routing table in Diag > Routes. pfSense should already have a default route and it should be via the ISP gateway, 1.1.1.2 in your diagram.
If it does not go to System Routing and make sure the WAN gateway is set as default.
However even if there is no default route or the WAN gateway has not been applied correctly so there's no NAT pfSense itself should still be able to ping 1.1.1.2 because it's directly connected.
Does the WAN even show as linked? Is that set statically?
Steve
-
Yes, the subnets are private and Nat is enabled on edge router which is pfsense.
The default route is configured which refers to 1.1.1.2 (gateway of ISP)
Yes the wan interface is configured statically and when I connect it to switch which goes to isp, it shows up .is it possible the problem from DNS?
I took some snapshots and will sent them soon.
-
And yet from pfSense you cannot ping the gateway?
The gateway may not respond to ping of course. Can you ping anything upstream? 8.8.8.8 for example?
Steve
-
Hi Steve
Exactly , I can not ping the gateway from PFsense and also ping to 8.8.8.8 from pfsense is not successful but when I use the fourth card (opt), ping to 8.8.8.8 and gateway are succesful and can browse internet.NOTE: the fourth card is connected directly to latop and I configured it as dhcp and I use also to access pfsense GUI.
-
please find some snapshots for pfsense router
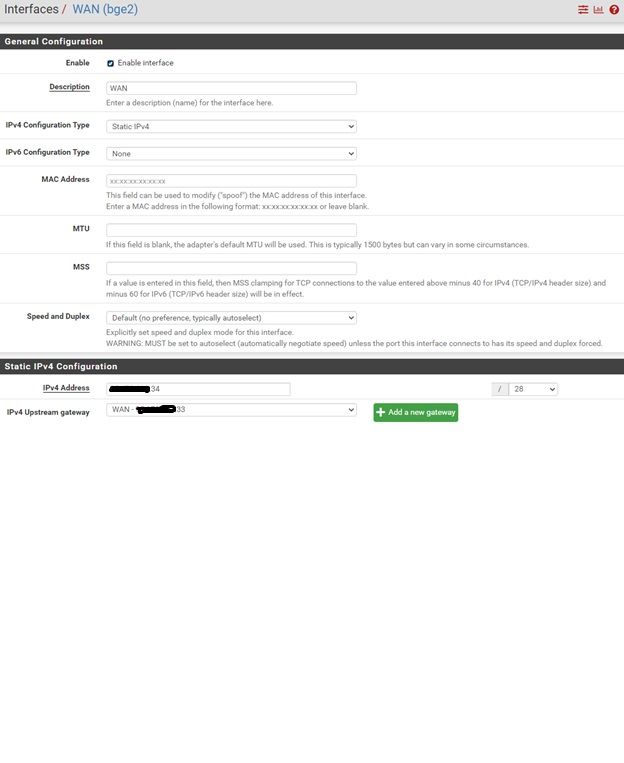
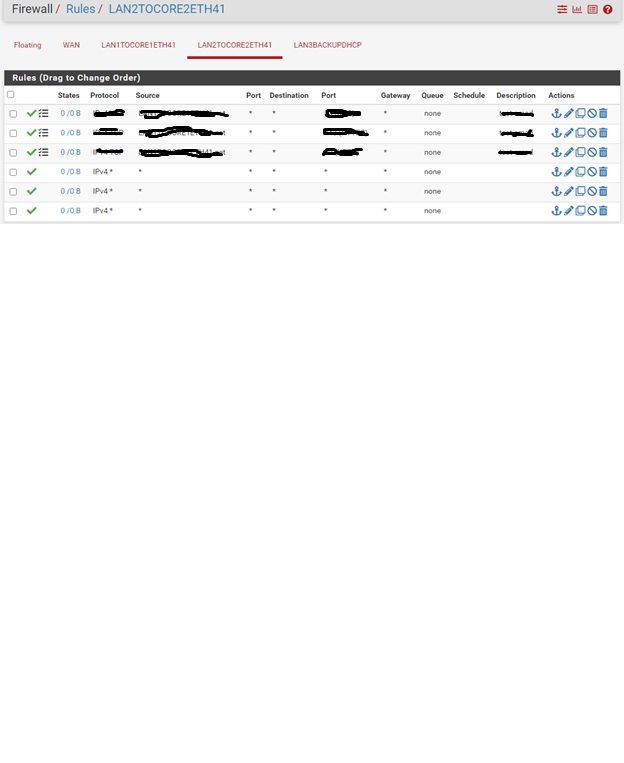
-
@emad4 said in Intenet is not accessible using PFsense:
but when I use the fourth card (opt), ping to 8.8.8.8 and gateway are succesful and can browse internet.
Exactly how are you 'using' that? How is pfSense configured to use that?
Can you ping 8.8.8.8 from the pfSense webgui if you set the IP of the '4th card' as the source?
You need to work out why pfSense cannot ping the gateway before doing anything else. That is a basic layer 2 (maybe even layer 1) problem. Nothing else will work until that does.
Steve
-
Yes but the first and second cards are connected to nexus switches while the fourth card is not.
I tested different cables but the same thing.Yes ,I can ping 8.8.8.8 from pfsense shell and the IP is set on 192.168.1.1
-
@emad4 said in Intenet is not accessible using PFsense:
I can not ping the gateway from PFsense and also ping to 8.8.8.8 from pfsense is not successful
So how is that different to that? What were you doing that failed?
It shouldn't make any difference where you ping from internally since you have auto outbound NAT set. All traffic appears to come from the WAN IP.
Setting the source to the WAN should always work as it's in the same subnet as the gateway.
Steve
-
Almost everything is default
I don't know what shall I do -
Well if you can't ping the gateway from pfSense then either the gateway is not responding or pfSense is not actually connected to it.
Does the gateway appear in the pfSense ARP table?
-
@stephenw10
Concerning the gateway , it is working correctly because when I use the cisco router instead of PFSesne , the ping to gateway is ok.
but as you said , perhaps the pfsense is not connected to gateway, and that led me to a fact which is , there is a cisco switch between the pfsense and the gateway(ISP) and there are some configuration on it , so maybe the problem from there?
concerning the ARP table , I need to check that. -
@emad4 said in Intenet is not accessible using PFsense:
there is a cisco switch between the pfsense and the gateway(ISP) and there are some configuration on it , so maybe the problem from there?
Certainly could be. If it's not in the ARP table it's never going to work. And that is a layer 2 problem at least.
-
I discovered that ping between pfsense and gateway of isp is ok. (I was wrong before because I said ping is not ok bt pfsense and isp gateway)
Also ping from pfsense to 8.8.8.8 is ok
Ping from any lan to pfsense wan ip is OK
But ping from any lan to gateway isp is not successful. -
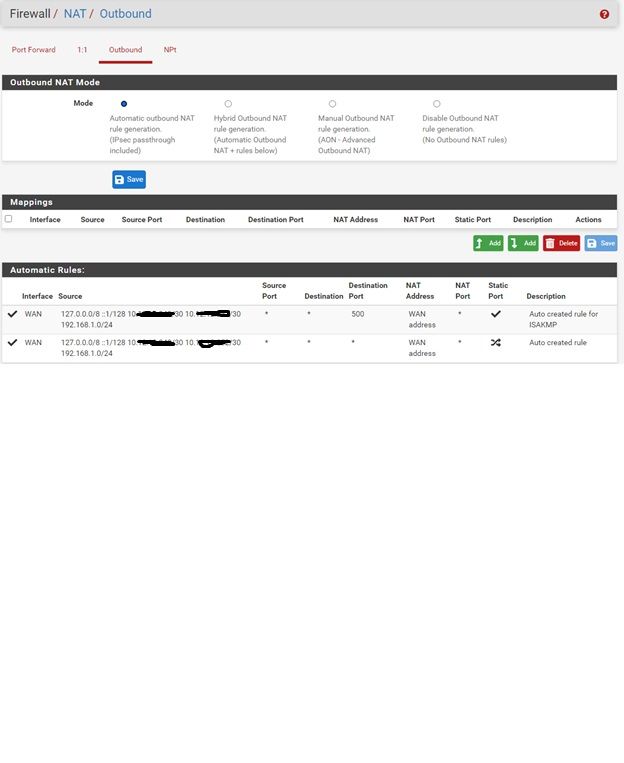
Ok, that implies there is no route back which probably means outbound NAT is not being applied.
Start a ping to the gateway from some internal client that fails. Then check the state table.
You should see two states created, on the internal interface and on the WAN interface. The on the WAN should show NAT as it leaves.
Steve
-
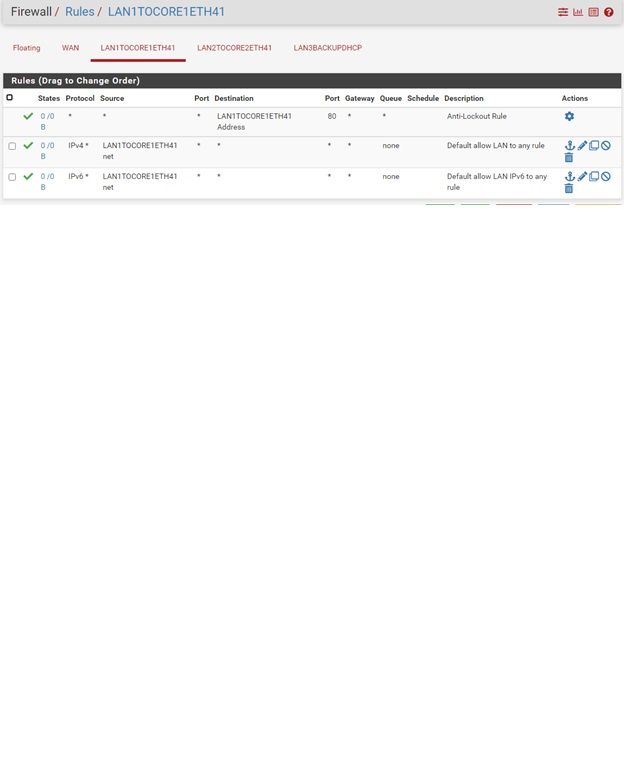
Reviewing the above screenshots you posted you have, for some unknown reason, obscured your internal private IP range, But it looks like the automatic outbound rules only cover the LAN subnet and local /30 transport subnets.
Switch to hybrid mode, add rules to cover other traffic. That could be one rule for all local 10. subnets.Steve
-
Okay , I will switch to hybrid mode and will give the result, but how I can add a rule to cover all the subnets , I think I have approximately 24 subnets, is it something like 0.0.0.0 0.0.0.0 next-hop-ip.
Note: I did not change anything in nat and I left it as default.
-
Moreover, how to check that pfsense is sending the back route to cisco switches , ospf is enabled on all devices including but how I can make pfsense redistribute routes via ospf, I remember I checked an option under the title redistribute in ospf setting and don't know if that was enough .
-
If they are all 10.x.x.x as shown in your diagram you can just use 10.0.0.0/8. That's probably a wider subnet than you need though. Better to specify the minimum subnet size to cover them.
Steve
-
Check OSPF status on the switches to see if pfSense is advertising a default route.
Or just try to connect out from a client and see if that traffic is passed in pfSense.
St5eve