pfSense with OpenWRT Guest logon with VLAN
-
@johnpoz I know you are a busy guy and I've certainly learned a lot of things from you... So I do respect your abilities. If you wan't to help me play with this, I'll gladly send you a WRT3200ACM to bash around.
-
@ramosel really? Sure why not - I could do that ;)
But why doesn't it show a little radio icon, when your lan shows 2?
BTW - why do you have guesttest on channel 10? Channels to use for 2.4 are 1,6 or 11.. That wouldn't be the reason for your issue - but not a good channel to choose..
-
You dont need OpenWRT to handle that.
Use a range extender together with pfsense and a VLAN capable switch.
https://www.asus.com/dk/Networking-IoT-Servers/Range-Extenders-/All-series/RP-AX56/
This works like a charm creating the networks you need and letting pfsense handle VLANs.
-
@johnpoz said in pfSense with OpenWRT Guest logon with VLAN:
@ramosel really? Sure why not - I could do that ;)
But why doesn't it show a little radio icon, when your lan shows 2?
BTW - why do you have guesttest on channel 10? Channels to use for 2.4 are 1,6 or 11.. That wouldn't be the reason for your issue - but not a good channel to choose..
John, you are so right.. But, it's my "testbed" for this guest network issue. I live in a Loooong house stretched out across a mountain side in a T shape with the vertical element of the T traveling up the mountain. My "production" WAPs ARE on 1, 6 and 11... at the end points of the T. That way I get pretty good coverage when I'm out on the tractor or excavator too. The "testbed" WAP lives in the TE closet under the house farthest from 11.
I'll get a WRT3200ACM loaded and configured up to my current working point. My email is on my profile page. Send me a shipping address and I'll get it off to you.
PS: I think I need to fix my profile... my age is off by about 40 years?!?!
-
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
WAP lives in the TE closet under the house farthest from 11.
If its farthest from where 11 is, then it should also be on 11 as well.. There is really no reason to ever use anything other than 1,6 and 11.
but since I don't see how you have any radio assigned to this new network your calling guesttest and on this port with .10 vlan ID - how would anyone connect to it?
-
Mmm, this sure looks like a bridge problem.
This shouldn't be that difficult, it something OpenWRT does all the time in comercial deployments. Been a while since I've tried it. But not so long I've never seen LuCI

When you associate the VAP with the LAN network clients are able to connect to it? So not a wireless issue?
Might be easier to spot the problem from the uci output at the command line. I'm betting there's a missing device on the bridge....
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Mmm, this sure looks like a bridge problem.
This shouldn't be that difficult, it something OpenWRT does all the time in comercial deployments. Been a while since I've tried it. But not so long I've never seen LuCI

When you associate the VAP with the LAN network clients are able to connect to it? So not a wireless issue?
Might be easier to spot the problem from the uci output at the command line. I'm betting there's a missing device on the bridge....
Steve
I agree Steve, it shouldn't. But it's been evading me and ideas seem to have dried up on 3 different OpenWRT specific forums... So either I'm a complete doofus newb, I'm trying to do something that can't be done or there is some nuance I and others haven't stumbled into.... yet. I fully take this as my screwup if someone finds the problem. The DSA is a good step forward but I admit I don't really, fully understand it. As far as bridging goes, one can only make changes on the br-lan device. But at this point, ANY change I make to "Bridge VLAN Filtering" causes a lockout condition... no big deal, you wait 90 seconds and revert when the option presents. Since I am not using the WAN, I assign it to the br-lan and use that for the back-haul connection. Currently I have the default SSIDs set with different names so I can readily test connections to them. But in production, they would be the same. I also have 802.11r on all SSIDs. I found if I had it on the default wireless everything worked fine. But once I built out the GuestTest, if I didn't enable 802.11r on the Guest wireless, the default wireless (on the same radio) would reject logons, not fail the password, just reject logon. DTIM is set to 3 as Apple products seem to like it better. I do not enable IPv6 anywhere in the home network. I've also removed the native (cut down) version of WPAD and installed the full version. dnsmasq, firewall and odhcpd are all disabled since these are run as dumb APs.
Network 6/1/2022 root@Testbed_OpenWrt:/etc/config# cat network config interface 'loopback' option device 'lo' option proto 'static' option ipaddr '127.0.0.1' option netmask '255.0.0.0' config globals 'globals' config device option name 'br-lan' option type 'bridge' option ipv6 '0' option bridge_empty '1' list ports 'lan1' list ports 'lan2' list ports 'lan3' list ports 'lan4' list ports 'wan' config interface 'lan' option device 'br-lan' option proto 'static' option netmask '255.255.255.0' option ip6assign '60' option gateway '192.168.1.1' list dns '192.168.1.1' option ipaddr '192.168.1.6' option delegate '0' config device option name 'wan' option ipv6 '0' config device option name 'wlan1-1' option ipv6 '0' config device option name 'wlan0' option ipv6 '0' config device option name 'wlan1' option ipv6 '0' config device option name 'eth0' option ipv6 '0' config device option type '8021q' option ifname 'br-lan' option vid '10' option name 'br-lan.10' option ipv6 '0' option macaddr '60:38:e0:BB:c6:68' config interface 'GuestTest' option proto 'static' option ipaddr '172.16.10.6' option netmask '255.255.255.192' option gateway '172.16.10.1' option device 'br-lan.10'Wireless 6/1/2022 config wifi-device 'radio0' option type 'mac80211' option path 'soc/soc:pcie/pci0000:00/0000:00:01.0/0000:01:00.0' option band '5g' option htmode 'VHT80' option country 'US' option cell_density '0' option channel '44' config wifi-iface 'default_radio0' option device 'radio0' option network 'lan' option mode 'ap' option dtim_period '3' option ieee80211r '1' option mobility_domain '123F' option ft_over_ds '0' option ft_psk_generate_local '1' option encryption 'psk2' option ssid 'OpenWRT5' option key 'xxxxxxxx' option max_inactivity '14400' config wifi-device 'radio1' option type 'mac80211' option path 'soc/soc:pcie/pci0000:00/0000:00:02.0/0000:02:00.0' option band '2g' option htmode 'HT20' option country 'US' option cell_density '0' option channel '11' config wifi-iface 'default_radio1' option device 'radio1' option network 'lan' option mode 'ap' option ieee80211r '1' option mobility_domain '123F' option ft_over_ds '0' option ft_psk_generate_local '1' option dtim_period '3' option encryption 'psk2' option ssid 'OpenWRT' option key 'xxxxxxxx' option max_inactivity '14400' option disassoc_low_ack '0' config wifi-device 'radio2' option type 'mac80211' option path 'platform/soc/soc:internal-regs/f10d8000.sdhci/mmc_host/mmc0/mmc0:0001/mmc0:0001:1' option channel '34' option band '5g' option htmode 'VHT80' option disabled '1' option country 'US' option cell_density '0' config wifi-iface 'default_radio2' option device 'radio2' option network 'lan' option mode 'ap' option ssid 'OpenWrt' option dtim_period '3' option encryption 'psk2+ccmp' option key 'xxxxxxxx' option ieee80211r '1' option mobility_domain '123f' option ft_over_ds '0' option ft_psk_generate_local '1' config wifi-iface 'wifinet3' option device 'radio1' option mode 'ap' option key 'xxxxxxxx' option ssid 'GuestTest' option dtim_period '3' option network 'GuestTest' option disassoc_low_ack '0' option ieee80211r '1' option ft_over_ds '0' option ft_psk_generate_local '1' option encryption 'psk2+ccmp' option mobility_domain '123f' option isolate '1' -
Ok, I need to test this but I think your problem here is that you only actually have one bridge device. You have created a VLAN device and named it br-lan.10 but it isn't a bridge device.
We can't see you're switch config there but can I assume WAN is eth0? Or that could be the internal port connected to the switch?
What I would do though is create a VLAN device on the uplink ethernet port. Then create a bridge device with that VLAN as a port. Then create an interface using that new bridge. And then add the VAP to that interface.
I have to wait until later to test it to avoid angry Facebook users.

Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Ok, I need to test this but I think your problem here is that you only actually have one bridge device. You have created a VLAN device and named it br-lan.10 but it isn't a bridge device.
We can't see you're switch config there but can I assume WAN is eth0? Or that could be the internal port connected to the switch?
What I would do though is create a VLAN device on the uplink ethernet port. Then create a bridge device with that VLAN as a port. Then create an interface using that new bridge. And then add the VAP to that interface.
I have to wait until later to test it to avoid angry Facebook users.

Steve
No problem, I can wait. Lets not PO the Facebook folks... The ones in Berkeley are liable to call 911... again... (not joking). This isn't an urgent thing, just something that needs to get done. I've been banging on it for a while now... I guess it's a route few follow. But I prefer to let pfSense do all the routing, rules, vlans, dhcp, etc... as it does it so much better. I just need it to flow to dumb APs
What you describe is how I tested it under ver 19.07,9? But that was still SWConfig. Under the new version (now 21.02.3) and going forward, they are DSA you just don't have that path... that I see. I could very well be wrong.
Rick
-
Forgot I had an AP300 already setup.

So, yeah, this works:
root@AP300:~# uci show network network.loopback=interface network.loopback.device='lo' network.loopback.proto='static' network.loopback.ipaddr='127.0.0.1' network.loopback.netmask='255.0.0.0' network.globals=globals network.globals.ula_prefix='fd21:90da:7fd9::/48' network.@device[0]=device network.@device[0].name='br-lan' network.@device[0].type='bridge' network.@device[0].ports='eth0' network.lan=interface network.lan.device='br-lan' network.lan.proto='dhcp' network.lan.delegate='0' network.@device[1]=device network.@device[1].type='8021q' network.@device[1].ifname='eth0' network.@device[1].vid='1001' network.@device[1].name='eth0.1001' network.@device[2]=device network.@device[2].type='bridge' network.@device[2].name='br-guest' network.@device[2].ports='eth0.1001' network.GUEST=interface network.GUEST.proto='dhcp' network.GUEST.device='br-guest' network.GUEST.delegate='0'Then:
root@AP300:~# uci show wireless.wifinet2 wireless.wifinet2=wifi-iface wireless.wifinet2.device='radio0' wireless.wifinet2.mode='ap' wireless.wifinet2.ssid='AP300-Guest' wireless.wifinet2.encryption='sae-mixed' wireless.wifinet2.key='1234512345' wireless.wifinet2.ieee80211w='1' wireless.wifinet2.network='GUEST'Clients connect to that and pull a lease from a dhcp server on VLAN1001.
That's a 21.02 snapshot:
root@AP300:~# uname -a Linux AP300 5.4.143 #0 Mon Sep 6 02:58:45 2021 mips GNU/LinuxThere is no switch on that device so DSA doesn't come into play. I'm not sure how those devices you have are laid out in hardware but if it has only one internal NIC you would need to configure the switch. However it looks like you already did that bit correctly since the vlan assigned as an interface is pulling a lease in the correct subnet.
Steve
-
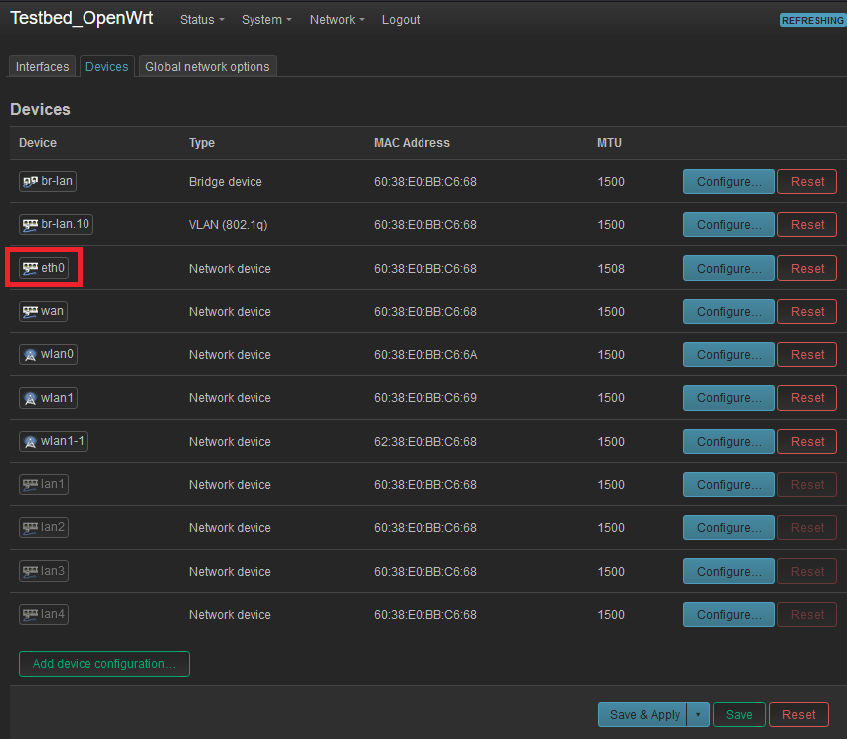
@stephenw10 The (network.@device[1].ifname='eth0') is throwing me. If you are in LuCI and select the dropdown for network, is there a "Switch" entry under Interfaces and Wireless? Or do you get Interfaces and Wireless with no Switch?
Sorry, botched that, had to edit.
-
No there's no switch in the AP300, it's an access point.
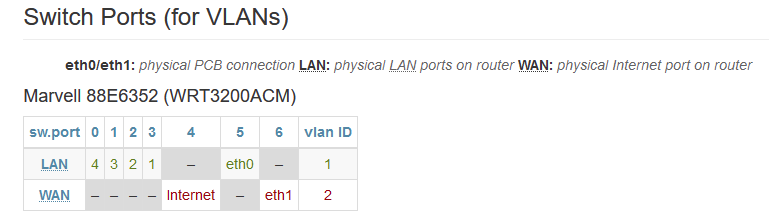
What's the hardware layout in the WRT3200ACM? Is this correct for your version?
https://openwrt.org/toh/linksys/wrt3200acm#switch_ports_for_vlansIf so and you are using the eth1 (WAN) port as the uplink you should be able to create the VLAN there and then add that to the new bridge device. I've used eth0 because that's the only port on the AP300.
You could create it on eth0 (the internal switch port) on your router but then you need to configure the switch to trunk that VLAN. Or use port based VLANs to just pass it.
It looks like OpenWRT will also allow you to create a VLAN on the bridge interface which is what you have done. For me that's less logical. YMMV!
There's probably several ways to do this. It's definitely possible.
Steve
-
Oh, wait think I read that switch diagram wrong. So the hardware actually has 5 physical ports? LAN 1-4 and WAN?
In fact both actual NICs (eth0 and eth1) are connected to the switch on internal ports 5 and 6?If you're using port VLAN mode (not 802.1q) then all VLAN traffic is passed. So create a VLAN interface on eth0. Create a bridge device with that in it. Create an interface with the new bridge. Assign the guest wifi to that.
There are in fact numerous ways you could do this depending what you want.
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
No there's no switch in the AP300, it's an access point.
Steve, I wasn't talking about the AP300 hardware, but in the OpenWRT LuCI, under the Network tab, does it show "Switch"?
Yes, the WRT3200ACM has 4 ports plus the WAN port.
-
No I don't see a switch menu in LuCI because there's no switch to configure.
What is your switch config currently?
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
What is your switch config currently?
I'm not really sure, there is no "Switch" function on a full DSA... that's where I think I was getting hung up on your suggestion. Ver 21 has moved to DSA... but only for some devices and the tell is whether you have the "Switch" function or not. But I digress. I follow your suggestion starting at "Create a bridge" device...". I'm not following you on "create a VLAN interface on eth0". Please elaborate.
Thanks,
Rick -
Hmm, well there must still be a way of configuring the switch IC. Look at the full
uci showoutput. What's in there that relates to the switch ports?But since you already created VLAN device and then when you added it as an interface it correctly pulled a dhcp lease from that VLAN implies however you have switch configured it must be passing the traffic.
However you created it on the existing bridge device which is not logical to me. Maybe it could work.I suggest you remove the VLAN device you created and instead create on eth0. Then create the bridge on that. Then the interface as the new bridge device.
Now when you are adding the VAP to the new interface you are adding it to a bridge and not to a VLAN. And underneath the OpenWRT config Linux still needs to bridge the traffic between those interfaces which is I think what was failing for you.Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
I suggest you remove the VLAN device you created and instead create on eth0. Then create the bridge on that. Then the interface as the new bridge device.
Now when you are adding the VAP to the new interface you are adding it to a bridge and not to a VLAN. And underneath the OpenWRT config Linux still needs to bridge the traffic between those interfaces which is I think what was failing for you.I know YOU know what you are talking about and trust you are right. I'm starting to feel like an idiot. I can't even get to the VAP point of this as I can't make what you have lined out work (again, starting with the interface as a DHCP client to verify connectivity with the pfSense supplied VLAN and DHCP server).
Am I reading/following your suggestion wrong?
Create the VLAN 10 device 802.1q with eth0 as the base device = eth0.10
Create a bridge for software VLAN eth0.10 and Switch port WAN = br.eth0.10
Create the Interface for my Guest function as a DHCP client and the device is br.eth0.10The Interface never gets an address. Lots of outbound packets, nothing inbound.
I'm sure I'm doing something wrong... just not sure what?
-
Ok, having read this and this, specifically this: https://openwrt.org/docs/guide-user/network/dsa/converting-to-dsa#wireless
I can absolutely see why you have it configured as you do and might expect it to work like that.
I also find myself beginning to hate the DSA with a fiery passion!

It seems like it hides half the ports presenting them to you as though they are interfaces and 'helpfully' adding all the VLANs and switch settings for you. Which I hate. But even more so when it doesn't do it correctly!
No idea how you know which eth ports the switch is using internally or how they are configured if you want change that....So, according to that doc, you should be able create the VLAN device on the bridge as you showed. And you should be able to add the wifi network to it directly. But you will have to enable bridge VLAN filtering in order to have the VAP added to the bridge with the correct tags by whatever dark magic powers DSA.
Or just pretend the switch doesn't exist since we know without VLAN filtering enabled it just passes all VLAN (port based vlan mode) and do what I outlined above which still works fine in 21.X.
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Ok, having read this and this, specifically this: https://openwrt.org/docs/guide-user/network/dsa/converting-to-dsa#wireless
I can absolutely see why you have it configured as you do and might expect it to work like that.
I also find myself beginning to hate the DSA with a fiery passion!

It seems like it hides half the ports presenting them to you as though they are interfaces and 'helpfully' adding all the VLANs and switch settings for you. Which I hate. But even more so when it doesn't do it correctly!
No idea how you know which eth ports the switch is using internally or how they are configured if you want change that....OK, I had to chuckle at "fiery passion"... but then the reality of "This is MY problem and I still haven't resolved it" set in.
The best clue I have as tho which eth port is in play comes from the Network/Devices.
It only shows "eth0". And, that does correlate with the information as you too found on the OpenWRT site regarding the WRT3200ACM.