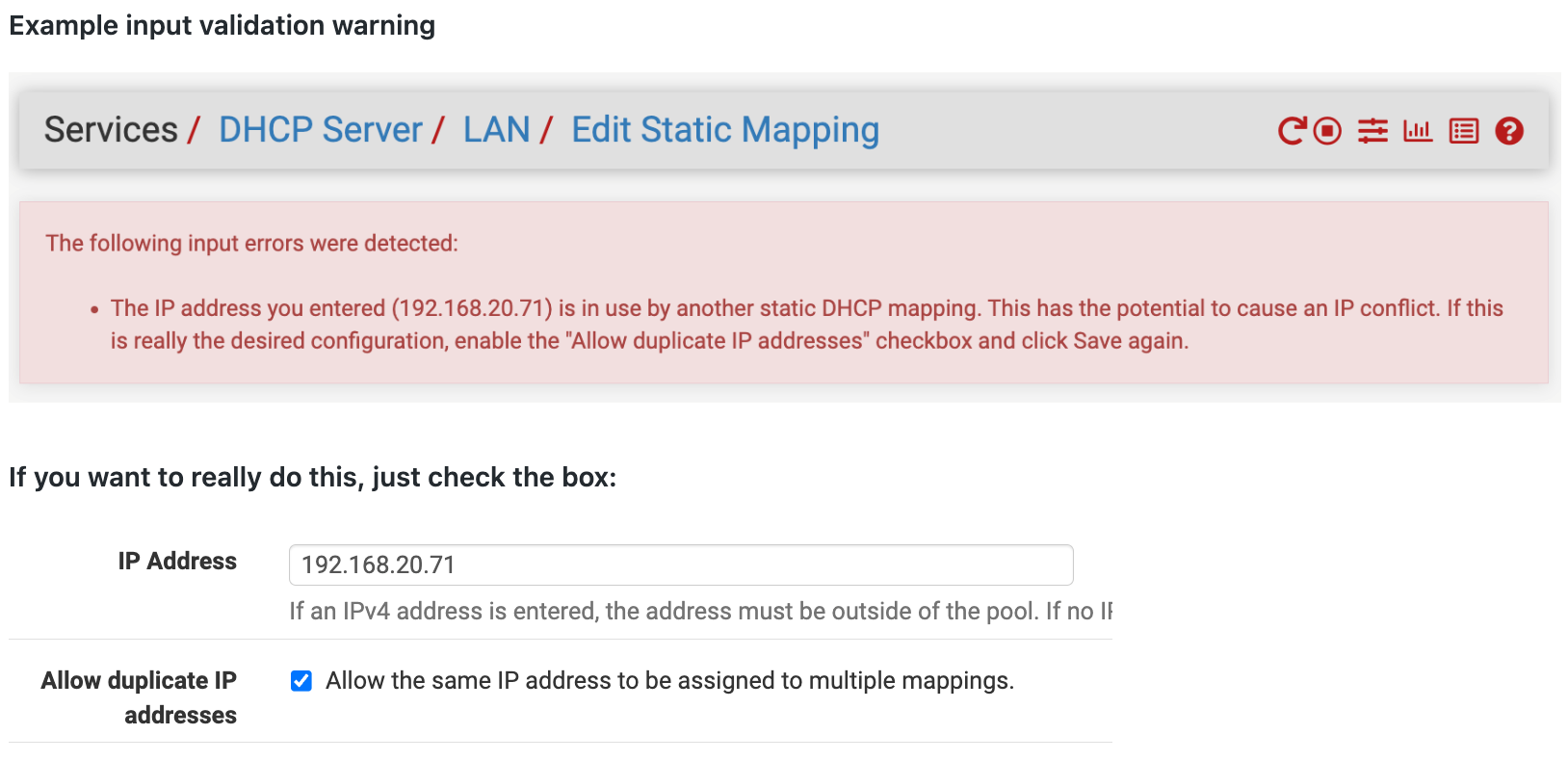
Why does the UI allow duplicate IP addresses (different MACs) in DHCP static mappings?
-
Yesterday I was troubleshooting an issue where a VM was constantly losing it's connectivity (Windows machine, the famous "
 ️yellow exclamation mark"). After a lot of head scratching I finally realized it was a simple IP address conflict on the pfSense.
️yellow exclamation mark"). After a lot of head scratching I finally realized it was a simple IP address conflict on the pfSense.I didn't realize that I'd mistakenly assigned the same static DHCP mappings to 2 VMs.
I searched the git history for when this change was made, and found it here:
Can I ask what the reasoning is to allow this? I understand the corner case of a device with multiple interfaces (e.g. wired & wireless) where only one is supposed to be connected at any given time, and the user wants the IP to remain constant. But that is solveable in other ways. I think this is a potential footgun.
It would be nice if at least a warning infoblock was printed after hitting Save.
-
-
@luckman212 POLA dictates that checkbox should default to checked. Does it?
-
@derelict Having it default to checked would negate the entire purpose of this change. POLA was not applied to the original commit, so I do not think it applies here either. I was more "astonished" when my DHCP was broken due to an address conflict.
-
@luckman212 As long as the behavior does not change for existing configurations.
-
@derelict Correct—Nothing would change at all until the user actually goes in to edit an entry and either creates a new duplicate (or tries to save an existing one). At that point, the warning would be shown. All they have to do is check the box and re-save.