pfSense with CloudFlare (and WireGuard - soon) - setup AD DS
-
- Do you have your AD DNS server configured to resolve?
- Do you have your AD DNS server's IP address being given out by the AD DHCP server as the DNS for clients to utilize?
- When you say your Internet quits working, can you be more specific. Do you mean browsing or pinging an external host by domain name from a device on your LAN does not work with DNS turned off in pfSense, but it works when DNS in pfSense is enabled? If so, the you do not have things set properly as your either clients seem to be using pfSense for DNS or you do not have the AD DNS server configured to resolve (with roots properly imported).
I promise you this is not difficult at all. You are not getting all of the configuration correct.
-
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
- Do you have your AD DNS server configured to resolve?
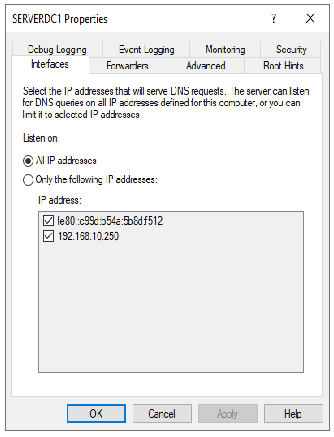
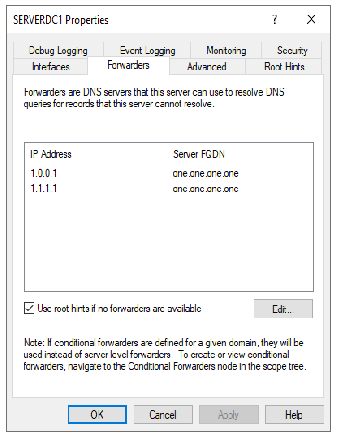
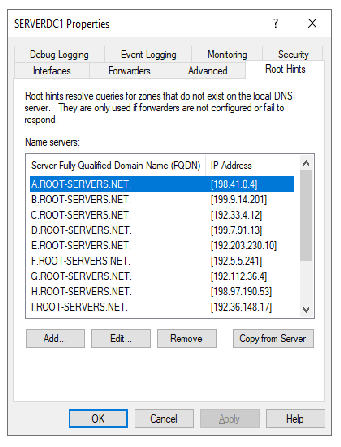
I believe I am. From the AD DNS - not having any issues getting to the Internet. From the DNS tool - all the root hints resolve and I have the following settings (see images)
- Do you have your AD DNS server's IP address being given out by the AD DHCP server as the DNS for clients to utilize?
I believe this is working -- this one of my home computers (not joined to the Domain -- yet) - but it looks like it is getting the right IPs ( gateway - 192.168.10.254 = pfSense // 192.168.10.250 = AD DNS )
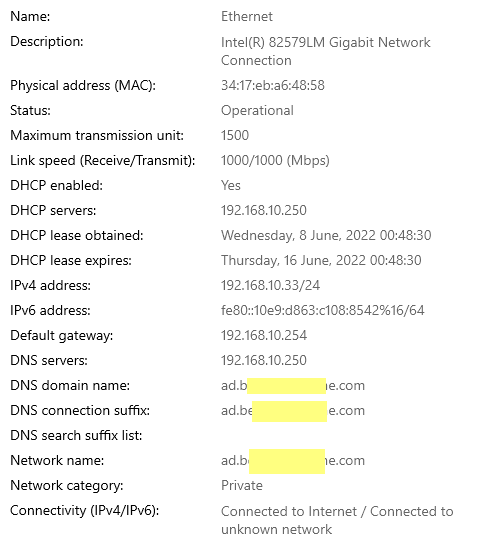
- When you say your Internet quits working, can you be more specific. Do you mean browsing or pinging an external host by domain name from a device on your LAN does not work with DNS turned off in pfSense, but it works when DNS in pfSense is enabled? If so, the you do not have things set properly as your either clients seem to be using pfSense for DNS or you do not have the AD DNS server configured to resolve (with roots properly imported).
When I turned off the DNS Resolver feature in pfSense - then from the machine shown in #2 above - I tried to go to a new website...and I got :page cannot be displayed: error. I also tried to ping google.com and got No Response. Soon as I turned on the DNS resolver on in pfSense and unchecked everything except the DNSSEC (what appears to be the defaults) - everything started working again.
I promise you this is not difficult at all. You are not getting all of the configuration correct.
Yeah - I did not think it was hard either...as I am no idiot...but again, when NETGEAR ORBI was doing all the Routing and DNS and DHCP (never had these problems) - it is just with the pfSense.

If there is anything you want an image of - let me know.
-
-
For IPv6
Unless you are actually using IPv6 and have a public IPv6 address through your ISP, you will need to go in and delete all the IPv6 root servers on the Windows AD box. You do that on the same screen where you checked the resolving. Just select and remove the IPv6 addresses (again, if you don't have a public IPv6 address for pfSense. -
For DNS:
Do you have any rules in place on the pfSense firewall that would be interfering here? Do you have DNS redirects in place?And it really makes zero sense that as soon as you enable the Resolver on pfSense that things start working. That really screams a misconfiguration someplace.
My first thought is your client is looking to pfSense for DNS, but from the screen shot you posted that does NOT seem to be the case. That leaves maybe a firewall rule or DNS redirect on the firewall that is interfering with your AD server's DNS role. Let's see your LAN interface firewall rules and any you might have on the FLOATING RULES tab. If DNS works when you enable the Resolver on pfSense, then that means your client is getting sent there for DNS for some reason (but it should not be).
While I don't think it's the problem here, you really do not need the forwarder IP addresses if you are going to use the root hints and let AD DNS resolve.
-
I have done that in the DNS tool - root hints. There are no IPv6 addresses there (except the Link-Local one)...if you disable ipv6 protocol completely - you get other errors (apparently AD DS needs ipv6 for something).
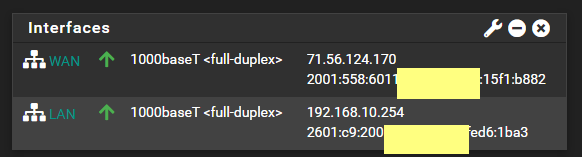
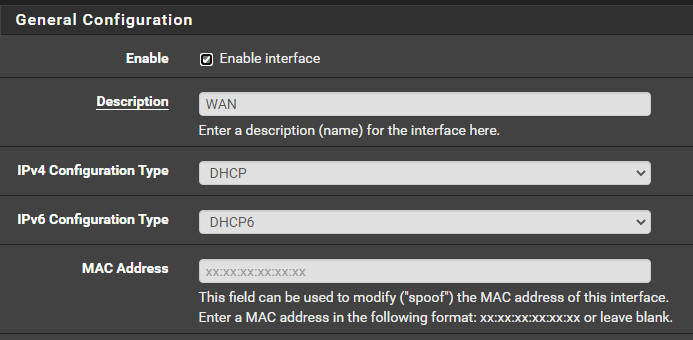
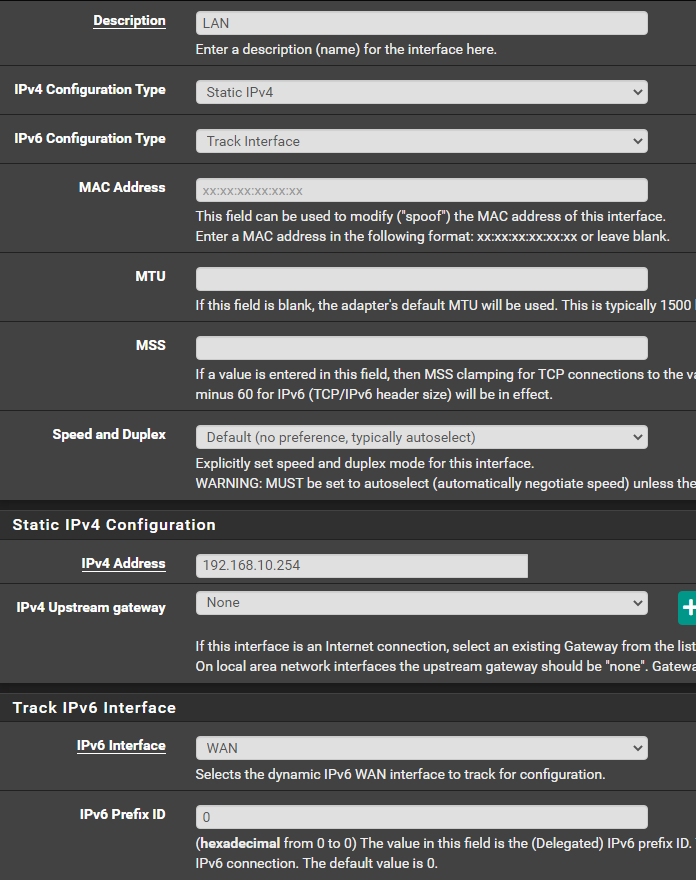
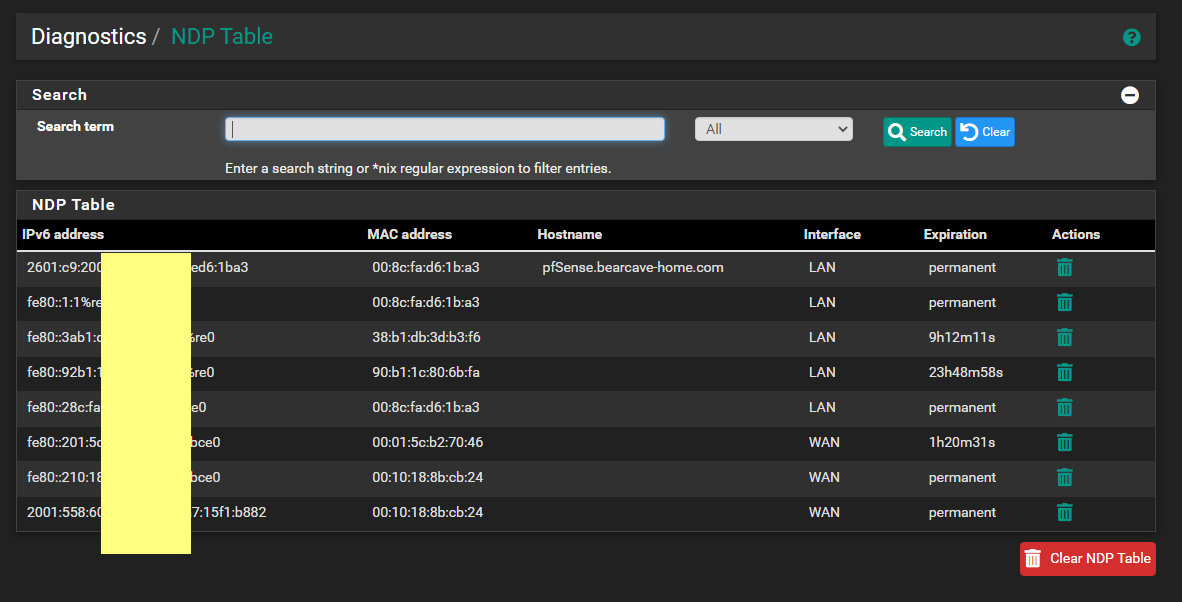
-
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
For DNS:
Do you have any rules in place on the pfSense firewall that would be interfering here? Do you have DNS redirects in place?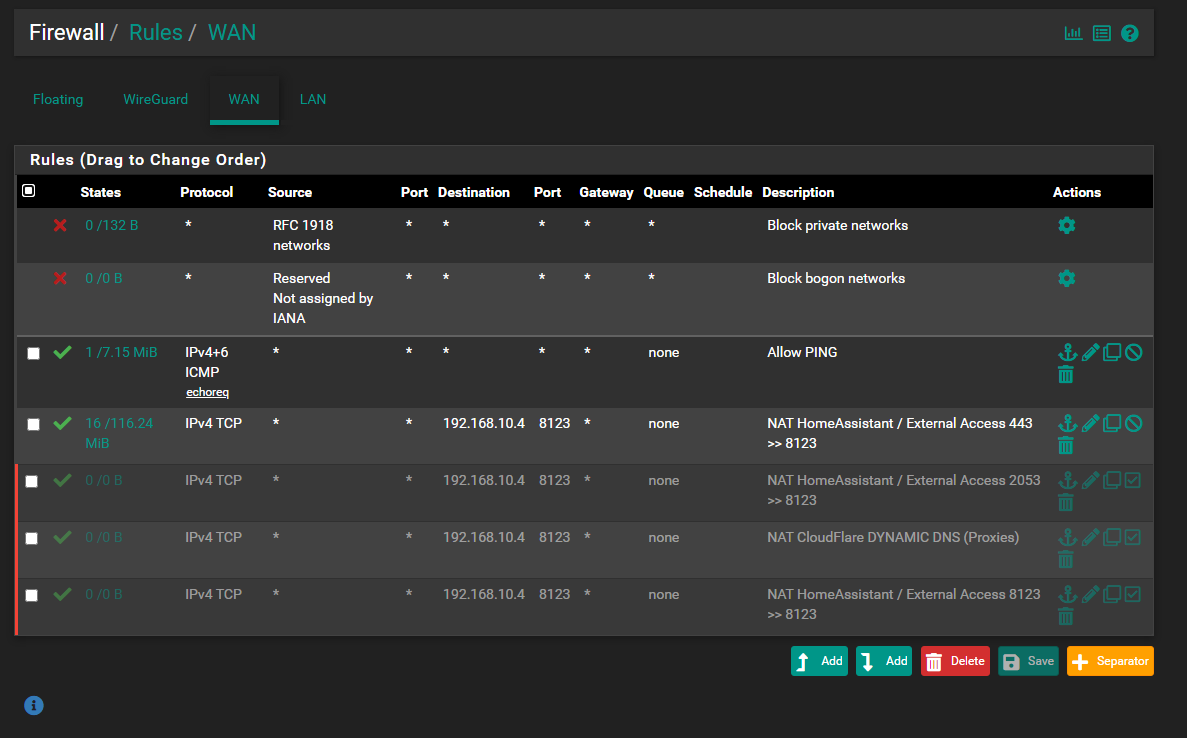
And it really makes zero sense that as soon as you enable the Resolver on pfSense that things start working. That really screams a misconfiguration someplace.
My first thought is your client is looking to pfSense for DNS, but from the screen shot you posted that does NOT seem to be the case. That leaves maybe a firewall rule or DNS redirect on the firewall that is interfering with your AD server's DNS role. Let's see your LAN interface firewall rules and any you might have on the FLOATING RULES tab. If DNS works when you enable the Resolver on pfSense, then that means your client is getting sent there for DNS for some reason (but it should not be).
While I don't think it's the problem here, you really do not need the forwarder IP addresses if you are going to use the root hints and let AD DNS resolve.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
For DNS:
Do you have any rules in place on the pfSense firewall that would be interfering here? Do you have DNS redirects in place?
And it really makes zero sense that as soon as you enable the Resolver on pfSense that things start working. That really screams a misconfiguration someplace.
My first thought is your client is looking to pfSense for DNS, but from the screen shot you posted that does NOT seem to be the case. That leaves maybe a firewall rule or DNS redirect on the firewall that is interfering with your AD server's DNS role. Let's see your LAN interface firewall rules and any you might have on the FLOATING RULES tab. If DNS works when you enable the Resolver on pfSense, then that means your client is getting sent there for DNS for some reason (but it should not be).
While I don't think it's the problem here, you really do not need the forwarder IP addresses if you are going to use the root hints and let AD DNS resolve.
Not WAN rules. Show LAN rules and the FLOATING rules (if you have any of those).
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
I have done that in the DNS tool - root hints. There are no IPv6 addresses there (except the Link-Local one)...if you disable ipv6 protocol completely - you get other errors (apparently AD DS needs ipv6 for something).




I don't think you understood what I was saying in my IPv6 post.
If you have do NOT have a public IPv6 address on your WAN (and thus a delegation for your LAN), then you would remove the root hints IPv6 addresses. But since you DO have a public IPv6 (since you are showing one), then do NOT remove the IPv6 addresses for the root hints. And make sure that your AD domain controllers have proper IPv6 addresses assigned from the IPv6 subnet used on your LAN.
-
Also, you will need to enter the appropriate domain overrides in the DNS Resolver on pfSense so that
unboundwill know to go ask your AD DNS server for the local hostnames of local devices listed in things like the ARP table.But having (or not having) the domain overrides configured has no impact on external DNS lookups working. You have still seem to have something misconfigured for that not to be working from a client machine on your LAN.
-
IPv6 on your LAN
You did not state initially state you wanted to use IPv6. That is possibly going to be problematic if you do not have a static IPv6 subnet to work with (meaning NOT one configured by tracking your WAN IPv6 delegation).Did you configure a DHCPv6 setup in the Active Directory DHCP server? If so, realize that unless you have a true static IPv6 prefix, you will have to change the DHCPv6 scope every time your WAN prefix changes.
If IPv6 is available, Windows will default to using it first. So that means the IPv6 configuration must be fully functional.
You can, of course, let pfSense be the DHCPv6 server (or use something like SLAAC). But if you do that, local clients will not have their IPv6 address registered in the Active Directory DNS.
-
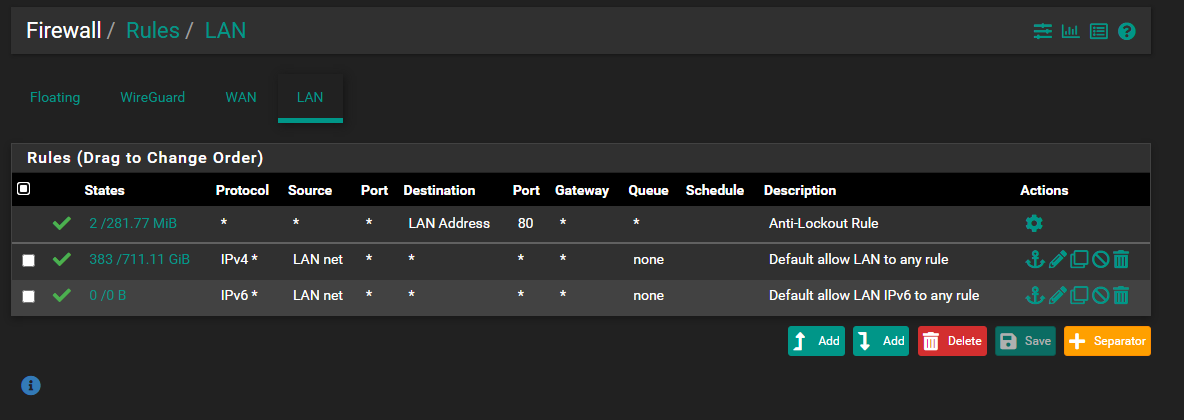
WireGuard is there - but it has not been setup yet or configured. Just the PACKAGE installed.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:


WireGuard is there - but it has not been setup yet or configured. Just the PACKAGE installed.

Okay, I don't see any DNS redirect rules.
Let's do this step-by-step.
- Turn off the DNS Resolver on pfSense (disable it for now).
- Open a command prompt session on a Windows client on your LAN (use either a laptop or desktop PC).
- Execute this command:
nslookup cnn.comPost what comes back from that command. What should happen is your AD DNS server should go out and resolve that domain name to several IPv4 and IPv6 addresses. Here is what that looks like on my desktop Windows PC.
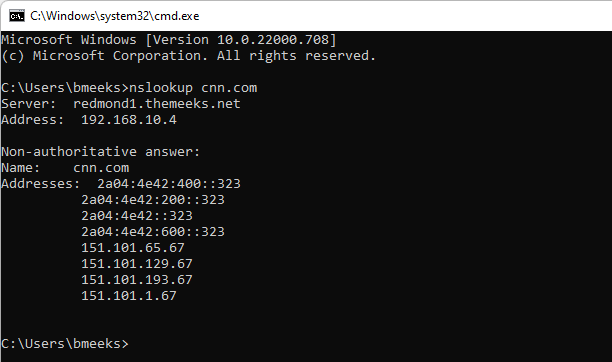
You can see in the above screen shot that the DNS lookup request was handled by one of my domain controllers (redmond1 is the machine name) at IP address 192.168.10.4. It resolved the domain "cnn.com" to that list of IP addresses.
- If the above steps don't work, then let's first figure out why and get that working.
-
-
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
I wanted to say thank you again for your assist with this.
IPv6 on your LAN
You did not state initially state you wanted to use IPv6. That is possibly going to be problematic if you do not have a static IPv6 subnet to work with (meaning NOT one configured by tracking your WAN IPv6 delegation).Before I decided to move to the AD DS to handle DNS and DHCP, pfSense was my DNS and DHCP/DHCPv6 -- using those same settings I showed earlier...WAN (DHCP / DHCPv6 from my ISP) and LAN (Track Interface = WAN). I would get an IPv6 address for both of them - and I watched them for weeks - they never changed....and my devices were indeed getting v6 addresses.
Did you configure a DHCPv6 setup in the Active Directory DHCP server? If so, realize that unless you have a true static IPv6 prefix, you will have to change the DHCPv6 scope every time your WAN prefix changes.
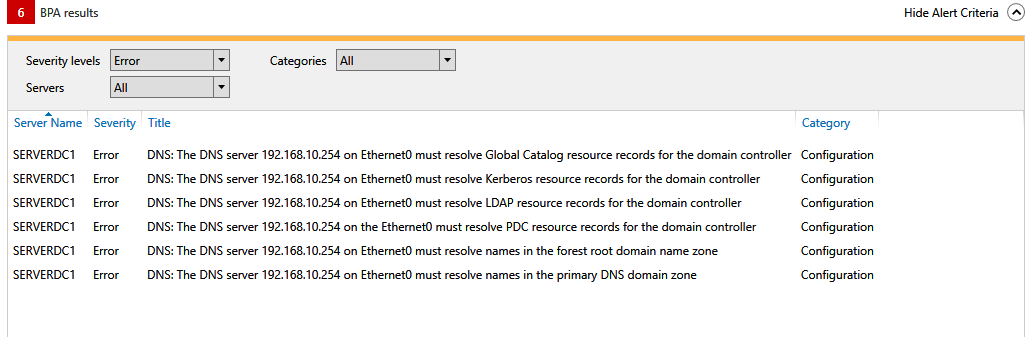
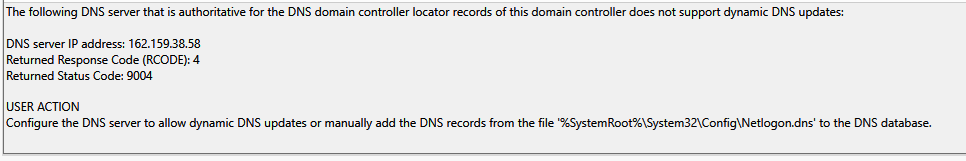
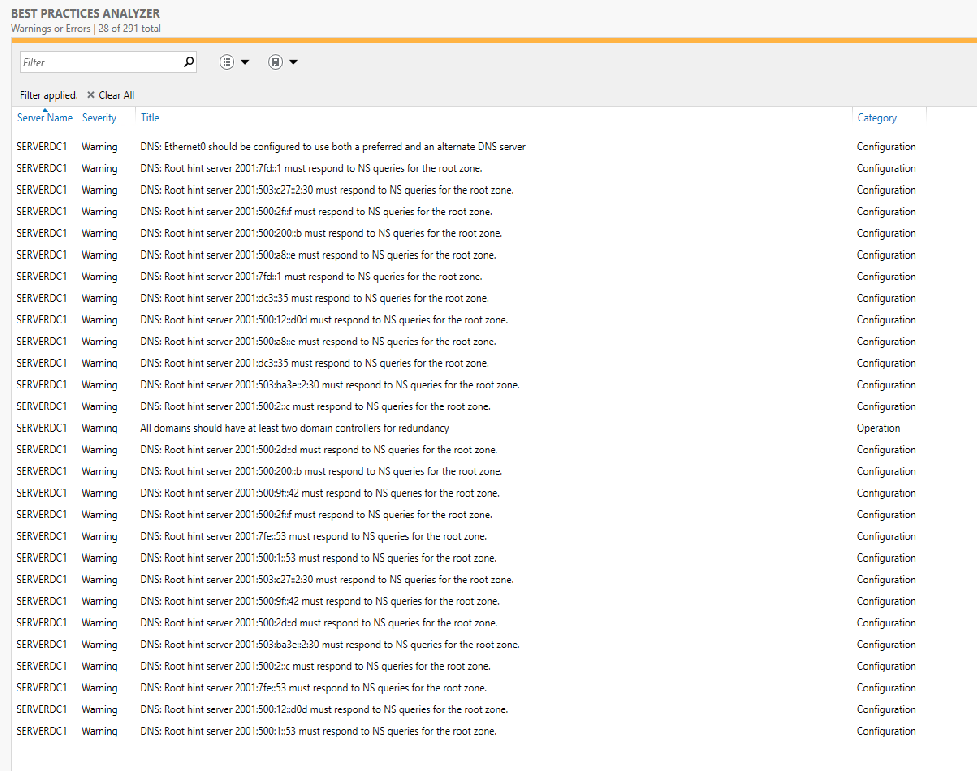
No - not yet...that is what I meant when I mentioned that I wanted to set that up. I just find it strange as there are no v6 Root Hints configured - but the Best Practices Analyzer in Windows shows them.
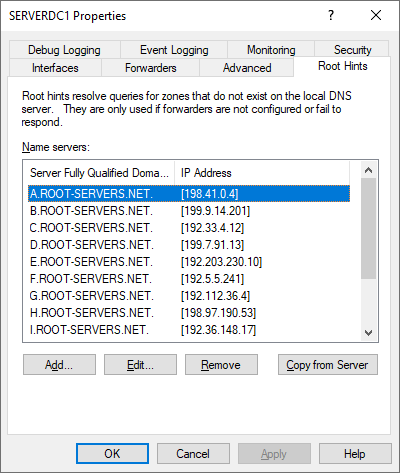
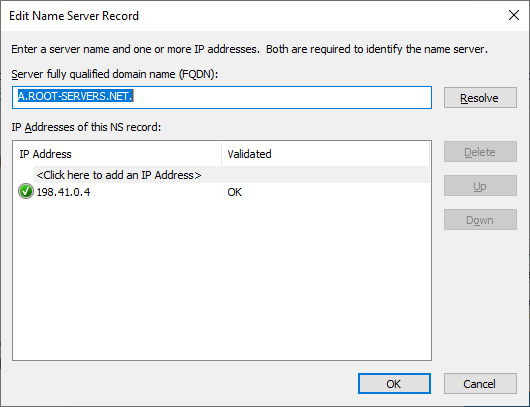
If IPv6 is available, Windows will default to using it first. So that means the IPv6 configuration must be fully functional.
You can, of course, let pfSense be the DHCPv6 server (or use something like SLAAC). But if you do that, local clients will not have their IPv6 address registered in the Active Directory DNS.
-
I have also noticed that only a few of my devices when they get a DHCP address - - are registering in the DNS. Before I made this change -- none of them were doing this.
So when I ping a device by name - I get no response (no resolution). Same if I ping the IP.
Does not make any sense why DNS records are not getting created for my network in DNS.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
I have also noticed that only a few of my devices when they get a DHCP address - - are registering in the DNS. Before I made this change -- none of them were doing this.
So when I ping a device by name - I get no response (no resolution). Same if I ping the IP.

Does not make any sense why DNS records are not getting created for my network in DNS.
Checking that option just tells the DHCP server to always update DNS. This is sometimes required for dumb devices like IoT stuff. But in order for this to actually work, the DHCP client on the device requesting an IP address has to have some kind of hostname to start with that it can give to the DHCP server when asking for an IP. Otherwise there is nothing for the DHCP server to put into DNS. It can't pull the hostname out of the ether. The requesting device must offer it first.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
I wanted to say thank you again for your assist with this.
IPv6 on your LAN
You did not state initially state you wanted to use IPv6. That is possibly going to be problematic if you do not have a static IPv6 subnet to work with (meaning NOT one configured by tracking your WAN IPv6 delegation).Before I decided to move to the AD DS to handle DNS and DHCP, pfSense was my DNS and DHCP/DHCPv6 -- using those same settings I showed earlier...WAN (DHCP / DHCPv6 from my ISP) and LAN (Track Interface = WAN). I would get an IPv6 address for both of them - and I watched them for weeks - they never changed....and my devices were indeed getting v6 addresses.
Did you configure a DHCPv6 setup in the Active Directory DHCP server? If so, realize that unless you have a true static IPv6 prefix, you will have to change the DHCPv6 scope every time your WAN prefix changes.
No - not yet...that is what I meant when I mentioned that I wanted to set that up. I just find it strange as there are no v6 Root Hints configured - but the Best Practices Analyzer in Windows shows them.


If IPv6 is available, Windows will default to using it first. So that means the IPv6 configuration must be fully functional.
You can, of course, let pfSense be the DHCPv6 server (or use something like SLAAC). But if you do that, local clients will not have their IPv6 address registered in the Active Directory DNS.
You will likely want to update the list of root servers by clicking the Copy from Server button and putting the IP address of one of the root servers in the box within the dialog that pops up. Use 191.41.0.4. That will pull in a fresh list and you should then see several IPv6 servers.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
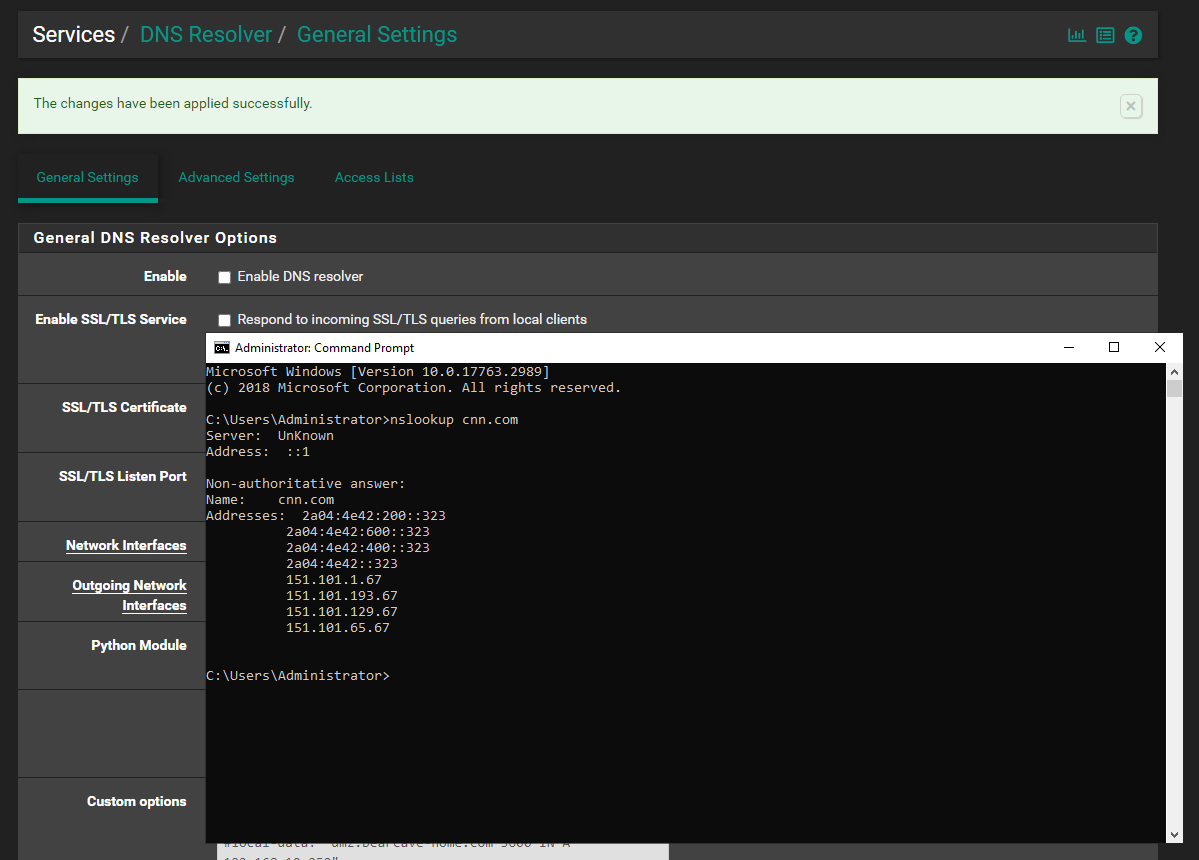
In your screenshot above, notice that your AD DNS server does not have a hostname shown. It says "Unknown".
Did you create a proper static hostname entry for it in the forward lookup zone in DNS? Also, do you have a proper reverse pointer lookup zone defined and is there a record there pointing to the hostname for the static IP of the AD DNS server?
Refer back to my example and you will see that
nslookupshould be able to resolve a valid hostname for your AD DNS server. Mine was "redmond1.themeeks.net", for example. -
That was the first thing that I did when I setup the DNS.
See entry for 192.168.10.250
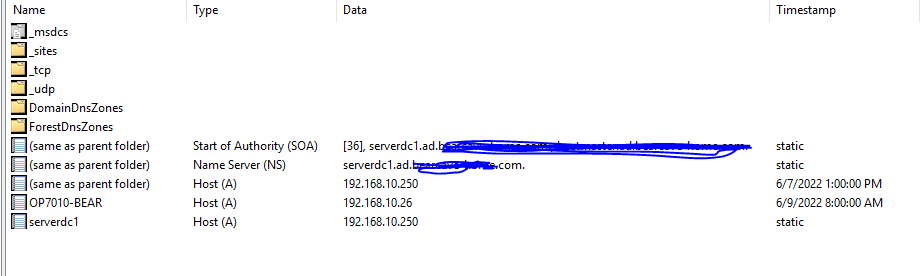
the PTR record is also there for it
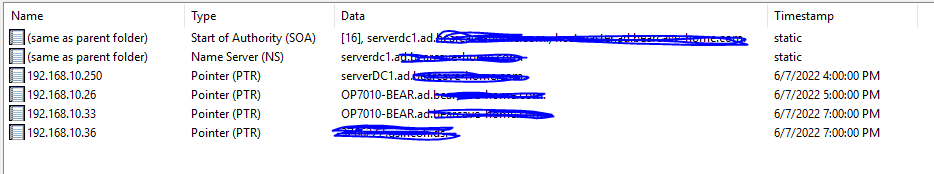
Notice that only the OP7010-BEAR created a DNS record when DHCP gave it an address...the 2x entries for it in the REV LOOKUP are from a reboot where I had the WiFi turned on...it got .26....wired is .33. The last entry in the reverse lookup is my work laptop which is on another VPN accessed Domain.
I also just noticed that the NETWORK is no longer showing as a DOMAIN - but as PRIVATE:
---this is apparently a known "BUG" in Windows 2019.