Ipsec Configuration not Working!
-
@gabacho4 now both sides are running on 2.6.
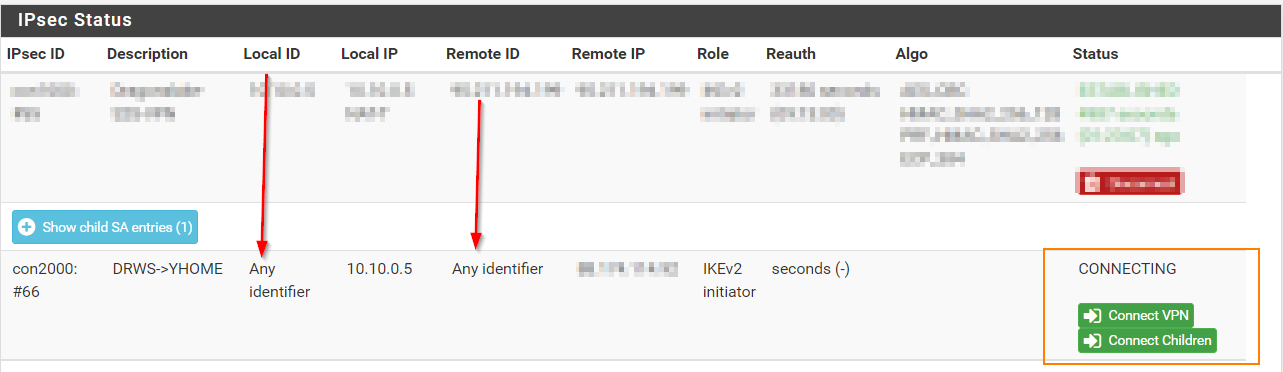
But still not working!
For your information when I check the port with the Public IPs here https://www.yougetsignal.com/tools/open-ports/:
SiteB is open
But SiteA is closed! do you think this is what makes the problem? and since it's a simple internetBox I do not have a firewall to ope the ports at all.
-
@ibnkamala sorry just got home from work. So it appears in the last screenshot that both the P1s are connected. That would seem better than it was before. Can you show me the logs so I can see what the P2 is doing? I’m not going to lie to you, your setup is insanely more complicated than I’d ever use. Why would you have pfsense behind another firewall and other hardware? And what is an internet box? A modem? A router? An ONT?
-
@ibnkamala Ok so I did some Googling. Are you located in Switzerland? I find a internetBox that the ISP in Switzerland offers. If not Switzerland perhaps you are in another European country where the internetBox is used. If you have the device I have found, you can most certainly do port forwarding and/or set up a DMZ. I can't find anything about Ipsec passthrough but it's either there or a DMZ/port forwarding would get the job done.
Some advice - except for art, less is not more. I'm a little tweaked to find out you're using virtualized instances of pfsense that are behind multiple devices etc. Should have asked more about your setup at the beginning but for the next time, cough up all the details from the get go please.
-
SiteA Logs:
Last 50 IPsec Log Entries. (Maximum 50)
Time Process PID Message
Jun 13 14:56:36 charon 35179 09[CFG] mark_out = 0/0
Jun 13 14:56:36 charon 35179 09[CFG] set_mark_in = 0/0
Jun 13 14:56:36 charon 35179 09[CFG] set_mark_out = 0/0
Jun 13 14:56:36 charon 35179 09[CFG] inactivity = 0
Jun 13 14:56:36 charon 35179 09[CFG] proposals = ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
Jun 13 14:56:36 charon 35179 09[CFG] local_ts = 192.168.1.0/24|/0
Jun 13 14:56:36 charon 35179 09[CFG] remote_ts = 10.10.0.0/24|/0
Jun 13 14:56:36 charon 35179 09[CFG] hw_offload = no
Jun 13 14:56:36 charon 35179 09[CFG] sha256_96 = 0
Jun 13 14:56:36 charon 35179 09[CFG] copy_df = 1
Jun 13 14:56:36 charon 35179 09[CFG] copy_ecn = 1
Jun 13 14:56:36 charon 35179 09[CFG] copy_dscp = out
Jun 13 14:56:36 charon 35179 09[CFG] version = 2
Jun 13 14:56:36 charon 35179 09[CFG] local_addrs = 192.168.1.27
Jun 13 14:56:36 charon 35179 09[CFG] remote_addrs = SiteB
Jun 13 14:56:36 charon 35179 09[CFG] local_port = 500
Jun 13 14:56:36 charon 35179 09[CFG] remote_port = 500
Jun 13 14:56:36 charon 35179 09[CFG] send_certreq = 1
Jun 13 14:56:36 charon 35179 09[CFG] send_cert = CERT_SEND_IF_ASKED
Jun 13 14:56:36 charon 35179 09[CFG] ppk_id = (null)
Jun 13 14:56:36 charon 35179 09[CFG] ppk_required = 0
Jun 13 14:56:36 charon 35179 09[CFG] mobike = 0
Jun 13 14:56:36 charon 35179 09[CFG] aggressive = 0
Jun 13 14:56:36 charon 35179 09[CFG] dscp = 0x00
Jun 13 14:56:36 charon 35179 09[CFG] encap = 0
Jun 13 14:56:36 charon 35179 09[CFG] dpd_delay = 10
Jun 13 14:56:36 charon 35179 09[CFG] dpd_timeout = 0
Jun 13 14:56:36 charon 35179 09[CFG] fragmentation = 2
Jun 13 14:56:36 charon 35179 09[CFG] childless = 0
Jun 13 14:56:36 charon 35179 09[CFG] unique = UNIQUE_REPLACE
Jun 13 14:56:36 charon 35179 09[CFG] keyingtries = 1
Jun 13 14:56:36 charon 35179 09[CFG] reauth_time = 0
Jun 13 14:56:36 charon 35179 09[CFG] rekey_time = 34920
Jun 13 14:56:36 charon 35179 09[CFG] over_time = 3880
Jun 13 14:56:36 charon 35179 09[CFG] rand_time = 3880
Jun 13 14:56:36 charon 35179 09[CFG] proposals = IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jun 13 14:56:36 charon 35179 09[CFG] if_id_in = 0
Jun 13 14:56:36 charon 35179 09[CFG] if_id_out = 0
Jun 13 14:56:36 charon 35179 09[CFG] local:
Jun 13 14:56:36 charon 35179 09[CFG] class = pre-shared key
Jun 13 14:56:36 charon 35179 09[CFG] id = SiteA
Jun 13 14:56:36 charon 35179 09[CFG] remote:
Jun 13 14:56:36 charon 35179 09[CFG] class = pre-shared key
Jun 13 14:56:36 charon 35179 09[CFG] id = SiteB
Jun 13 14:56:36 charon 35179 09[CFG] updated vici connection: con1
Jun 13 14:56:36 charon 35179 07[CFG] vici client 472 disconnected
Jun 13 14:56:42 charon 35179 13[CFG] vici client 473 connected
Jun 13 14:56:42 charon 35179 16[CFG] vici client 473 registered for: list-sa
Jun 13 14:56:42 charon 35179 12[CFG] vici client 473 requests: list-sas
Jun 13 14:56:42 charon 35179 13[CFG] vici client 473 disconnected -
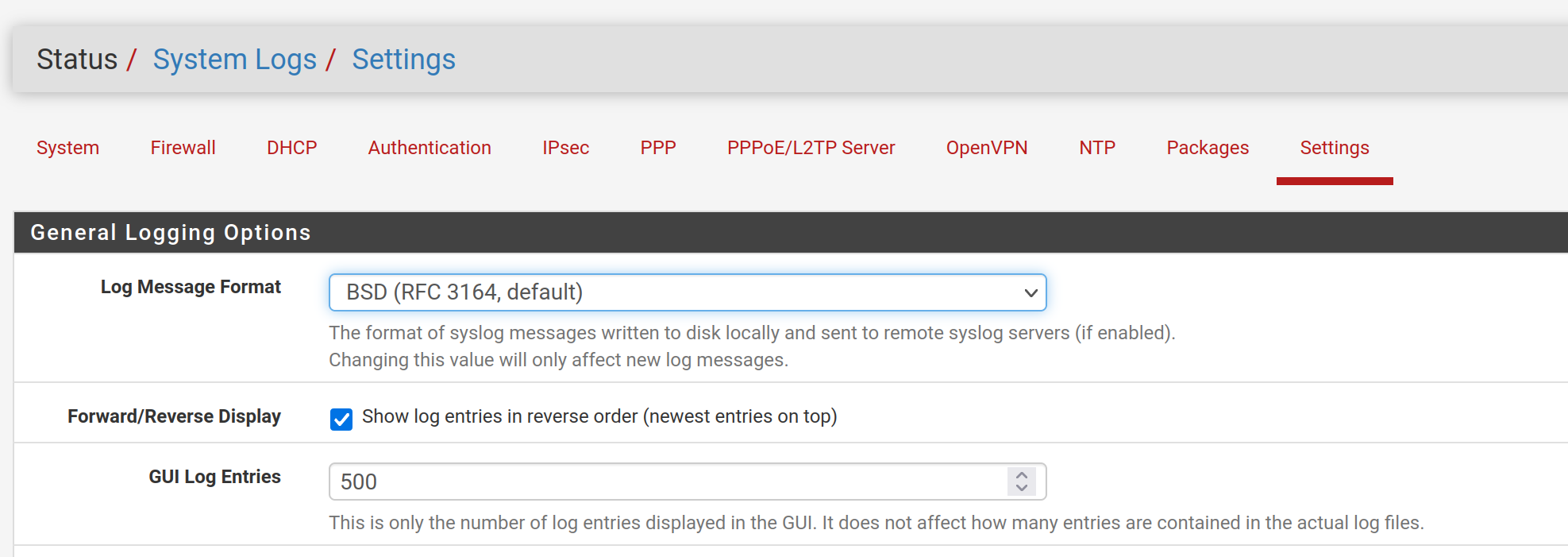
@ibnkamala can you go to Status - System Logs - Settings and change the GUI log entries from 50 to 500?
-
@gabacho4 I can't post my logs because
I am in France, once side is orange livebox pro fibre/SiteB and the other end is freebox revolution fibre/SiteA
-
@ibnkamala attach them as a file then.
-
@ibnkamala said in Ipsec Configuration not Working!:
@gabacho4 I can't post my logs because

I am in France, once side is orange bank pro firber /SiteB and the other end is freebox revolution fibre/SiteA
OK then note what I said about being able to port forward or set up a DMZ. Your device should have documentation that shows how to do this.
-
@gabacho4 please find attached logs in PDF and Word document with 500 log records.
Saying thank you is not enough for your great help, however I have to say it
-
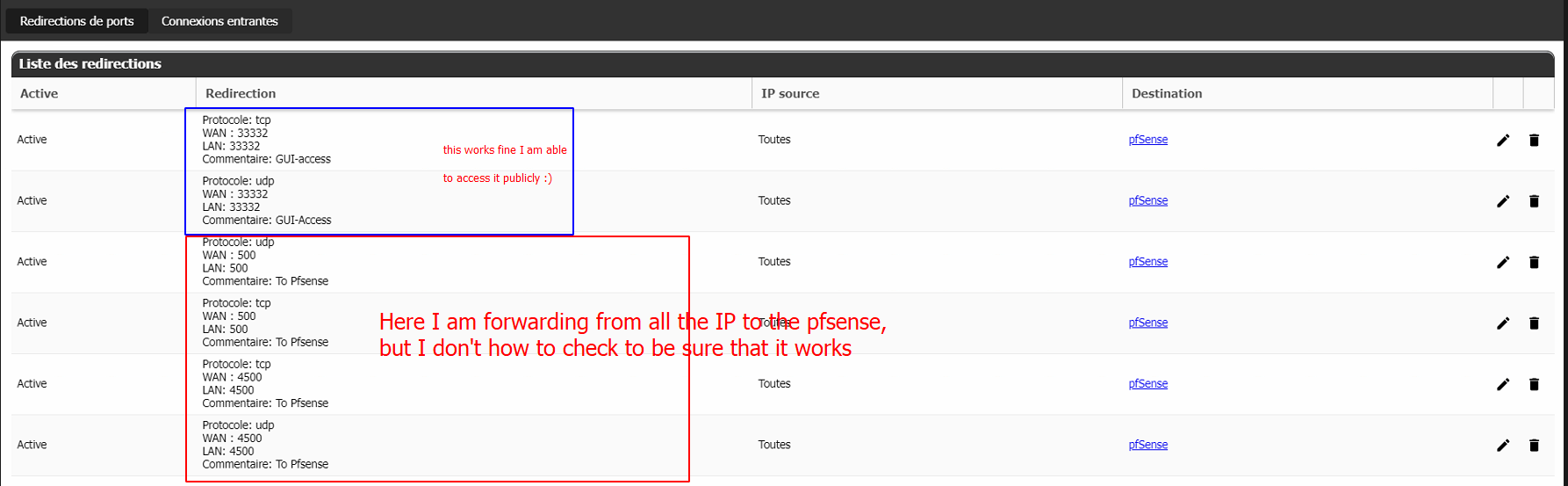
@gabacho4 I have already port forward in place, https works fine I am even able to access publicly the pfsense gui, and since I have not change the pfsense ipsec default ports which I think it uses 500 and 4500 so I have crteated below reules.
-
@gabacho4 in my real configuration I will be using https://shop.netgate.com/products/6100-max-pfsense instead of SiteA but still will be behind NAT and won't be here in France it will be in Barcelona
Concerning the SiteB / there won't be any changes. which will happen in 3 days. on Th 16th of June. but for behind a proper firewall and router.
But I wanted to do the manipulation to see how it works, but sadly I am not there yet :)
-
@ibnkamala I don't see that the port forwarding allows the esp protocol through. This is why most internet devices support IPsec passthrough. Can you put the Pfsense box on a DMZ and then try. Looking at your logs, it looks like SiteB tries to connect to SiteA but never gets a response. Would seem to indicate to me that things are not getting through.
-
@gabacho4 will do that.
-
Now that both boxes are on 2.6, may I suggest switching to WireGuard since it is more NAT friendly, and requires just a single UDP port to be forwarded. You can try this without disturbing the IPsec config you have done so far (just disable the P1 to test)
https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-s2s.html
-
@luckman212 what do you mean exactly I have to disable phase1 in both sites, then how can we test ? I will forward simple to the Pfsense.
-
@ibnkamala I am saying: forwarding the ports and protocols needed to make IPSEC work in a double-NAT scenario (such as you have) is not an easy task. It seems you might be a little over your head with it.
So, I suggested changing strategy and trying Wireguard, which is a completely different protocol, to establish the site-to-site tunnel. I posted a link to the guide so you could try to set it up.
If you do give that a try, just stick to the default port (udp/51820) and forward that port from "Simple Internet Box" to your inside SiteA pfSense, and also forward from SiteB Sonicwall to pfSense. It's just another possible solution.
-
@gabacho4 tenia este problema y exactamente esta era la solucion, mis 2 firewalls estan detras del NAT, me funciono perfectamente para la conexion IPSEC. Solo me sucedio de Pfsense a Pfsense.
aclaro, uso la version 2.6, tal vez el compañero deba actualizar la su version. -
@gary-lopez quieres decir que usando el KeyID era la clave para tu éxito? Lo siento pero después de cuatro meses y muchos mensajes entre mi y el amigo, no estoy seguro cual te ayudo. De todas maneras te felicito.
-
@gabacho4 Asi es, ya estoy un poco familiarizado, no soy experto pero ese problema lo tenia desde hace meses pero no le dedique mucho tiempo ya que en produccion tengo de Pfsense a un Fortigate y me dejo levantar la VPN sin la necesidad de poner la KEY ID, use como identificador My IP Address que es la que te da por Default. Otra ventaja que tengo es que mi ISP o modem lo tengo en DMZ y el servico de Dynamic DNS en el pfsense.
-
@gary-lopez es posible que haya otra solución pero no he experimentado hasta ahora. Una de mis instancias de pfsense esta detras de NAT y la otra no. Ya que pude hacer la conexión de esta manera no quise gastar mas tiempo y energía. Si te dan las ganas un día de estos, deberías investigar VTI IPSec ya que ese tipo te da una interfaz y gateway que puedes usar para PBR etc.