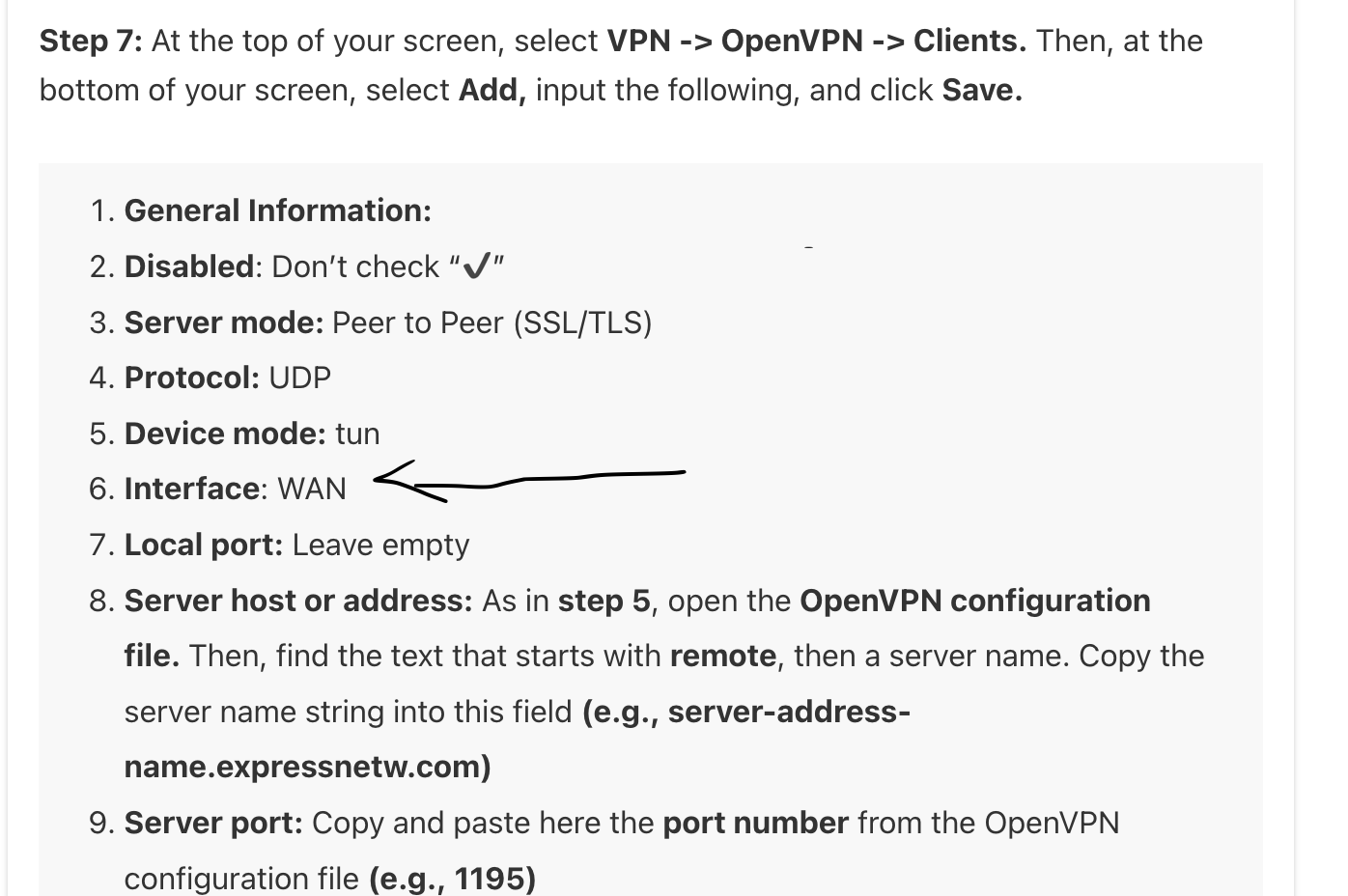
netgate 5100
-
@akuma1x I truly appreciate the help! I have followed your guide to setup the rules on the worklan.
However, I'm a little confused as to what I should add on the LAN rules side.
Action: Block
Interface: LAN
Address Family: IPv4
Protocol: any
Source: LAN net
Destination: WorkLAN net
Description: give it a good name here
SAVEIs the above rule correct? What would be the second rule for the LAN side?
-
@blackbirdwilliams Also, I have openvpn setup to allow me to remote into the lan. Will this cause issues with setting up express VPN on the worklan side of things? BTW the Block rule I have added on the lan side, stops the ping from going through from the lan to worklan! Seems like it works after all! This is great.
Now I just need a little more guidance as to how to get express on the worklan. I have backup my settings at this point, just in case everything crashes and burns when I try to tweak the guide to fit my setup. Will keep you posted. Any tips would be greatly appreciated. Thank you for the help thus far!
-
Would I change number 6. Interface to worklan? I don't want the express VPN to be on the LAN side. Not too sure how to customize this.
-
@blackbirdwilliams Here's what you setup on the LAN network:
Make a new rule on the LAN network, move it to the top, right under your anti-lockout rule.
Action: Reject or Block - either one will work
Interface: LAN
Address Family: IPv4
Protocol: any
Source: LAN net
Destination: WORKLAN net
Description: give it a good name here
SAVEAnd you're done with that one. Make another rule, move it all the way down to the bottom after you are finished making it.
Action: Pass
Interface: LAN
Address Family: IPv4
Protocol: any
Source: LAN net
Destination: any
Description: give it a good name here
SAVEThat second LAN rule should technically already be there, created automatically when pfsense is first setup. If you look at your LAN rules right away, after a fresh install, it says "Default allow LAN to any rule". It's rule number 2 in this screenshot:
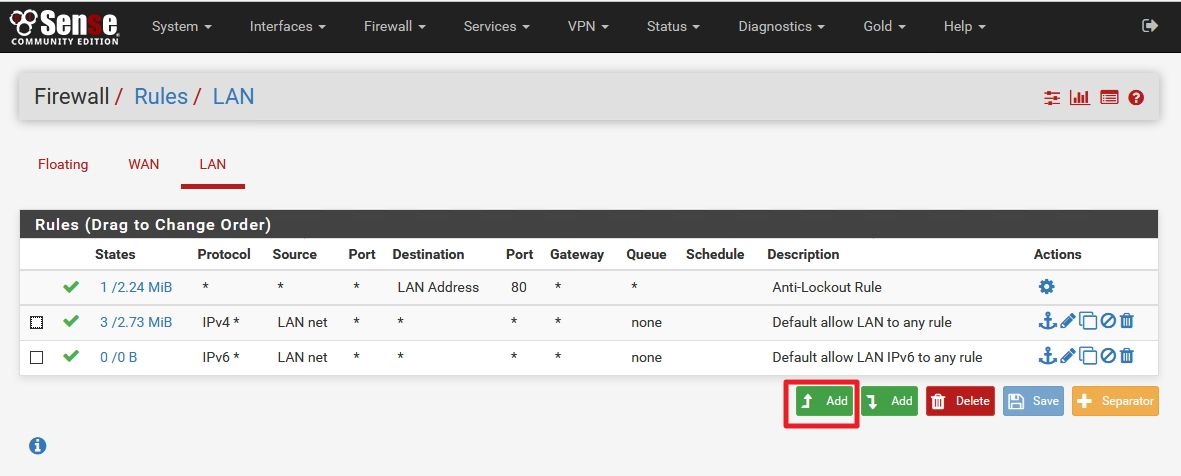
So, long story short, sorry... If you simply create the first rule above (the LAN block rule), and move it into position #2 on your LAN network, you'll be all good to go.
Again, put up some screenshots, if you're comfortable with that, so we can check your rule settings.
-
@blackbirdwilliams said in netgate 5100:
Would I change number 6. Interface to worklan?
No. The OpenVPN client has to connect out of the WAN.
As long as you have set 'do not pull routes' as shown in step 40 there nothing should change.
Once you have that up you need to:
Assign the OpenVPN client as an interface. This will give you a gateway to route to.
Make sure the firewall default route is still via the WAN dhcp gateway. In System > Routing > Gateways, make sure the default gateway is set the WAN_DHCP not automatic.
Add policy routing to the pass rule on WORKLAN to make that traffic go via the VPN.See: https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/assign.html
Steve
-
@akuma1x I think I'm good to do with the rules. Here is a screenshot
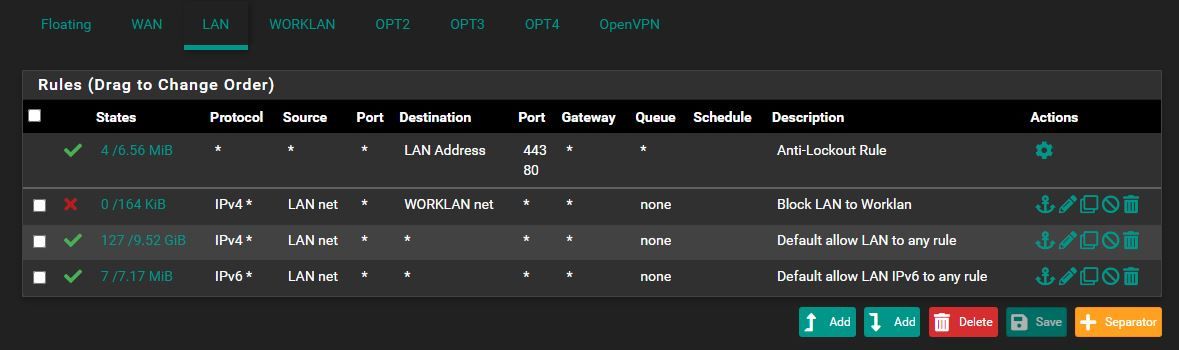 of the LAN side and worklan.
of the LAN side and worklan. 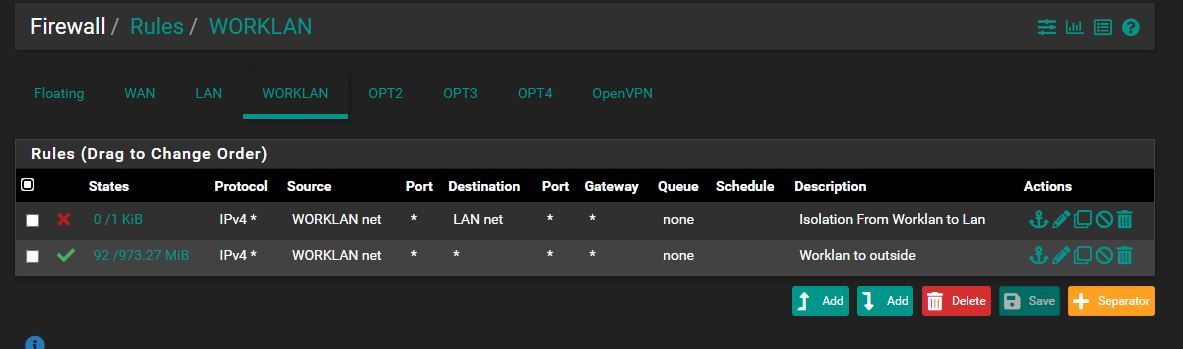
-
@stephenw10 I have an OpenVPN rule on my wan side to allow me to remote in. Will this interfere with anything on the express vpn side?
If I follow the guide for express VPN to the T, wont that enable the VPN for all of the LAN? I want to keep the LAN coming out of my regular ISP. However, have the worklan only use the VPN.
Could I get a little more explicit guidance?
I truly appreciate your help!!!
-
@blackbirdwilliams Yep, that's it, looks good!
So, the ExpressVPN connection you're working on will go in your WORKLAN rule, in the "to outside" rule. When your VPN settings are all done and working, you simply add the VPN connection as your gateway in that rule, like @stephenw10 commented just above.
-
@blackbirdwilliams said in netgate 5100:
Could I get a little more explicit guidance?
Here's a good video that walks you thru using a VPN service as a pfsense client to send a network (or a single machine, or an alias of machines) out a VPN connection.
https://www.youtube.com/watch?v=sGif5rXE3Ps
-
@akuma1x Great Video! I'm going to give it a shot now. Will keep you posted. Thank you for your time!
-
@akuma1x I cant get the express vpn to work. Status Down....
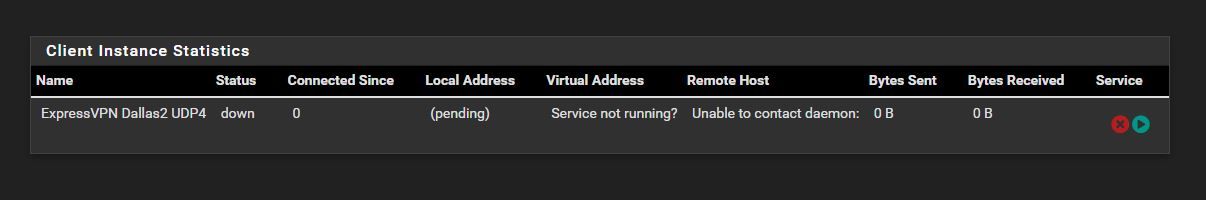
-
One thing to be aware of here is that the OpenVPN rules tab applies to all OpenVPN connections. If you have an OpenVPN server running already you probably have an allow all tule there so that connected clients can access resources behind the firewall. But when you get the ExpressVPN connection working that rule will also apply to it and you don't want to allow random connections from ExpressVPN! So make sure that rule it limited to your own subnet as source. Or alternatively assign your server as an interface the same way as the client and then you can apply the rules to those interfaces individually.
Steve