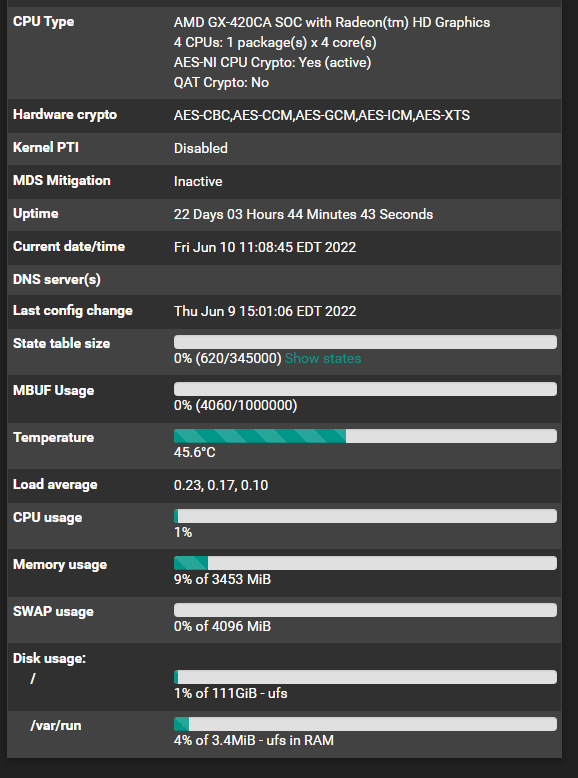
pfSense 2.5.2 - Web Console super slow
-
I used that link - found in another search for COMCAST, IPV6 and PFSENSE. I appear to be getting IPv6 addresses to my devices. Some of them (like ANDROID and AMAZON devices - require a reboot to get these). Will do that later.
I have it enabled now as follows:
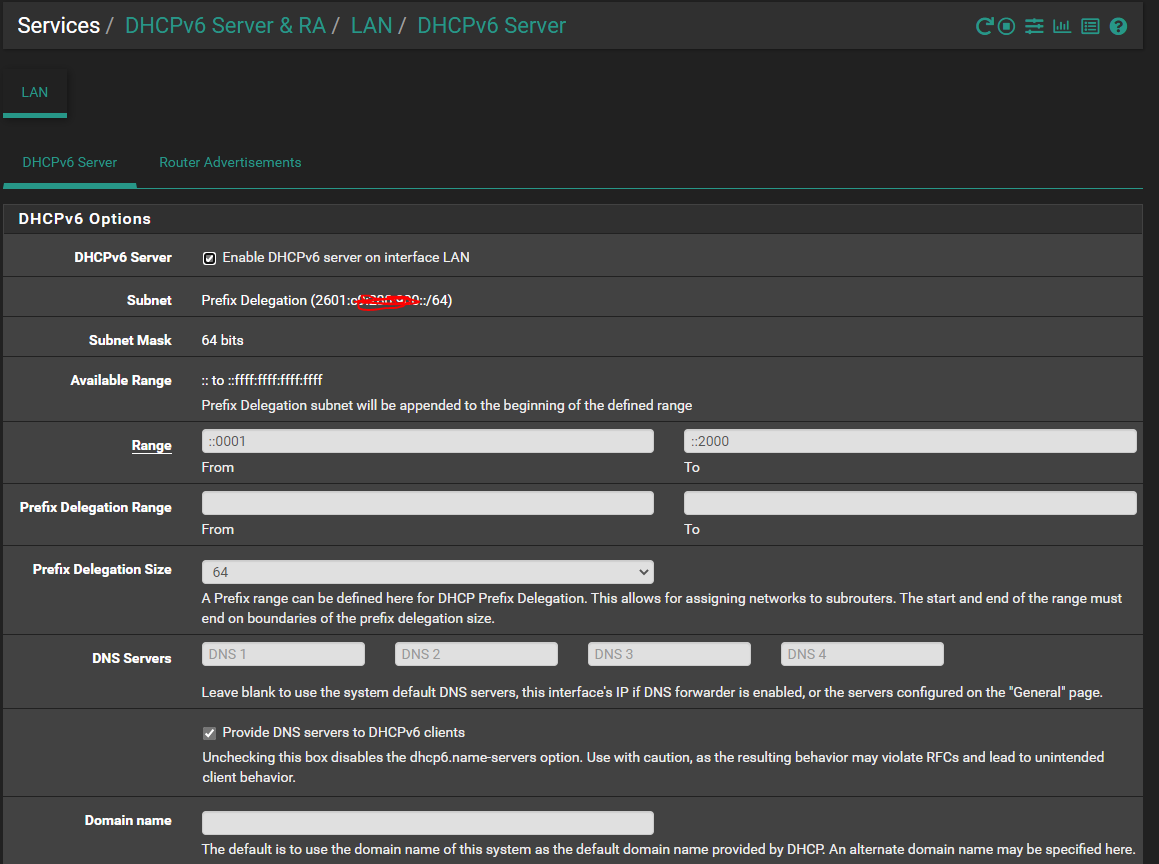
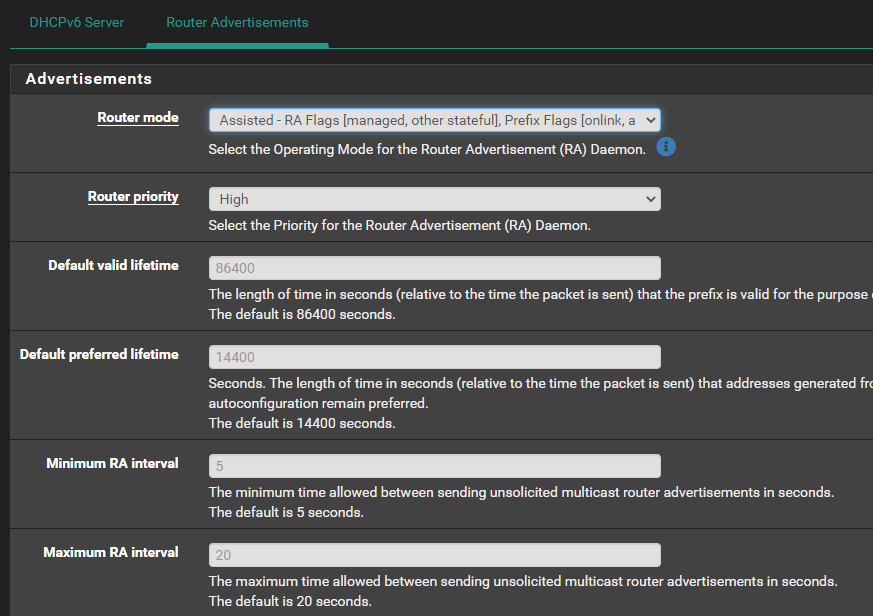
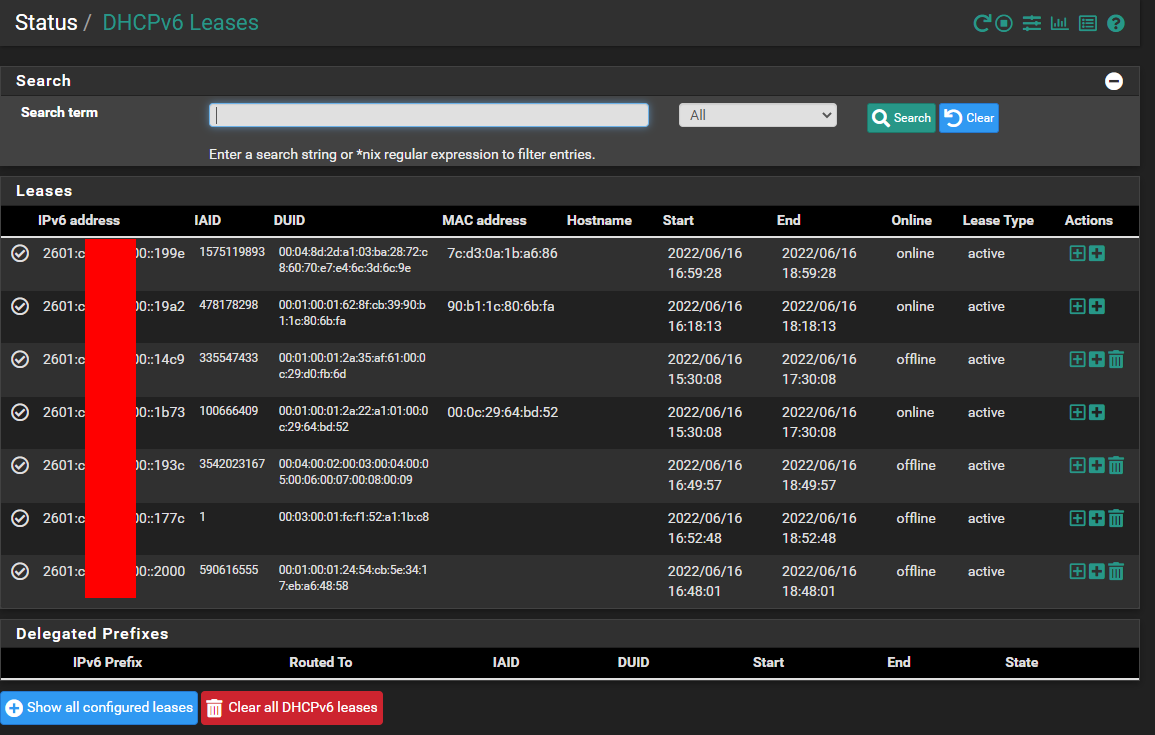
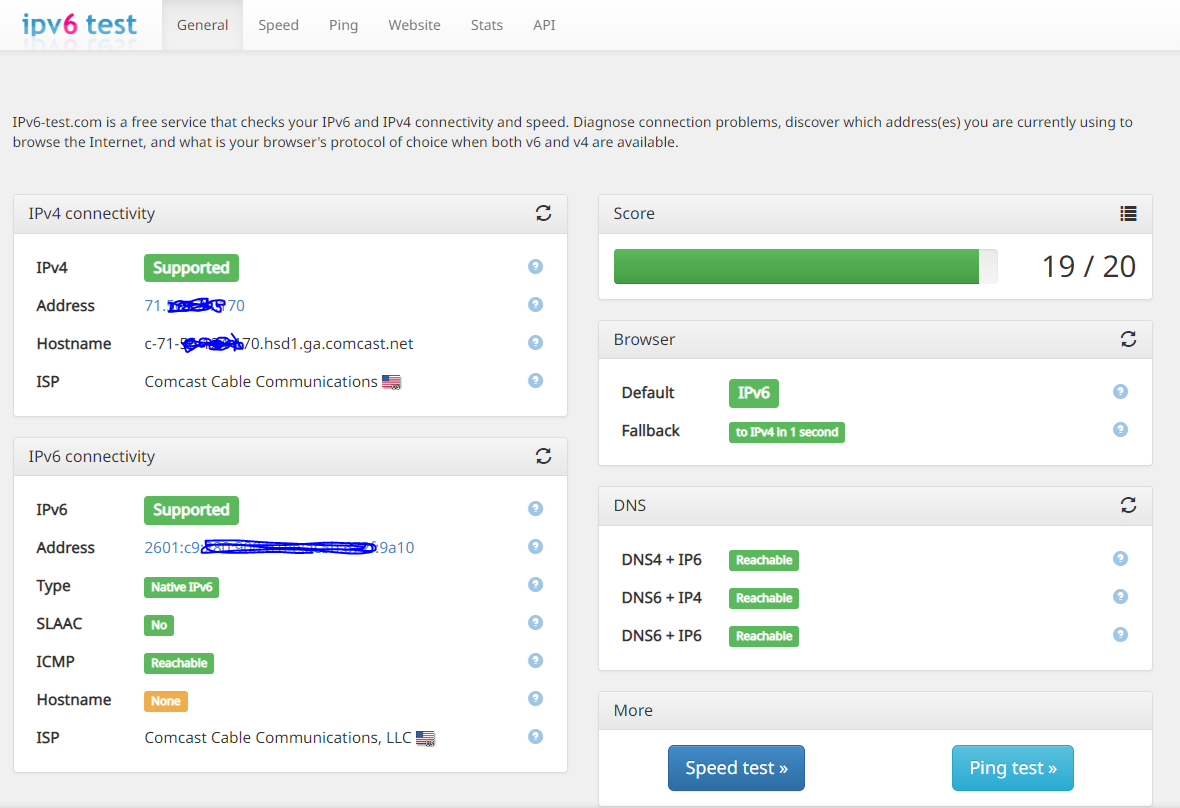
Also it appears that my IPv6 is working - based on this site --
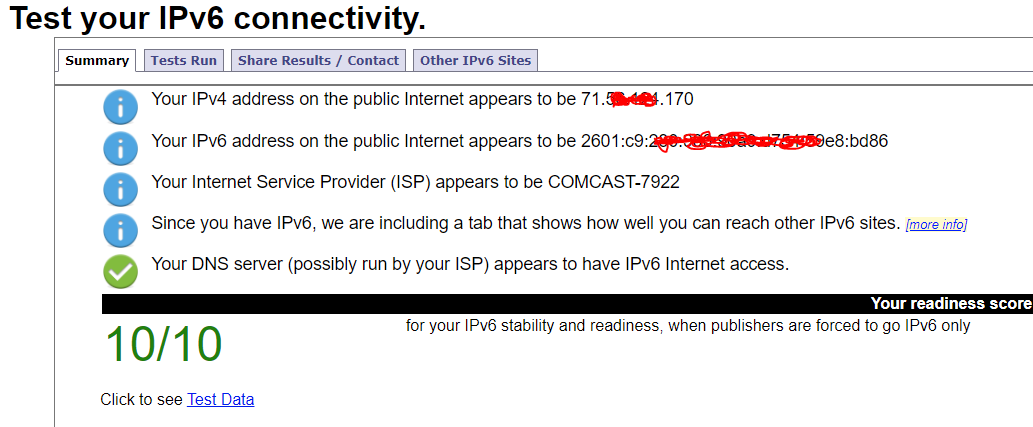
-
I just gotta get passed this one:
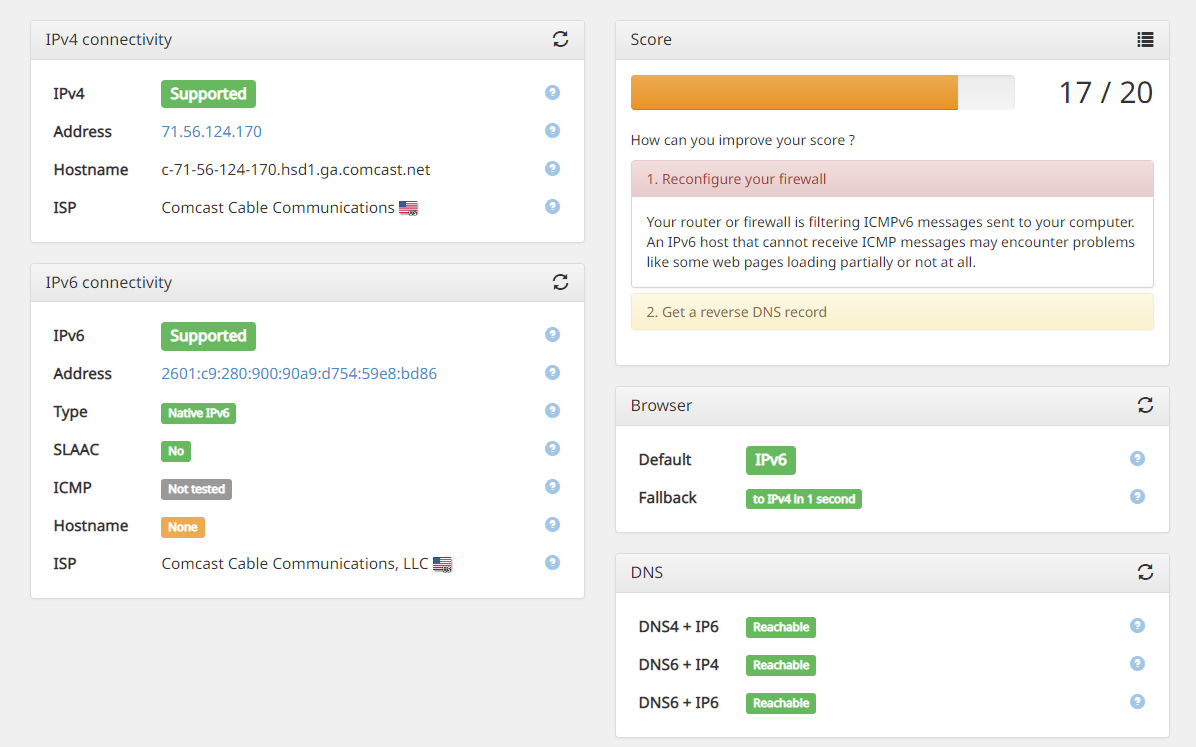
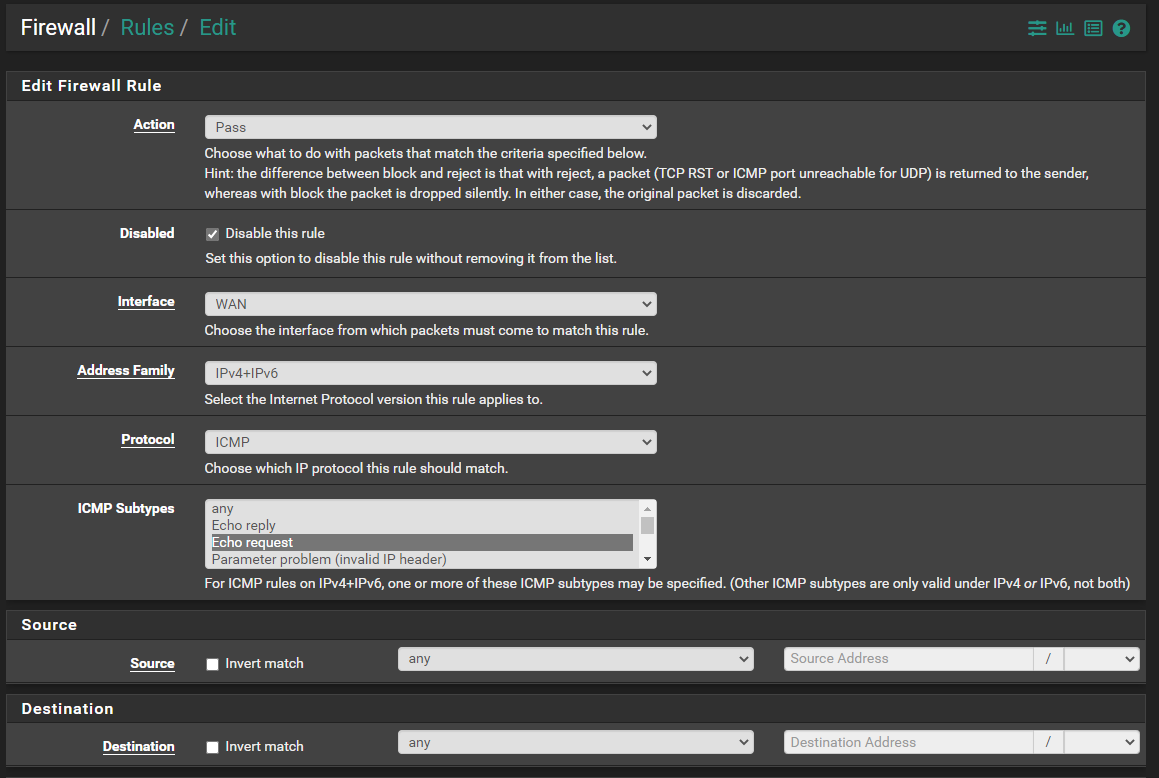
As I have these rules set:
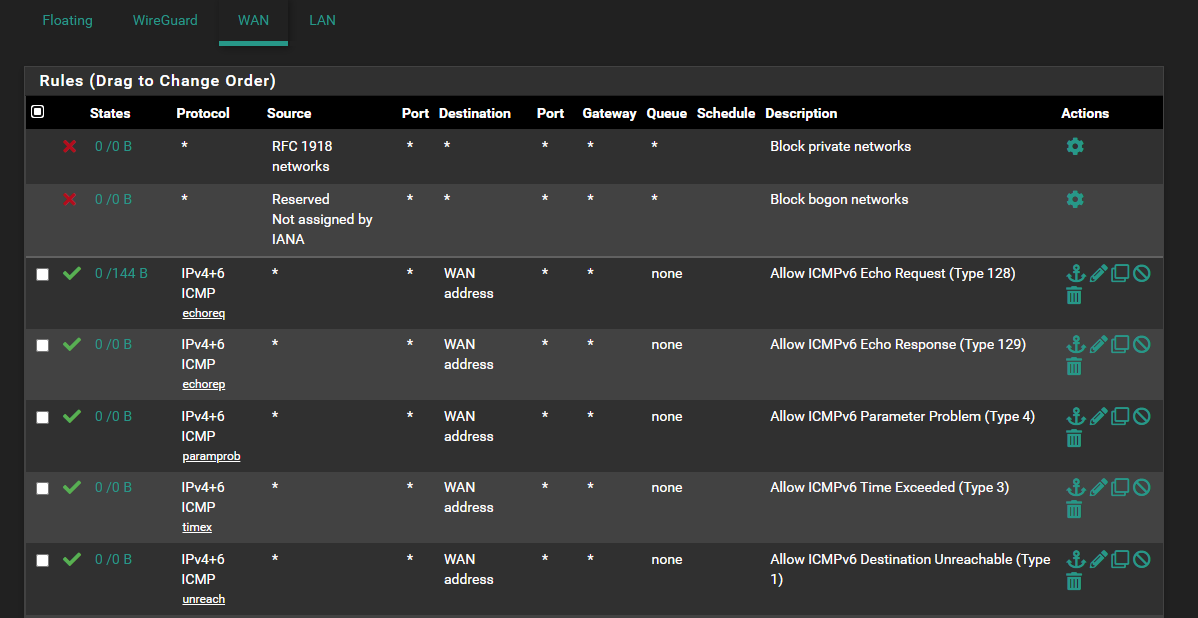
-
Break your ICMP rules on the WAN into separate rules for IPv4 and IPv6. Don't use the "IPv4+6" choice. Instead, create a rule for IPv4 ICMP traffic and then a separate rule for IPv6 ICMP traffic.
See the post here: https://potatoforinter.net/553/centurylink-ipv6-with-pfsense/.
-
I used to have a single ICMP rule for IPv4+IPv6 and it was as follows (it is still there - just disabled). When I was using that (before attempting to do the AD DS stuff - I would get a 19/20 from here: https://ipv6-test.com/
COMCAST (my ISP - does not yet set or use hostnames in the IPv6 realm for residential customers).
-
@bearhntr
Not sure you are understanding what I meant. In the ADDRESS FAMILY box, do NOT choose "IPv4+IPv6". Instead, create separate sets of rules for each protocol. So a set of rules where ADDRESS FAMILY is set for "IPv6" only, and then a set where ADDRESS FAMILY is set for "IPv4" only. For each family of rules you will choose ICMP in the PROTOCOL drop-down.In this link I posted earlier: https://potatoforinter.net/553/centurylink-ipv6-with-pfsense/, scroll down to #8 and read and follow those steps. Notice how it explicitly says "(don’t select IPv4+6 with ICMP – weird things happen)".
Also realized a bit later after my initial post above that the firewall on your testing client might be interfering. Windows by default will block unsolicited external traffic using the Windows Defender Firewall. External in your case would be the Internet. And with IPv6, there is no NAT usually, so your Windows client's IPv6 LAN address is exposed to the Internet. So that test site is going to attempt to ping the IPv6 address of your testing client (I assume that's a Windows machine). So you may have to put a firewall rule in place on the Windows machine to allow unsolicited inbound IPv6 if you want to pass the test.
-
I understood -- I have not gone through that 'potato' article yet.
I rebuilt my AD DS - got rid of the ESXi and move it back to a stand-alone server. I am still setting that back up - updates and such....then I am going to decide if I am going to do the AD DS stuff again - or just let the pfSense handle it all.
-
-
Thank you both for your assistance. Things appear to be back to the way they were before I tried to bring a Domain Controller into the mix. I still want to do that - but thinking I am going to let pfSense handle the Internet and DNS.
I guess I will have to do a little more research as how to do that - so as to prevent the IP BATTLE which is pfSense and Windows Server 2019 AD DS. LoL
I will keep looking for a setup guide, as I am sure that I am not the only one to have done this.
-
@bearhntr In the DNS Resolver "Domain Overrides" section add a line for your domain and each DC:
example.lan 192.168.0.2
example.lan 192.168.0.3Then any request for example.lan is forwarded to one of those two IPs.
and optionally for reverse:
0.168.192.in-addr.arpa 192.168.0.2
0.168.192.in-addr.arpa 192.168.0.3 -
Not following -- are your suggestions "should I decide to make a new Domain Controller" ??
I just find it so 'strange' that when I did this before (when Netgear ORBI was my router, DNS and DHCP) - I never had a problem. Perhaps it has logic in place to handle the IP Head-Butting. LOL
My goal (when I can get the UNIFI stuff I want) to remove the Netgear ORBI all together and install the Ubiquiti system for Wireless, etc. But, I have read someplace that I could do away with pfSense too with that system.
-
@bearhntr I thought you were asking how to get DNS functioning for your Windows domain, while using pfSense as a DNS server for IPv6. The options are: 1) don't, or 2) have pfSense forward requests for the Windows domain to the Windows DNS server, or 3) use only Windows DNS and have it forward all requests to pfSense.
The challenge with Windows AD is that when using Windows DNS under IPv4 and pfSense DNS under IPv6, pfSense doesn't know the Windows AD zone exists.
-
@steveits said in pfSense 2.5.2 - Web Console super slow:
The challenge with Windows AD is that when using Windows DNS under IPv4 and pfSense DNS under IPv6, pfSense doesn't know the Windows AD zone exists.
Unless you do as both @SteveITS and I have suggested and put the appropriate domain overrides and reverse pointer zones in the DNS Resolver options on pfSense so that it knows where to go (the Authoritative server) for DNS lookups related to your AD domain and local LAN IP space.
The bottom line here is that IF you want to use Windows AD and have some of your LAN clients be domain members, then you MUST let Windows AD do the DNS (and probably DHCP) stuff. You will never have good luck trying to run Active Directory with only
unboundas your DNS server running on pfSense.But if you abandon the use of Active Directory, then certainly it can be easier to use the default
unboundsettings in pfSense for DNS in your network. -
@bearhntr said in pfSense 2.5.2 - Web Console super slow:
I just find it so 'strange' that when I did this before (when Netgear ORBI was my router, DNS and DHCP) - I never had a problem. Perhaps it has logic in place to handle the IP Head-Butting. LOL
But when you had this "other" working setup did you also have an Active Directory domain in use with your Windows clients all being domain members? If you did, and were not using AD DNS, then I really don't see how it worked properly. If you did NOT have AD in place, then most certainly the old setup would have been fine.
The use of Active Directory in the mix is what makes the setup more complicated. That's because Microsoft's AD configuration creates "stuff" that most DNS servers don't tolerate in their configuration. Thus you generally are forced to use the Microsoft AD DNS server when you set up an Active Directory environment. That in turn makes the overall configuration of DNS (and DHCP, if you use it) more complicated and nuanced.
You really have to understand how it all works together so you can get the pieces configured correctly. It most definitely does work just fine when correctly configured. I am using that setup now, and before I was switched over to CGNAT by my ISP, I had a functioning Hurricane Electric IPv6 tunnel setup working just fine with routable IPv6 addresses in my LAN and in use by my Windows clients and servers. I could pass the IPv6 test sites with no issue. Once I got moved to CGNAT and lost the ability to use my Hurricane Electric tunnel, I had to dismantle the IPv6 stuff.
-
This is mainly where alot of my confusion lies. I only have 5 (at the moment) machines which will be "part" (joined) to the DOMAIN. As I build VMs for testing software products they may or may not get joined to the domain (single point of authentication as a lot of the testing I do is for this) -- still trying to decide if I am going to stand up a mail server. Since I am being forced to work from home - I am trying to set up my own lab at home, so that I do not have to do things over the VPN to the office and eat up more ISP bandwidth.
Here is what I really want:
-
ALL of "MY" devices to have an IP address and NAME that I set. I had in the ORBI when I was using it (each room with a number... for example the kitchen was xxx.xxx.xxx.03x - meaning that every networked device in that room was .30 to .39 ....each room had a specific number). I did that so that if I started seeing errors for a device I could find it easily. Some of my devices let me SET the hostname, others I have to do it from DNS.
-
I am not a huge fan of DNS, but I like to be able (have the option) to identify things by name....but I will make RSVP for devices in DHCP.
-
The LAB that I am standing up - maybe I should go down a VLAN path for this...although many of the Windows devices I want in the domain (for folder sharing, backups, etc,) are "MY" machines not LAB. As I am not super familiar with VLANs and setting them up - I opted to use one segment.
-
As I find that Linux and Mac OSes are not super-friendly with a Windows AD DS - I am hoping to set this all up in a manner (for my SmartHome) that should I sell my home - I can leave it all here for the next owner.
-
I am still thinking that I have something "hidden" or not correct in pfSense from all the playing and suggestions I was doing - that may be doing some stuff. I was going to completely reload pfSense 2.6 and rebuild from scratch - so I want to do it right the first time.
-
I have my own Top-Level Domain name - so I want to use that in pfSense and trying to make the decision if I want to do a sub-domain in the AD DS or something else.
-
I also have a CloudFlare account which I am using in my SmartHome to give DDNS support to my HomeAssistant installation.
-
I also want to look into setting up WireGuard VPN.
-
-
-
@bearhntr said in pfSense 2.5.2 - Web Console super slow:
When I had it setup before -- I was using the ORBI as my Router - DNS - DHCP...and Windows AD DS also seemed to be working in conjunction - but I would get strange outcomes from things there too.
As I said, when using Windows AD, you really must use a Microsoft DNS server in order for all of the Active Directory things to work. Some bits and pieces might sort of work with a non-Microsoft DNS server, but some key parts will not work and lead to the strange outcomes you referenced.