Unable To Port Forward
-
Port Forward as well as WAN and LAN firewall rules should be there.
Also I've seen people make separate rules for UDP and TCP while there is an option to use UDP+TCP. Is there any issue with just using UDP+TCP rather than making 2 rules for them?
I ran "test Port" heres the result
Also heres the result from ipconfig. Just to show the local ip
-
@exlow well not ever going to work, since pfsense can not talk to that IP on that port.. That wouldn't matter what your rules or forwards are..
You need to figure out why that is happening before you worry about your forwarding not working. Service is not listing on the port you think it is? Its not actually running, that device is running a firewall? Its not using pfsense as its gateway.
Can pfsense even ping that IP?
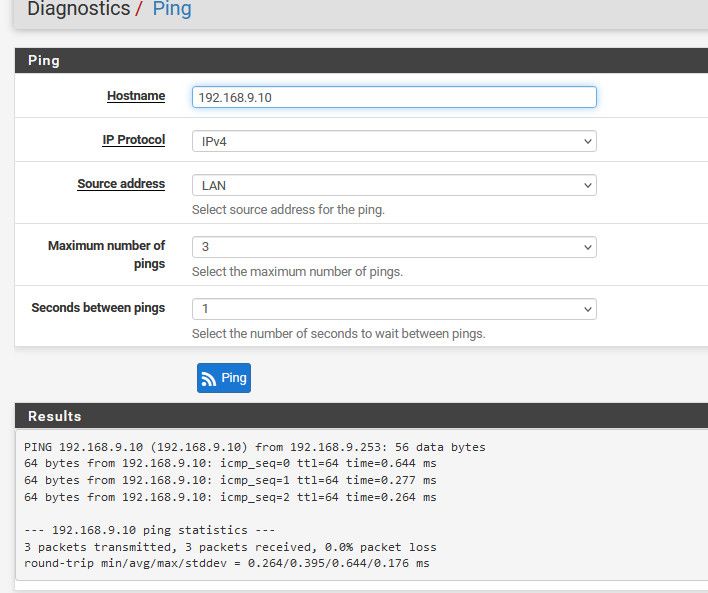
-
@johnpoz I did get a ping on 192.168.1.19, 0% loss. There is a firewall(windows 11) but I have allowed both incoming and outbound traffic for port 25565. "Minecraft" is the name and the rules are at the very top of the first screenshot.
What do you mean by "Service is not listing on the port you think it is?"? I don't follow you on that question.
-
@exlow look on that box with netstat - does it show that port being listened on?
example
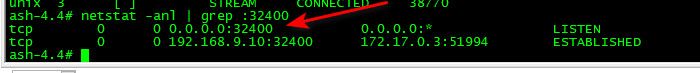
That is showing my nas is listening on 32400 on all of its IPs.
Validate your box is actually listening on that port, if it is and your test fails - then your firewall settings are wrong for allowing access. Or maybe its only listening on loopback 127.0.0.1
-
@johnpoz
C:\Users\infin>
I don't think I'm running the right command. But here's what I got from running netstat
-
@exlow use
netstat -an
This will show you listening ports - that is just showing you stuff you have connections too.
the n of that makes sure it shows number for the ports vs service names
-
@johnpoz Thanks for that. Heres all the listening ports.
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING
TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING
TCP 0.0.0.0:10801 0.0.0.0:0 LISTENING
TCP 0.0.0.0:34034 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49671 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49672 0.0.0.0:0 LISTENING
TCP 0.0.0.0:54288 0.0.0.0:0 LISTENING
TCP 127.0.0.1:5939 0.0.0.0:0 LISTENING
TCP 127.0.0.1:6463 0.0.0.0:0 LISTENING
TCP 127.0.0.1:27060 0.0.0.0:0 LISTENING
TCP 192.168.1.19:139 0.0.0.0:0 LISTENING -
@exlow well don't see any 25565 port listening, so no you wouldn't be able to talk to anything on that port.
Is that the full list?
-
@johnpoz futher down I've got this but still not 25565 I ran finder on the whole list, No 25565 at all.
TCP [::]:135 [::]:0 LISTENING
TCP [::]:445 [::]:0 LISTENING
TCP [::]:7680 [::]:0 LISTENING
TCP [::]:10801 [::]:0 LISTENING
TCP [::]:34034 [::]:0 LISTENING
TCP [::]:49664 [::]:0 LISTENING
TCP [::]:49665 [::]:0 LISTENING
TCP [::]:49666 [::]:0 LISTENING
TCP [::]:49667 [::]:0 LISTENING
TCP [::]:49668 [::]:0 LISTENING
TCP [::]:49671 [::]:0 LISTENING
TCP [::]:49672 [::]:0 LISTENING
TCP [::]:54288 [::]:0 LISTENING
TCP [::1]:10801 [::1]:64893 ESTABLISHED
TCP [::1]:49670 [::]:0 LISTENING
TCP [::1]:64893 [::1]:10801 ESTABLISHED -
@exlow yeah your not listening on that port - so no portforward you setup is ever going to work, since the box isn't listening on the port your trying to forward too.
You sure the service that is suppose to listen on that port is actually running?
-
@johnpoz So use a different port?
-
@exlow is the service/application you set to listen on that port even running?
-
@johnpoz nope... I've been at this so long I forgot to start the sever.
So the sever is running now. And the port 25565 is listening. The port still is not open. I will re-try the LAN sniff.
-
@exlow yeah to the port test from pfsense.
-
@johnpoz Still nothing from https://www.yougetsignal.com when I run a packet capture on the LAN network with 25565 selected.
-
@exlow does your port test work? from pfsense?
Where did you post your port forward and firewall rules - the only thing I saw was outbound nat page.
-
@johnpoz We've got an open port... I combined TCP/UDP inside the firewall into one rule and checked the port and its open. Only took 3 hours to get to this point. Thank you so much for the help man. I honestly still don't exactly know how changing the two separate Rules into one did anything but its working.
-
@exlow said in Unable To Port Forward:
I honestly still don't exactly know how changing the two separate Rules into one did anything but its working.
Have no idea what rules or firewall rules you had, but those port checkers are only going to test TCP.. They do not test UDP.. You said yourself it wasn't listening even.
But here is a test, and I don't even have anything listening on that port..
My forward, my wan rules, my sniff on lan side
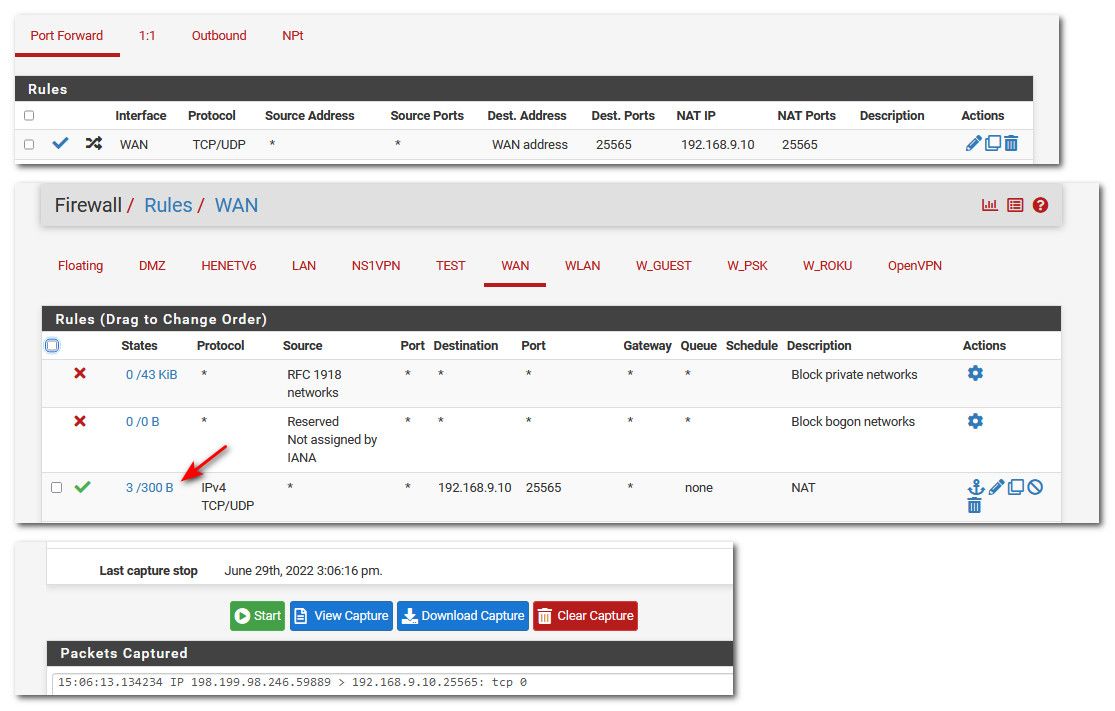
The rule prob had nothing to do with it, since before your service wasn't even listening.
Notice the rule that is on my wan, -- notice where it shows 3/300B this shows the rule was actually evaluated.
If your wan rule that allows the port forward is only every 0/0 then that means its not being evaluated.. When you sniff on the lan side when you do the test.. Pfsense will send the traffic on, as long as it can talk to that IP, be it that IP is listening on that port or not.. As long as pfsense can talk to it, ie it has an mac address via arp it would send the traffic on.
-
@johnpoz Heres what I've got.
The only odd thing is when I try snuffing the LAN side I still get nothing back from 25565.
-
@exlow Well then it wouldn't work..
Your either sniffing wrong, you have to select the interface the box is on 192.168.1.19, is that your lan, you show multiple other interfaces.
Again sniffing you prob need to filter for that port.. By default it limits to 100 packets, its quite possible your missing it in your capture by time you start the capture and go and test..
if your sending to it, and you don't get anything back - that also screams firewall on the box, or again not listening.. Maybe the service is crashing..
Here is pfsense roll in this, you forward to IP X, does pfsense have a mac address for that IP, then it forwards the traffic to it - that box actually send an answer, or sending it to pfsense has nothing to do with pfsense.





