Can't get pfBlockerNG to block pornhub.com
-
No problem that pfSense configuration website I sent is my favorite.
I tested my firewalls DNS, it will still see that address however, it is blocked on the USER side from accessing it on any browser that is included in the Squidguard blocks USER configured IP addresses to static MAC mappings.
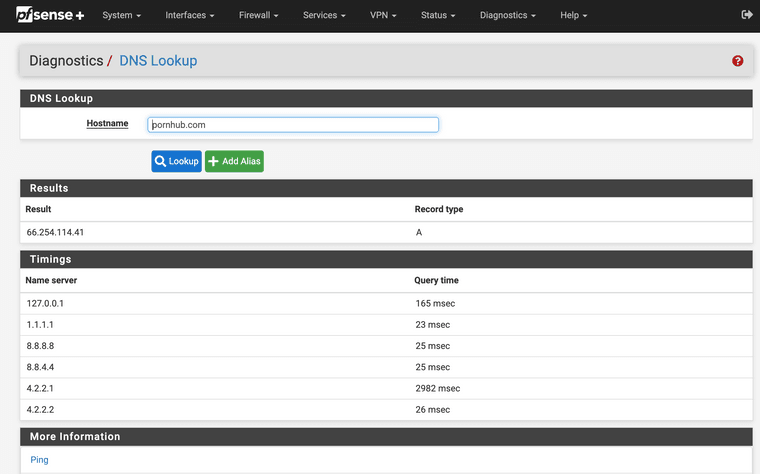
(Image: Firewall Sees the IP address)
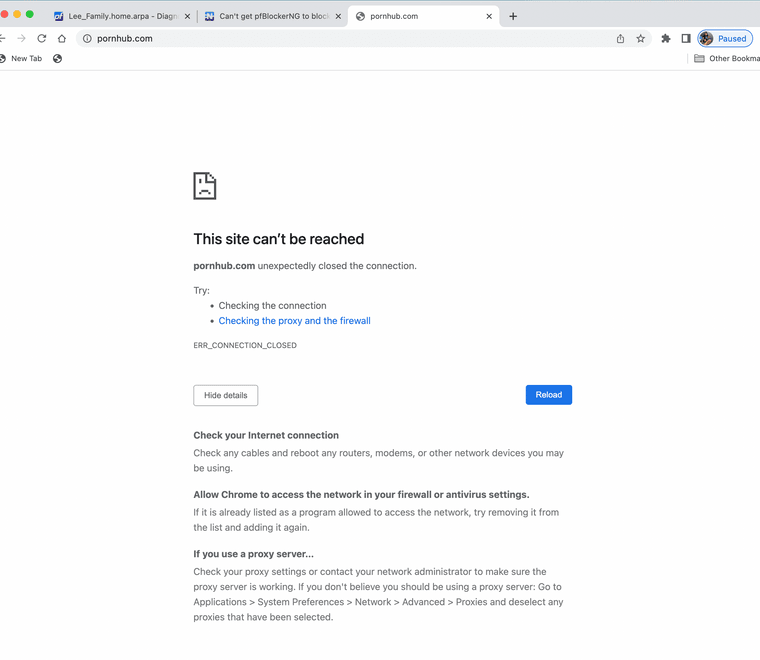
(Image: End users can not get to it)Keep in mind this is SSL based if I use a HTTP request I have a custom webpage.
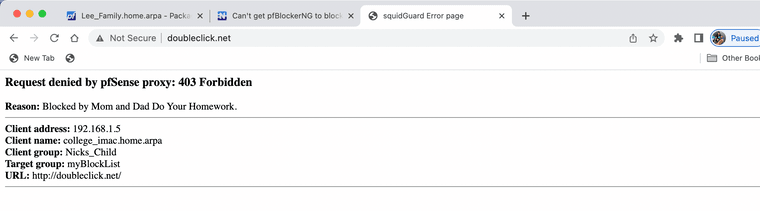
(Image: HTTP site blocked)One more detail you must also block out the IP addresses in the URL to make this fully work this way no one can use dig or use nslookup and grab that IP and plug it in and access the site still. Also block major network atomizers that bypass proxies online.
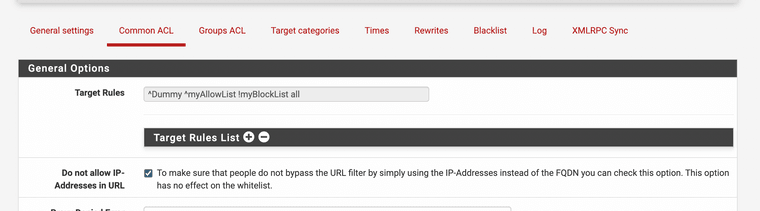
(Image: IP block for URL access)
-
@lpd7 said in Can't get pfBlockerNG to block pornhub.com:
ip for the server was the loopback for the pFS box
...which means it's working. :) Ensure your PC isn't caching the old DNS...in Windows run "ipconfig /flushdns" to empty the cache, and close your browser.
-
@jonathanlee I have been looking over the instructions both from what you provided and from the link that goes step by step all of which is good stuff.
I attempted to start working on it but pulled back as I dont want to foul up my active box and am waiting for a new case so I can get a second box up and running which is what I will use for this build. The question that I have is about vlans....are they a necessity and if so can I use the LAN interface for that purpose?
My setup is configured with the WAN coming into one port on the FW and the LAN going out another port to a managed switch which connects various APs and other non managed switches and hard wired computers.
The instructions in the link (https://forum.it-monkey.net/index.php?topic=23.0) doesnt seem to mention vlans so just want to verify this can be done without the use of vlans.
I know what vlans are but have no experience with them so am trying to keep a handle on the learning curve, once I master one function then move onto another.
Once I get the other box up and running (hopefully by july 4 weekend) I will use that in isolation with a single pc to test the rules/blocking once it all seems to be working I will do the switch over.
Thank you.
-
@lpd7 If you are using the pfsense as a dns resolver cant you also just set up a host override pointing to 127.0.0.1 ?
That blocks it for sure. -
@michmoor I am using dns resolver but am unfamiliar with the remedy you suggest. Based on what I have seen and been told it appears the resolution is a bit more in depth but I can be wrong as there seems to be many schools of thought on this topic.
So to restate:
I want to control/limit access by local devices/clients to web sites of my choosing. I do not want to have to configure each device individually but rather have the FW do the work. This is particularly important for those web sites whose URLs are encrypted (DoT, DoH).So would the solution proposed by jonathanlee within this thread be the correct path and if so I have a question about vlans.
or
Are the instructions listed at https://forum.it-monkey.net/index.php?topic=23.0 the solution I am seeking.
Appreciate the feedback.
-
@lpd7 said in Can't get pfBlockerNG to block pornhub.com:
web sites whose URLs are encrypted (DoT, DoH).
Just to correct a misnomer here - the website is not encrypted via dot or doh, your browser is bypassing your dns and looking up the IP of the website via dns through the dot or doh server.
You can still setup an host alias for pornhub.com so that pfsense looks up that fqdn and blocks the IP it finds. This should be the same no matter where its looked up from. While pfblocker can do that, its also just a simple native host alias in pfsense.
-
@johnpoz The browsers are using the PFBox for DNS resolution, I have already confirmed that using nslookup within the PF command line. Why is this topic so confusing to get a straight answer to and why do there seem to be so many supposed ways to accomplish this? Seems to me this is something that is core to the system and not something that should be so obscure to accomplish.
-
@lpd7 if you are using VLANs you would need to add each of those subnets into the access control list on the Squid Proxy as well as create Access control Lists on the firewall for them. That would be the only difference as they are still going into the firewall. I am not running VLANs as it's just used in my home.
-
@lpd7 not sure where you going with that statement - its not even your thread. And to be honest I haven't paid to much attention to this whole thread because I agree with you - not being able to get pfblocker to block a domain is clear user error that is for sure.
My point was urls are not encrypted via dot or doh - that is encryption for a dns lookup not the site, etc
If your browser is using dot or doh - you can not block anything via dns, which would be what pfblocker normally does, etc.. Sure it could block via an IP in a rule, just like you can do with an alias.. But if your just telling the browser via a dns look up that some fqdn is 127.0.0.1 or 10.10.10.10 a browser via doh is going to circumvent that.
-
@jonathanlee Thank you for that info it makes things a bit clearer and probably simpler to implement. My new case was just delivered so I am going to put together a second box from which to work on this and hopefully with the help from kind souls such as yourself I can get it running as needed. Thanks again and Happy 4th weekend.
-
@johnpoz Didnt realize that I had to own a thread to ask a question to which the thread was related. Maybe I didnt articulate the issue clearly. If a URL is using HTTPS it seems that the system is unable to see the URL because its encrypted and that additional steps are required to get it to see and filter based on a block list. That is a summary of what I have put together based on all of the feedback from various sources, all I am trying to do now is sift through everything and find the correct way to achieve the goal.
-
@lpd7 you can block https urls. Remember all browsers use what are called get requests, proxies use the get requests only to understand when you say that's a block. The data on https when a connection is made that's encrypted and comes after the get request is approved.
-
@lpd7 you can ask a question sure - but quite often users jump into a thread when their problem isn't the same.
Doh in a browser circumvents your local dns - nslookup might show that the system is using your local dns (pfsense).. But the browser isn't if its using doh.
If your device ask for something.domain.tld and you return 127.0.0.1 or 10.10.10.10 is isn't going to get to http or https://something.domain.tld
But if using doh and it gets the public IP 1.2.3.4 for example - unless you block that actual IP, then sure the browser can get there.
-
Make sure you have the latest version of pfBlockerNG installed. It's always good to stay up to date. Now, regarding the issue with blocking pornhub.com, it might be worth double-checking your category settings in Shallalist and UT1 Summary. Ensure that the appropriate categories related to adult content and porn are selected.
-
Let’s put my 5c to this: small child from 7(?)yo able to install some app called “free VPN” and Your pfSense are out of game with this: until You not blocking ALL possible VPN protocols - access to PH are open to it…
After You find abilities to blocking ALL possible VPN protocols, the NewNode protocol are from 1 tap away on child’s smartphone.
And am not sure You have a sufficient skills to block NewNode… (sorry bro!) -
@Sergei_Shablovsky I use proxy based blocking with certificates, the firewall can be set to inspect VPN tunnels also in advanced settings in pfSense or Snort. VPNs are not invincible by any means. Again proxy or dns blocking is not invincible also. Just depends on the amount of time it takes to get around the firewall. I think with the proxy it makes it take longer to get around it. You can make it block the ports that the VPN are using also, the free ones will always use the same ports, control access to that port…
-
@JonathanLee said in Can't get pfBlockerNG to block pornhub.com:
@Sergei_Shablovsky I use proxy based blocking with certificates, the firewall can be set to inspect VPN tunnels also in advanced settings in pfSense or Snort. VPNs are not invincible by any means. Again proxy or dns blocking is not invincible also. Just depends on the amount of time it takes to get around the firewall. I think with the proxy it makes it take longer to get around it. You can make it block the ports that the VPN are using also, the free ones will always use the same ports, control access to that port…
I thinking that would be interesting for You to read https://github.com/clostra/newnode/blob/master/docs/newnode-spec.md
Just try on test iPhone/Android: connect to Your customers lan, install NewNode app, start pcap on an certain interface, and then try to connect to PH.
If pfSense able to block access, - You are win, I’m loose. If not - analyse the dump by WireShark and create additional FW rules…NewNode VPN
https://apps.apple.com/us/app/newnode-vpn/id1473074621NewNode
https://apps.apple.com/us/app/newnode/id1603136752 -
@Sergei_Shablovsky said in Can't get pfBlockerNG to block pornhub.com:
https://github.com/clostra/newnode/blob/master/docs/newnode-spec.md
Thanks for the info, I will have to get a sandbox going to test this, I am doing classes again so I might not have time anytime soon.
-
Hello again, I got some time, I am spinning up a VM to test it.
My CAL 2 class HW done, and checked, and POLS quiz done.
Just waiting for my one approved VM copy to download per my original Apple software license. I get one VM of the software to use onto of the host software.

That software package says it stops host services so I want it in a sandbox/vm to test.
3-4 hrs for my vm to fully spin up I estimate. I am betting on AppID to spot it.
-
@Sergei_Shablovsky I have attempted 2 different installs over Virtualbox Version 7.0.8_BETA4 r156879 (Qt6.3.0) on M1 processor, all crash with the development version. I am going to create an ISO and move it to my Windows 11 system and install the VM there I should be able to test this sometime tomorrow. Sorry I even tried Unbuntu with M1 virtualbox. It acts like the iMac has something using the virtualization hardware.