DNS over IPSEC VPN
-
Hello Everyone,
First post to the forum please be gentle. :)
I have two PFSENSE devices that have a functional IPSEC VPN between them.
Any IP address from the main office can ping an address to the branch office and vice versa.
Traffic is currently passing. Hyper-V replica is working as we speak.
However, the one computer in the branch cannot resolve DNS from the main office (the branch does not have a domain controller). Therefore, the one computer, which is a domain member, cannot connect to the domain controller in the main office.
The main office is 192.168.16.0 and the branch is 192.168.96.0. I have tried setting the branch windows computer to the DNS of the main office (192.168.16.6) but that doesn't work. I tried setting the windows computer DNS in the branch to its pfsense (192.168.96.1) and did the following:
General - Settings set DNS to main office 192.168.16.6
Services - DNS Resolver: Network Interfaces = All; Outgoing network interfaces=LAN and LOCLHOST; DNS Query forwarding checked; Domain and lookup server address adding to Domain Overrides; main office network and mask added to Access List.Still cannot ping main office computers by DNS name over the IPSEC VPN (and, yes, ping does work by IP address).
IPSEC VPN protocols set to ANY on both sides.
Firewall rules set to ANY on both sides.What am I missing? Is there a documented procedure on this?
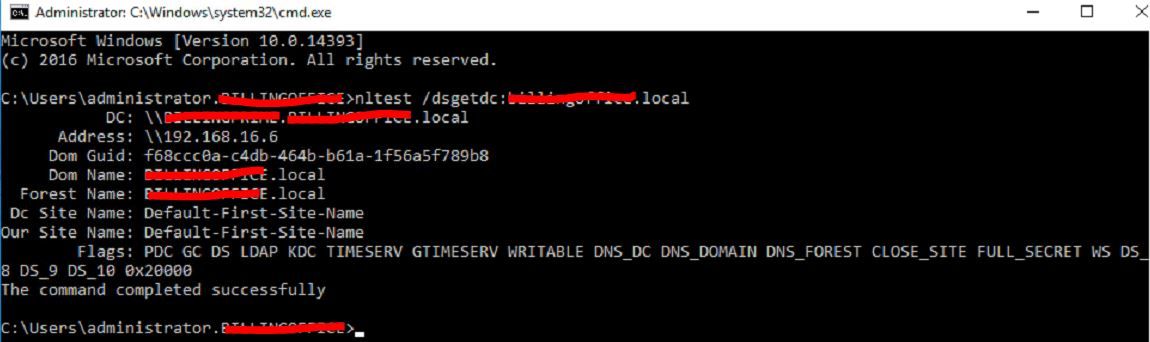
Amazingly, when I use NSLOOKUP in the branch is says my server is pfsense.home.arpa and when I enter the name of a server in the main office (e.g. SQLSERVER) I do get a non-authoritative answer with the full DNS name and correct ip address (192.168.16.35)
Thoughts?
JamesNT
-
Was just skimming your test ....
But often people gets bitten by the Unbound DNS Accesslist requirement.
pfSense/Unbound knows of the ip networks you have defined as/on "interfaces" , and for those no additional ACL is needed.
But often you need to add "Remote Networks" like "Client VPN ranges" and Remote site networks , to the ACL system , else Unbound will reject the query.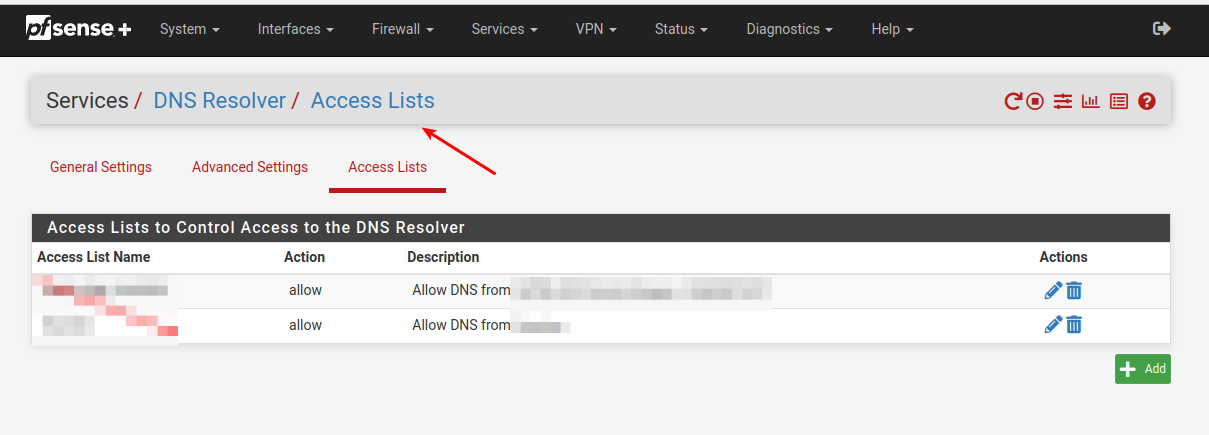
-
I had already added the main office network of 192.168.16.0/24 to ACL. What else would be needed there?
JamesNT
-
Could be several things ...
Siite1 pfSense where servers & Win DC are
Site2 Remote pfSense where clients w. dns issue are"1:
Did you use (handout) the same DNS suffix on both sites , for the clients ??2:
Did you try to ping the fqdn of the servers ?
What fqdn works for pinging a server , on a Site1 client ?3:
What DNS server is set (handed out) to the remote clients (Site 2) ?I mean ... You technically have 3 possibilities ...
Site1 pfSense
Site1 DC
Site2 pfSenseBut watch out Unbound might not like RFC1918 answers , unless you tell it to
4:
I would expect you have to allow DNS to pass on all relevant pfSense interfaces.
Do you see any deny's ?Do you use the domain override function on any of the pfSenses ??
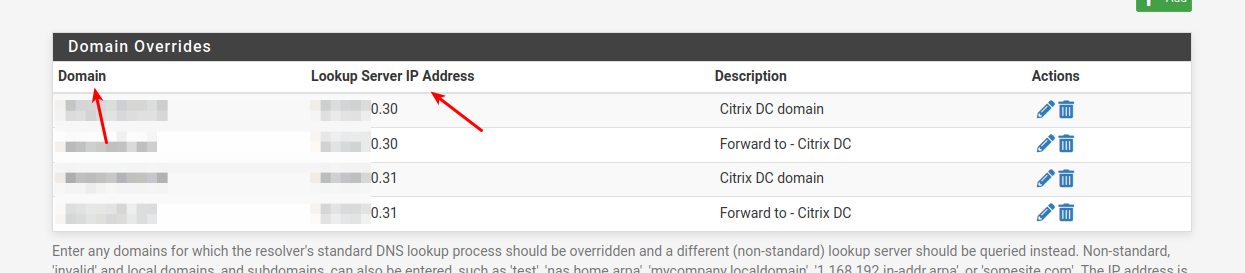
That's where you can tell it that any resolving for ie: "mydomain.com" should be forwarded to the dns server with ip address a.b.c.d
-
@jamesnt said in DNS over IPSEC VPN:
I had already added the main office network of 192.168.16.0/24 to ACL. What else would be needed there?
JamesNT
OOpzz
Missed the specifics here ....
You would need to add the ip network of the clients doing the requests , including the remote ip nets (any clients doing dns against that pfSense/Unbound)
The ACL goes for "Who is allowed to ask" not what is handed out as answer
-
@bingo600
Excellent, thank you. The remote server now sees the domain controller on the other side of the IPSEC VPN.