Trying to not log 224.0.0.0/24
-
I'm a new pfSense user with a 2100 for home use and am in the process of evaluating logs to create Pass rules to reduce some of the noise in the logs. After a week or two when I get a sense of what's normal traffic I'll consolidate the rules.
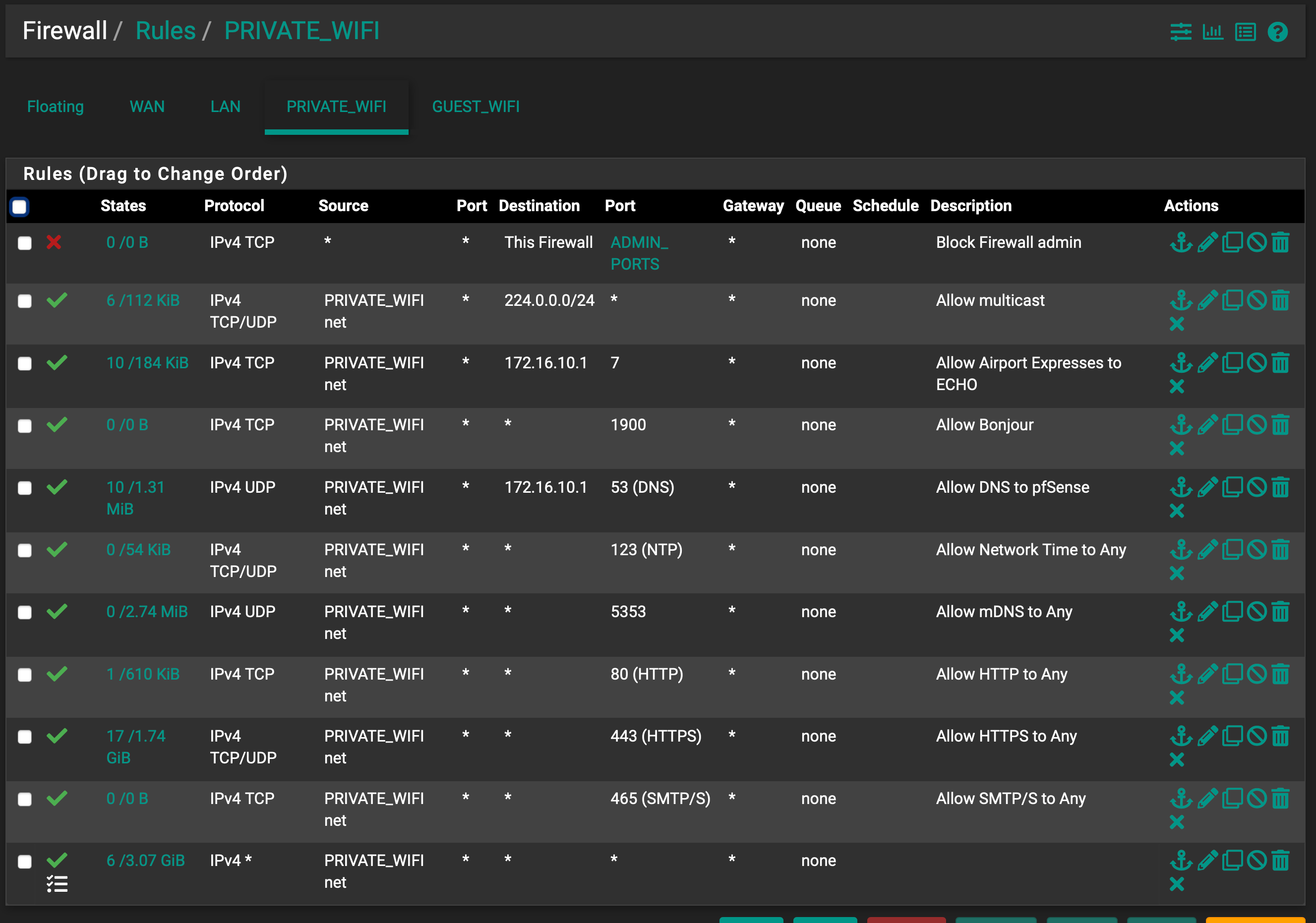
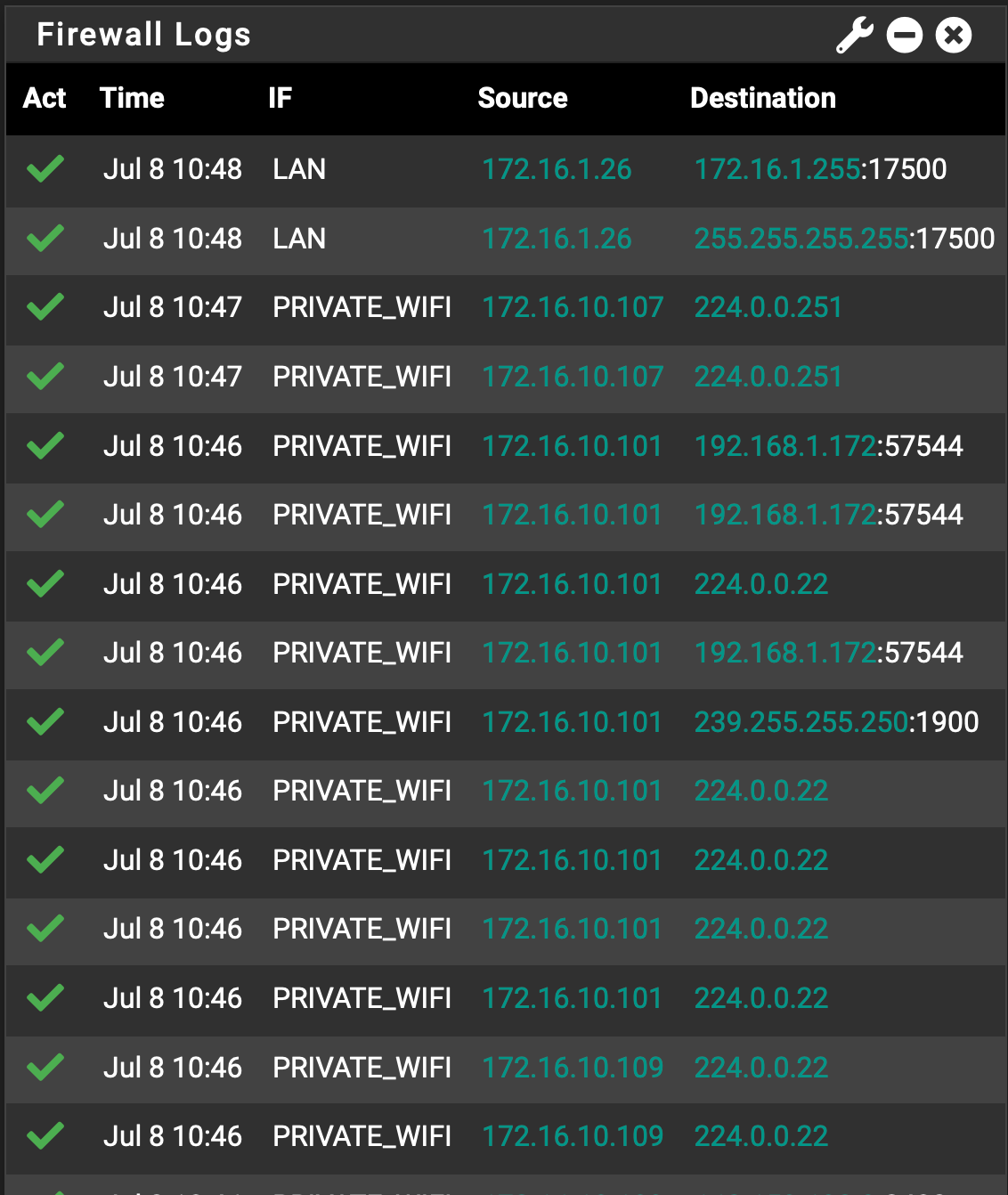
In PRIVATE_WIFI VLAN for iPhones, iPads, AppleTV, etc., I see multicast log entries to 224.0.0.2, .22 and .251 without any port number. I created a Pass rule for any 224.0.0.0/24 but I still see them in the log.
Similar behavior with 239.255.255.255:1900.
Is this a side effect of Avahi being installed?
How can I pass and not log these?
-
In the rule you can select if you want to log packets, probably that is checked.
If they are blocked by the default rule, then they show up and then your rule is not 100%.EDIT: Ok, they are allowed by the bottom rule to allow all, because that has logging enabled.
Your rule to capture multicasts is not 100% as it is not capturing them (or at least not all).
It's not always easy with avahi, but usually I would say to create mdns rule as follows:IPv4 UDP Source: * Port: * Destination: 224.0.0.251 Port:5353
So try to test with different rule settings and let us know.
-
@terryzb you might want to turn on rule descriptions in the log settings, so you can see which rule is logging those.
But yes if you want to allow for avahi to work, you need to allow the multicast address, but that should only really be 224.0.0.251
224.0.0.22 is IGMP and no it wouldn't have a port with it.. its a different protocol - but I see your logging your last rule that is any any rule which yes would log such traffic. See that little menu looking icon right under the green checkmark allow icon.
-
@johnpoz
Thanks John. Yes, I set the any any rule to log so I could see what's still coming into the interface after explicitly passing traffic I'm good with. The rules above are set to not log in order to visually reduce noise in the log so I can get a better idea of what's going on. Thanks for the tip on rule descriptions. I will turn that on to get more info.EDIT: I assumed you were talking about the Dashboard logging widget but I don't see an option for rule descriptions there, or in System Logs->Settings. Where is this set?
Thanks,
-Terry -
@terryzb said in Trying to not log 224.0.0.0/24:
System Logs->Settings.
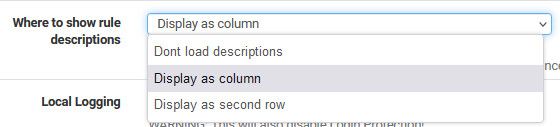
I don't think there is a way to see the descriptions in the widget.
-
And suppose you would want to capture all multicast, igmp, broadcasts, so these are not captured by the default rule?
I ask related to my post, how to allow or block internet access when avahi is used as well, the usual way seems to be:
net -> !RCF1918 allow/block

but that rule (with avahi) also captures the multicast, igmp and all other local traffic that is not rfc1918.
It would be better to capture all this with a designated rule, rather than getting that traffic mixed with an 'allow/block internet' rule.
Get me? how would you do that the correct way?
@terryzb sorry for using your thread for this question, but i guess it can help you too right? -
@johnpoz
Thanks John. It was already set to display as column. -
@hardware_bxl said in Trying to not log 224.0.0.0/24:
but that rule (with avahi) also captures the multicast, igmp and all other local traffic that is not rfc1918.
avahi is only going to work with 224.0.0.251 since this is the multicast address used with mdns. If you create a rule for 224.0.0/24 then yeah it would catch all the multicast.. So make a more specific rule for just the 224.0.0.251 address.
if you want to log that then put a rule above your any any rule that logs that. Same with anything specific else you want to log or not log.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated. If traffic goes through your rule set, and doesn't match then it would be denied. And by default logged.
So setup your rules that you want to log or not log so they are evaluated before your last rule or the default deny rule and do what you want be it allow and log or block and not log, etc.
example I want to log any traffic to 224.0.0.251
so in your list create that rule, set it to logNow you don't want to log any other multicast.
Below that rule, but above your last rule, but rule that says 224.0.0/24 and allow it or block it log it or don't log it, etc. -
@johnpoz said in Trying to not log 224.0.0.0/24:
So setup your rules that you want to log or not log so they are evaluated before your last rule or the default deny rule and do what you want be it allow and log or block and not log, etc.
example I want to log any traffic to 224.0.0.251
so in your list create that rule, set it to log
Now you don't want to log any other multicast.
Below that rule, but above your last rule, but rule that says 224.0.0/24 and allow it or block it log it or don't log it, etc.We're completely on the same page about rule order and logging John. My original question was why, even though I had a TCP/UDP 224.0.0.0/24 pass rule without logging near the top, was it still being caught by the Allow any any rule at the bottom and showing up in the log.
After your comment about 224.0.0.22 being IGMP, I changed the 224.0.0.0/24 pass no log rule to be IGMP and so far, 224.0.0.2, .22 and .251 seem to be caught by it and are not showing up in the log.
Thanks again for your help.
-Terry -
@terryzb or you could of changed it to any for the protocol.. Yeah igmp is not udp or tcp which is what your no log rule was ;)