Possible to traceroute from pfSense across VPN connection?
-
Outbound rules would be. Routing also applies.
What are you tracerouting to?
-
@stephenw10 I was testing wp.pl and gazeta.pl. I can't glance anything out of my FW rules to indicate the issue could be there, but I did disable some "probable" rules and tested, but still the same 96.x.x.29 is the first hop IP.
-
You have any static routes for those that would apply via WAN?
What pfSense version are you running?
-
I do not have any static routes. I'm on 22.05 SG-2440.
-
@bartkowski said in Possible to traceroute from pfSense across VPN connection?:
I have a NordVPN connection (use with policy routing) established and would like to perform a traceroute across that connection. Is that possible from pfSense, GUI or command?
No. The policy routing is applied to incoming traffic on the interface you've defined the rule. But pfSense itself doesn't obey it.
You can only trace the route from a device connected to this interface. -
You may not have added them as static routes but they might be there for other reasons such as DNS servers or VPN endpoints. Check Diag > Routes to be sure.
Steve
-
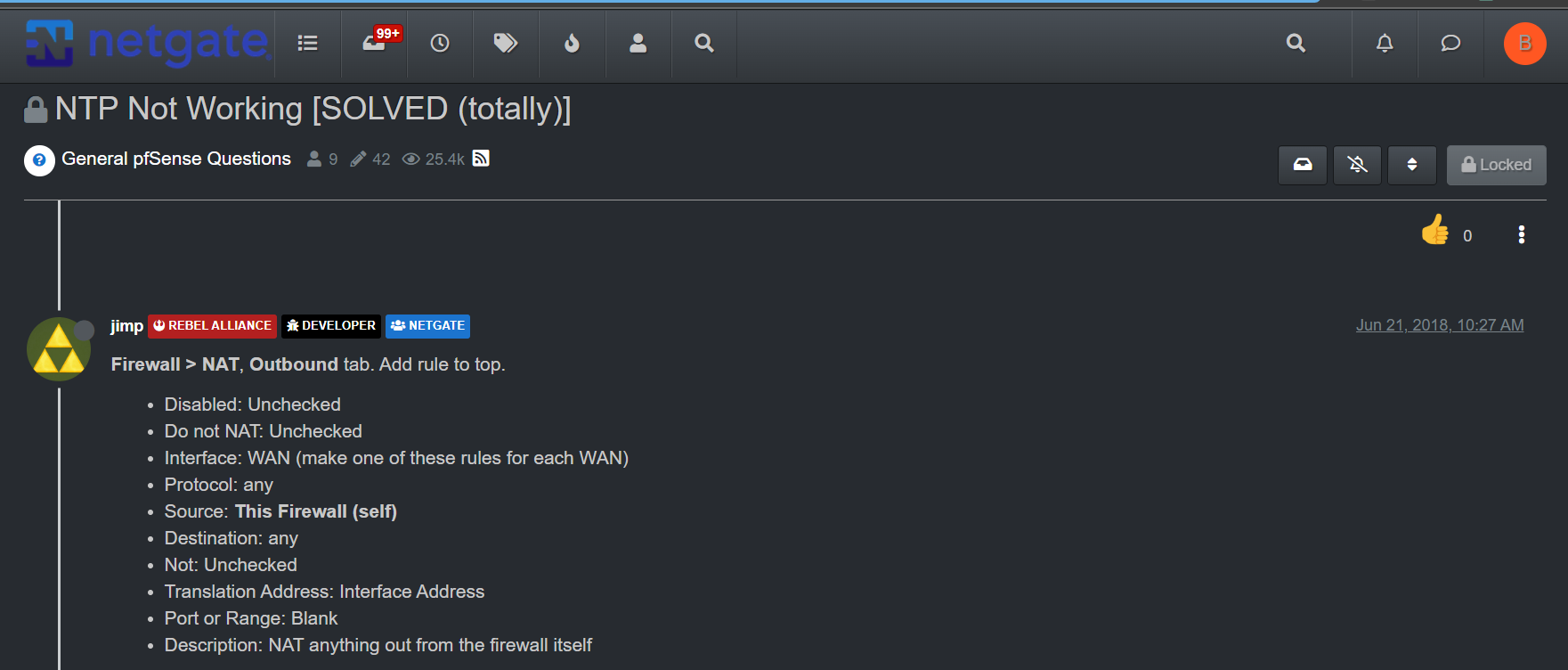
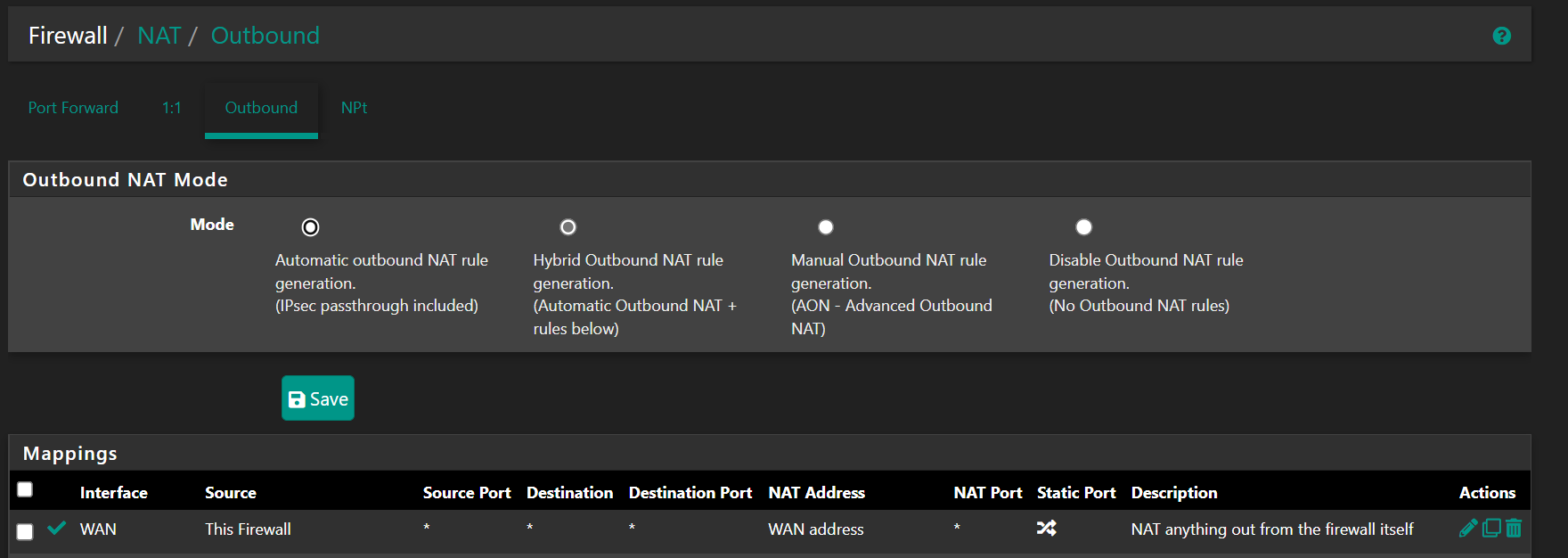
@stephenw10 I think I may have found my issue, an Outbound NAT mapping which I put in to fix some other issue (NTP if I recall correctly).
-
In automatic mode it ignores any manually entered rules. Also that rule would only apply to traffic leaving the WAN and not the VPN.
-
@stephenw10 If I disable the Outbound NAT rule and do my traceroute, the first hop is on IP from VPN provider, 10.8.2.1. With the rule active, it goes out my WAN via 96.x.x.29.
-
That rule shown in your screenshot? With Outbound NAT set to automatic mode?
-
@stephenw10 Yes, but it is set to Hybrid.
edit: and yes, this rule is to fix NTP, without, NTP does not work.
-
Ah, well try changing that rule to destination port 123 so it only catches NTP traffic.
-
@stephenw10 That did it, thank you.
Here is the relevant thread and note from JimP about this rule. ( I cannot post hyperlinks)