Just trying to forward 443 to an internal server
-
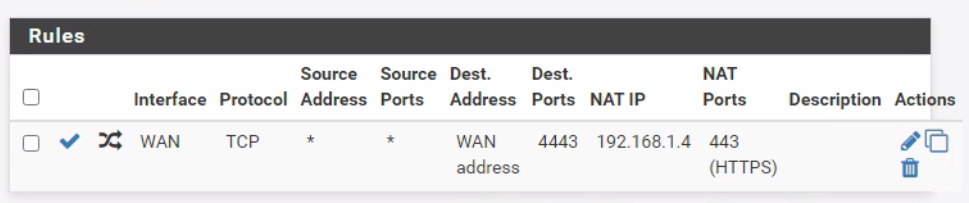
To start off, I've taken the web interface off 443 as it was somehow available from the web and interfering with the NAT translation. Here is my config:
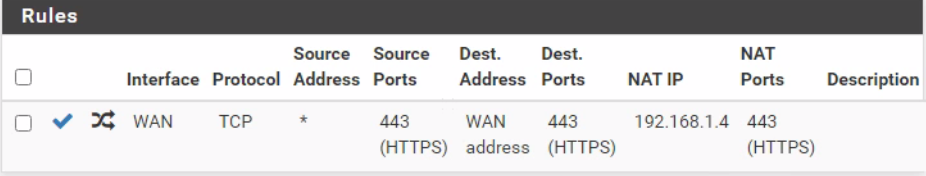
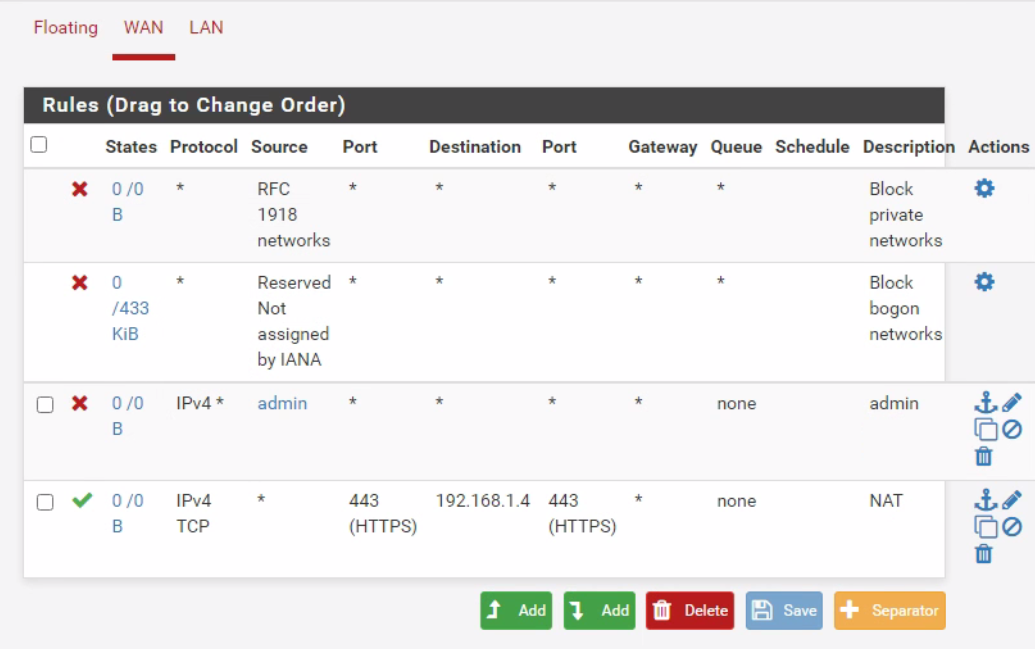
No matter what I look up as a reference and follow I can't get to the webpage hosted on 192.168.1.4.
If I go to that IP address internally it works. HTTPS to the external IP just has it spinning and timing out eventually.Where am I going wrong? Any help is appreciated.
-
@combat_wombat27
Don't state a source port, it's dynamic. -
@viragomann Source Port removed. Still getting the same spinning never opening on the external IP.
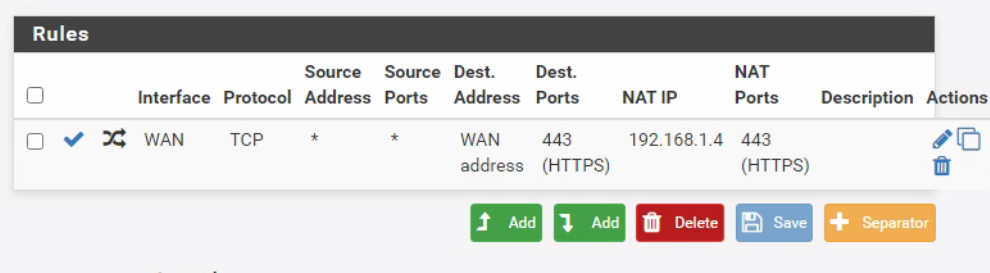
-
@combat_wombat27
Are you sure that the web server is responding?Does your WAN have a public IP or is it behind a NAT router?
-
@viragomann the webserver is responding on it's IP as expected.
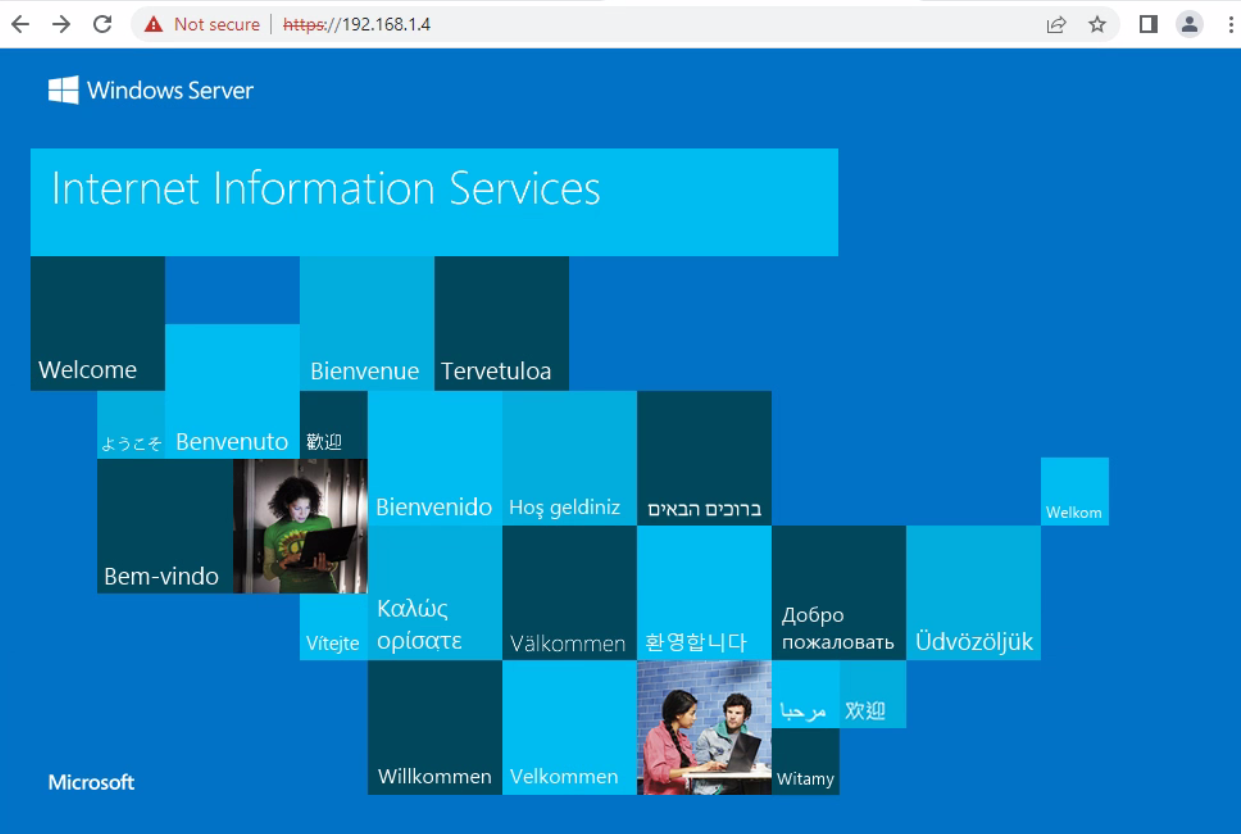
The firewall is directly connected to the ISPs connection on the WAN. No natting there. I also know you CAN reach 443 at that IP as when it was on port 443 instead of HTTP 80, the firewall's GUI was accessible. I changed it over to port 80 HTTP in order to try and avoid it being IN THE WAY for the port I want to forward to the server.
-
@combat_wombat27
So this screen shows an access from inside your network. The question is, if the server does respond if the request is coming from outside. -
@viragomann no, that is the whole problem. I'm not getting the site externally as expected.
-
@combat_wombat27 Try going back to https on pfSense but set it to port 444 or something else, then try to access your webserver on 443.
-
@combat_wombat27
So possibly the Windows server is blocking access from outside.For reliably testing forward also port 80.
When using https, the client is expecting an SSL cert from the server.To investigate you go to Diagnostic > Packet capture on pfSense and run a capture on LAN.
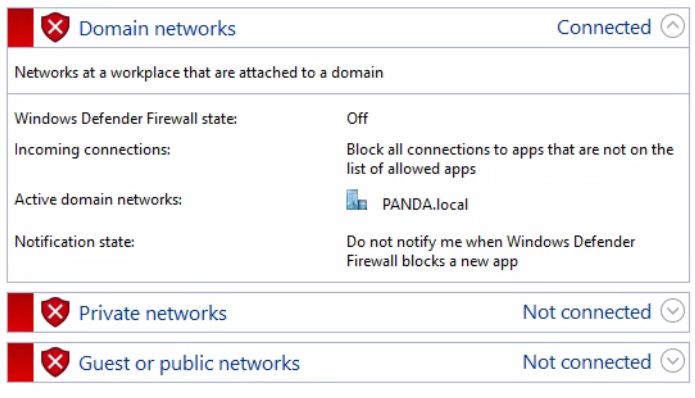
If you can see request packets to the internal IP, but no responses, the Windows firewall is probably blocking it. -
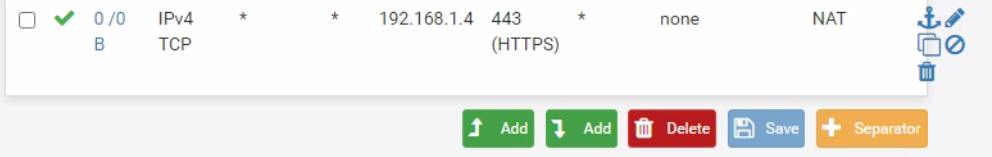
@viragomann I'm afraid I have to disagree that the server is blocking anything. As far as it is concerned it is successfully displaying its webpage via its IP, which would be NATed to in the case of external access. I'm busy using port 80 for the web GUI of the firewall. It is not establishing a secure connection using the right SSL cert. It is also notable that the firewall rule doesn't show any passed traffic.
-
@jarhead Okay, I did as requested and the site is still unavailable externally.
-
@combat_wombat27 Interesting. How about trying a different external port forwarded to the server on 443?
Alternatively you can change the port on the server itself but I would try a different external port just for testing.
Do you have any other NAT's? Curious if it's just 443 or all ports not working. -
@jarhead Okay, I just tried 4443 and it has made no difference. I can't leave this permanently as it is for the proper workings of a standard RDP Gateway, but at least for testing I can. It hasn't worked. Also, I don't have any other ports forwarded to compare with.
-
@combat_wombat27 You might wanna try the previous advice of windows firewall. Just turn it off altogether for testing only.
Try a port scanning site like GRC Shields Up to see if it shows the port open. Can imagine it would but can't hurt to try.
Were you able to access pfSense on 443?
-
@jarhead I still disagree that it has anything to do with this, but that said I have already tried and it made no difference.
-
@combat_wombat27 Just to be sure, when you changed to 4443, you did add that port to the URL, correct?
-
@jarhead Yes, https://externalip:4443
-
@combat_wombat27 Sorry, but had to ask.
Did you reboot pfSense after changing it's web port? Shouldn't have to but the NAT you have should be working also so... couldn't hurt.
Any chance you have anything else on your LAN you can forward a port to for testing? Just trying to see if NAT is working at all.
Had a weird trouble not too long ago and just recreating the NAT fixed it. I think that was because the user was changing so many things it got a little loopy but it did fix it. Worth a shot.
-
@jarhead I appreciate the reply. I rebooted the firewall at 5 PM yesterday and it has made no difference for me. I have also completely deleted and recreated the rules yesterday as well. Finally, I'm not sure what I would use on what port to help testing.
-
@combat_wombat27 so with any port forward you should validate traffic is actually getting to pfsense wan to be able to forward it.
Go to say can you see me . org, put in your port your wanting to forward.
Now sniff on pfsense wan for that port.. Do you see it get there?
example, testing with 4443
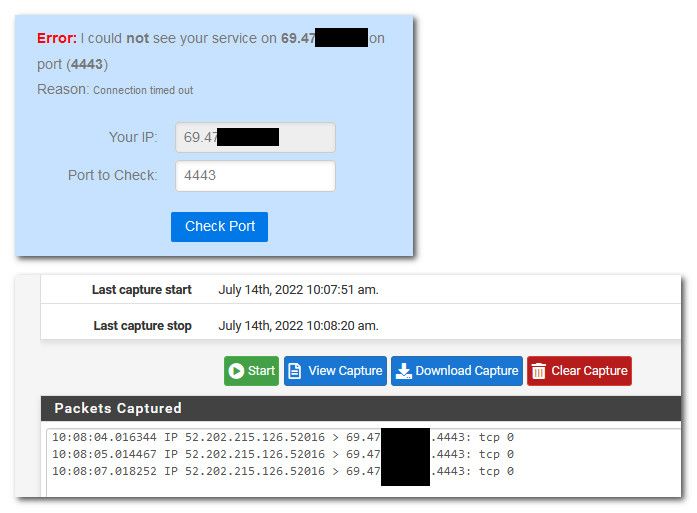
If you see the traffic get there, then sniff on your lan side interface.. Do you see pfsense send it on?
So here setup forward 4443 to box on my lan network 192.168.9.100
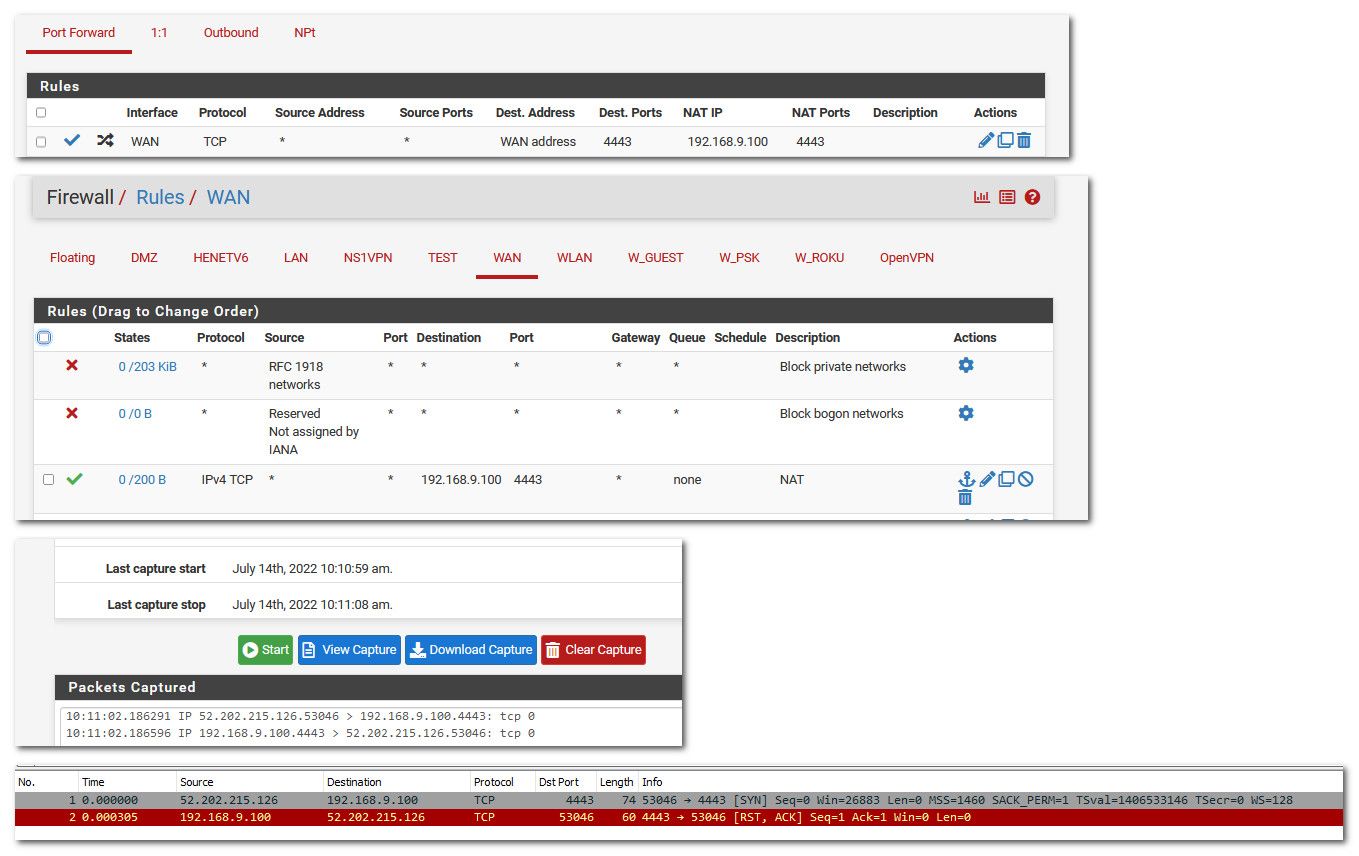
You can see that pfsense sent it on, now my pc answered with a RST what this is 9.100 saying go away, not listening on that port.. But the thing you want to be most interested in is that did pfsense send that traffic on to your 192.168 address you forwarded too. If it did, then pfsense did what you told it to do. And if not working, then not a pfsense issue, local firewall, wrong gateway on device your forwarding too, etc..
Also you can notice the firewall rule on wan is now seeing traffic 0/200 B means that rule has been evaluated. If your just seeing 0/0 after you have sent traffic this means that rule has not been even evaluated to let traffic in, maybe you have a floating rule? etc..