Searching for the fastest way to isolate each VLANs using pfSense firewall rules
-
@mauro-tridici just create an alias containing all your vlan-subnets. Block them all with a single rule.
If you need access to the pfsense device don't forget to add a rule on TOP to allow such access.
-
@mauro-tridici said in Searching for the fastest way to isolate each VLANs using pfSense firewall rules:
So, at the moment, since no particular rules have been defined, each VLANs hosts can reach each other.
Are you saying each host can access other hosts on the same vlan or other vlans?
With no rules applied all should be blocked except for the LAN interface. -
@heper many thanks, it is a very simple solution.
I appreciated it.
Do you know if we can also create a group of rules and "copy & paste" them on each interface? (maybe it's a too fanciful idea).Thanks,
Mauro -
@jarhead, in our case, each interface has a "accept any/any" very basic rule, just to test connectivity.
But, now, we are going to define the final firewall rules. Or, at least, we are thinking about them. -
@mauro-tridici You could also use interface groups.
https://docs.netgate.com/pfsense/en/latest/interfaces/groups.html
The rule processing order for user rules is:-
Floating rules
Interface group rules
Rules on the interface directly -
@mauro-tridici said in Searching for the fastest way to isolate each VLANs using pfSense firewall rules:
@jarhead, in our case, each interface has a "accept any/any" very basic rule, just to test connectivity.
But, now, we are going to define the final firewall rules. Or, at least, we are thinking about them.Gotcha, thought you had no rules yet.
So there's a button on the rules themselves, all the way to the right, that will copy the rule. Third icon.
Click that, then change the interface it's on to copy to different interfaces. -
If you remove the any to any, you have the default block behavior.
Then all you need to do is on all OPTs except for 9&10 is allow in from OPT9|10. I think an interface group of OPT1-8 and an interface group rule would do that.
Traffic out of OPT9 to OPT1 should wind up creating a state so the traffic back from OPT1 to OPT9 should be allowed back in.
OPT9 and OPT10 you could either put interface rules or just add them to the interface group.Basically what @NogBadTheBad is saying.
Simple rules are always easier to debug
-
Something like this.
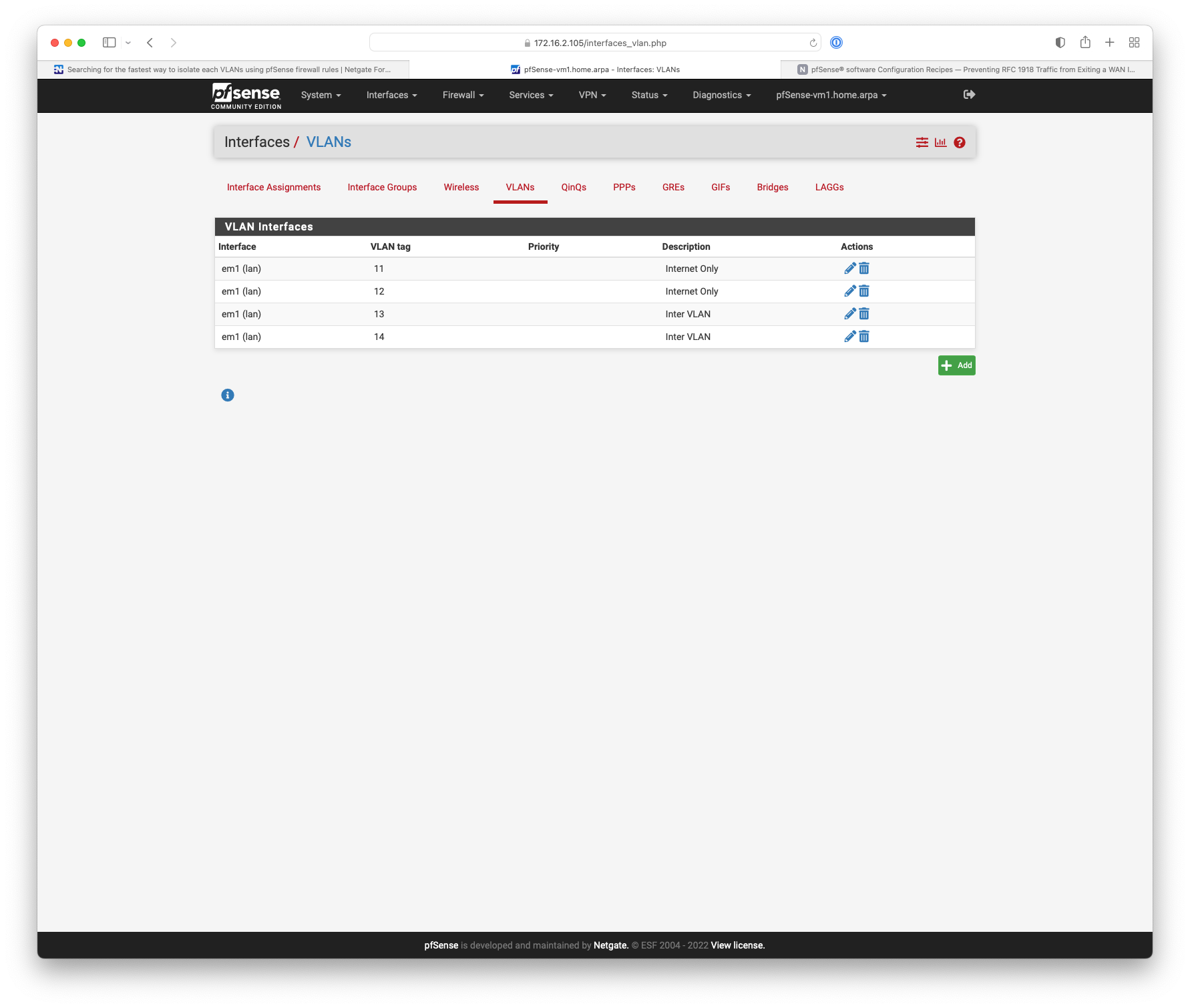
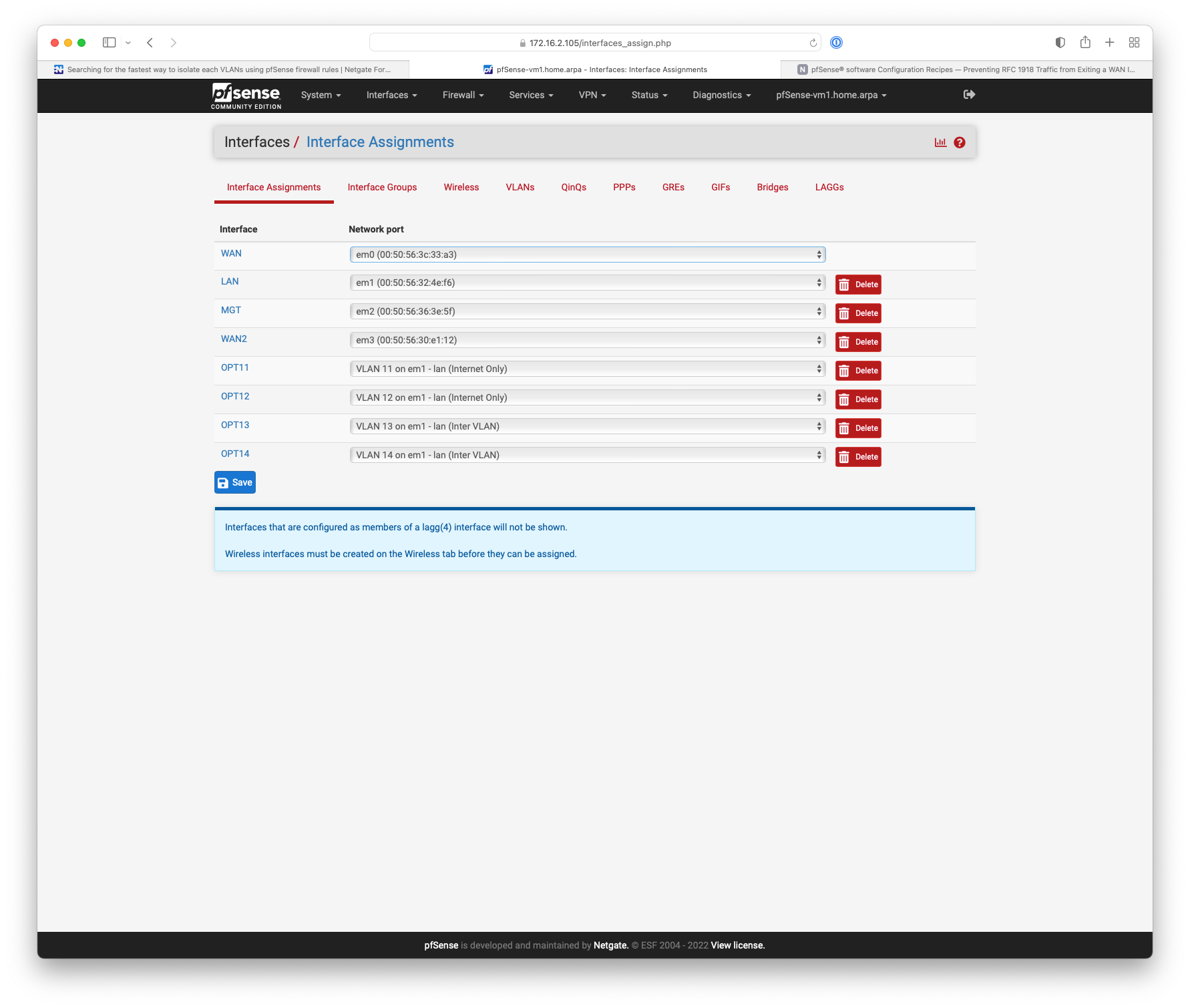
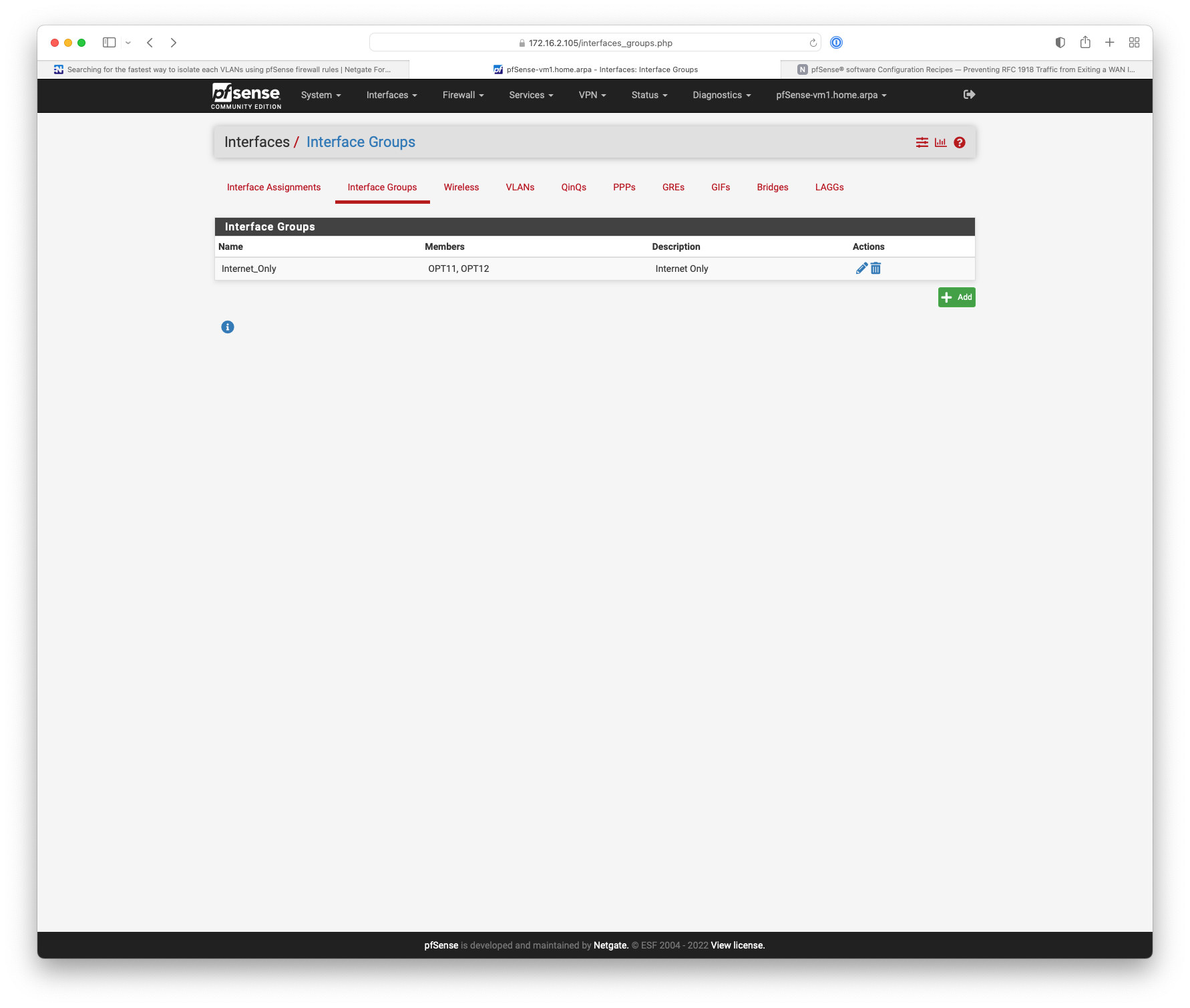
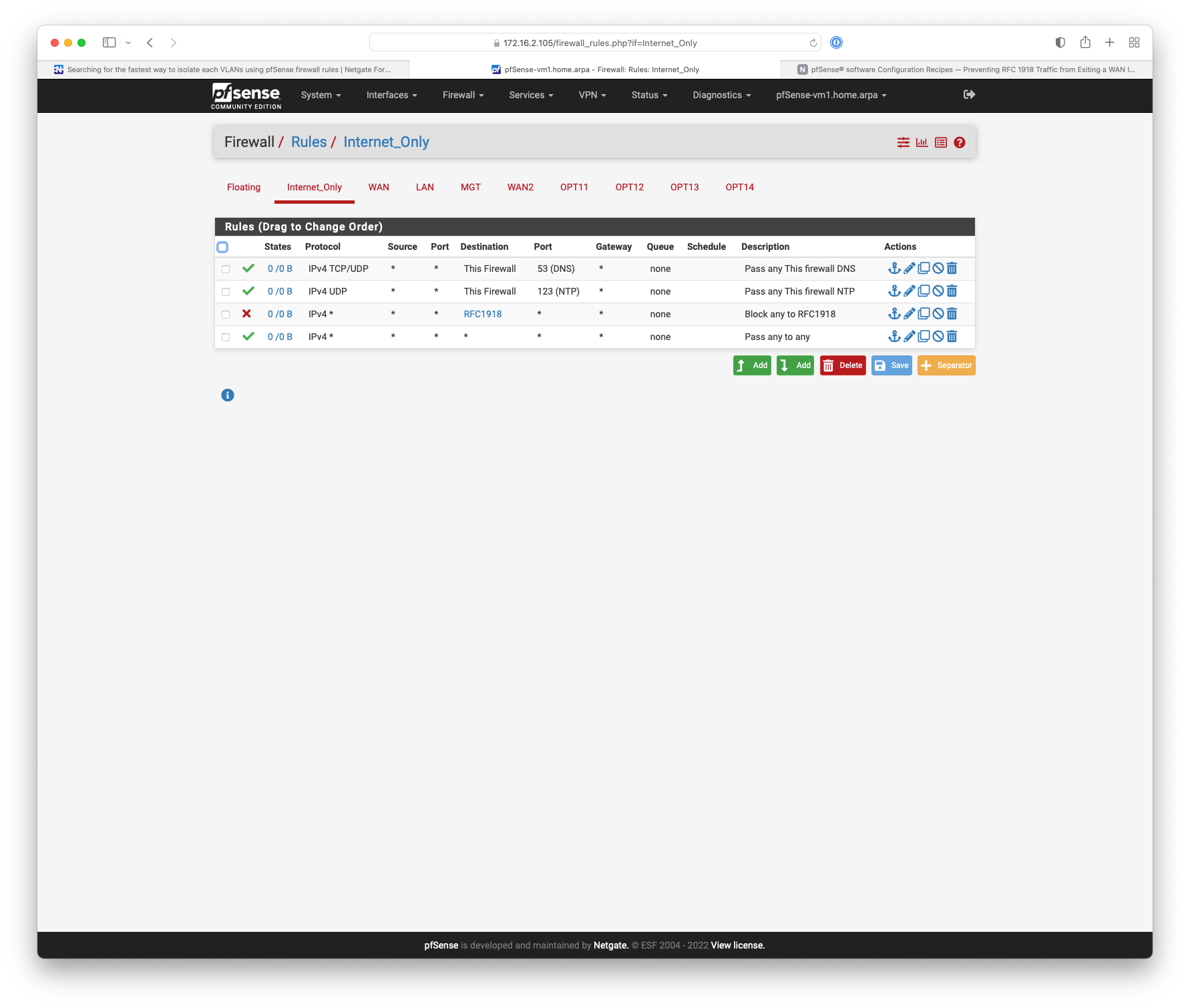
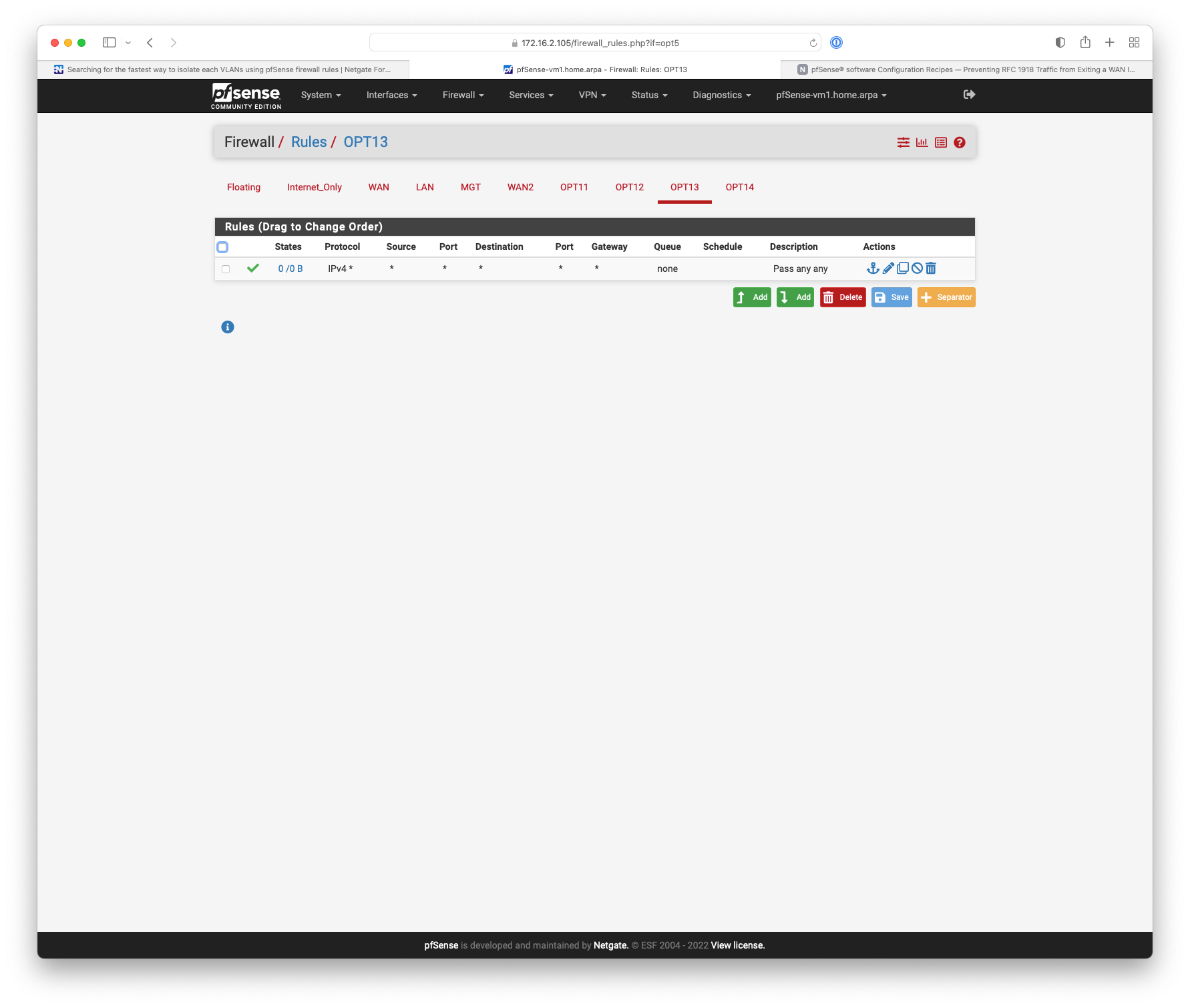
-
@nogbadthebad many thanks for your help. Appreciated.
-
@mauro-tridici No worries your welcome, I do however think you trying to simplify things may make it a bit harder for you in the long run

-
@nogbadthebad said in Searching for the fastest way to isolate each VLANs using pfSense firewall rules:
may make it a bit harder for you in the long run
I concur with this sentiment, vs looking for some shortcut on how few rules you can create to allow or block whatever you would be better off putting very explicit rules on each interface tab.
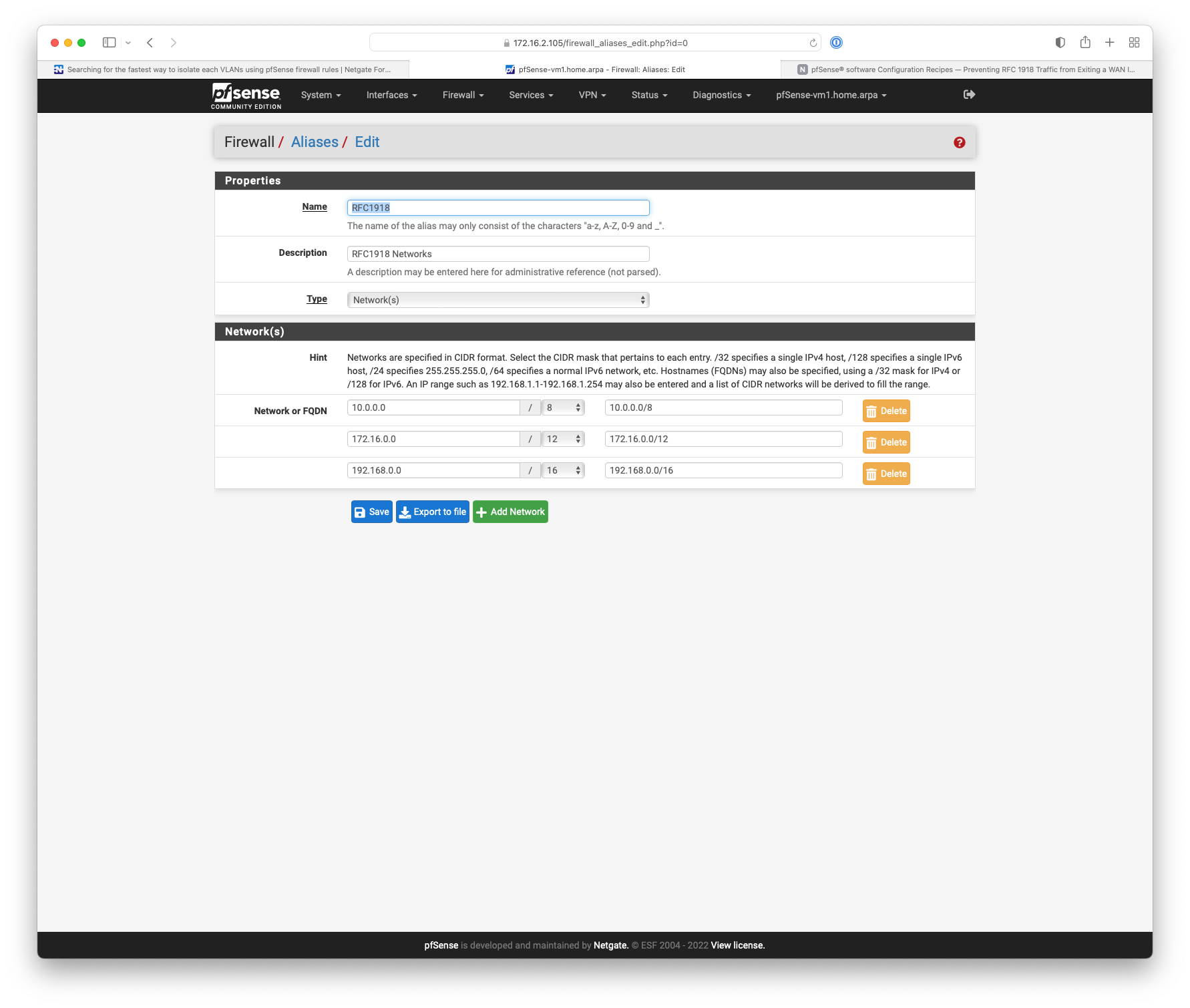
If your looking for simple way to block access to other vlans, assume all your vlans are rfc1918 is just create an alias that has all rfc1918 space. And use that alias on a rule on each interface to block access to your other vlans.