Site2Site Not Quite Working
-
Following:
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.htmlI set-up a server<-->remote site2site OpenVPN. Status > OpenVPN shows the connection is good on both ends.
I'm unable to access remote resouces (like the remote router webadmin page) from the server LAN.
Firewall logs on server initially showed default denied, so I added a firewall rule to allow traffic from the server LAN to the remote LAN (basically an any-any rule).
With the new rule in place, firewall log on server shows traffic is passed. However, I still am unable to load remote resources.
On the remote, there is an OpenVPN any-any rule (per the receipe linked above). Remote firewall logs don't show any traffic.
I think maybe the server side traffic isn't being routed to the VPN, but I'm not sure how to make that happen.
Do I need to assign an interface? The receipe doesn't mention the need to do this. I've tried anyway, but adding the interface then adding it the firewall rule gateway didn't work
-
@ximulate
Are both VPN endpoints the default gateway in their respective LAN?Did you configure the "Remote Networks" properly on each site?
On the remote, there is an OpenVPN any-any rule (per the receipe linked above). Remote firewall logs don't show any traffic.
Is logging enabled in the rule?
-
@viragomann
Yes, logging is enabledThe default gateway for both the "server" and "remote" firewalls is out to the internet via the WAN gateway.
I'm familar with using firewall rules to redirect traffic from the default gateway to alternative gateways. On the Server firewall, for the LAN, I tried each of the following (the ServerLAN is 192.168.11.0/24; remote LAN is 192.168.12.0/24)
Pass: Any, Any
Pass: Any, Destination (remote NET)
Pass: Any, Destination (remote NET), Gateway: (Interface:Remote)
Pass: Any, Destination (Network:192.168.12.0/24), Gateway:(Interface:Remote) -
@ximulate said in Site2Site Not Quite Working:
The default gateway for both the "server" and "remote" firewalls is out to the internet via the WAN gateway.
I'm familar with using firewall rules to redirect traffic from the default gateway to alternative gateways.The outside gateway is not relevant here. The question is if the VPN endpoint is the default gateway on the machines, which you want to communicate over the VPN.
Redirecting to the OpenVPN endpoint from the gateway will not work.
So maybe you can provide a network map for better understanding.
-
Ahh, OK I understand your question (I think). The default gateway of the machines is the network IP of the firewall. In DHCP Server configuration, I just leave the Gateway empty so it uses the default firewall interface. Machines on each LAN still need internet access through the WAN.
"Server" Network
LAN network: 192.168.11.0/24
pfSense Firewall: 192.168.11.1
DHCP Server: 192.168.11.221 - 192.168.11.250
OpenVPN Tunnel: 10.3.101.0/24
OpenVPN Local network(s): 192.168.11.0/24, 192.168.12.0/24
OpenVPN Remote network(s): 192.168.12.0/24Remote (Client) Network
LAN network: 192.168.12.0/24
pfSense Firewall: 192.168.12.1
DHCP Server: 192.168.12.221 - 192.168.12.250
OpenVPN Tunnel: (the receipe states to leave at default, which is empty)
OpenVPN Remote network(s): (the receipe states to leave at default, which is empty) -
@ximulate said in Site2Site Not Quite Working:
"Server" Network
LAN network: 192.168.11.0/24
OpenVPN Tunnel: 10.3.101.0/24
OpenVPN Local network(s): 192.168.11.0/24, 192.168.12.0/24192.168.11.0/24 is the tunnel network. This should not be stated at "Local network(s)".
Remote (Client) Network
OpenVPN Remote network(s): (the receipe states to leave at default, which is empty)You may stated the server site LAN here anyway for proper routing.
Check Diagnostic > Routes on both sites and look if the routes are set properly.The quoted pfSense docs section describes a site-to-multiple-site VPN. This requires to configure Client Specific Overrides for each client. Did you do this?
If you have a single client only CSO is not needed, but you should rather change the tunnel network to a /30 on the server. -
@ximulate
192.168.11.0/24 is the LAN network for the machines on the service side of the VPN. Here is a screen shot of it from IPv4 Routes in Diagnositics / Routes:
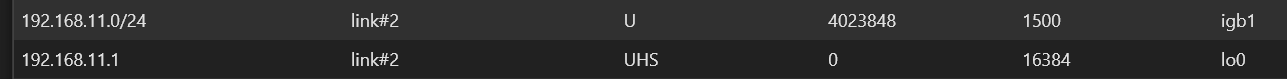
Theres nothing else listed related to the LAN network or VPN tunnel, not any item related to the client/remote LAN (192.168.12.0/24)Yes, I did set-up Client Specific Overrides. Default settings, except:
Server List: (selected site2site VPN)
IPv4 Remote Network/s: 192.168.12.0/24Client / Remote Network screenshot of IPv4 Routes in Diagnostics / Routers
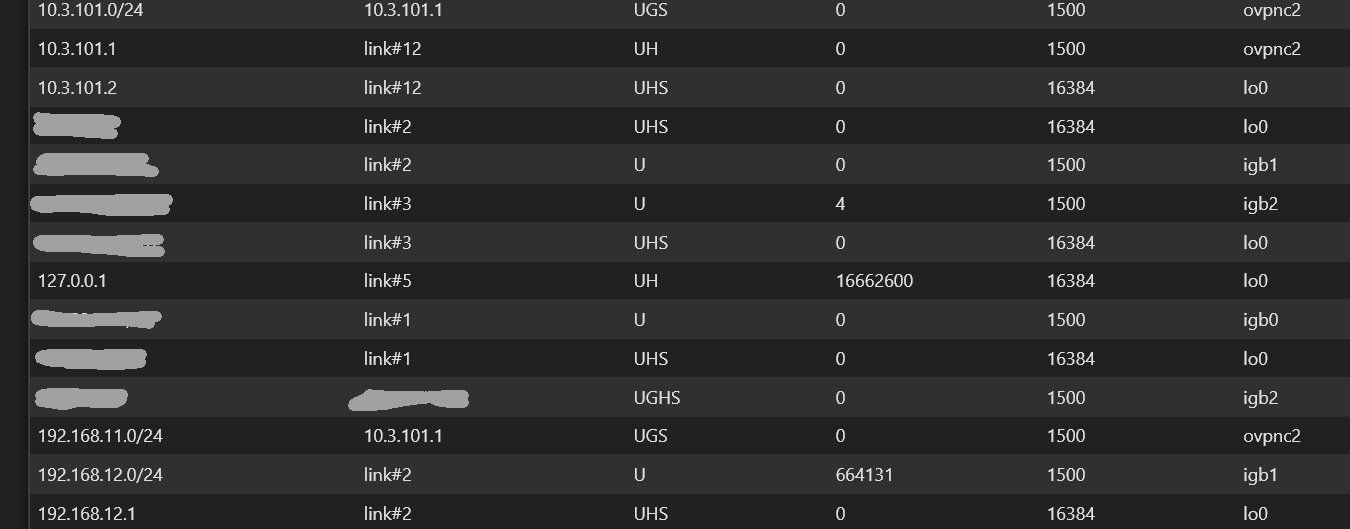
I was trying to start small, but just setting up a single client
-
@ximulate said in Site2Site Not Quite Working:
192.168.11.0/24 is the LAN network for the machines on the service side of the VPN.
Correct. My mistake.
Yes, I did set-up Client Specific Overrides. Default settings, except:
Server List: (selected site2site VPN)
IPv4 Remote Network/s: 192.168.12.0/24So you should see a route for 192.168.12.0/24 pointing to the client, when the connection is established. If not, the CSO presumably is not applied.
I was trying to start small, but just setting up a single client
The multi-purpose server setup with more complicated. I's only recommend that if you really intend to connect multiple clients later.
If you to it with CSO check the OpenVPN log. There should be an entry for the client connecting and if the CSO is applied. Otherwise possibly the server does not determine the client.
In the server settings you can decide how to identify the client by the "Username as Common Name" option. According to this settings the "Common Name" in the CSO has to match either the client certificates common name or the clients user name.
-
Thank you for your continued help with this.
I restarted the client connection, and now see a route on the Server to the client LAN (192.168.12.0/24), but connection is still failing (still unable to load resources on client side from server side. For example, from a machine (192.168.11.11) on the server LAN (192.168.11.0/24), I'm unable to access the web admin page of the client router 192.168.12.1)
In the OpenVPN logs on the Client, I see:
openvpn 52317 ERROR: FreeBSD route add command failed: external program exited with error status: 1Routes for server
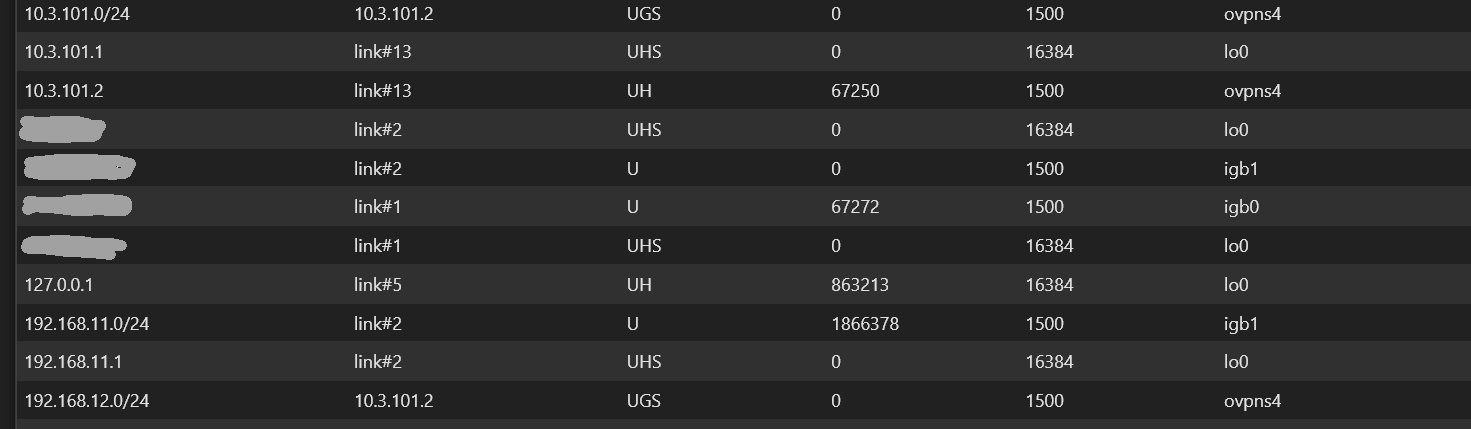
Routes for client
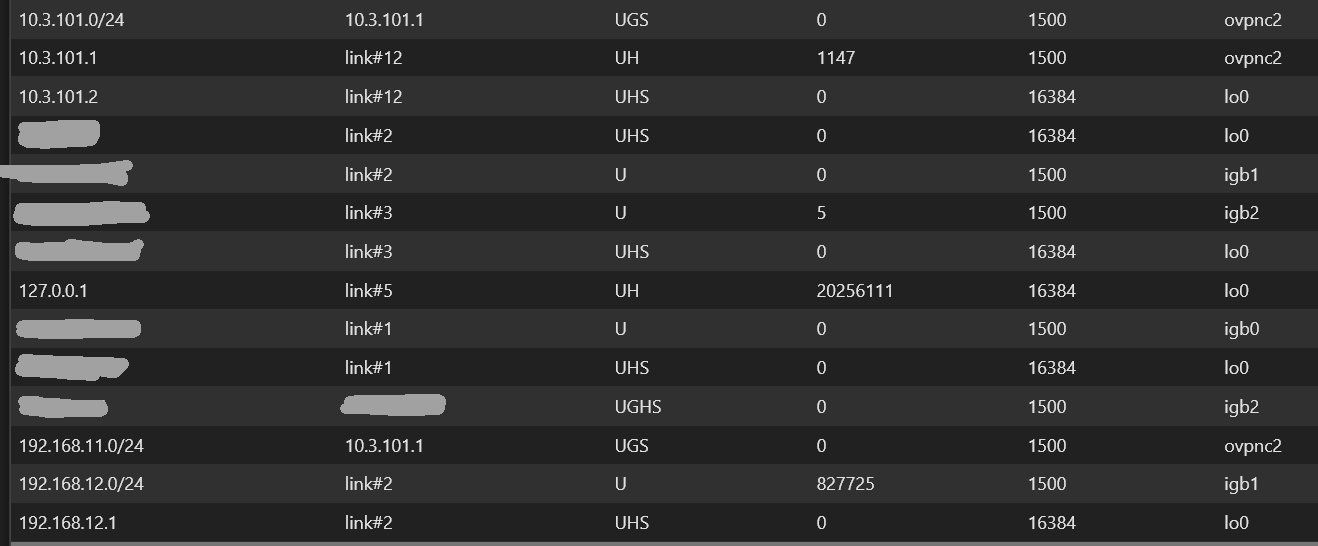
-
@ximulate
As mentioned, check the OpenVPN log on the server to find out if the CSO is applied properly.
Routing to clients on an access server with CSO is somewhat more complicated. pfSense has to add the route and additionally OpenVPN has to add a route for the client internally (iroute), since it's capable to handle multiple clients.In the OpenVPN logs on the Client, I see:
openvpn 52317 ERROR: FreeBSD route add command failed: external program exited with error status: 1
Some more information on this in the log?
Since the client has added the route, it should work from the point of the client. But possibly there is something else wrong in the settings.Also ensure that you need a firewall rule permitting the access on all incoming interfaces. So for access from the clients LAN to the servers LAN, these are: clients LAN, servers OpenVPN
-
As mentioned, check the OpenVPN log on the server to find out if the CSO is applied properly.
The above mentioned settings were input into CSO, and saved. Not sure what else to do. I don't see anything in the log to confirm CSO is applied
server OpenVPN log shows the following, repeatedly:
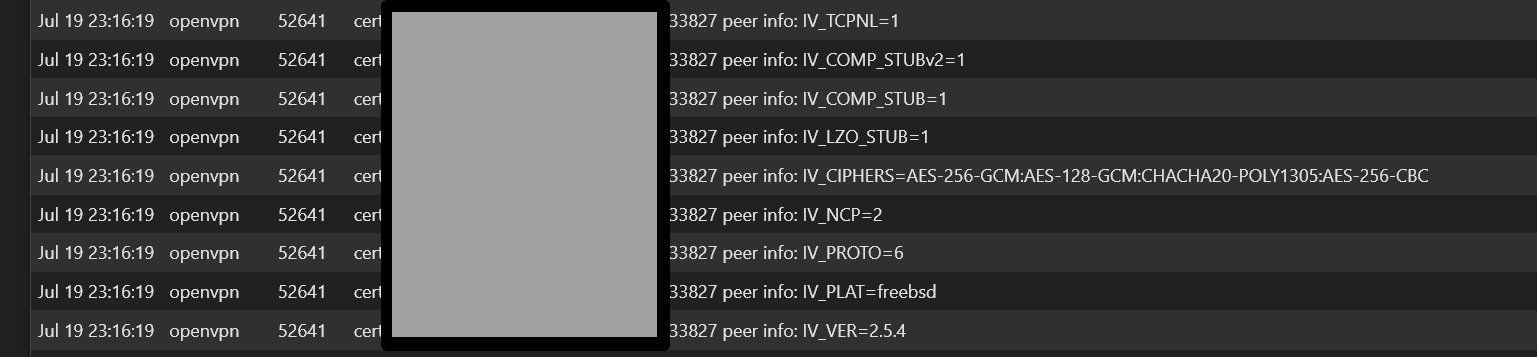
Firewall Rules on both server and client for OpenVPN:
Pass IPv4 Source: * Destination: *On server, firewall rules for LAN include:
Pass IPv4 Source: *, Destination 192.168.12.0/24 Port:* Gateway: * -
Some more information on this in the log?
I don't see anymore information regarding this in the log.
-
@ximulate
Okay, even noticed that the CSO part is not logged with default log level.
So I changed the log level in the server setting to 3, then I got the info:
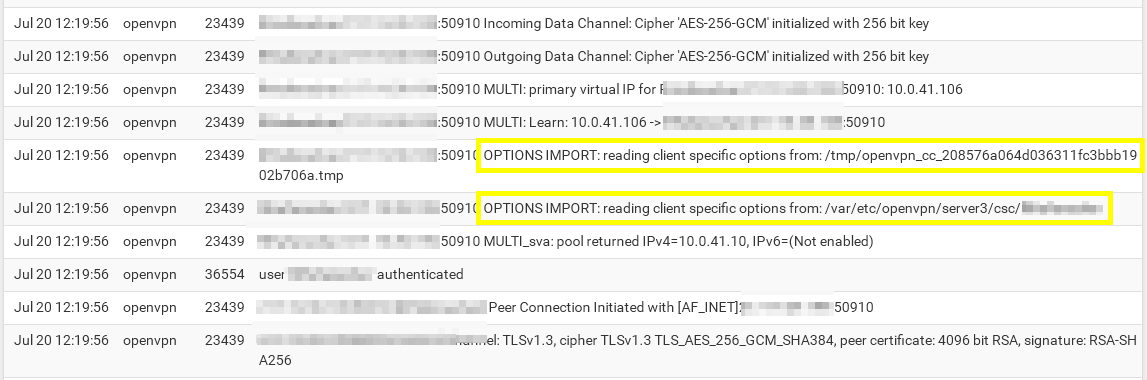
-
@viragomann
Client side OpenVPN log, at verbosity 3:
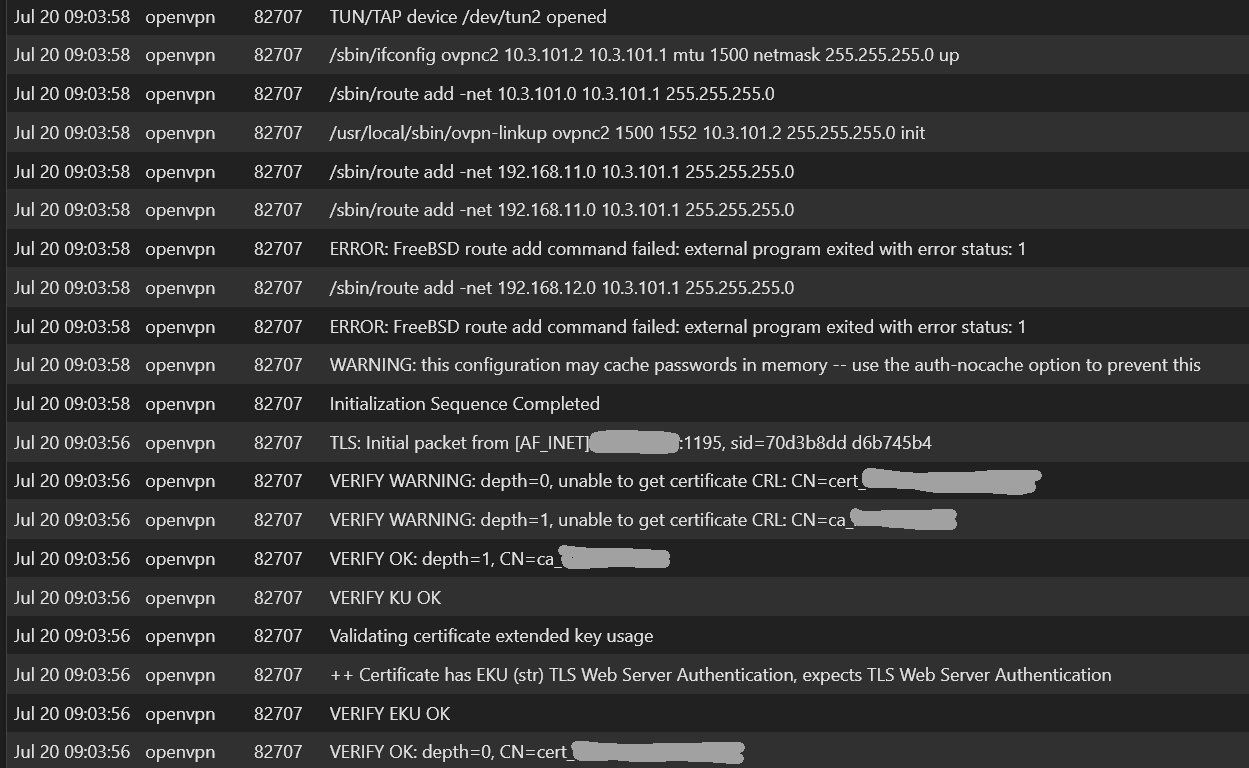
two things stand out to me:
Error: FreeBSD rout add command failedI see this warning on the server side OpenVPN logs also:
Verify Warning: unable to get certificate -
@ximulate said in Site2Site Not Quite Working:
Client side OpenVPN log, at verbosity 3:
The server log is way more of interesting here. The CSO part can only be found in the server log.
Error: FreeBSD rout add command failed
This is due the server is pushing a route for the clients LAN network, which cannot be added naturally.
That's why I don't like this setup method as mentioned above. I'd rather add the remote networks in the client config.
However, it should work anyway.Verify Warning: unable to get certificate
The whole warning says "Verify Warning: unable to get certificate CRL" (Certificate Revocation List).
This is normal. The client complains that he cannot pull the CRL, since it is not provided in the internet. -
@viragomann
One the Server side verbosity 3, I'm now see this:
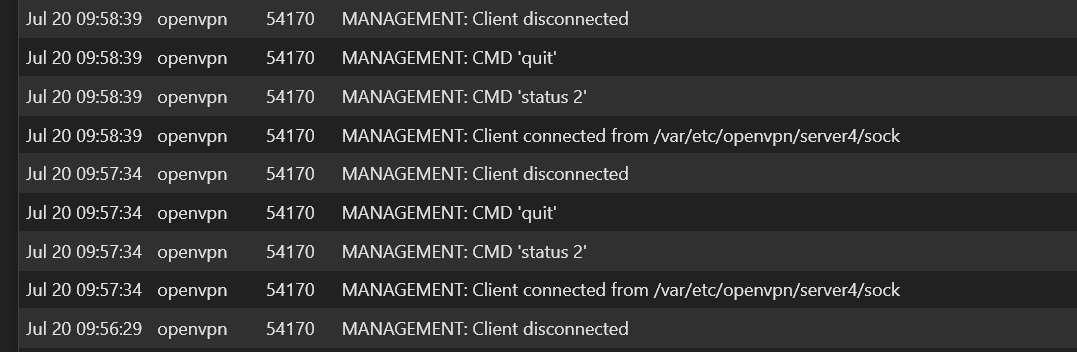
-
@ximulate
Need to see the section, when the client establishes the connection. -
Server side logs (after reboot of client router)...
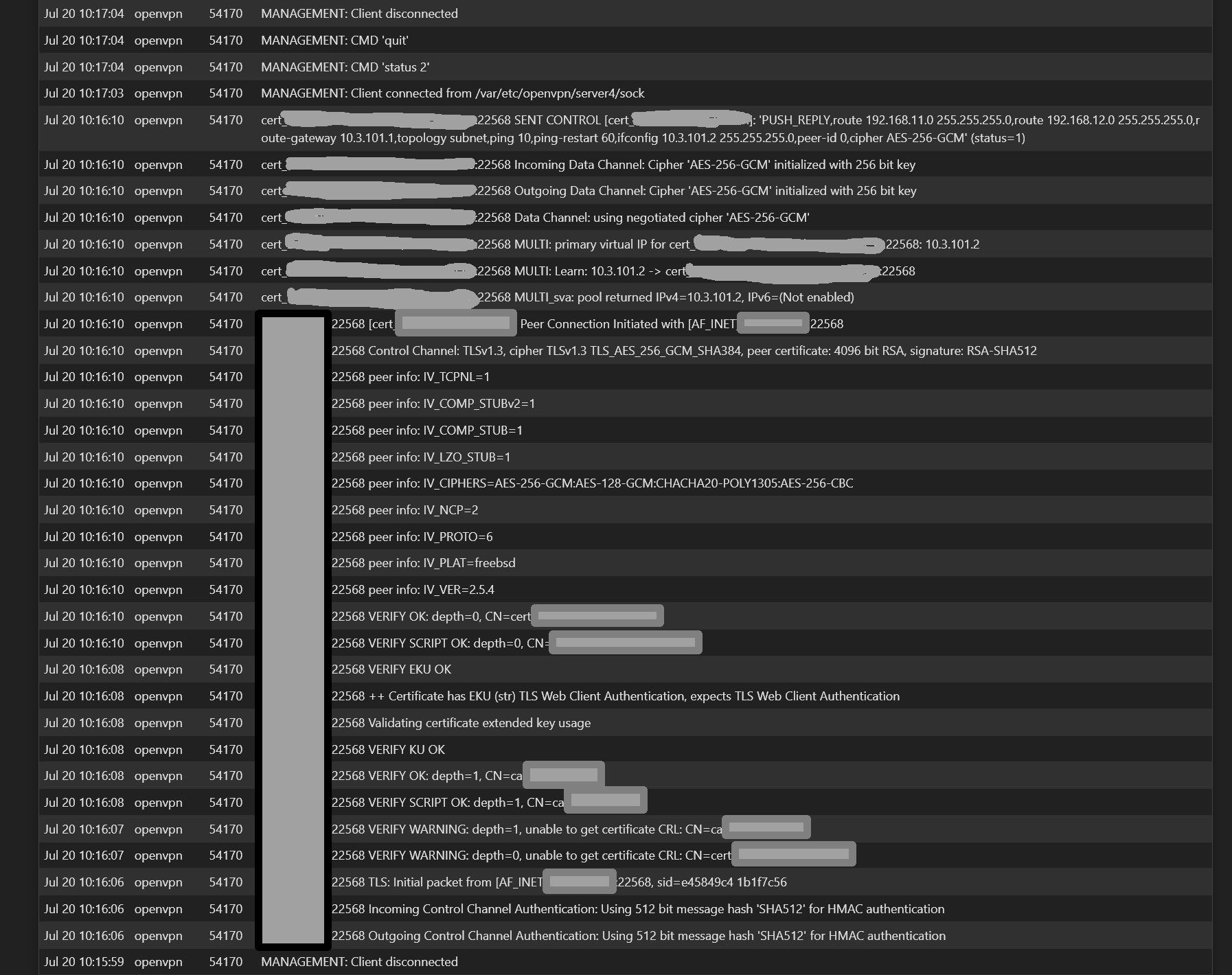
At
Jul 20 10:17:04, MANAGEMENT: .......Those management messages repeat as shown in previous post
-
@ximulate
So there is no note of the CSO in the log. Hence the route within OpenVPN won't work.As mentioned above in post #8 check if the common name in the CSO and server settings are correct.
-
@viragomann
That was it! Its now working. Thank you for your help and patience