IPSec won't ping from Site A -> B until B has pinged to A
-
I have an IPSec VPN configured as per the documentation - https://docs.netgate.com/pfsense/en/latest/recipes/ipsec-s2s-psk.html
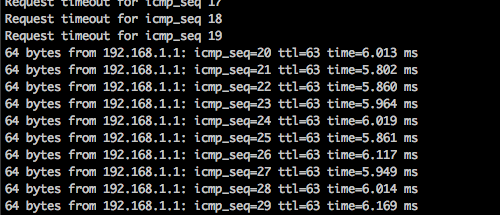
However, I have noticed that for some reason, when pinging from site A to B (192.168.30.10 -> 192.168.1.1) the pings timeout. That is until I ping from Site B PFSense to any IP in the 192.168.30/24 subnet.
What's stranger is I can see the IPSec status page showing packets sent, I'm just not getting anything back.
As soon as I ping from Site B to Site A, Site A's pings instantly begin getting responses - almost as if it doesn't know the route to take until established by site B. After a short while with no traffic flowing from site B to site A the connection is lost again. Any ideas why this would be the case?
Thanks
-
@chrispage can you post screenshots of the P1 and P2 configuration on both sides as well as your firewall rules? Also is either side behind NAT?
-
@gabacho4 I think I may have solved it, off the back of your message I decided to abstract out all of my firewall rules and now it seems to be responding as I'd expect.
I'll let you know if it still isn't solved, but in the meantime, appreciate your help!
-
@gabacho4 OK, that didn't solve it. So to establish pinging from Site A -> B I first have to ping Site B -> A. The second I ping Site A from B, firewall traffic instantly starts flowing from A -> B:
As far as firewall setup, I've got UDP ports 500 & 4500 whitelisted for each respective site on the WAN interface.
Then on the IPSec interface:
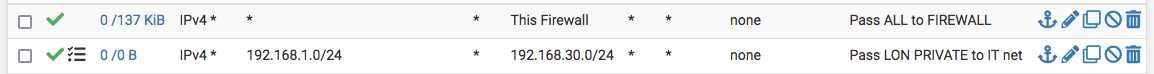
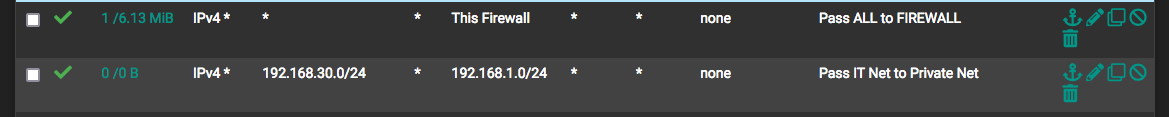
Site A
Site B
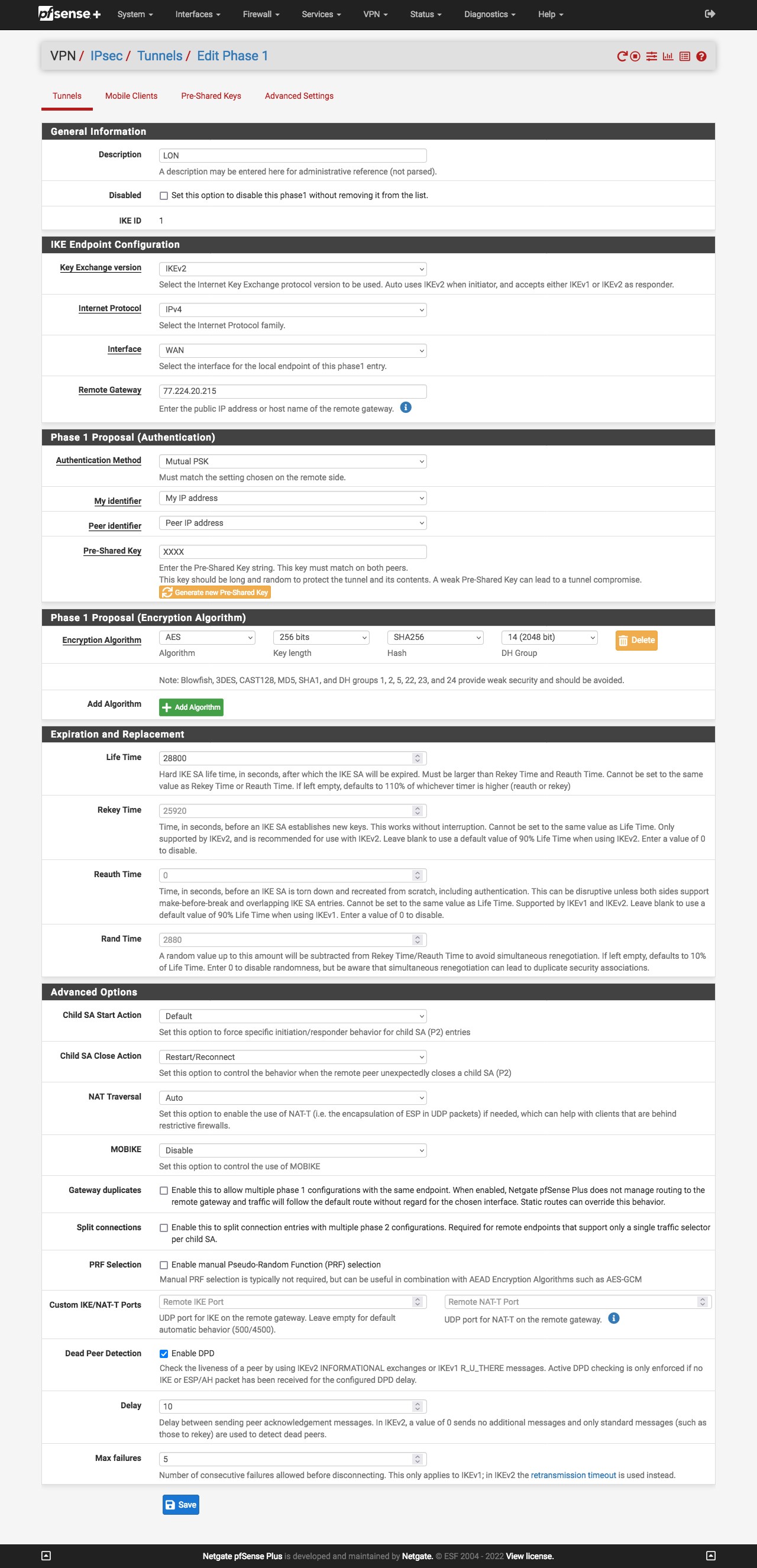
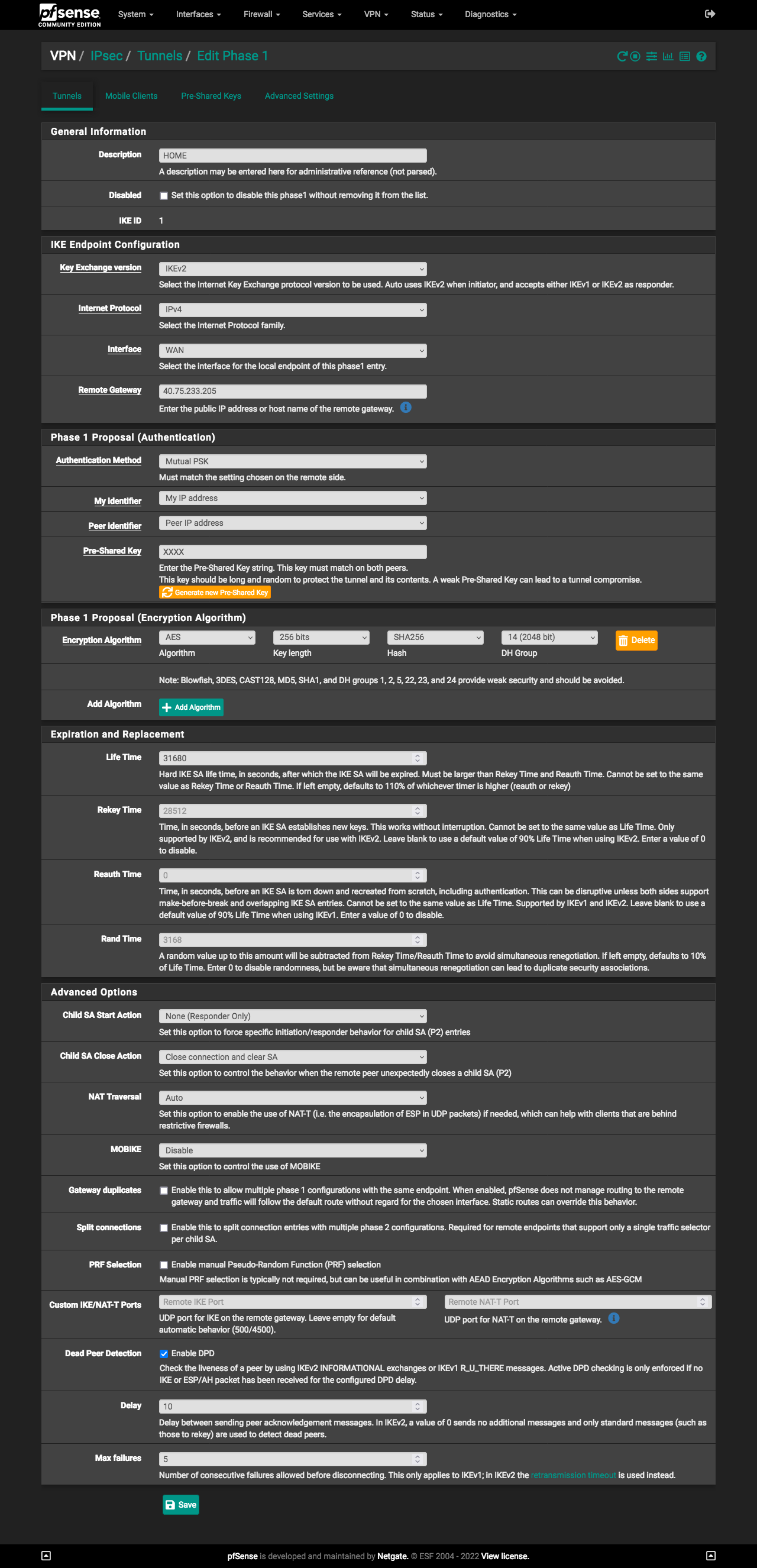
Site A - phase 1
Site A - phase 2
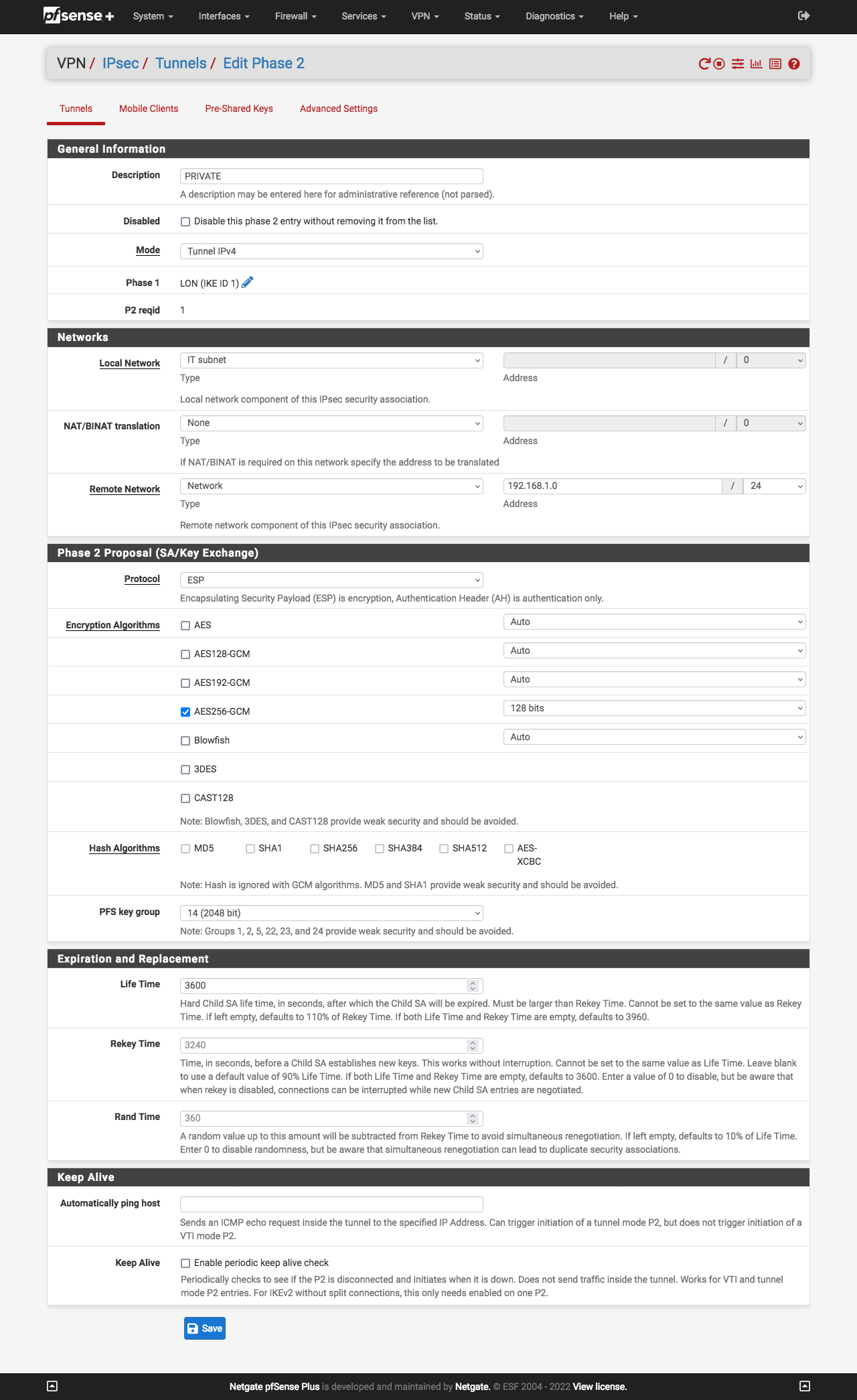
Site B - phase 1
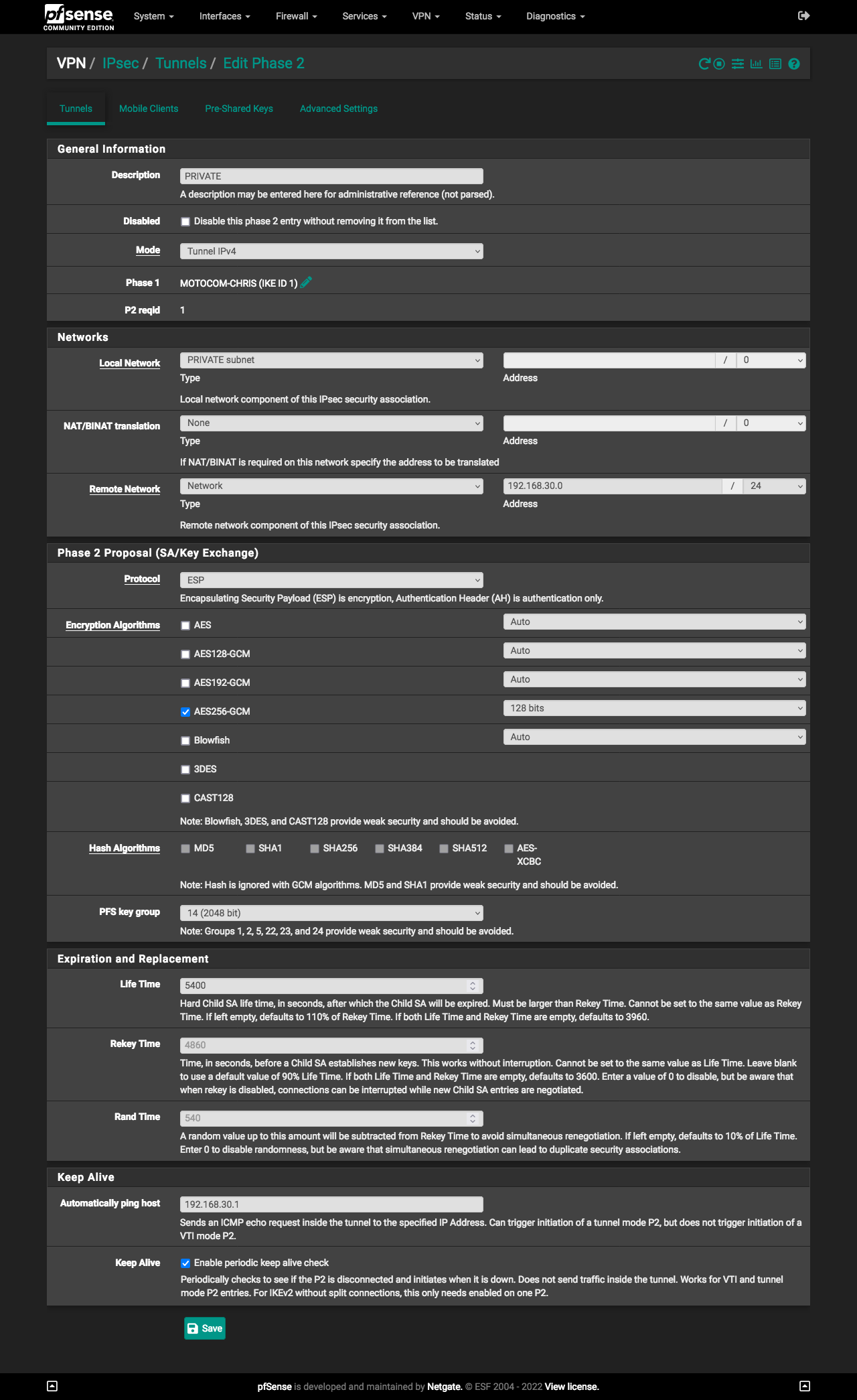
Site B - phase 2
Thanks,
Chris. -
Chris
So first things first. You are going to want to (somewhat urgently) go back and edit your screenshots and remove your WAN IP. Don't want to give that to the world. Danger Will Robinson! Danger!
One observation for consideration - if your system support GCM algorithms, as it seemingly does based on your P2 config, why not set your P1 encryption algorithm on both sides to AES256-GCM instead of AES-256?
In order to remove any extra variables, in your IPSEC firewall rules, put an accept all rule at the bottom for both site A and B. This may not be how you want it to be when all is said and done but this will enable us to first determine all is working well first and then you can tighten things up. It will also allow you to see if any other traffic is hitting that firewall ruleset.
I also note that your Site A and Site B, P1 Expiration and Replacement (Life Time, Rekey Time, and Rand Time) are different. These should match! Adjust so that they are the same on both sides.
You have the same issue with the settings for the P2. Life, Rekey, and Rand Times should be the same for both sites.
For both the Site A and Site B, in the Advanced Options of the P1, try changing the Child SA Start Action and Child SA Close Action both to default. I believe the way you have things now is what is causing your connectivity issues.
For both the Site A and Site B, in the P2, at the bottom in the Keep Alive section, check the "enable periodic keep alive check."
Make all those changes and then let's see where we are at. Before you do so, will you also provide me a screenshot of your IPSEC logs? (Status, -> System Logs -> IPSEC).
-
BTW - per your note that you have whitelisted ports 500 and 4500 on the WAN, you don't need to do that. pfSense does that automatically for you unless you disabled that setting. Please advise.
-
@gabacho4 Thanks for your response!
So first things first. You are going to want to (somewhat urgently) go back and edit your screenshots and remove your WAN IP. Don't want to give that to the world. Danger Will Robinson! Danger!
It's ok, I got some random ones online and swapped them out, so they are not my actual WAN IP's

One observation for consideration - if your system support GCM algorithms, as it seemingly does based on your P2 config, why not set your P1 encryption algorithm on both sides to AES256-GCM instead of AES-256?
Good question. I was having issues (the same as I am now) so I went back to the drawing board and followed the PFSense setup guide in its entirety which defaulted to this setup.
I also note that your Site A and Site B, P1 Expiration and Replacement (Life Time, Rekey Time, and Rand Time) are different. These should match! Adjust so that they are the same on both sides.
This is also the suggestion of the PFSense setup guide, I'll leave these for now and follow the advice below.
For both the Site A and Site B, in the Advanced Options of the P1, try changing the Child SA Start Action and Child SA Close Action both to default. I believe the way you have things now is what is causing your connectivity issues.
For both the Site A and Site B, in the P2, at the bottom in the Keep Alive section, check the "enable periodic keep alive check."I'll make these changes.
BTW - per your note that you have whitelisted ports 500 and 4500 on the WAN, you don't need to do that. pfSense does that automatically for you unless you disabled that setting. Please advise.
I didn't know this - useful, thanks!
Chris.
-
Early signs are looking good - I can instantly ping as soon as the tunnel is established. I'll keep an eye and leave it for a bit to see what happens...
Appreciate your help on this!
-
@chrispage easy day. I don’t know why but I’m kind of a nerd when it comes to IPSec. It’s a pain in the butt sometimes but I like to take advantage of hardware acceleration. WireGuard is pretty awesome if you haven’t tried that and is far simpler. But it doesn’t leverage any hardware acceleration so it can have an impact on cpu depending on what your hardware is.
I don’t recall in the documentation where it says to have different values for life time etc. Can you point that out to me? I’m fairly confident I’ve seen guidance stating the opposite.
-
Just reviewed the documentation, so the time values were automatically generated by your router or were they ones you created? I see in the documentation:
Life Time
The default 28800 is OK for this endpoint.The other lifetime-related values (Rekey Time, Reauth Time, Rand Time) should be left at their defaults on this endpoint as they are automatically calculated as the correct values.
I’ve never seen other values before but if it’s hardware dependent then I guess that would make sense.
-
Nevermind..just found the guidance in the documentation. Man, you learn something every day. I’ll have to adjust my setup now!
-
@gabacho4 well your recommendations seem to be working for me so for now I'll be sticking with that! So far so good, still happily pinging away!
I appreciate your IPSec nerdiness - it's certainly helped me out so thanks for that ;)
-
@gabacho4 right, so working from home again today and noticed the same thing is happening again (ah man!)
If I keep pinging it, phase 2 tunnel remains open. However if I leave it for a minute or so, it stops responding to traffic from site a -> b.
Eventually either I manually initiate a ping from site b -> site a or IPSec keepalive ping runs and brings the tunnel back to life.
As far as logs go, there's nothing I wouldn't expect on either end, as below...
2022-07-26 09:17:42.639596+01:00 charon 5863 12[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:17:42.639664+01:00 charon 5863 12[ENC] <con1|724> parsed INFORMATIONAL request 16 [ ]
2022-07-26 09:17:42.639720+01:00 charon 5863 12[ENC] <con1|724> generating INFORMATIONAL response 16 [ ]
2022-07-26 09:17:42.639767+01:00 charon 5863 12[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:17:52.691369+01:00 charon 5863 13[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:17:52.691441+01:00 charon 5863 13[ENC] <con1|724> parsed INFORMATIONAL request 17 [ ]
2022-07-26 09:17:52.691478+01:00 charon 5863 13[ENC] <con1|724> generating INFORMATIONAL response 17 [ ]
2022-07-26 09:17:52.691534+01:00 charon 5863 13[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:01.845443+01:00 charon 5863 08[IKE] <con1|724> sending DPD request
2022-07-26 09:18:01.845486+01:00 charon 5863 08[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:18:01.845514+01:00 charon 5863 08[IKE] <con1|724> activating new tasks
2022-07-26 09:18:01.845543+01:00 charon 5863 08[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:18:01.845572+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL request 13 [ ]
2022-07-26 09:18:01.845640+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:01.852339+01:00 charon 5863 08[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:01.852393+01:00 charon 5863 08[ENC] <con1|724> parsed INFORMATIONAL response 13 [ ]
2022-07-26 09:18:01.852417+01:00 charon 5863 08[IKE] <con1|724> activating new tasks
2022-07-26 09:18:01.852452+01:00 charon 5863 08[IKE] <con1|724> nothing to initiate
2022-07-26 09:18:11.704381+01:00 charon 5863 05[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:11.704452+01:00 charon 5863 05[ENC] <con1|724> parsed INFORMATIONAL request 18 [ ]
2022-07-26 09:18:11.704489+01:00 charon 5863 05[ENC] <con1|724> generating INFORMATIONAL response 18 [ ]
2022-07-26 09:18:11.704532+01:00 charon 5863 05[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:20.912446+01:00 charon 5863 05[IKE] <con1|724> sending DPD request
2022-07-26 09:18:20.912527+01:00 charon 5863 05[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:18:20.912576+01:00 charon 5863 05[IKE] <con1|724> activating new tasks
2022-07-26 09:18:20.912636+01:00 charon 5863 05[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:18:20.912689+01:00 charon 5863 05[ENC] <con1|724> generating INFORMATIONAL request 14 [ ]
2022-07-26 09:18:20.912803+01:00 charon 5863 05[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:20.919686+01:00 charon 5863 05[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:20.919751+01:00 charon 5863 05[ENC] <con1|724> parsed INFORMATIONAL response 14 [ ]
2022-07-26 09:18:20.919777+01:00 charon 5863 05[IKE] <con1|724> activating new tasks
2022-07-26 09:18:20.919812+01:00 charon 5863 05[IKE] <con1|724> nothing to initiate
2022-07-26 09:18:30.799984+01:00 charon 5863 05[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:30.800058+01:00 charon 5863 05[ENC] <con1|724> parsed INFORMATIONAL request 19 [ ]
2022-07-26 09:18:30.800105+01:00 charon 5863 05[ENC] <con1|724> generating INFORMATIONAL response 19 [ ]
2022-07-26 09:18:30.800149+01:00 charon 5863 05[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:39.937634+01:00 charon 5863 16[IKE] <con1|724> sending DPD request
2022-07-26 09:18:39.937679+01:00 charon 5863 16[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:18:39.937711+01:00 charon 5863 16[IKE] <con1|724> activating new tasks
2022-07-26 09:18:39.937740+01:00 charon 5863 16[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:18:39.937788+01:00 charon 5863 16[ENC] <con1|724> generating INFORMATIONAL request 15 [ ]
2022-07-26 09:18:39.937870+01:00 charon 5863 16[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:39.945121+01:00 charon 5863 16[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:39.945170+01:00 charon 5863 16[ENC] <con1|724> parsed INFORMATIONAL response 15 [ ]
2022-07-26 09:18:39.945192+01:00 charon 5863 16[IKE] <con1|724> activating new tasks
2022-07-26 09:18:39.945231+01:00 charon 5863 16[IKE] <con1|724> nothing to initiate
2022-07-26 09:18:49.924878+01:00 charon 5863 14[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:49.924960+01:00 charon 5863 14[ENC] <con1|724> parsed INFORMATIONAL request 20 [ ]
2022-07-26 09:18:49.925006+01:00 charon 5863 14[ENC] <con1|724> generating INFORMATIONAL response 20 [ ]
2022-07-26 09:18:49.925049+01:00 charon 5863 14[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:59.927890+01:00 charon 5863 10[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:59.927960+01:00 charon 5863 10[ENC] <con1|724> parsed INFORMATIONAL request 21 [ ]
2022-07-26 09:18:59.927995+01:00 charon 5863 10[ENC] <con1|724> generating INFORMATIONAL response 21 [ ]
2022-07-26 09:18:59.928038+01:00 charon 5863 10[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:09.994610+01:00 charon 5863 10[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:09.994721+01:00 charon 5863 10[ENC] <con1|724> parsed INFORMATIONAL request 22 [ ]
2022-07-26 09:19:09.994778+01:00 charon 5863 10[ENC] <con1|724> generating INFORMATIONAL response 22 [ ]
2022-07-26 09:19:09.994849+01:00 charon 5863 10[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:19.996800+01:00 charon 5863 08[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:19.996884+01:00 charon 5863 08[ENC] <con1|724> parsed INFORMATIONAL request 23 [ ]
2022-07-26 09:19:19.996928+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL response 23 [ ]
2022-07-26 09:19:19.997050+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:30.000328+01:00 charon 5863 11[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:30.000429+01:00 charon 5863 11[ENC] <con1|724> parsed INFORMATIONAL request 24 [ ]
2022-07-26 09:19:30.000496+01:00 charon 5863 11[ENC] <con1|724> generating INFORMATIONAL response 24 [ ]
2022-07-26 09:19:30.000586+01:00 charon 5863 11[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:40.003944+01:00 charon 5863 12[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:40.004053+01:00 charon 5863 12[ENC] <con1|724> parsed INFORMATIONAL request 25 [ ]
2022-07-26 09:19:40.004132+01:00 charon 5863 12[ENC] <con1|724> generating INFORMATIONAL response 25 [ ]
2022-07-26 09:19:40.004206+01:00 charon 5863 12[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:50.096681+01:00 charon 5863 08[IKE] <con1|724> sending DPD request
2022-07-26 09:19:50.096726+01:00 charon 5863 08[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:19:50.096762+01:00 charon 5863 08[IKE] <con1|724> activating new tasks
2022-07-26 09:19:50.096799+01:00 charon 5863 08[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:19:50.096829+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL request 16 [ ]
2022-07-26 09:19:50.096897+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:50.096965+01:00 charon 5863 06[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:50.097004+01:00 charon 5863 06[ENC] <con1|724> parsed INFORMATIONAL request 26 [ ]
2022-07-26 09:19:50.097035+01:00 charon 5863 06[ENC] <con1|724> generating INFORMATIONAL response 26 [ ]
2022-07-26 09:19:50.097076+01:00 charon 5863 06[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:50.106546+01:00 charon 5863 06[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:50.106593+01:00 charon 5863 06[ENC] <con1|724> parsed INFORMATIONAL response 16 [ ]
2022-07-26 09:19:50.106616+01:00 charon 5863 06[IKE] <con1|724> activating new tasks
2022-07-26 09:19:50.106651+01:00 charon 5863 06[IKE] <con1|724> nothing to initiate
2022-07-26 09:20:00.100373+01:00 charon 5863 11[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:20:00.100444+01:00 charon 5863 11[ENC] <con1|724> parsed INFORMATIONAL request 27 [ ]
2022-07-26 09:20:00.100480+01:00 charon 5863 11[ENC] <con1|724> generating INFORMATIONAL response 27 [ ]
2022-07-26 09:20:00.100525+01:00 charon 5863 11[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:20:10.103514+01:00 charon 5863 15[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:20:10.103641+01:00 charon 5863 15[ENC] <con1|724> parsed INFORMATIONAL request 28 [ ]
2022-07-26 09:20:10.103738+01:00 charon 5863 15[ENC] <con1|724> generating INFORMATIONAL response 28 [ ]
2022-07-26 09:20:10.103852+01:00 charon 5863 15[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:22:59.538736+01:00 charon 5863 11[IKE] <con1|724> sending DPD request
2022-07-26 09:22:59.538788+01:00 charon 5863 11[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:22:59.538832+01:00 charon 5863 11[IKE] <con1|724> activating new tasks
2022-07-26 09:22:59.538888+01:00 charon 5863 11[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:22:59.538935+01:00 charon 5863 11[ENC] <con1|724> generating INFORMATIONAL request 17 [ ]
2022-07-26 09:22:59.539040+01:00 charon 5863 11[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:22:59.546468+01:00 charon 5863 11[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:22:59.546518+01:00 charon 5863 11[ENC] <con1|724> parsed INFORMATIONAL response 17 [ ]
2022-07-26 09:22:59.546541+01:00 charon 5863 11[IKE] <con1|724> activating new tasks
2022-07-26 09:22:59.546576+01:00 charon 5863 11[IKE] <con1|724> nothing to initiate
2022-07-26 09:23:03.314643+01:00 charon 5863 11[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:23:03.314727+01:00 charon 5863 11[ENC] <con1|724> parsed INFORMATIONAL request 29 [ ]
2022-07-26 09:23:03.314771+01:00 charon 5863 11[ENC] <con1|724> generating INFORMATIONAL response 29 [ ]
2022-07-26 09:23:03.314818+01:00 charon 5863 11[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:23:13.270108+01:00 charon 5863 08[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:23:13.270198+01:00 charon 5863 08[ENC] <con1|724> parsed INFORMATIONAL request 30 [ ]
2022-07-26 09:23:13.270266+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL response 30 [ ]
2022-07-26 09:23:13.270335+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:23:23.310863+01:00 charon 5863 08[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:23:23.310932+01:00 charon 5863 08[ENC] <con1|724> parsed INFORMATIONAL request 31 [ ]
2022-07-26 09:23:23.310968+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL response 31 [ ]
2022-07-26 09:23:23.311017+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:23:33.350443+01:00 charon 5863 15[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:23:33.350568+01:00 charon 5863 15[ENC] <con1|724> parsed INFORMATIONAL request 32 [ ]
2022-07-26 09:23:33.350618+01:00 charon 5863 15[ENC] <con1|724> generating INFORMATIONAL response 32 [ ]
2022-07-26 09:23:33.350696+01:00 charon 5863 15[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)I have the exact same settings from two other sites into Site B and it works no problems at all.
Additionally, I had to add port 500 into the firewall rules as otherwise I was getting
retransmit 4 of request with message ID 0errors when attempting to establish a connection. Now that's gone, but the problem persists!Chris.