Odd internet slowness with Netgear GS324TP Switch
-
@jarhead said in Odd internet slowness with Netgear GS324TP Switch:
BSD and having an untagged vlan on a trunk
I have not run into this, and I run a native untagged on the interface my vlans are on.
I am not sure where the problem is - but those speeds are horrible, so clearly something is wrong..
-
-
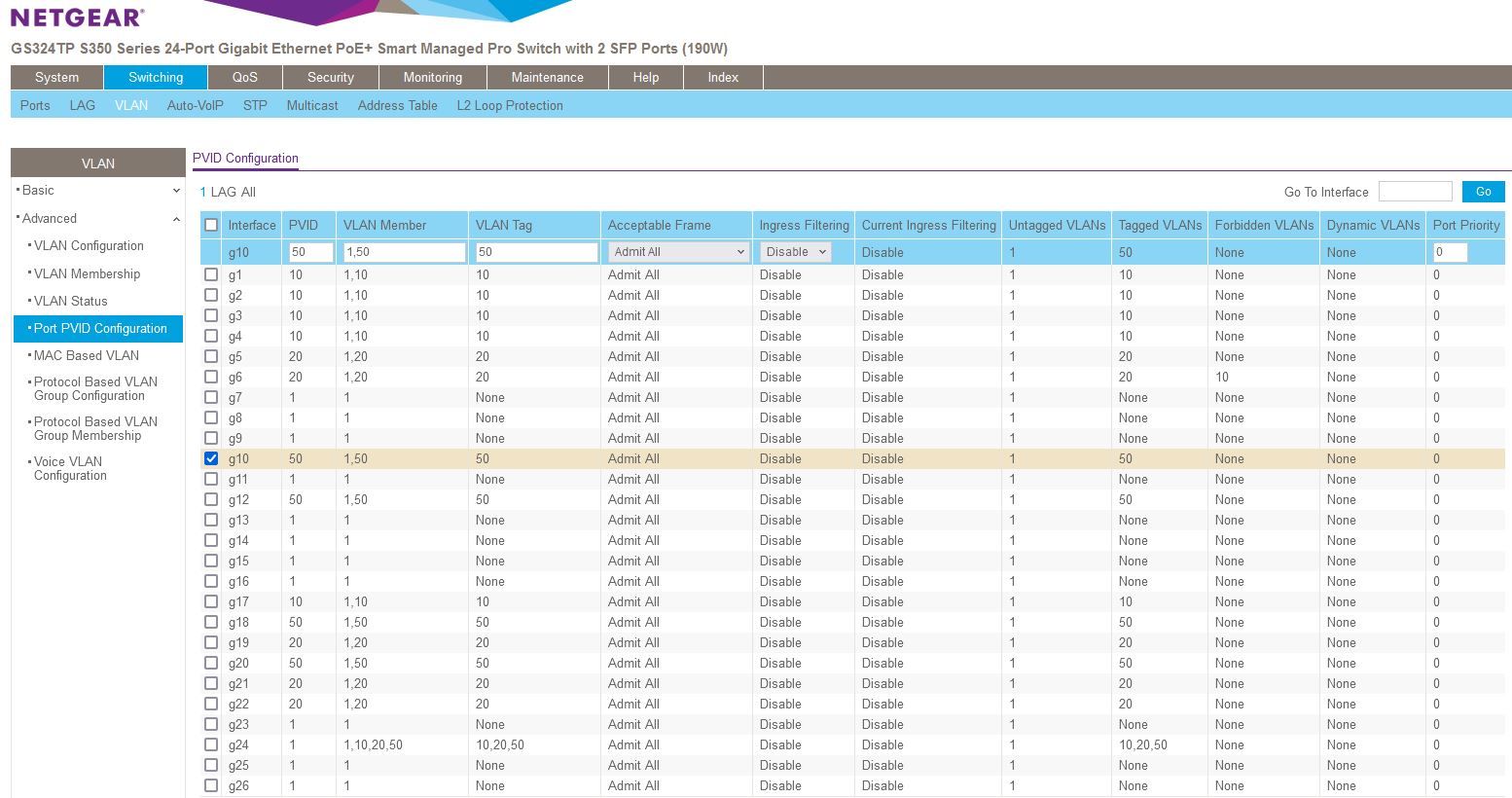
@creationguy You have every port untagged with vlan 1, why?
You also have ports that should be in the other vlans as tagged. They should be untagged.
Good rule of thumb, you only tag a vlan if the device you're plugging into that port is also tagged.
Remove vlan 1 from ports it's not being used on and untag the ports that are not trunked.
So ports 1-4 should be untagged with vlan 10 ONLY.
Ports 5 and 6 untagged with vlan 20 only etc. -
@jarhead I am new to VLANs, I found a couple of guides for Netgear managed switches and that's what worked. I've updated the settings:
VLAN 1 is a default VLAN on the switch that I can't seem to disable.In order for me to get the two devices on guest to obtain an IP, I had to:
Un-tag the two ports, and set their PVID to the VLAN as these devices are not 802.1q aware. I found this thread here.I don't have a way though to test if these devices can reach other VLANs. I do know that desktops on this VLAN 50 can't see devices on other VLANs, but those devices are not set up the same way (Untagged None).
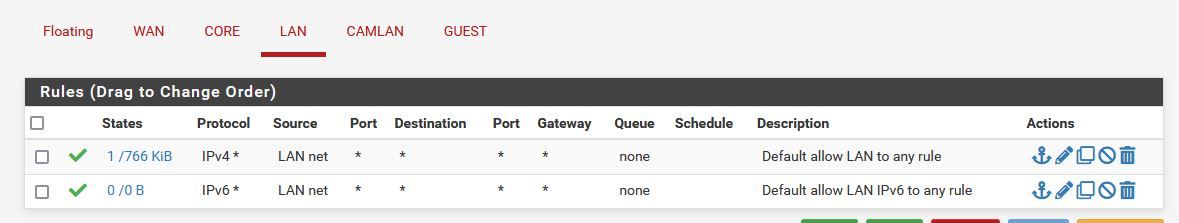
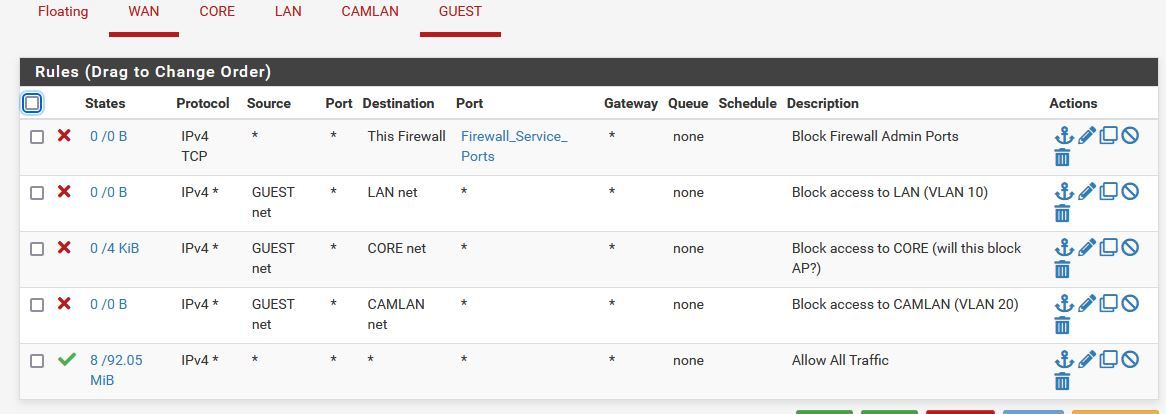
Edit: I placed a desktop in VLAN 50, the same manor as port 10 pictured above. I have a firewall rule set up so that 50 cannot access ANY, just internet. VLAN 10 can access all VLANs. This desktop cannot ping desktop in VLAN 10 until a desktop in VLAN 10 pings that VLAN 50 desktop. After awhile, VLAN 50 desktop can no longer ping VLAN 10 desktop. See below for the rules.
-
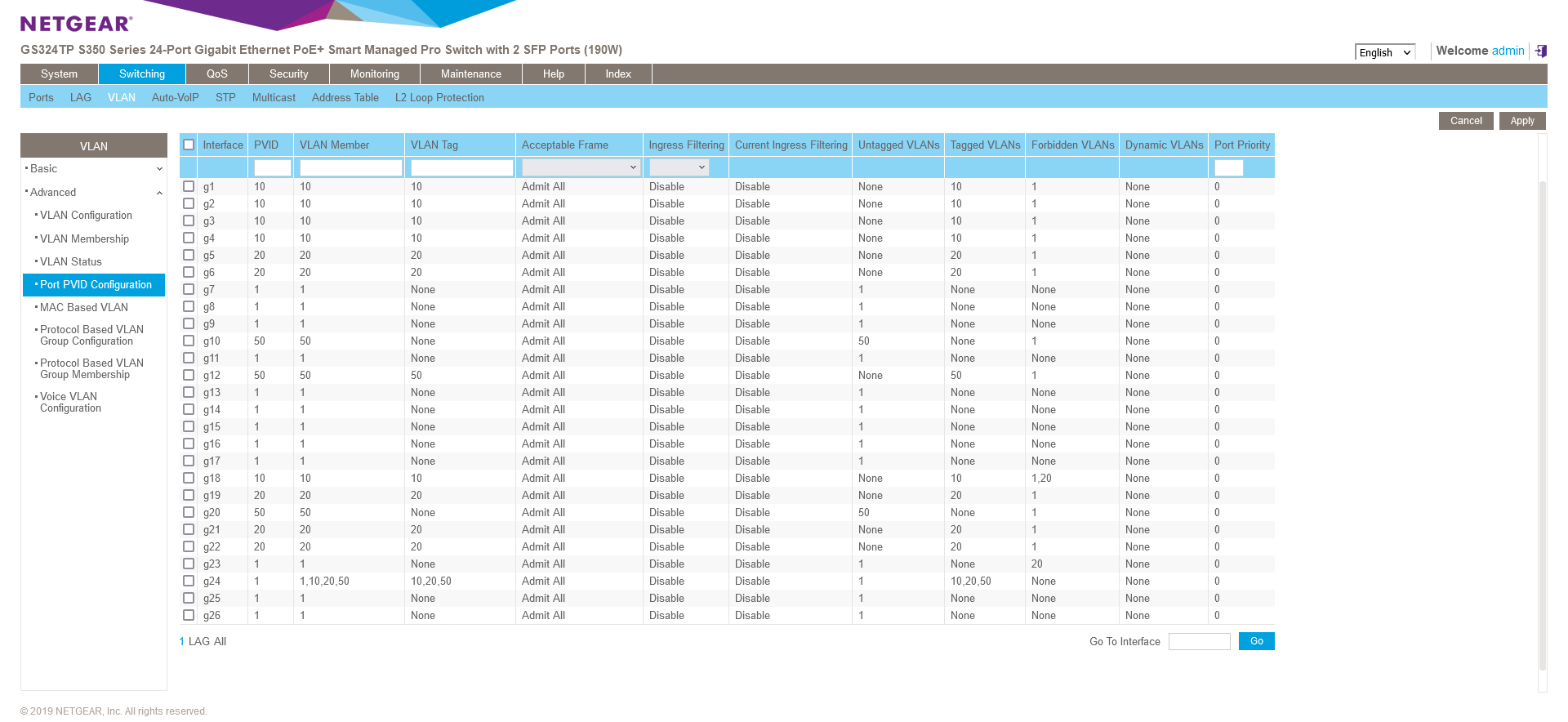
@creationguy You still have the ports tagged. They should be untagged unless your devices themselves are also tagged (hint: they aren't).
Ports 1-6 should be untagged ONLY. Nothing tagged on them. Along with all other ports that are "device" ports.
Only port that should be tagged is trunk ports (hint: port 24).
So only the port going to pfSense and any ports going to AP's that are using vlans if you have any. -
@jarhead I'm confused now- you should that ports 1-6, which I want on VLAN 10 should be untagged, are you saying untagged under the VLAN Tag column?
I reset the switch, and configured port 7 for VLAN 10.
Thank you for taking the time to help with this.
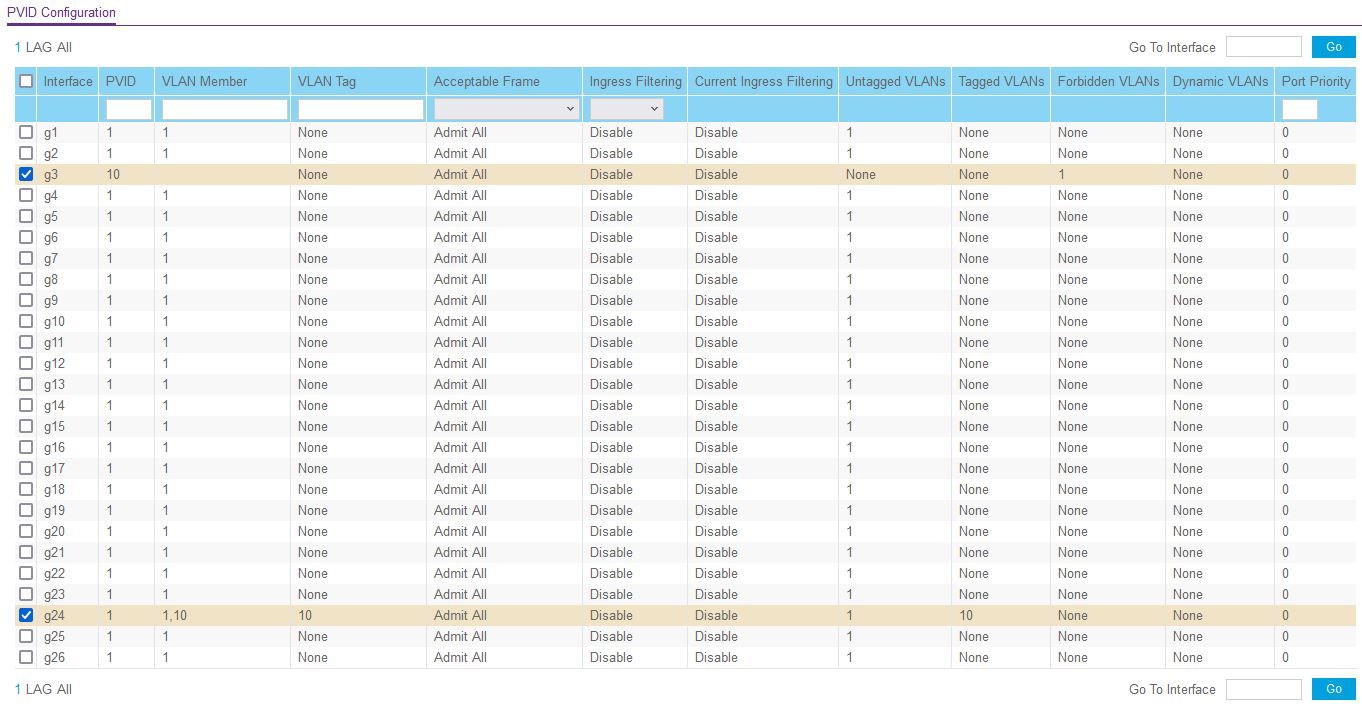
-
@creationguy Again, only tag a port if the device connected to it is also tagged.
So if you're plugging pc's into ports, they should be untagged ports.If you go back to the pic from the previous post, under the "Vlan tag" column, all ports should be NONE except the port going to pfSense (port 24).
1-4 should be untagged with vlan id 10, 5 and 6 untagged with vlan id 20.
They should all (except 24) look like port 20 except with the correct vlans on them.Fix the switch, then we'll get to the firewall. You have issues there with understanding rules.
@johnpoz will go into much more detail for you than I will but to sum it up, putting a rule on vlan 10 does not stop other vlans from talking to vlan 10. You need a rule on the other interfaces to do that.
That's why you could ping one way, which created a state that allowed you to ping the other way. -
@jarhead
Ports 1-4 should be on VLAN 10, with port 1 needing to access VLAN 1 which is the switch (built in Netgear setting).
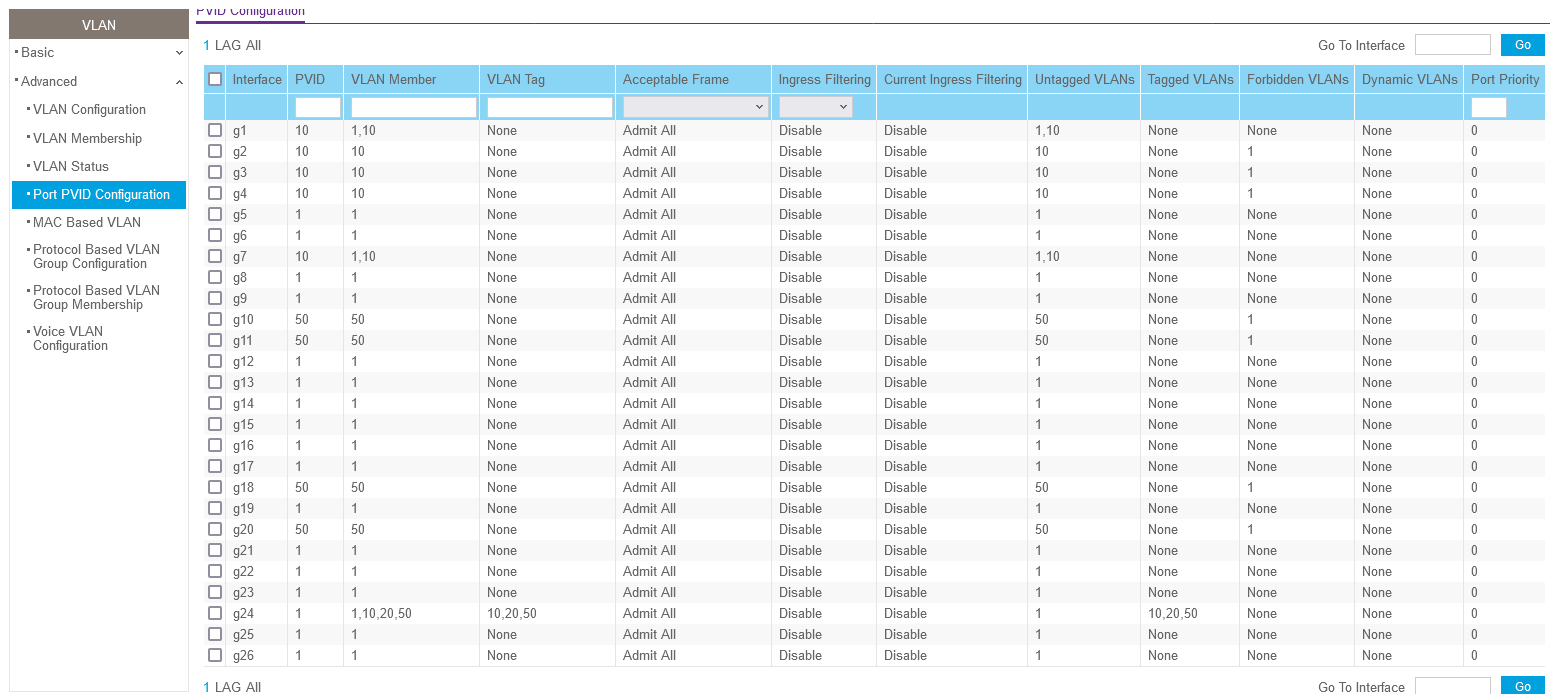
The others shown are guest devices, of which, can't access VLAN 10, unless the device on VLAN 10 pings it. Eventually it stops being able to ping it.
I thought that my rules were fine, as shown below, I have the Guest set to not be able to communicate with the specified VLANs.
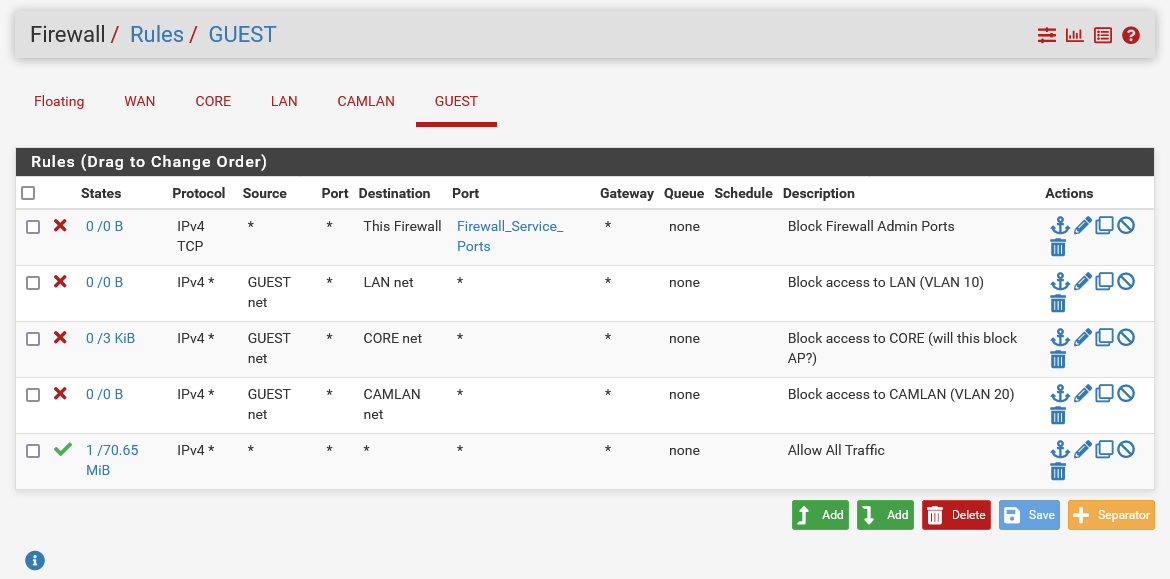
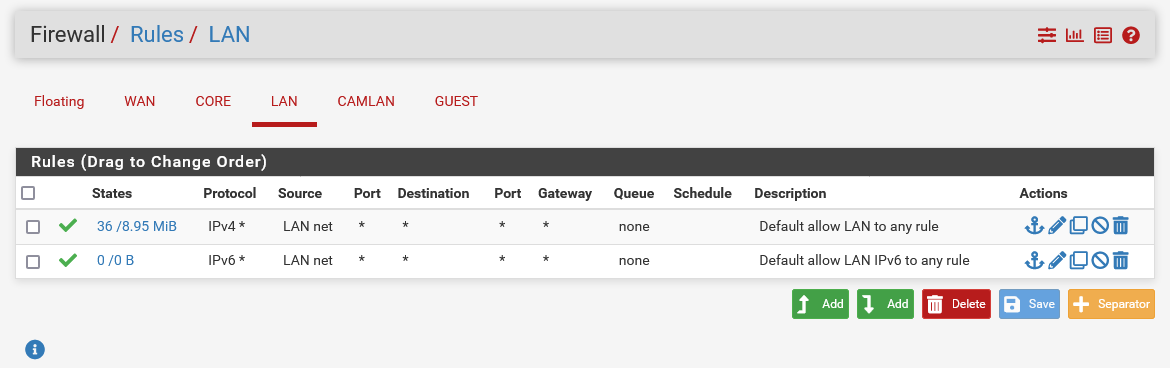
-
@creationguy said in Odd internet slowness with Netgear GS324TP Switch:
Ports 1-4 should be on VLAN 10, with port 1 needing to access VLAN 1 which is the switch (built in Netgear setting).
Having port 1 as untagged on two VLANs can cause problems and could result in data leaking into VLAN 10.
-
@creationguy Get rid of vlan 1 on ports 1 and 7. If you're saying you can't take it off of port 1, switch ports. ie leave port 1 at vlan 1 only and use port 5 as vlan 10.
As I said earlier, you'll need to add a rule on your other interfaces to stop them from accessing vlan 10. You can use the copy feature of your existing rule and just change the interface it's on and source/destination as needed. -
@rcoleman-netgate said in Odd internet slowness with Netgear GS324TP Switch:
@creationguy said in Odd internet slowness with Netgear GS324TP Switch:
Ports 1-4 should be on VLAN 10, with port 1 needing to access VLAN 1 which is the switch (built in Netgear setting).
Having port 1 as untagged on two VLANs can cause problems and could result in data leaking into VLAN 10.
How would I configure the port so that I could access the switch to manage?
-
@creationguy Had you tried iperf with the settings like that. Should see a difference now.
-
This post is deleted! -
@creationguy said in Odd internet slowness with Netgear GS324TP Switch:
How would I configure the port so that I could access the switch to manage?
Move your pfSense to port 1?
Also ... it should be accessible through pf via VLAN1 -
@rcoleman-netgate VLAN 1 isn't hard-coded by the switch to be on only Port 1, port 1 is just the port that my primary desktop is on where I would normally log into the switch to make changes. I took off VLAN1 from the ports, I can still access the switch. Looks like I'm all set there. Thanks for the information on data leaking.
@Jarhead Data transfer is still slow across the VLANs.
-
@creationguy Wow, saw a switch set the same as you originally had and once the vlans were corrected the problem was fixed. I'll see if I can find that thread for reference.
Next thing I would do is disable all firewall rules except the any any on all interfaces.
Can you try adding vlan 1 as tagged to the interface going to the switch? You would also have to tag vlan 1 on port 24 in the switch. ie No untagged vlans on the trunk.
-
@jarhead said in Odd internet slowness with Netgear GS324TP Switch:
You would also have to tag vlan 1 on port 24 in the switch
Tagging vlan 1 is not normal - many devices do not support it even.
Vlan one is just the default untagged vlan, there is no significance to the ID number to be honest. Untagged traffic coming in defaults to vlan 1, if you want untagged traffic to be on a different vlan, then just set that - there is nothing to do with vlan 1..
-
@johnpoz Not looking for untagged traffic, trying to get rid of it actually.
I have vlan 1 tagged with no issues.
-
@jarhead but does the sending device allow you to tag vlan1?
I just do not see the point of tagging vlan 1, just don't use it - have your device use vlan 100 or something and tag that.
-
@johnpoz Doesn't matter anymore. I found the bug I mentioned earlier in this thread and it was referring to tagged and untagged vlans on a bridge interface so wouldn't apply here.
Maybe it really is related to the dual nic?
Doesn't seem to be much more it can be a this point.@CreationGuy Any chance you have another nic you can add to the system?