LAN to LAN/OPT not working. What am I missing?
-
@kanagram
Two things to check here:Ensure the pfSense is the default gateway on all devices.
Ensure that the destination devices firewalls don't block access from outside their own subnet.
-
@kanagram such a problem screams what @viragomann has already mentioned. Either the device in your 10 network is not pointing to pfsense as its gateway.
Or the device your trying to pings firewall isn't allowing you. Which is why it pings from pfsense, because pfsense is pinging from its 10 address.
Windows out the box for example firewall will allow ping from local network, but some other network no.
Adjust your firewall on the 10 device your trying to ping to allow the traffic you want from your 192.168.200 network.
-
Thank you @viragomann and @johnpoz for your answers.
SOLVED!
For future colleagues with the same need:
Based on forum help I understood that this was not a routing problem, as I can't change my LAN2 GWs, so I needed to use NAT.I've just switched mode to hybrid NAT, and created an outbound rule:
Source:LAN1 destination: LAN2, leaving everything else by default.I've also double cheched the firewall rules to be fine.
And now I can ping from one LAN to the other.
Thank you.
-
@kanagram said in LAN to LAN/OPT not working. What am I missing?:
as I can't change my LAN2 GWs, so I needed to use NAT.
Wait .... Use NAT to ping from LAN to another LAN ? Then that s new.
The gateway talk also makes me think.
As you use a upstream ISP router using 192.168.1.1/24 on its LAN, you had to remaps the LAN network of pfSense as it use also 192.168.1.1/24 be default.
( I would have remapped the ISP router to 192.168.200.1/24 as it only has one client ;: pfSense )pfSense would be using the default DHCP client on its WAN interface.
You wouldn't have to "touch" any "gateway" or "routing" setting - no where.Again : why would you even need to change anything on the NAT pages ?
Mine are all default for yrears, and I can ping from any of my LAN interfaces any other LAN interface just fine.
That is, if there are firewall rules on all LAN interfaces that permit / do not block ICMPv4. -
@kanagram
What you did here is masquerading and is a bad workaround.
Don't recommend others to do this as well, please!This circumvents either that the firewall on the destination device blocks outside sources or that pfSense is not set as the default gateway.
Both possible reasons were already mentioned here. -
@gertjan In your configuration, everything in your LAN2 is using your pfsense box as its GW, so it can be solved with routing.
In my configuration, everything in my LAN2 is using another GW (not pfsense) and I can't change their GWs.
By enabling NAT, what I'm doing is basically managing the LAN2 as a WAN interface.
-
@viragomann Happy to learn better approaches. Thank you for sharing your thoughts. What I have is this:
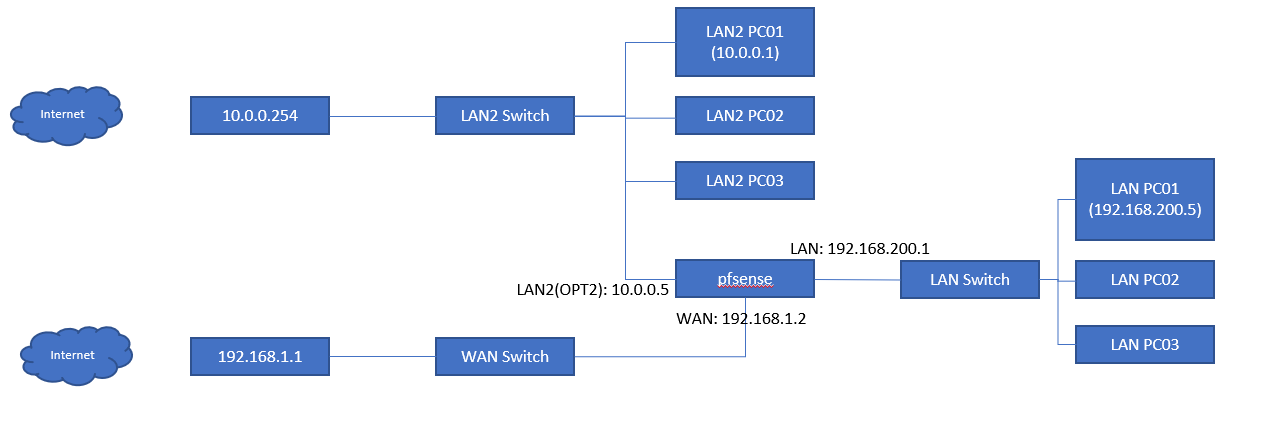
What I want is basically creating an isolated LAN that is able to have internet access and also access LAN2 PCs (without changing their configuration), but for the opposite to not to happen. LAN2 machines should not see LAN machines unless I define to open some ports.
What alternatives would you recommend for this approach?
-
@kanagram said in LAN to LAN/OPT not working. What am I missing?:
What I want is basically creating an isolated LAN that is able to have internet access and also access LAN2 PCs (without changing their configuration), but for the opposite to not to happen.
This part can be achieved with firewall rules.
The other part is the routing challenge.If you don't care to see the origin source IP address on the LAN2 devices, masquerading can be a proper solution for your. But under the terms of security it's a bad one.
Your set up is not well designed for routing between LAN and LAN2, since both network segments uses different upstream routers.
In a proper set up both upstream routers are directly connected together by a separated transit network and both have a static route for the respective network segment behind the other router. So all traffic from both networks is passing both routers.
Don't know if this is possible with your LAN2 router.If not the only way to avoid masquerading would be to add a static route for LAN pointing to pfSense to each LAN2 device.
-
@kanagram so you have 2 internet connections..
Why do you not just directly manage both of these internet connections on pfsense, and run whatever or how many networks behind pfsense that you want.
-
@johnpoz Thank you John. Because I can't change the LAN2 structure. It is not managed be me.
-
@viragomann Thank you for your suggestions.